Web applications are an integral part of digital businesses. If you want to grow and keep your business successful, you need to keep your web apps safe from malicious actors or hackers. Web application penetration testing ensures that you know about the weaknesses before cybercriminals take advantage of them. This builds trust among your clients/customers and gives you an edge over your competitors.
As per IT Governance’s research of January 2024, there were 4,645 publicly disclosed cyber security incidents and 29,530,829,012 records were known to be breached. As per Statista, there was a massive Yahoo data breach in the United States that impacted over 3 billion online users in the same month.
In this blog, we will focus on web application penetration testing, its benefits, and its methodologies.
What is Web Application Penetration Testing?
Web application penetration testing is a cybersecurity practice that involves simulating real attacks on web apps to identify and fix vulnerabilities. Pen testers, also called “ethical hackers”, use automated tools and manual techniques to go deep within the app to uncover complex security weaknesses. This is because hackers can use these weaknesses to get unauthorized access and perform illegal actions like data breaches and payment manipulation.
What is the Purpose of Web Application Penetration Testing
Technology is always changing and improving, and your cyber defenses that worked yesterday might not work tomorrow. More people are developing software that hackers can use to breach a website or web application. Additionally, as web applications often store sensitive data, people target it for their gain.
Web app penetration testing detects network vulnerabilities so that businesses take necessary steps to patch those flaws and prevent risks to their information. However, without regular pen tests, your business data can be accessed by cybercriminals, putting your organization and your clients at risk.
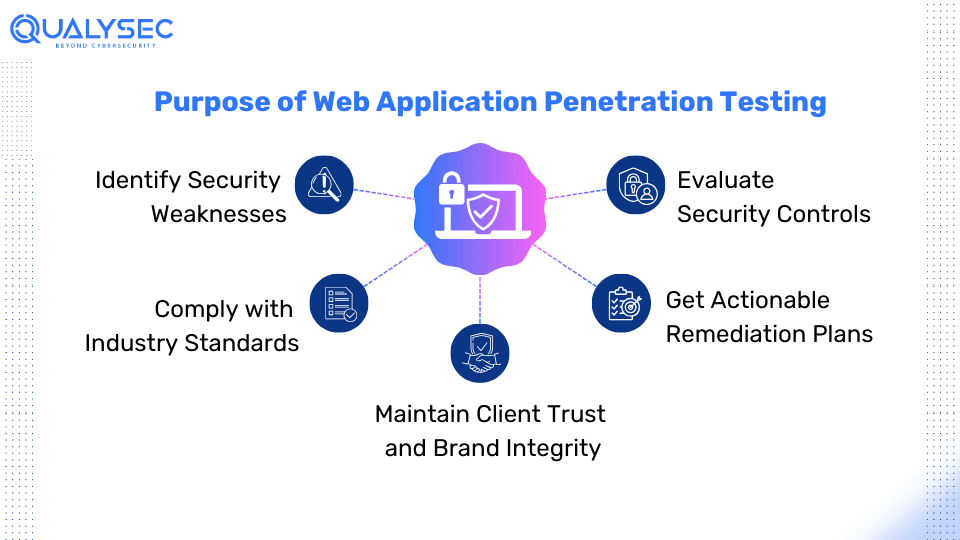
1. Identify Security Weaknesses
Discover vulnerabilities in the website or web application’s design and implementation that could range from simple misconfigurations to complex logical flaws.
2. Evaluate Security Controls
Assess the effectiveness of the cyber security measures implemented within the web application, including how well the application resists attacks and protects sensitive data.
3. Comply with Industry Standards
Website penetration testing can help ensure the application adheres to industry frameworks and regulations such as HIPAA, GDPR, PCI DSS, ISO 27001, etc., which are vital for maintaining trust and compliance requirements.
4. Get Actionable Remediation Plans
The web application penetration testing results have detailed findings and recommendations for developers to fix all the vulnerabilities effectively.
5. Maintain Client Trust and Brand Integrity
A company’s business and reputation can get severely damaged through a data breach. Regular penetration testing makes the website and web application secure. Additionally, it demonstrates trust and protects the brand’s reputation.
Do you want to secure your website and web applications from cyberattacks? Qualysec Technologies follows a hybrid approach of web app penetration testing that offers in-depth and accurate results. Use our services to find weaknesses in your web apps and fix them immediately. Click below now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Common Web Application Security Risks
There are various types of vulnerabilities that can harm a web application inside out, significantly hampering your business. Open Web Application Security Project (OWASP), a non-profit foundation that supports organizations in improving their security of web applications, has provided these top 10 security risks.
OWASP’s Top 10 Web Application Security Risks:
-
- Security misconfigurations
- Broken access control
- Authentication issues
- Cryptographic failure
- Injection flaws
- Vulnerable and outdated components
- Identification and authentication failures
- Insecure design
- Security logging and monitoring failures
- Software and data integrity failures
Different Types of Web Application Penetration Testing
There are basically three types of web app penetration testing that can be opted by businesses as per requirement. These are black box testing, white box testing, and grey box testing. The approach is determined through the level of information provided by the client to the pentester. Let’s discuss each of them in detail.
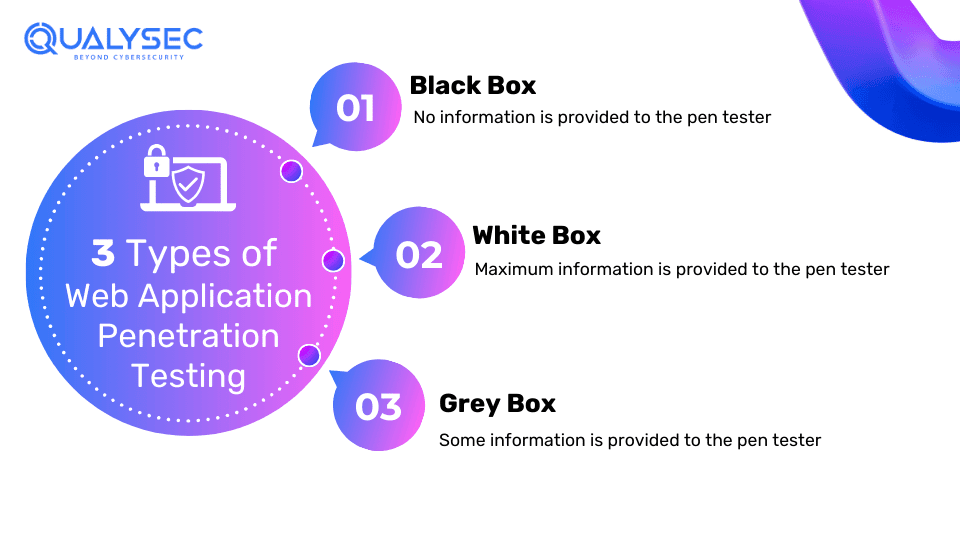
1. Black Box Penetration Testing
In Black Box penesting, the pentesters have no prior knowledge of the architecture, source code, or internal workings of the web application. This approach simulates how a hacker with no inside information would attempt to attack the application. In this process, the testers focus on discovering the vulnerabilities by interacting with the application, investigating inputs, and analyzing the responses.
2. White Box Penetration Testing
With White Box Pentesting approach, the pentesters are given complete access to the source code, internal architecture, and database schema of the web application. They can use various processes such as code review, architecture analysis, and design review to discover vulnerabilities. As pentesters have all the access, they can pinpoint the exact location of the vulnerabilities and the impact they can potentially have.
3. Grey Box Penetration Testing
Grey Box Pentesting is probably the most used and best approach for web application penetration testing. This is where the pentesters have limited information about the application, including a combination of some internal insights and external knowledge. As the testers have very limited but crucial information about the application, they focus on areas that are more likely to be vulnerable and offer a more realistic assessment.
Web Application Penetration Testing Methodology
Web app penetration tests focus on the web app environment by gathering information about the app from the client or using public web pages. Then they test the application with appropriate tools and techniques. The results of the pen tests are documented and sent to the client for further action.
Generally, cybersecurity companies follow an industry-standard Web app pentest methodology based on the OWASP Application Security Verification Standard (ASVS) and Testing Guide. However, some penetration testing firms modify these steps to offer more in-depth and accurate results.
1. Gathering Information:
The 1st stage of web application penetration testing is to gather as much information about the application as possible. This is where the company provides the necessary information to the penetration testing team. Additionally, the testing team can also gather information from publicly available web pages. They use this information and apply several approaches and tools to gain all the technical insights.
2. Planning
The pentesters establish their objective and goals by probing deep into the web application’s complex technicality and functionality. Through strategic approach and research, the testers modify their method to target specific vulnerabilities and cyber threats in the application.
A well-informed web application penetration testing strategy is created, which describes the scope, methodology, and testing criteria. Along with that, the business may also offer a high-level checklist to help guide the testers through their testing process.
3. Automated Vulnerability Scan
Then an automatic scan is done in a staging environment using automated vulnerability scanners. This is done to examine the web application’s surface level for vulnerabilities thoroughly. Through this invasive scan, pentesters can effectively identify and mitigate surface-level vulnerabilities.
4. Manual Penetration Testing
This is the main part of web app penetration testing. Penesters use manual techniques to simulate real-world attacks to find possible weak points. This technique provides a full evaluation of potential vulnerabilities in the web application. This strategy tests the resilience of web applications by looking for loopholes in authentication, data management, and other vital areas. As a result, it will eventually help improve the overall security of the web application.
5. Reporting
The penetration testing team locates and categorizes vulnerabilities discovered throughout the investigation. A senior cyber security consultant does a high-level penetration test and analyzes the results extensively. The report describes the vulnerabilities detected and the web application’s security status. This helps the client, and their developers get relevant and detailed information about the application’s security state and suggestions for maintaining a strong cyber security for their business.
Do you want to know what a real-time web application penetration testing report looks like? Download a copy of our sample report here!
Latest Penetration Testing Report

6. Remediation Support
If the development team needs help fixing the detected vulnerabilities, the penetration testing service provider can offer valuable support through consultation calls. In fact, they ask for direct engagement with the development to analyze and respond to the detected security problems of the web application.
7. Retesting
After the development team has completed the mitigation of the detected vulnerabilities, the testing team retests the applications. This is done to ensure that the mitigation worked, and the vulnerabilities are effectively eradicated. After all the retests are done, the final report will include the following sections:
-
- History of Discoveries
- State of Assessment
- Screenshots
8. LOA and Certificate
Along with the report, the web application penetration testing company will also provide a Letter of Attestation (LOA). This letter will contain the conclusion of the penetration testing and include:
-
- Confirmed security level
- Security information for stakeholders
- Completion of compliance
Along with that, the testing company will also provide a Security Certificate, which proves that you have successfully conducted penetration testing for web applications. As a result, the web apps are now safe and it is secure to use those services.
Difference Between Automated Vulnerability Scanning and Manual Penetration Testing
Businesses often confuse vulnerability scanning with penetration testing. Despite both methods having the same aim – finding vulnerabilities in the given application, their working structure is completely different. Additionally, it is best to choose a penetration testing company that offers both these services, as it helps with comprehensive results.
| Aspect | Automated Vulnerability Scanning | Manual Penetration Testing |
| Methodology | Uses automated tools to scan for vulnerabilities. | Involves skilled testers manually identifying, exploiting, and verifying vulnerabilities. |
| Coverage | Provides broad coverage by scanning large numbers of assets quickly. | Offers deeper coverage by simulating real-world attacks and exploring complex vulnerabilities that automated tools may miss. |
| False Positives | May generate false positives due to limitations in automated scanning algorithms. | Less prone to false positives as it involves human testers. |
| Customization | Limited customization options as it relies on a predefined scanning script. | Highly customizable as testers can tailor the testing approach based on the specific needs and objectives of the organization |
| Depth of Analysis | Provides surface-level analysis by identifying known vulnerabilities and misconfigurations. | Offers in-depth analysis by exploring potential real cyberattack vectors. |
| Expertise Required | Requires minimal expertise to operate automated scanning tools and interpret scan results. | Requires skilled security professionals with expertise in ethical hacking, network security, and application security to perform manual tests effectively. |
| Compliance and Reporting | Provides standardized reports with vulnerability summaries and severity ratings. | Offers detailed reports with findings, exploitation techniques, and remediation recommendations tailored to the organization’s requirements. |
Conclusion
Web application penetration testing helps in developing a safe and risk-free web app. As a result, it is a crucial factor in securing the Software Development Lifecycle (SDLC). It is advised to conduct penetration testing for your web application before or after pushing it for production. This is because penetration testing ensures business and its users are secure from cyber threats and data breaches.
Additionally, web application penetration testing helps to maintain brand reputation and comply with industry standards. Choose the pen test provider wisely and ensure they offer both automated vulnerability scanning and manual penetration testing for better results.
Scared about your web app? Leave us a message and we will get back to you with the latest penetration testing tools and techniques: https://qualysec.com/contact-us/
FAQs
Q: What is web application penetration testing?
A: Web application penetration testing is the process of simulating real attacks on a web application to find vulnerabilities that hackers can use to infiltrate. Additionally, it helps in assessing and improving the current security controls of the web application.
Q: Why web application security testing is important?
A: Since web applications store a ton of sensitive information, they are a primary target of cybercriminals. Penetration testing helps identify potential weak points in the applications, thus strengthening the overall security.
Q: How can we secure web applications?
A: The best way to secure web applications is by conducting regular penetration testing. It helps find security flaws in the web app and suggest methods to fix them.
Q: What is the difference between network and web app pentesting?
A: Network pentesting mainly focuses on the design, implementation, and maintenance of a network. Web app pentesting focuses more on the application and the security surrounding it, such as coding errors and insecure software use.
































































































































































































































































































































































































































































































































0 Comments