In this interconnected world, the security of digital assets is inevitable. The data, applications, and resources of organizations stored online are always vulnerable to some kind of cyber threat. To protect them, the best option is to implement vulnerability assessment and penetration testing (VAPT) services. These services find and fix potential vulnerabilities that could be exploited by cyber attackers or hackers.
As per a report from IBM, the highest recorded data breach in 2023 was $4.35 million, with an average ransomware attack costing $4.54 million. Cyber security experts predict that global cybercrime costs will grow by 15% in each upcoming year, reaching $10.5 trillion annually by the end of 2025.
With data breaches and cybercrimes increasing exponentially, having strong security for your digital assets is now more important than ever. In this blog, we will discuss vulnerability assessment and penetration testing, their importance, and the different types that organizations can choose from.
What is Vulnerability Assessment and Penetration Testing
Vulnerability assessment and penetration testing are two parts of vulnerability testing that are often combined to achieve a comprehensive vulnerability analysis. Vulnerability assessment tools identify vulnerabilities that are already present, however, they do not differentiate between the security flaws that can be used by attacks to cause damage. Penetration testing, on the other hand, detects all those vulnerabilities that can be used for unauthorized access or to conduct any kind of malicious activity.
Together, the entire VAPT process provides a detailed report of the security flaws present in the IT environment and the risks associated with them.
Vulnerability Assessment VS Penetration Testing
Vulnerability assessment involves using automated tools to identify vulnerabilities in the security measures. In contrast, penetration testing is done manually by cyber security professionals, to determine vulnerabilities that hackers could exploit.
| Vulnerability Assessment | Penetration Testing |
| Focused on detecting and categorizing vulnerabilities in the tested environment. | It involves simulating real-world cyberattacks to find vulnerabilities in the tested environment. |
| Mostly automated scans. | Requires manual testing along with automated scans. |
| May miss critical and complex vulnerabilities. | Detects all kinds of vulnerabilities, even the ones that vulnerability scans miss. |
| Takes significantly less time and money than penetration testing. | It is time-consuming and expensive but yields better results. |
Penetration Testing
Penetration testing involves finding vulnerabilities, security flaws, and risks in a digital environment. It is done to improve the organization’s security system and defend the IT infrastructure from evolving cyber threats. Penetration testing or pentesting is a part of the ethical hacking process that specifically focuses only on penetrating the IT environment.
Vulnerability Assessment
Vulnerability assessment is a security testing technique to find and measure security issues in a given environment. Furthermore, it uses automation tools to assess the security position of the given area. It identifies potential vulnerabilities and provides required mitigation techniques to either remove them or reduce them below the risk level.
The report of Vulnerability Assessment and Penetration Testing (VAPT) will consist of all the vulnerabilities found and recommendations to fix them.
Benefits of Conducting Vulnerability Assessment and Penetration Testing
Vulnerability Assessment and Penetration Testing (VAPT) services provide organizations with a more comprehensive evaluation than any single test alone. Further, here are the many benefits of conducting VAPT:
Identify Vulnerabilities Before Cybercriminals
Nowadays cybercriminals are using automated tools to find and exploit vulnerabilities in an IT infrastructure. These tools scan networks, open ports, and use many other techniques to find any weaknesses and then use them to gain access and execute malicious activities.
Organizations can conduct vulnerability assessments and penetration testing to track down these weaknesses. This way you can remove them before criminals use them for their benefit and strengthen the overall security posture.
Streamline the Fixes you Need to Do
Some vulnerabilities are difficult to find and may not be recognized until they are identified. Because of VAPT, you can uncover these flaws, and help you remediate them. Rather than applying random fixes across the network components, you can pinpoint specific vulnerabilities that need fixing. In addition, you will also be able to know what areas should be given more priority.
Protect the Integrity of your Digital Assets
Many vulnerabilities are also found in malicious code that are hidden inside applications and services. As a result, cybercriminals can use them to steal sensitive data. However, with regular vulnerability assessment and penetration testing services, you can find these weak spots effectively and ensure that your digital assets are safe.
Comply with Industry Standards
One of the most important benefits of conducting vulnerability assessment and penetration testing is you can comply with certain mandatory regulatory standards. Certain industries like healthcare and finance need organizations to meet their standards of HIPAA and PCI DSS. If you do not meet the requirements, it may lead to severe financial penalties and reputation damage. For this reason, VAPT is conducted regularly by organizations.
Enhance Credibility with Customers and Partners
Your customers, partners, and stakeholders are the ones who drive your business forward. Doing regular vulnerability assessment and penetration testing as a part of your security measures shows that you take the security of your business seriously. As a result, it builds credibility with them since they find it secure to do business with you. It’s an easy and effective way to tell them that their data is secure with you.
How do VAPT Services Prevent Data Breaches?
Data breaches are among the top challenges faced by organizations in the digital world. It is also equally challenging for individuals who face security risks like financial loss, identity theft, and loss of trust. Data stands as the most important yet weakest asset in any organization. For this reason, companies conduct VAPT services to protect their network and data from various cyberattacks.
VAPT involves finding weaknesses present in the existing security measures. As a result, conducting regular VAPT services will reveal through which hackers or attackers could enter the network and do malicious acts like stealing sensitive data.
Do you want to keep your organization’s sensitive data safe from hackers? Book a consultation with Qualysec Technologies now and secure your data from potential breaches!
Types of Vulnerability Assessment and Penetration Testing Services
Vulnerability Assessment and Penetration Testing (VAPT) consist of a broad range of security testing services, designed to identify and fix cybersecurity flaws across the organization’s IT infrastructure. To ensure you choose the right type of VAPT service for your company, it is important to understand each of them. Furthermore, each VAPT service can vary significantly in scope, timeline, and price. So make sure you choose the one your company needs the most.
Web Application VAPT Services
Web application VAPT is a security testing method conducted to find security flaws or vulnerabilities in web applications and corporate websites. These vulnerabilities keep the websites and web apps open for hackers or attacks to carry out malicious acts like unauthorized access, data breaches, and more. As companies are consistently moving their most crucial business on the web, they have become a major attack point.
Benefits of Conducting Web App VAPT Services:
- Secure web apps and websites from hackers
- Prevent data stealing
- Prevent financial loss
- Comply with certain industry regulations
- Increase trust for customers and partners
- Increase return on investment (ROI)
Mobile App VAPT Services
Nowadays almost every individual carries a mobile device and uses several apps. As a result, more and more companies are producing mobile apps to enhance their reach. However, this is giving rise to multiple cyber threats that are constantly evolving.
Mobile app VAPT services or mobile app vulnerability assessment and penetration testing involves systematically scanning app code and its functionalities for vulnerabilities. Penetration testers simulate real-world attacks to find out security flaws that could be exploited by hackers.
Benefits of Mobile App VAPT Services
- Protect mobile app data from hackers
- Prevent unauthorized access
- Prevent monetary loss
- Comply with industry standards
- Enhance reputation and trust
- Optimize mobile app performance
Network VAPT Services
Network VAPT services involve vulnerability scanning and penetration testing techniques to find weaknesses in the network and network devices of an organization. As businesses and individuals connect through the network, attackers target them to gain unauthorized access. Network VAPT checks the strength of existing network security and finds and fixes security gaps in them.
Benefits of Network VAPT Services
- Identify network vulnerabilities
- Enhance network security
- Ensure compliance with industry regulations
- Prevent unauthorized access to network resources, including servers, databases, and internal systems.
- Enhance trust among stakeholders
API VAPT Services
API vulnerability assessment and penetration testing services is a security testing process that targets RESTful APIs to discover potential vulnerabilities, security flaws, and coding errors, which could result in data breaches or system crashes. VAPT services for APIs usually involve assessing the API’s design and architecture, checking its input validation, identifying existing vulnerabilities, and analyzing authentication mechanisms, access controls, and data handling processes.
Benefits of API VAPT Services
- Prevent unauthorized access, data breaches, and leaks
- Comply with data security and privacy regulations
- Identify API vulnerabilities
- Improve API’s performance
- Save potential costs from data recovery and remediation
Cloud VAPT Services
Cloud VAPT or vulnerability assessment and penetration testing services involve detecting and exploiting security flaws in cloud infrastructure by simulating a real and controlled cyberattack. it is performed by cybersecurity professionals under the guidelines of cloud service providers like AWS and GCP. The process helps in finding and fixing security gaps before they are used by hackers or attackers for malicious activities.
Benefits of Cloud VAPT Services
- Identify cloud security risks
- Prevent data breaches and unauthorized access in the cloud environment
- Ensure compliance with regulatory requirements
- Optime the usage of cloud resources
- Secure cloud environment from third-party risks
- Build customer and partners’ trust
IoT VAPT Services
Though IoT devices bring a lot of convenience into our lives, these connected devices also bring a lot of security concerns. Inadequate security measures, weak authentication and authorization, and vulnerabilities in third-party software can make an IoT device prone to various cyberattacks. IoT VAPT services are a systematic approach to finding and mitigating potential vulnerabilities and risks at every stage of an IoT device’s lifecycle.
Benefits of IoT VAPT Services
- Improve the security of IoT devices
- Reduce cyberattacks and data breaches
- Identify and mitigate evolving risks with IoT infrastructure
- Comply with relevant industry standards
- Build trust among customers
- Save financial and reputational costs associated with cyberattacks
AI/ML VAPT Services
Artificial intelligence (AI) and Machine Learning (ML) are being integrated with almost every web application and software nowadays and will continue in the future too. With this integration, the security concern has also increased in these applications. AI/ML VAPT services identify, examine, and remediate vulnerabilities present in AI/ML applications, along with recommendations to enhance their overall security. because AI applications store sensitive data and have powerful decision-making mechanisms, cyber security is a must for them.
Benefits of AI/ML VAPT Services
- Find and fix security vulnerabilities in AI/ML applications
- Enhance AIL/ML Model security
- Reduce the risk of data breaches and tampering
- Identify and mitigate biases within AI/ML models
- Ensures compliance with regulatory requirements and ethical guidelines
- Optimize performance and accuracy of AI/ML applications
Source Code Review
Source code review is a vital part of the secure software development lifecycle (SDLC). It involves a detailed analysis of the programming code of a software or application to detect vulnerabilities that hackers could exploit. Skilled cybersecurity professionals use vulnerability assessment and penetration testing methods to analyze the code’s design and implementation flaws to identify potential security risks.
Benefits of Source Code Review
- Find bugs early
- Comply with coding standards
- Ensure consistency in design and implementation
- Optimize code for better performance
- Higher software or application security
- Increase confidence of stakeholders
Common Vulnerability Assessment and Penetration Testing (VAPT) Process
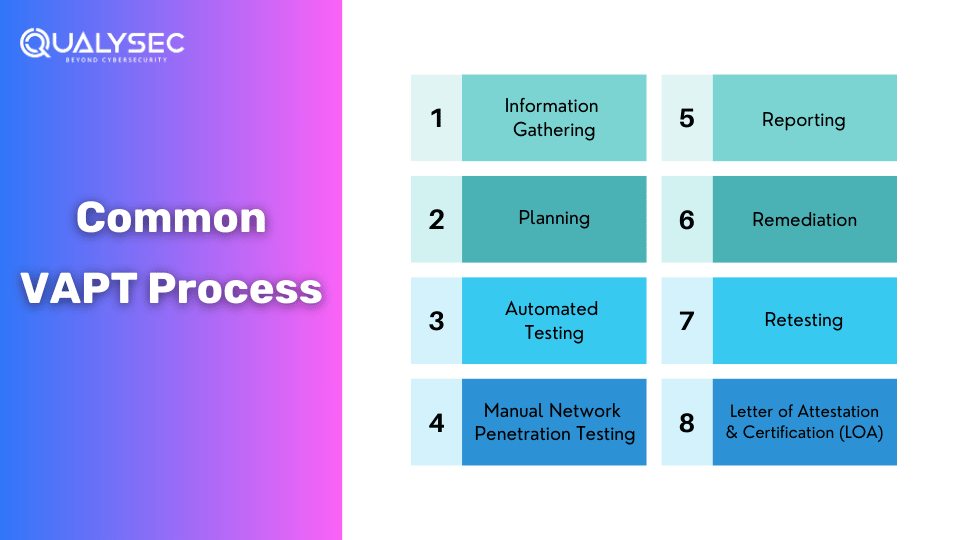
From gathering information to retesting, there are quite a few steps that are commonly used in the vulnerability assessment and penetration testing (VAPT) Process. Though the information and scope may vary for each environment that is being tested, the core procedure remains the same.
Vulnerability assessment involves using specialized tools to perform vulnerability scans to find vulnerabilities in the application. On the contrary, penetration testing involves expert cybersecurity professionals manually simulating real-world cyberattacks to uncover security flaws.
After all the testing is done, the VAPT company provides a report to the organization. The report contains a summary of the testing process and the vulnerabilities found. In addition to that, the report will also consist of remediation methods to fix those vulnerabilities. After the necessary fixes are done, the tested environment is retested to check whether the remediation worked or not.
Common Tools used for VAPT Services
Vulnerability assessment and penetration testing (VAPT) tools help detect vulnerabilities present in an IT infrastructure. They also offer a wide range of features such as automating certain tasks, generating reports, and collaborating with other team members. With so many VAPT tools available, it can be overwhelming to know which one works best. So here are a few tools that work wonders for VAPT services:
- Nmap
- Metasploit
- Nessus
- Wireshark
- Burp Suite
- Nikto
- OpenVAS
- Sqlmap
- W3af
- Kali Linux
- Netsparker
- Zed Attack Proxy
- MobSF
- Pacu
Conclusion
Vulnerability assessment and penetration testing (VAPT) services are essential to find and address cyber threats and vulnerabilities that hackers could use to exploit the system. Along with actively rectifying potential risks in an IT infrastructure, VAPT services enhance the overall security posture of the organization.
The combination of automated vulnerability scans and manual penetration testing techniques offered by Qualysec Technologies provides a systematic approach to strengthen security posture. Regular VAPT services are essential to protect sensitive data, comply with necessary industry standards, safeguard digital assets from evolving cyber threats, and maintain the reputation of the organization.
FAQs
Q: What are VAPT Services?
A: VAPT stands for vulnerability assessment and penetration testing, which is a security testing measure to identify vulnerabilities in applications, networks, cloud, and other digital assets. Both vulnerability assessment and penetration testing have specific techniques and strengths and are often done together to achieve a comprehensive analysis.
Q: What types of vulnerabilities VAPT services can detect?
A: VAPT services can detect various types of vulnerabilities such as misconfigurations, weak authentication mechanisms, weak encryption, insecure network protocols, code errors, and more.
Q: How often should VAPT be conducted?
A: Typically, VAPT should be conducted regularly, at least once or twice a year. Organizations should also conduct VAPT when there is a big change in their digital infrastructure or if they want to comply with industry standards.
Q: How to choose the right VAPT service provider?
A: Consider the following factors while choosing the right VAPT service provider:
- Check expertise and experience
- Evaluate track record
- Review methodologies and tools used
- Consider compliance and industry standards
- Check the pricing
- Seek references and recommendations
































































































































































































































































































































































































































































































































0 Comments