A recent study by Gartner concludes that 80% of compliance leaders find third-party risks after initial onboarding and due diligence processes have been conducted; this reflects the increasing complexity of third-party relationships. This raises the need for risk management approaches in third-party management.
Investing in vendor risk assessment procedures—such as enhancing procurement processes, encouraging supervision, and mitigating associated risks with vendors—can yield organizations substantial benefits; the advantages are not limited to these. To delve further into this crucial practice of vendor risk assessment, read our blog for an in-depth exploration of its significance and effective conducting methods.
What is Vendor Risk Assessment?
Vendor risk assessment is the process of evaluating risks that may arise from outsourcing business to third-party vendors, suppliers, and contractors. Vendor risk assessments allow firms to understand the exposure levels associated with these third-party entities and help them gain insights into security, privacy, and other threats that could emerge when vendors are involved in handling data, business operations, or customer interactions. It provides a holistic understanding of various threats that may challenge the organization.
What is a Vendor Risk Assessment Process?
A vendor risk assessment examines potential risks while engaging external partners. It has five key stages in the process:
- Selection: Initial screening to shortlist vendors with low-risk levels
- Onboarding: Vetting controls by the vendor before allowing access
- Monitoring: Regularly checking performance, contracts, and compliance
- Termination: Ensuring data protection when relationships come to an end
- Incident Response: Assessing the impact of the breach and creating mitigation plans.
A vendor risk assessment usually consists of issuing questionnaires for the vendors to detail the information security controls, data protection policies, compliance frameworks, subcontracting practices, and many more. Companies may gather financial, legal, and operational information to scope broader business risks.
Vendor assessments help organizations evaluate the risks that arise from vendor exposure. Security teams can assign a risk score and identify possible impacts across issues such as data breaches, service disruptions, audits, regulations, and reputation. Initial assessments take place in the screening and selection of a vendor. Follow-up assessments enforce compliance with regulatory standards and prevent unanticipated threats initiated by vendors.
Why Vendor Risk Assessment is important?
Vendor risk assessments play a very important role in controlling potential risks by third-party service providers. It allows vendor risk assessments that ensure careful management of risk when outsourcing services, sharing data, or giving supplier network access.
With greater responsibilities undertaken by vendors, the regulatory landscape further requires proper third-party risk assessment. Assessments provide continuous visibility into vendor performance and policy changes. They help confirm that vendors uphold security and privacy standards throughout the business relationship and enable organizations to be better positioned to reduce impacts from security incidents.
Identifying and mitigating risks early on can save you from financial losses in case of security breaches or operational disruptions. Therefore, an active third-party risk assessment process is crucial to promoting operational resilience, business continuity, compliance with standards, data security within the vendor ecosystem, and effective governance of third-party relationships.
Vendor risk assessments are more than just looking for vulnerabilities. It is an opportunity to start meaningful dialogues with vendors about security measures, compliance issues, and mutual expectations. By actively collaborating to mitigate the risks at hand, you fortify partnerships. This results in enhanced security and stability.
When to do a Vendor Risk Assessment?
Regular vendor risk assessments must be performed to maintain security, privacy, resilience, and compliance at all levels of vendor relationships. The results of such assessments give an insight into the trends of risks over time and enable holistic governance with targeted oversight of every individual provider. Below are some critical points that should be performed in organizations at the following stages:
1. Onboarding process:
First, do thorough inherent risk assessments before thinking of adding new vendors and, in the process, be aligned with your target risk tolerance.
2. Pre-audits
Whether internal or external, preparation for an audit calls for a risk assessment of the vendor involved in the process to ensure adherence to regulatory requirements and compliance with audit expectations.
3. Recurring assessments
Regular risk assessments should be conducted throughout the lifecycle of the vendor relationships. Periodic evaluations ensure ongoing compliance, assess changes in risk status—and validate adherence to agreed-upon standards.
4. Upon contract renewals
Reassess the risk profile of your vendors before renewing contracts. This process ensures that your vendors’ risk aligns with your evolving business needs and standards before contract renewal.
5. During incidents
A vendor risk assessment is necessary in case of security incidents or breaches. This gives you an understanding of the scope of the violation and allows you to determine its impact on your organization—crucial steps toward developing effective incident response plans.
6. During Termination
When terminating a vendor relationship, a final assessment is necessary. It ensures proper migration or secure disposal of sensitive data that confirms adherence to contract terms.
How to do Vendor Risk Assessment?
The business needs to perform a vendor risk assessment to develop an assessment strategy. This helps a business understand vulnerabilities related to its vendors. It enables businesses to develop effective plans addressing them.
Here are the 6 steps to performing vendor risk assessment:
Step 1: Assigning roles
Start by building a cross-functional team consisting of stakeholders from different areas such as risk management, procurement, IT compliance, and security operations. Every role brings unique priorities, uniting perspectives, and knowledge to the vendor risk assessment process. The collaborative approach ensures that all risks connected with third-party relationships are covered comprehensively while promoting an understanding of the multi-faceted aspects of vendor risk assessment.
Step 2: Establish your risk appetite
After assembling your team, assess and define an acceptable level of risk your organization can tolerate. Critical to this step is the evaluation and definition of various types of risk: data security, financial risks, and operational risks. A risk matrix method helps streamline this process.
Step 3: Calculating your risk matrix
This matrix helps categorize critical risks for you: anything scoring above a 6 on our 10-point scale signals an imminent danger. It further helps in identifying risk thresholds once we establish some remediation plans, thus enabling us to assess with precision and clarity. This way, we can weigh if the benefits are worth the risks we’re taking.
Step 4: Establish vendor risk assessment process
Now that we know what risks we are comfortable with, it is time to set up our game plan for checking out potential vendors. Develop a structured and standardized vendor risk assessment process. Tailor the process to suit different vendors based on their criticality, access to sensitive data, or susceptibility to continuity events. Start with internal profiling and tiering review that will classify vendors as well as define the type, scope, and frequency of assessment needed per classification.
Step 5: Vendor risk assessment questionnaire
We distribute comprehensive questionnaires to our vendors or groups of vendors following this step. Security questionnaires try to gain essential information regarding the vendors’ internal controls, information security practices, compliance requirements, financial stability, and third-party supplier data.
For example, questions may focus on the data encryption techniques to protect information, access control mechanisms, compliance with particular regulatory requirements, such as GDPR or HIPAA, financial health indicators, and the level of scrutiny applied to their supply chain. Standardized or proprietary questionnaires are determined by the preference of the organization and current industry best practices.
Step 6: Continuously monitor risks
Continuous risk monitoring will help you track evolving cybersecurity vulnerabilities, regulatory compliance requirements, credential risk exposures, data breaches, operational disruptions, financial instabilities, or reputational risks associated with the vendor ecosystem.
Step 7: Categorize and remediate risks
Identify the risks and categorize them as acceptable or unacceptable based on the organization’s risk tolerance levels. The unacceptable risks must be remediated before engaging with the vendor. Remediation strategies may include requesting security certifications, discontinuing relationships with associated vendors, or modifying business practices to mitigate risks.
Five Best Practices for Effective Vendor Risk Assessment
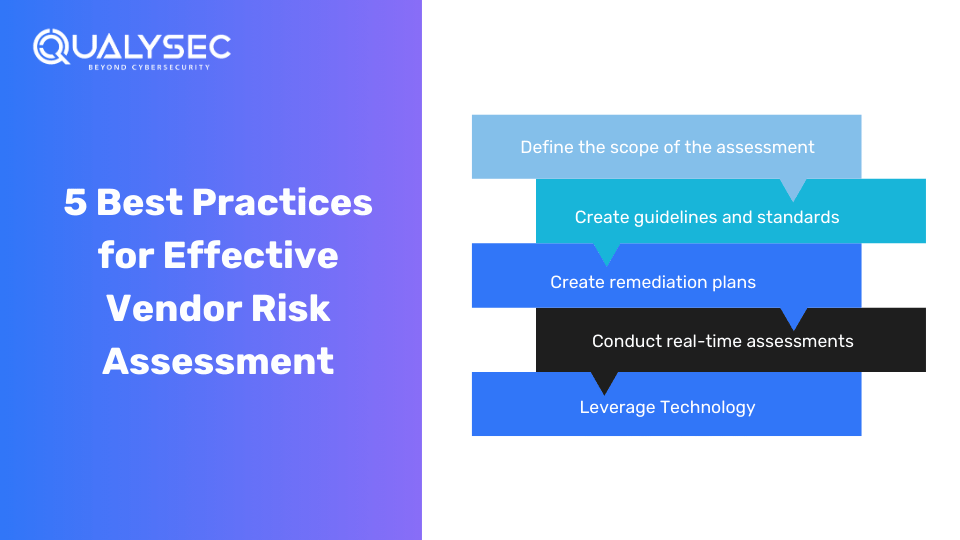
Managing thirty-party vendor risks is the most important aspect of today’s business landscape. To proactively assess and mitigate potential risks posed by vendors, implementing these five essential best practices in vendor risk assessments is crucial:
Define the scope of the assessment
- Start by recognizing the inherent risks to kick off assessments.
- Tailor assessments to focus on key areas without unnecessary scrutiny.
- For example, focus on security risk assessments only for the vendors that need access.
Create guidelines and standards
- Create questionnaires with expectations of specific answers.
- Establish clear standards on how the vendors should answer.
- Ease the identification of risks by providing guidelines on expected answers.
Create remediation plans
- Create a catalog of suggested actions associated with identified risks.
- Provide pre-defined guidance for the quick and efficient resolution of risks.
- Simplify the process of risk resolution with ready-made solutions.
Conduct real-time assessments
- Combine due diligence questionnaires with ongoing monitoring for deeper insight.
- Assess vendors through their reported data and other external information.
- Obtain a panoramic view of vendor risks through a holistic assessment approach.
Leverage Technology
- Apply automation to simplify the process of security risk assessment, data gathering, and managing risks.
- Look for reliable software partners that can offer comprehensive oversight of the risks from the vendors.
Qualysec Helps Create an Effective Vendor Risk Management Approach.
A compliance automation solution such as Qualysec helps you put together a robust third-party vendor risk assessment process while helping to rapidly expedite audit readiness on the relevant security framework. You can add the vendors directly to the platform, and you can decide the type of information the vendor has access to; automatically, the risk will be calculated. A due diligence report and its reviews can be added along with maintained from a dashboard centralized.
Reach out to our compliance experts now to streamline vendor management and tie it to security compliance.
FAQs
1. Why is it so vital to do vendor risk assessments for your business?
Vendor risk assessments serve as risk mitigation measures for your business relationships. They are critically important in helping you establish risks and vulnerabilities that are likely to affect your operations and data security as well as your reputation. By understanding these risks and being able to manage them appropriately, your business will be safeguarded against disruptions and financial loss.
2. When should we conduct vendor risk assessments?
We suggest having regular assessments, especially on new vendor onboarding and at intervals during a vendor relationship cycle. The nature of your business, the criticality of vendor relationships, and changes in the business environment may dictate the frequency at which you hold vendor risk assessments.
However, using an automation tool streamlines this process by automating your assessments, continuously monitoring the changes, and keeping a current understanding of vendor risks.
3. Which information can we get from the vendors to aid the assessment?
During the process of making vendor risk assessments, details about the operations of the vendor, their security practices, compliance measures, financial stability, and subcontractor relationships are typically gathered. The information becomes helpful in ascertaining the possible risks linked with that vendor.
Further, it doesn’t just make sure alignment of your business with its standards but it also opens ways to a more strategic approach in the decision of collaborations and partnerships.
4. Are there specific tools or software for vendor risk assessments?
Yes. Such vendor risk management software and tools do exist. With such tools, you can automate tasks, manage data, and offer insights that are comprehensive about the risks; these tools streamline the process of third-party risk management.































































































































































































































































































































































































































































































































0 Comments