VAPT: What is it?
Vulnerability assessment and penetration testing (VAPT) are security methods that discover and address potential flaws in a system. VAPT audit ensures comprehensive cybersecurity by combining vulnerability assessment (identifying flaws) with penetration testing (exploiting flaws to determine security strength).
It is the process of identifying and exploiting all potential vulnerabilities in your infrastructure, ultimately reducing them. VAPT is carried out by security specialists who specialize in offensive exploitation. In a nutshell, VAPT is a proactive “hacking” activity where you compromise your infrastructure before hackers arrive to search for weaknesses.
To find possible vulnerabilities, a VAPT audit’s VA (Vulnerability Assessment) uses various automated technologies and security engineers. VA is followed by a penetration test (PT), in which vulnerabilities discovered during the VA process are exploited by simulating a real-world attack. Indeed, were you aware? A new estimate claims that with 5.3 million compromised accounts, India came in fifth place worldwide for data breaches in 2023.
Why is the VAPT Audit Necessary?
The following factors, which are explained below, make vulnerability assessment and penetration testing, or VAPT, necessary:
1. By Implementing Thorough Assessment:
VAPT provides an in-depth approach that pairs vulnerability audits with pentests, which not only discover weak links in your systems but also replicate actual attacks to figure out their potential, its impact, and routes of attack.
2. Make Security Your Top Priority:
Frequent VAPT reports might be an effective way to enhance security procedures in the software development life cycle. During the evaluation and production stages, vulnerabilities can be found and fixed by developers prior to the release. This enables organizations to implement a security-first policy by effortlessly moving from DevOps to DevSecOps.
3. Boost the Safety Form:
By organizing VAPT audits frequently, companies can evaluate the state of your security over time. This lets them monitor progress, detect continuing errors, and estimate how well the safety measures are functioning.
4. Maintain Compliance with Security Guidelines:
Organizations must conduct routine security testing in order to comply with several rules and regulations. While pentest reports help with compliance assessments for SOC2, ISO 27001, CERT-IN, HIPAA, and other compliances, frequent vulnerability checks can assist in making sure businesses meet these standards.
5. Develop Stakeholder Trust:
A VAPT audit displays to all stakeholders the commitment to data safety by effectively finding and addressing issues. This increases confidence and belief in the capacity of your company to secure private data, especially with clients and suppliers.
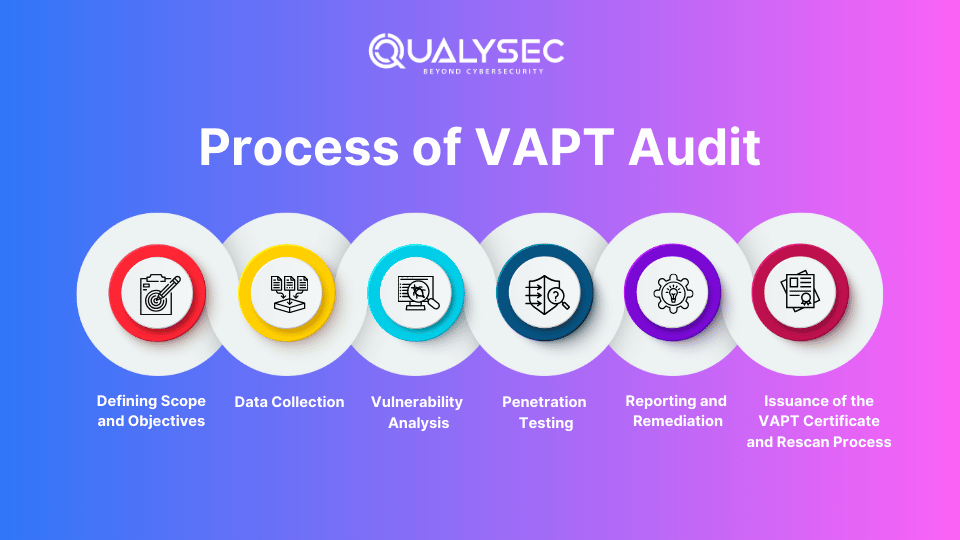
What Is the Procedure for VAPT Audit?
- Initial Stage: Defining and Programming
This phase establishes the VAPT’s aims, purposes, and limitations. It includes setting up ways to interact with your VAPT testing provider, defining important assets to be examined, and choosing the audit method and compliance standards. - Second Stage: Data Collection
Using readily available data along with approved methods, the team collects information about the selected systems, network setup, and potential flaws during this VAPT audit phase. When it comes to a grey box, they also begin mapping the target systems and collect information from consumers. - Third Stage: Evaluation of Vulnerabilities
At this point, vendors use automated devices and smart scanners to check the systems for identified vulnerabilities. This phase finds potential vulnerabilities in security processes, installation settings, and software. - Stage four: Testing for Penetration
Here, security experts try to use hacking techniques to take advantage of flaws that have been found. In order to evaluate the possible impact and efficacy of your security policies, this phase simulates actual attacks. - Stage five: Prevention & Reporting
Following exploitation, it offers a thorough VAPT report that includes information on the flaws found, the attempts at exploitation, and repair suggestions. This phase also entails developing a strategy to fix the weaknesses and improve the security posture as a whole. - Stage six: Issuance of the VAPT Certificate and Rescan
Once the vulnerabilities have been repaired, some penetration testing companies occasionally bid rescans to confirm the above, produce fresh reports, and problem widely certifiable VAPT certificate that enable compliance audits.
Download a VAPT report for free here!
Latest Penetration Testing Report

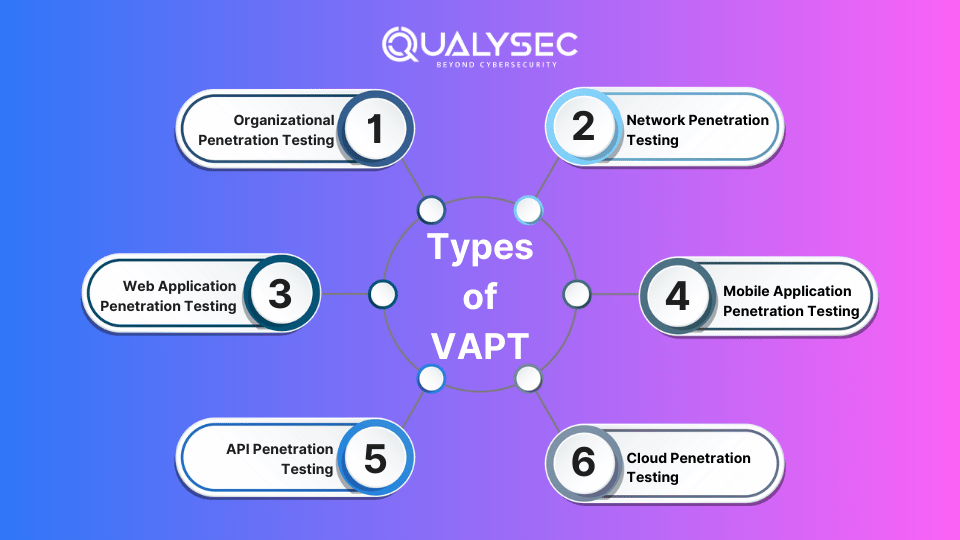
The Important Types of VAPT
1. Organizational penetration testing
Organization penetration testing is a comprehensive evaluation that replicates real-world attacks on an organization’s IT infrastructure, including the cloud, APIs, networks, web and mobile applications, and physical security. Pen testers often use a combination of vulnerability assessments, social engineering techniques, and exploit kits to uncover vulnerabilities and related attack vectors.
2. Network Penetration Testing
It employs ethical hacking methodologies to meticulously probe your network defenses for exploitable data storage and transfer vulnerabilities. Standard techniques include scanning, exploitation, fuzzing, and privilege escalation.
Adopting a phased approach, penetration testing experts map the network architecture, identify systems and services, and then leverage various automated tools and manual techniques to gain unauthorized access, mimicking real-world attacker behavior.
3. Penetration Testing for Web Applications
Web application pentesters use both automatic and human technologies to look for flaws in business logic, input verification, approval, and security.
To assist people with recognizing, prioritizing, and mitigating risks before attackers do so, skilled pentesters try to alter sessions, introduce malware (such as SQL injection or XSS), and take advantage of logical errors.
4. Testing for Mobile Penetration
Mobile penetration testing helps to improve the security of your application by identifying weaknesses in a mobile application’s code, APIs, and data storage through both static and dynamic evaluation.
Pentesters frequently focus on domains such as unsafe stored data (cleartext passwords), intercept personal information when in transit, exploit business logic faults, and gaps in inter-app contact or API integrations, among others, to find CVEs and zero days.
5. Testing API Penetration
In order to find vulnerabilities like invalid verification, injection errors, IDOR, and authorization issues, API vulnerability evaluation and penetration testing carefully build requests based on attacks in real life.
In order to automate attacks, fuzze data streams, and identify prone business logic flaws like payment gateway abuse, pentesters can use automated tools like Postman.
6. Penetration Testing for Clouds
Identifying threats in your cloud setups, APIs, data storage, and accessibility limits is the ultimate objective of cloud pentests and VAPT audits. It uses a variety of methods to search for zero-days and cloud-based CVEs, including automated tools with traditional testing. These commonly include SAST, DAST, API the fuzzing technique, server-less function exploitation, IAM, and cloud setup methods.
Our experts at Qualysec have helped secure fintech, SaaS, and enterprise systems across 25+ countries. Manual + Automated Pentesting. No false positives. Actionable reports.

How to Select the Best VAPT Provider for You?
1. Know What You Need
Understand the unique requirements of the business before looking into provider options. Consider the IT infrastructure’s scale and degree of complexity, industrial rules, timeline, cost, and aimed range of the VAPT.
2. Look for Methodological Depth
To ensure a thorough evaluation, look for VAPT providers who use well-known techniques like the OWASP Testing Guide (OTG) or PTES (Penetration Testing Execution Standard). Ask them about their testing procedures and how they are customized to meet your particular requirements.
3. Make open and transparent communication a priority
Select a provider who encourages honest and open communication throughout the VAPT procedure, as these tests can take ten to fifteen business days.
In order to reduce obstacles and improve the effectiveness of the VAPT cycle, companies should give customers regular progress reports, clear clarification of findings, and a joint remedial method.
4. Look Past Cost
Although price is a crucial consideration, seek out VAPT providers who deliver quality in terms of return on investment (ROI) above the appraisal. Assess the depth of the reports, any customized measures, post-assessment support, remedial suggestions, and reconfirmation options. People having a track record of success in VAPT, particularly in the business and resource categories, must be granted preference. Having three or more years of expertise in a specific application type and certifications like OSCP can also be beneficial.
How Can Qualysec Help with Your VAPT Audit?
Qualysec is a reliable cybersecurity firm that provides excellent VAPT audits and a variety of vulnerability assessment options. To examine and evaluate the major weaknesses in your IT environment, the organization uses advanced tools and procedures. Qualysec assists enterprises in recognizing, preventing, and appropriately managing risks by concentrating on network and application security. Whether you require sporadic vulnerability assessments or targeted security solutions, Qualysec’s team is ready to protect your valuables.
Qualysec also provides a complete range of other services, such as:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- Blockchain Pentesting
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
VAPT Certifications and Career Opportunities
For cybersecurity professionals, a job in VAPT offers interesting options. Penetration testing, security analysis, consulting, and security engineering are some of the most popular job choices. There are a number of VAPT certificates available because all the jobs are based on the same foundation; however, some of the most well-liked ones are as follows:
- Ethical Hacker Certified (CEH)
- Certified Professional in Offensive Security (OSCP)
- Professional Certification in Information Systems Security (CISSP)
A degree offers a good starting point, but practical experience is essential. Engage in labs or your own endeavors to develop your VAPT understanding and acquire useful skills.
Conclusion
Nowadays, the question is not whether to do a VAPT audit, but rather which VAPT is perfect for your company considering the present state of cybercrime. A thorough VAPT audit with continuous scanning not only improves your security posture but also fosters a security-first mindset, year-round compliance, and increased consumer trust. Choose a VAPT service provider who goes above and beyond the call of duty. Consider their methods, scanning capabilities, VAPT experience in your business, and team’s level of specialization.
FAQ
1. What is the difference between the VAPT and Pentest?
A more thorough security assessment is provided by VAPT (Vulnerability Assessment and Penetration Testing), which combines vulnerability scanning and manual pentesting. Pentesting is only concerned with mimicking attacks to take advantage of weaknesses.
2. What is the cost of a VAPT?
VAPT typically costs between $500 and $50,000 or more. Pricing frequently fluctuates depending on your needs, the services offered, the level of investigation, and the various VAPT businesses.
3. How does VAPT relate to cyber security?
The methodical process of vulnerability assessment and penetration testing (VAPT) in cyber security aims to strengthen your company’s security posture by locating, ranking, and addressing common vulnerabilities (CVEs) in its IT structures, such as XSS bugs, SQL injections, and misconfiguration.
4. Why is VAPT important?
To detect and reduce security threats, VAPT is needed. It thoroughly assesses a system’s risks, protecting businesses in securing their IT systems and data against possible cyberattacks by revealing hidden vulnerabilities that standard security methods could miss. As a result, it ensures a more stable and safe web experience.
































































































































































































































































































































































































































































































































0 Comments