SaaS (Software as a Service) are changing how businesses operate in this digital era. SaaS products save organizations from purchasing servers and other digital infrastructure, which is why its security is inevitable. SaaS security services protect these applications from unauthorized access, data breaches, and other cyber threats, all while maintaining the integrity and confidentiality of sensitive data.
A recent SaaS risk report reveals that in an average SaaS company, $28 million worth of data is at risk. Another survey says that 81% of organizations found vulnerabilities in their sensitive SaaS data and needed enhanced security measures.
SaaS applications contain a huge amount of sensitive data. They can be accessed by a mass of users from almost any device, posing a high risk to the privacy of sensitive information. In this blog, we will discuss the importance of SaaS security, the challenges faced, and its best practices.
What is SaaS Security?
SaaS security refers to managing, monitoring, and safeguarding sensitive data present in SaaS applications from evolving cyber threats. SaaS products have become very popular due to the flexibility, affordability, and scalability they offer. However, with great features come great risks. SaaS providers and their customers are now facing a variety of security challenges for which they need proper security measures.
Many regulatory bodies worldwide have mandatory security guidelines such as GDPR, EU-US, etc. Each SaaS business must comply with these guidelines to avoid penalties and offer secure services. Whether you are just starting or adding a new aspect to your IT assets, SaaS security is and should be a top priority.
Why is SaaS Security Important?
With over 30,000 SaaS applications functioning globally, they are one of the major targets for cybercriminals. SaaS security is important for multiple reasons, such as:
- To protect sensitive data from being compromised by hackers or cyber threats.
- To avoid legal penalties, reputation damage, and loss of customers.
- To increase the trust of the SaaS provider.
- To comply with necessary security standards and regulations.
- To enhance the overall security of SaaS platforms.
The Configuration of SaaS Security
Organizations that offer cloud-based services can use preventive measures like SaaS security posture management to continuously monitor and protect sensitive data. From a bird’s eye view, an ideal SaaS product technology stack looks like a three-layer cake, each part representing different environments.
These three layers of SaaS security are:
- Infrastructure (server-side)
- Network (the internet)
- Application and Software (client-side)
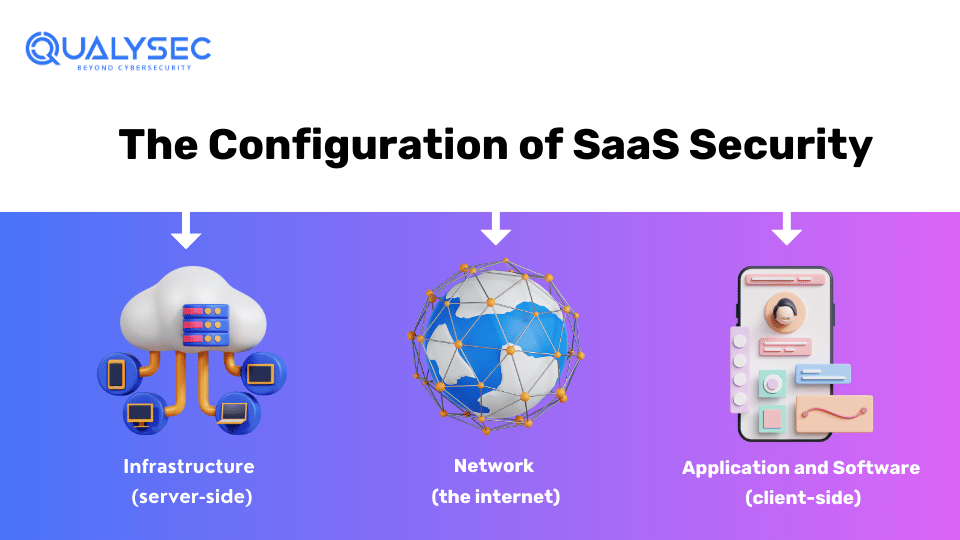
Infrastructure
The infrastructure or the server side of the technology stack of SaaS security handles the internal exchange of information. For example, if your SaaS business uses AWS (Amazon Web Services), you must secure all the data exchange between AWS and your software.
Every action initiated from the client side starts at this level. Also, depending on the storage type you purchase, be it shared, dedicated, or individual server), you need to enhance your SaaS security measures accordingly.
Network
The exchange of data and information between the server side and the client travels through the internet. This is probably the most vulnerable layer for every SaaS business. Through weak encryptions of data packets, hackers can easily find backdoors to sneak inside.
The effectiveness of SaaS security depends on how well data encryption is implemented and the ability to monitor internet exchanges in real time. With digital payments and online KYCs becoming more common, businesses are constantly exchanging sensitive information. Therefore, it is essential to have strong network security measures in place.
Application and Software
Application and software are the third and final layer of SaaS security. A single data breach in this layer can result in the loss of a lot of users. So, it’s crucial to have impenetrable SaaS security measures to protect user data.
The third-party applications and software that are being used need to be constantly monitored. Also, as the client-side environment can be very unpredictable, it demands higher security measures than usual.
5 Ways to Protect Sensitive Data in SaaS Applications
In every market, companies need to evolve and add new features or tools to their SaaS products. Whether you are fixing bugs or adding new features, it is essential to have security measures for these changes. Let’s look at the best SaaS security practices you can follow to protect sensitive data.
1. Strong Data Encryption
Data encryption keeps every piece of information safe from constant cyberattacks. Whether it is internal communication or customer service conversations, data must be encrypted. Here are a few types of encryptions on your SaaS product to keep data secure:
- Data Encryption Standard (DES)
- TripleDES
- RSA
- Advanced Encryption Standard
- TwoFish
These encryption methods enhance the security of your SaaS products with their secure algorithms made by experts in data encryption.
2. Use Multiple Locations to Back Up User Data
It is essential to manage customer data to offer satisfactory services. By backing up user data in several locations such as disaster recovery, you can ensure if one system fails, it won’t compromise the entire infrastructure. Many cloud platforms provide backup features, but it’s important to back up regularly and on time.
3. Educate Users
Studies show that maximum cloud security failures happen due to customers. When bringing a new user on board, it is essential to educate them on keeping their data safe. Make sure your customers know how to operate your SaaS application or platform correctly. Careful customers can make an added layer of security for your organization.
4. Use Strong Passwords
From email to banking, the safety of the digital world is all about passwords. But to easily remember, users are keeping weak passwords or using the same password repeatedly. Nowadays, hackers are becoming more intelligent at figuring out passwords using automated tools and public information available online. Hence, you must have strong password policies that are hard to crack.
5. Consult a SaaS Security Firm
If you have doubts, it is better to consult experts. Consult a good third-party SaaS security firm to employ experts in data encryption, software monitoring, and AI surveillance. You can use their expertise and advanced testing tools to build a secure SaaS platform. They can even help you during the unfortunate events of data breaches and cyberattacks.
Want an expert cybersecurity firm to help you discover the weaknesses present in your SaaS applications? Choose Qualysec for fast penetration testing services and strengthen your SaaS security. Contact now!
7 Risks Associated with SaaS Applications
Privacy advocates, such as information security experts and IT departments often raise concerns about purchasing and using SaaS applications. These concerns usually focus on privacy and cybersecurity. Here are seven potential risks associated with SaaS applications.

1. Access Management
Access management in SaaS applications is very crucial as they store sensitive data. SaaS users should check if a single access point in the public cloud can expose confidential information. It is also important to ask about the design of access controls and check if there are any risks to network security, like poor patching or lack of monitoring.
2. Misconfigurations
Many SaaS products add more layers to make their systems more complicated, increasing the chances of misconfigurations. Even a small mistake in configuration can affect the availability of the cloud infrastructure. So, it is essential to pay extra attention to the smallest of details while configuring SaaS applications.
3. Regulatory Compliance
Certain regulatory bodies need SaaS applications to comply with industry standards. When you are inquiring that your SaaS suppliers have strong endpoint security measures, you need to ask these questions:
- What are the relevant rules or laws that handle customer data and how are they determined?
- Do your SaaS or cloud applications comply with privacy, regulatory, and data protection requirements like HIPAA, GDPR, SOX, etc.?
- Are your cloud providers okay with external security audits to check how secure they are?
- Does your cloud service provider have security certifications like ITIL, ISO, etc.?
4. Data Storage
Before buying new software, it is important to check where all the data is stored. For SaaS users, here are some questions they can ask to check data storage policies:
- Does the SaaS provider allow you to have control over where the data is stored?
- Is the data stored either on a secure cloud service like AWS or Microsoft, or is it stored in a private data center?
- Are there security measures like data encryption available at every stage of data storage?
- Can users share files, objects, and data with other users both inside and outside of their domain?
5. Data Retention
Before you use a SaaS application, you need to check how long the SaaS environment retains sensitive data. In addition, it is better to check who owns the data available in the cloud: the SaaS application provider or the user. Make sure to ask about the data retention policy for the cloud, who sets it, and whether there are any exceptions to this.
6. Unexpected Disaster
Disasters can happen anytime and can significantly impact your business. You must ask these SaaS security questions to be prepared in the unfortunate event of a disaster.
- What happens to the cloud application and all the data stored during a natural disaster?
- Does your service agreement cover force majeure events?
- Does your service provider guarantee a complete restoration? If yes, then how long will it take what are the procedures?
7. Privacy and Data Breaches
Data breaches are common SaaS security threats that organizations face regularly. To know how well your service provider can deal with privacy and data breaches, ask these questions:
- What security measures does your cloud application provider take to prevent breaches? Are they prepared to handle cyberattacks like ransomware or malware?
- In case a breach occurs, how does your supplier detect it? Can they investigate and handle any illegal activity or intrusion? And does your contract allow you to hold them liable if the breach is caused by the negligence of the service provider?
Penetration testing helps SaaS providers know all the security flaws present in their applications. The testing reports will include all the vulnerabilities found in the current security measures and their remediation methods. Download a Sample Report to get an idea!
Solutions to Help Overcome These Security Risks
To tackle the security issues listed above, buyers should enhance their existing SaaS security and adapt to new ones as with the evolving SaaS environment. These SaaS security services can help overcome common security risks:
1. Risk Assessment
Practice risk assessment includes the following steps:
- Identify the right technology assets and data.
- Recognize where the data is stored.
- Understand how the data links to your business processes and other internal applications.
Regular security audits can help address any security risks identified.
If one of your SaaS applications poses a cyber risk, it can affect all other connected applications like falling dominoes. This is why it is important to address the risk of every SaaS application you use. You need to check everything from its risk setup to its compliance with necessary security standards and monitor access credentials for any suspicious behavior.
2. SaaS Security Awareness
It is essential to conduct security awareness campaigns in your organization to prevent security problems. If the SaaS users are not provided with proper awareness, they could unknowingly invite security threats, making them risk points.
Without formal awareness programs, your data could be exposed to various security risks like phishing scams, social engineering attacks, and accidental leaks. Instead of relying on the SaaS providers to offer security training sessions, your organization should take the lead in providing cloud security training. The basic training should cover important topics like data privacy and security risks.
3. Identity Access Management
Identity access management (IAM) involves three main aspects: authentication, authorization, and auditing. Authentication has evolved beyond traditional password-only authentication and now should involve multi-factor authentication, where users need to submit two or more pieces of evidence to prove their identity.
Organizations can also choose a single sign-on method if the users find multi-factor authentication too challenging. Single sign-on allows users to access multiple applications with a single set of credentials.
After authentication, users need to perform operations within the system. finally, auditing helps in reviewing authentication and authorization records to ensure the IAM functions work properly.
4. Third-Party Risk Management
Third-party risk management is a crucial part of your SaaS security service plan. If users are given unrestricted passes to connect any tool through APIs, it can lead to serious security problems. It is important to have processes to regulate API connections with SaaS products. Moreover, it is wise to offer API access to people who know how to perform necessary due diligence on third-party SaaS suppliers.
This is where you can use cloud access security brokers (CASBs). They can help you spot unauthorized SaaS products throughout your organization. You can use its insights to review those applications and decide whether to continue using them or find better alternatives.
5. Virtual Private Network/Virtual Private Cloud (VPN/VPC)
Virtual Private Network (VPN) and Virtual Private Cloud (VPC) in SaaS security services provide a safe environment for users to operate and store their data. These are better and safer options than multi-tenant systems. VPNs and VPCs allow users to log in and use SaaS applications from any location by securing endpoints and protecting the infrastructure.
Conclusion
Securing user data in SaaS applications is inevitable in this digital landscape. With the increase of cloud-based services, the importance of SaaS security has skyrocketed. Implementing strong SaaS security services can help keep data safe from hackers and cyber threats across three main layers: infrastructure, network, and applications. By following the best security practices like data encryption, strong password policies, and consulting SaaS security firms can strengthen your defenses.
SaaS security services are also important to comply with necessary security standards like HIPAA, SOX, GDPR, etc. With a range of security associated with SaaS applications like data breaches and misconfigurations, you need to have proper practices to address them. Overall, prioritizing SaaS security helps maintain trust and compliance, build reputation, and defend against evolving cyber threats.
FAQs
Q: Why is the security of SaaS applications important?
A: SaaS security refers to secure user privacy and data in SaaS applications. As they carry a huge amount of sensitive data, it can be accessed by mass users, thus posing a risk of leakage.
Q: How to keep data secure in SaaS applications?
A: You can protect sensitive data in SaaS applications by following these practices:
- Having strong data encryption
- Using multiple locations to back up user data
- By educating customers
- Using strong password policies
- Consulting a SaaS security firm
Q: What are the security issues in SaaS?
A: The top and most common security issues associated with SaaS applications are:
- Access management
- Misconfigurations
- Regulatory compliance
- Data storage
- Data retention
- Unexpected disaster
- Privacy and data breaches
Q: How to prevent unauthorized access in SaaS applications?
A: The best way to prevent unauthorized access in SaaS applications is to have multi-factor authentication. This is where users need to provide two or more pieces of information to prove their identity.
































































































































































































































































































































































































































































































































0 Comments