Penetration testing, also called pen testing, describes processes, tools, and services designed and implemented to simulate attacks and data breaches and find security vulnerabilities. You can run a pentest on a computer system, an entire network, or a web application.
The primary aim of a pentest is to identify vulnerabilities that attackers can exploit. There are various ways through which the identified vulnerabilities can be discovered. You can choose either manual pen tests, executed by a team of white hat hackers, or automated penetration testing, carried out by a software solution. Curious to learn more? Let’s dive in!
What are the Benefits of Penetration Testing?
Ideally, software and systems were designed to avoid hazardous security vulnerabilities in the design. A pen test shows how close it came to achieving that goal. Pen testing can help an organization in these ways:
- Find weaknesses in systems
- Determine the robustness of controls
- Support compliance with data privacy and security regulations (e.g., PCI DSS, HIPAA, GDPR)
- Provide qualitative and quantitative examples of the current security posture and budget priorities for management
Penetration Testing Process
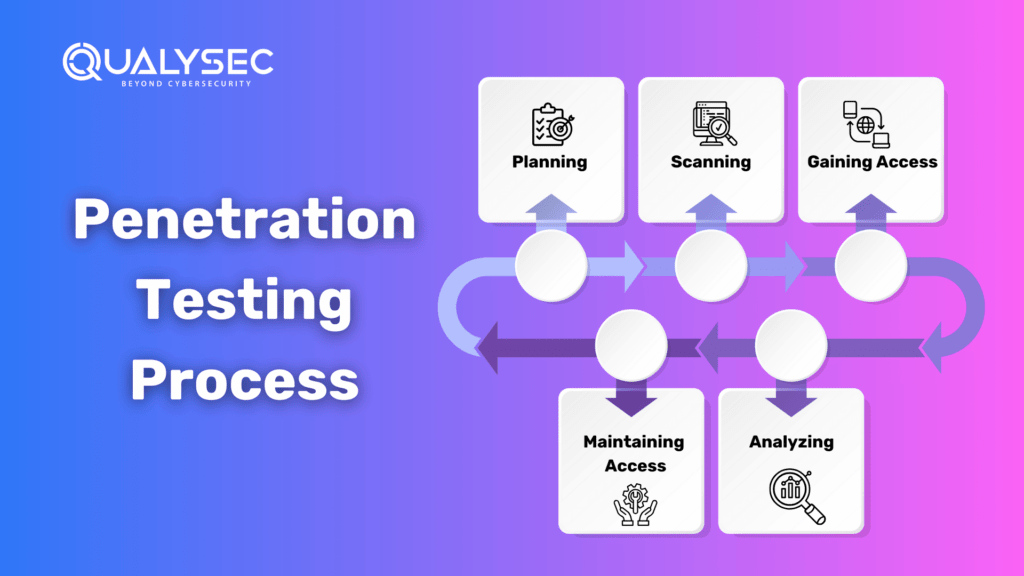
The penetration testing involves the following five fundamental stages:
- Planning: Identify and define the testing objective and scope. Collect intelligence information on the target, how the target works, and possible weaknesses.
- Scanning: Use the static and/or dynamic analysis of the network. This information allows the pentester to know how the application responds to various threats.
- Gaining Access: Identify the vulnerabilities in the target application using penetration testing techniques, such as cross-site scripting and SQL injection.
- Maintaining Access: Ascertain a criminal’s ability to retain access, owing to a vulnerability that has been exploited, and become privy to deeper forms of access.
- Analyzing: Assessing the penetration test’s results in a report describing vulnerabilities exploited, sensitive data accessed, and the timing of the response from the system during the penetration test.
Penetration Testing Methods
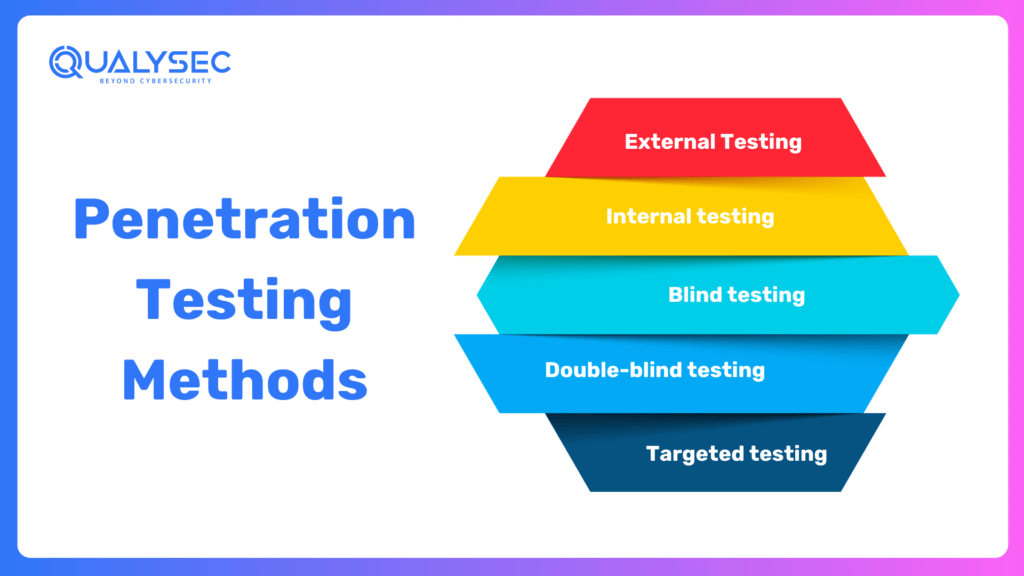
Let’s dive deeper into penetration testing methods that ethical hackers use to uncover vulnerabilities effectively.
1. External testing
External penetration tests target the assets of a company that is visible on the internet, for example, the web application itself, the company website and email, as well as domain name servers (DNS). The goal is to gain access to valuable data.
2. Internal testing
In an internal test, a tester who has access to the backside of an application behind its firewall simulates the attack of a malicious insider. This is not necessarily simulating a rogue employee. An ordinary starting scenario may be a worker whose ID and password were stolen because of a phishing attack.
3. Blind testing
In a blind test, only the name of the enterprise that is under attack is given to the tester. This provides security personnel with a real-time view of how an actual application assault would occur.
4. Double-blind testing
Security personnel do not know what kind of simulated attack will occur in a double-blind test. Just as in the real world, they would have no idea when their defenses were about to be tested before a breach attempt occurred.
5. Targeted testing
In this given condition, both the penetration tester and security personnel collaborate with each other and keep one another informed of their actions. It is very useful training in which a security team gets real-time feedback from a hacker’s point of view.
Penetration Testing Tools
Pen testers use a variety of tools to discover vulnerabilities. Some of the most popular tools are:
- Metasploit Framework: A broadly used platform for discovering and exploiting vulnerabilities
- Burp Suite: A tool for web application testing, including scanning and attack simulation
- Nmap (Network Mapper): Used to create network or system maps to discover vulnerabilities in connected systems
- Wireshark: Captures and analyzes network traffic to identify anomalies
- OWASP ZAP: A free, open-source tool focused on web application security
Latest Penetration Testing Report

Penetration Testing Use Cases
Penetration testing companies are using large and complex business-critical operations, as well as custom components. Some penetration tests are necessary when the software under development is to handle sensitive data or assets such as customer information, financial assets, and transaction data. Sensitive sectors like the government, medical, and financial services industries are under high regulation; they thus require strong security measures.
cybersecurity Suppose the recent infiltration provides your organization with a rather unpleasant experience. In that case, pen testing will offer powerful insight into the loopholes through which the breach was made, along with suggestions on mitigating them. In addition to the detected vulnerabilities, which were perhaps not yet exploited, this is also advantageous in preventing other future attacks.
Pen Test Challenges
Though extremely rewarding, penetration testing comes with certain challenges:
1. Limited Pool of Experts:
Trained and certified pen testers are high-demand specialists whose utilization can be challenging.
2. Constantly Evolving Threats:
Cybercriminals are ever devising new ways in which to implement their campaigns, making it difficult for the pen tests to keep up.
3. Cost and Time:
Conducting penetration testing typically takes time and financial resources and is a burden on small businesses.
Real-World Cases of Online Penetration Testing
Organizations resort to online penetration testing for large and complex business-critical operations; equally, for custom components, online penetration testing is aimed at developing software in situations involving the handling of sensitive data, extending from financial assets to customer information and transaction data. These sensitive clients include regulated industries such as government, healthcare, and financial services, and thus require state-of-the-art security measures.
If there was a breach in your organization, pen testing can help you examine the weaknesses that allowed the penetration and also provide suggestions on how to rectify those. Besides, you will find other vulnerable spots that were not exploited but still need to be secured to foil any future attempts of a breach.
Penetration Testing Services
automated penetration testingTwo types of penetration testing services include manual penetration tests and automated penetration tests.
Manual penetration is detailed, time-consuming, and mostly one of the oldest methods; it is always done by the outside contractor or security consultancy and always in agreement with the client on the scope of the testing engaged in. A certified ethical hacker, after an agreement with the contracted organization, attempts to seek internal and external weaknesses and tries to break into the organization’s computer systems within that testing scope and creates a report detailing the findings along with recommendations to fix the flaws found.
In Penetration Testing as a Service (PTaaS), the modern model combining automated frameworks seeking vulnerability testing across organizations is evolving. Thus testing with PTaaS software makes ease of access to the penetration testing-and it uses newer technologies like vulnerability scanning, dynamic application security testing (DAST), and fuzzing. PTaaS operates employing a mix of algorithms and technologies to allow super testing for finding security weaknesses and attempts to exploit them-without human assistance.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
How Frequently would you do the Pen Testing?
The frequency of penetration testing depends on your industry and its risk level. Generally, experts recommend:
- Annually: A minimum of once a year.
- After Significant Changes: Test after system upgrades or infrastructure changes.
- After significant incidents: Try to test your systems after a security breach to ensure all gaps are closed.
Conclusion
Penetration testing is a crucial element of cybersecurity companies. Simulating real-world attacks helps organizations build their defenses, regulate sensitive information, and establish trust with stakeholders alike. Whether one is a small startup or a multinational corporation, pen testing is an invaluable investment in the present digital economy.































































































































































































































































































































































































































































































































0 Comments