Dynamic Application Security Testing (DAST) is a process of application security in which testers examine web applications for vulnerabilities while it’s running. They simulate real attacks on the application to find weaknesses that real hackers could exploit for unauthorized access. This is a “black” box testing method in which the tester has no access or information about the application being tested.
Recently, it was exposed that 98% of web applications have vulnerabilities and are prone to cyberattacks. According to SiteLock, websites globally face approx. 94 attacks every day and are visited by bots approximately 2,608 times per week.
With cybercriminals looking for minute opportunities to steal your data, it is best to secure your applications regularly. This blog will help you learn more about dynamic application security testing (DAST), its importance, and its role in application security.
What is Dynamic Application Security Testing?
Dynamic application security testing (DAST) is the procedure of finding vulnerabilities in web applications during its production phase. It involves both automated and manual testing techniques to find weak points that hackers could exploit for their gain.
Since it is a black-box testing approach (with no info about the application’s code or infrastructure), the tester behaves like a real hacker to find where the security flaws lie. The testers test for common application and API vulnerabilities that could lead to cyberattacks.
The vulnerabilities that are found during the testing are documented, along with their impact level and remediation steps. This document helps organizations fix their security gaps and strengthen the overall security of the application.
Why is DAST Important?
If you test your application in the “development phase”, it will not protect the app from potential breaches during the “production phase”. Therefore, creating a diverse security program to mitigate overall security risks is essential. By performing DAST, you can detect critical security risks early in the software development life cycle (SDLC), allowing developers to address high-risk vulnerabilities quickly.
DAST solves many security challenges and:
-
- Delivers accurate vulnerability reports based on the application’s running state
- Helps developers in providing remediation steps to fix vulnerabilities
- Easily integrates security testing into the SDLC
- Improve your DevSecOps practices by using feedback from the security testing and integrating it into SecOps and DevOps tools.
- Protects applications and their source code effectively
Benefits of Conducting Dynamic Application Security Testing (DAST)
Dynamic Application Security Testing (DAST) offers a wide range of benefits when integrated with your organization’s security strategy. Here are some key advantages of conducting DAST:
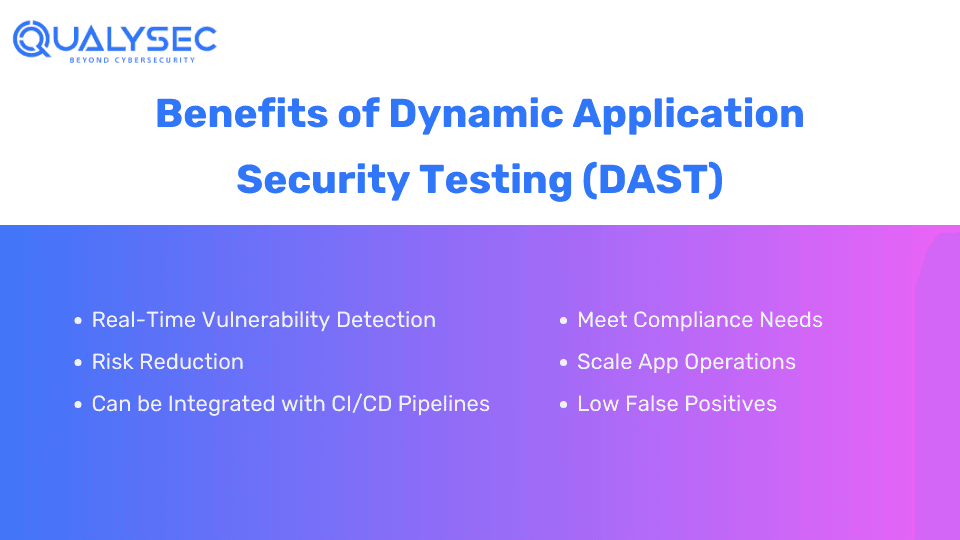
1. Real-Time Vulnerability Detection
Most web applications today have some form of vulnerability like security misconfigurations and outdated software. Dynamic application security testing (DAST) actively checks running web apps, detecting vulnerabilities in real time.
2. Risk Reduction
DAST lowers security risks by detecting vulnerabilities early in the SDLC. As a result, it prevents potential breaches and cyberattacks and enhances the overall security posture.
3. Integration with CI/CD Pipelines
DAST can seamlessly integrate into the development pipelines, including continuous integration and continuous delivery (CI/CD). Hence, it streamlines security checks throughout the development process.
4. Compliance
Implementing DAST in your security measures helps meet regulatory requirements and industry standards (for example GDPR, HIPAA, PCI DSS, and SOC 2). This prevents legal penalties and fines.
5. Scalability
Whether your applications are small or large-scale, DAST can adjust to your organization’s changing security needs. This helps keep your apps safe from evolving cyber threats.
6. Low False Positives
DAST is known for its low false positives. While other testing methods generate a lot of false results, DAST rarely generates incorrect reports of non-existent vulnerabilities.
Do you want to secure your applications from security risks? Contact us now for effective Dynamic Application Security Testing (DAST) services. We have expert cybersecurity professionals who can test your application for hidden vulnerabilities!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
How Does DAST Work?
DAST works by actively interacting with a web application while it is running to check for security problems. Here’s how it generally works:
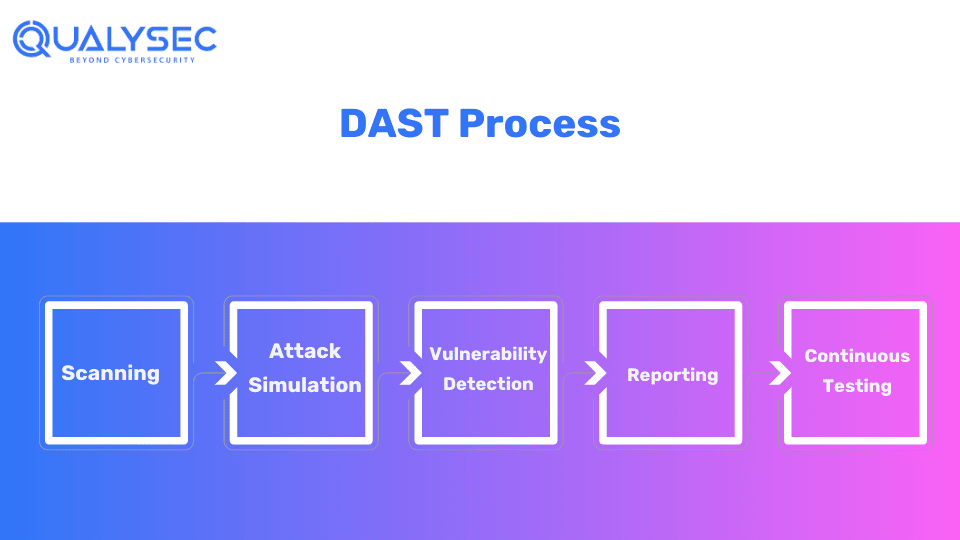
1. Scanning
DAST tools scan the target application to identify possible entry points and assess its overall security posture. This includes analyzing different components of the applications such as URLs, APIs, and forms.
2. Attack Simulation
In DAST, the testers act like real hackers and simulate real-world attacks on the application to find and exploit vulnerabilities. This includes testing common threats like XSS and CSRF.
3. Vulnerability Detection
After simulating real attacks, DAST analyses the response from the application to check if any security weakness has been exposed. If a vulnerability is detected, it will document its nature and the severity of its impact.
4. Reporting
After the testing is over, you will get a report of all the vulnerabilities detected, their impact level, and recommendations for remediation. Developers use this report to fix those vulnerabilities and organizations use this report for compliance needs.
5. Continuous Testing
DAST can be easily integrated into the software development life cycle (SDLC) to ensure security testing occurs regularly and consistently. Organizations can easily address vulnerabilities and enhance the overall security of their application by testing them throughout development and deployment.
Want to see a sample DAST report? Just click the link below and download one right now!
Latest Penetration Testing Report

Different Types of DAST
Many people consider DAST as an automated method, but it’s not. Dynamic application security testing is typically divided into 2 types
-
- Manual DAST
- Automated DAST
1. Manual DAST
Manual dynamic Application Security Testing (DAST) involves human testers analyzing the application to uncover vulnerabilities. While automated tools are quick, they are no match for the human mind.
Human testers, with their experience and knowledge, find vulnerabilities that automated scanners might miss. They explore different areas of the application, such as URLs and APIs, simulating real-world attacks to identify potential weaknesses.
2. Automated DAST
Automated dynamic application security testing (DAST) includes testing the application using specialized software for security vulnerabilities while they’re running. The software simulates real-world attacks by sending various requests to the application.
It helps identify weaknesses like cross-site scripting (XSS), SQL injection, and server-side request forgery. While they are good for routine checks, they might miss some complex or unique issues that require manual testing.
Different Types of Application Security Testing (AST)
Application security testing is a major part of DevSecOps, as it helps in finding security issues before the application is released to the market. There are mainly 4 types of Application Security Testing (AST):
1. Static Application Security Testing (SAST): It is a white box testing that analyzes source code or binaries while its components are at rest.
2. Dynamic Application Security Testing (DAST): As discussed above, DAST is a black-box testing process that shows how applications can be attacked from the outside.
3. Interactive Application Security Testing (IAST): It combines both the aspects of SAST and DAST. It provides real-time feedback on vulnerabilities and coding errors during application runtime.
4. Software Composition Analysis (SCA): SCA scans the code and analyzes third-party and open-source components in software applications. It checks for vulnerabilities and compliance licenses.
Difference Between SAST and DAST
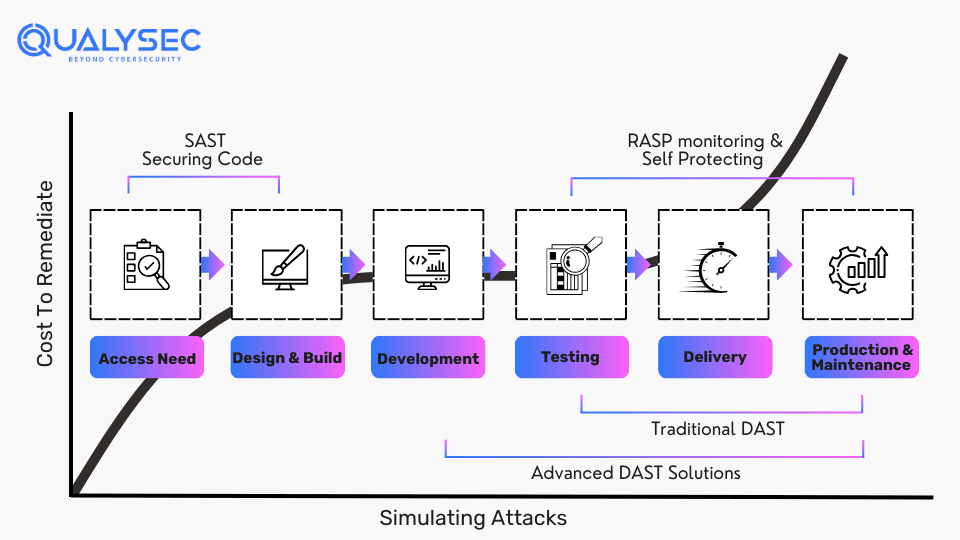
Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) are two common and essential methods for securing software applications.
Static Application Security Testing (SAST):
-
- Analyzes the source code or binaries of a software application without executing it.
- Identifies vulnerabilities by analyzing the code structure. It looks for coding errors and potential security weaknesses.
- Best suited for the early stages of app development
Dynamic Application Security Testing (DAST):
-
- Actively interacts with a running software application to identify vulnerabilities.
- Simulates real-world attacks by sending requests to the application. It aims to exploit weaknesses like XSS or CSRF.
- Well-suited for apps that are in production.
| Aspect | SAST | DAST |
| Method | Analyzes source code or binaries | Interacts with running applications |
| Execution | Does not execute the application | Actively interacts with the application |
| Vulnerability Identification | Identifies coding errors and weaknesses | Identifies vulnerabilities by simulating real attacks |
| Testing Stage | Early stages of development | Deployment and production environments |
| Suitability | Code quality and early vulnerability detection | Testing app behavior in real-world attack scenarios |
Conclusion
Dynamic Application Security Testing (DAST) is a critical process to ensure the security of web applications. It is an excellent way to deliver secure applications and avoid the risk of breaches. DAST offers developers a huge advantage by providing real-time feedback on security risks. By generating comprehensive vulnerability assessment reports, DAST helps organizations fix security issues and meet compliance needs.
While multiple open-source tools can help with application security testing, they are no match for human testers. At Qualysec, we test software applications for vulnerabilities and bugs in their running environment, along with proper steps to fix those issues. We follow both manual and automated DAST practices since we aim to provide a comprehensive result.
“Secure your web applications today! Contact us now! [email protected]”
FAQs
Q: What is a DAST in security?
A: Dynamic Application Security Testing (DAST) helps strengthen the security of software applications by finding vulnerabilities through simulated attacks. It analyses the application in its running environment and evaluates how it performs during a real cyberattack.
Q: What are DAST tools used for?
A: DAST tools provide how applications behave when they are in production. It helps businesses to address potential vulnerabilities before a hacker uses them to make an attack.
Q: How to do DAST testing?
A: For a running application, DAST scans can be automated on a schedule, in a CI/CD pipeline, or run independently by using the scanners anytime. Performing DAST during the SDLC helps the development team uncover vulnerabilities before their applications are in production.
Q: What are the benefits of DAST?
A: The key benefit of DAST is its ability to detect runtime issues in software applications by simulating real-world attacks. It offers precise vulnerability detection with very low false positives. Additionally, it helps with compliance requirements.






























































































































































































































































































































































































































































































































0 Comments