In the fast-paced digital world, the significance of cybersecurity cannot be overstated. Cyber threats are ever-evolving, and companies must prioritize their security measures to safeguard sensitive data and maintain customer trust. One crucial aspect of ensuring robust cybersecurity is conducting periodic security audits. In this article, we will explore how companies can effectively prepare for a cybersecurity audit to enhance their security posture.
Understanding the Importance of Cybersecurity Audit
Cybersecurity audits are comprehensive assessments that evaluate a company’s security measures, policies, and procedures. These audits help identify potential vulnerabilities and weaknesses, allowing businesses to proactively address security gaps before they can be exploited by malicious actors. A cybersecurity audit provides an objective view of the organization’s security posture, enabling management to make informed decisions to improve cybersecurity resilience.
The Role of the Cybersecurity Industry
The cybersecurity industry plays a pivotal role in assisting companies with security audits. Cybersecurity experts, such as penetration testers and auditors, bring their expertise to assess an organization’s security infrastructure, applications, and processes. Their impartial evaluation helps companies identify blind spots, weaknesses, and potential risks that might have been overlooked by internal teams.
The Basics of Penetration Testing
Penetration testing, or ethical hacking, is a controlled simulation of cyber-attacks aimed at identifying vulnerabilities in a company’s systems and networks. This process is an essential component of cybersecurity audits. During a penetration test, skilled professionals attempt to exploit security weaknesses, just as an actual attacker would. The findings provide valuable insights into the company’s security gaps and areas that require immediate attention.
Why Are Cybersecurity audits important?
Cybersecurity audits are essential in today’s threat landscape to assess and validate the effectiveness of an organization’s security controls. By evaluating security policies, procedures, and technologies, companies gain valuable insights into potential vulnerabilities and weaknesses that need to be addressed to maintain a strong security foundation. Discover the importance of security audits in safeguarding your business from cyber threats.
Importance of Cloud Penetration Testing
For companies utilizing cloud services, cloud penetration testing is crucial. It involves assessing cloud infrastructure, applications, and configurations to identify potential security weaknesses in the cloud environment. As cloud adoption increases, so do the risks associated with cloud security. Cloud penetration testing helps businesses ensure the safety of their cloud assets, data, and interactions with cloud service providers.
Steps to Prepare for a Cybersecurity Audit

Conduct a Security Risk Assessment
Start by conducting a comprehensive security risk assessment to identify potential threats and vulnerabilities. This evaluation will serve as a foundation for the subsequent security measures. The risk assessment should involve identifying critical assets, evaluating potential threats and impacts, and determining existing security controls.
Implement Robust Security Policies and Procedures
Develop and enforce comprehensive security policies and procedures that address specific risks and compliance requirements. These policies should cover data protection, access controls, incident response, and acceptable use of company resources.
Regularly Update Security Measures
Stay ahead of emerging cyber threats by regularly updating security measures, software, and security patches. This proactive approach ensures your systems are protected against the latest threats. Automated patch management systems can help streamline the process and ensure timely updates across the organization.
Perform Regular Penetration Testing
Regular penetration testing, including cloud penetration testing, helps identify and address vulnerabilities in your IT infrastructure and cloud environment. Engage professional ethical hackers to conduct controlled and authorized tests. Penetration tests should be performed at regular intervals and after significant changes to the IT infrastructure or cloud services.
Review Third-Party Security Practices
If your company relies on third-party vendors or cloud service providers, review their security practices to ensure they align with your security standards. Assess their compliance with relevant regulations and industry standards. Request security reports and certifications, and if necessary, conduct on-site visits to validate their security controls.
Develop an Incident Response Plan
Have a well-defined incident response plan in place to address security breaches promptly and effectively. Test the plan through simulated exercises to ensure its efficiency. The incident response plan should include clear roles and responsibilities, escalation procedures, communication protocols, and steps for containment, eradication, and recovery from security incidents.
How Often Does Cybersecurity Audit Need To Be Done?
- The frequency of security audits depends on factors like industry regulations, business size, and the evolving threat landscape.
- Regular security audits, including vulnerability assessments and penetration testing, should be conducted by businesses at least annually or after significant changes to their IT infrastructure or cloud services.
- High-risk industries or those handling sensitive data may need more frequent audits, such as quarterly or semi-annually, to ensure continuous security improvements.
Types Of Security Audits
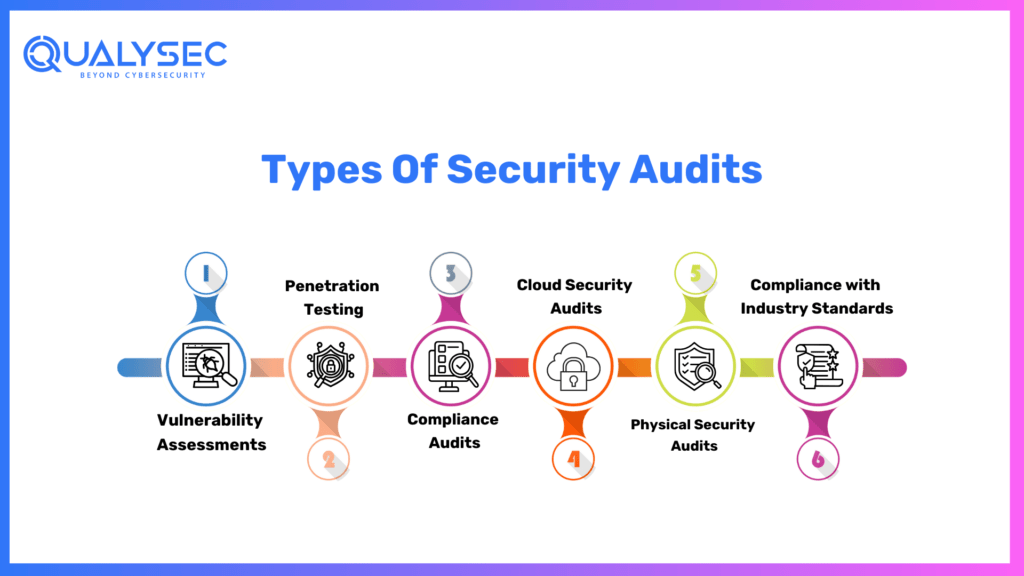
Vulnerability Assessments:
Vulnerability assessments identify and evaluate potential weaknesses in an organization’s systems, networks, and applications. These assessments help prioritize security vulnerabilities based on their severity, providing businesses with insights to implement effective security measures.
Penetration Testing:
Penetration testing, or ethical hacking, involves simulated cyber-attacks to test the security defenses of an organization. This type of audit allows companies to identify real-world vulnerabilities that malicious actors could exploit, enabling them to address these weaknesses before cyber incidents occur.
Compliance Audits:
Compliance audits assess an organization’s adherence to industry-specific regulations and standards. These audits are essential for companies operating in regulated industries such as healthcare, finance, and government, ensuring they meet legal requirements and protect sensitive data.
Cloud Security Audits:
Cloud security audits evaluate the security measures of cloud-based systems and applications. With the increasing adoption of cloud services, these audits help companies ensure the security of their data and interactions with cloud service providers.
Physical Security Audits:
Physical security audits assess the physical access controls and measures in place to protect an organization’s premises, assets, and critical infrastructure. This type of audit is crucial for safeguarding the physical security of employees, data centers, and sensitive information.
Compliance with Industry Standards
Cybersecurity audit also focus on ensuring compliance with industry-specific regulations and standards. Companies operating in healthcare, finance, or government sectors must adhere to strict security requirements. A cyber security audit helps verify that the organization meets these standards and safeguards sensitive data in line with relevant regulations.
A Safer Tomorrow: Qulaysec’s Proven Cybersecurity Audits
Qualysec, A Cybersecurity company founded in 2020 is a leading cybersecurity provider. Qulaysec is also known for its renowned cutting-edge technology and expertise in cybersecurity assessments. With a team of skilled professionals, Qulaysec offers a comprehensive range of services, including various vulnerability assessments and penetration testing.
What sets Qulaysec apart is its commitment to staying ahead of the curve in terms of emerging threats and advanced hacking techniques. They employ state-of-the-art tools and methodologies to ensure thorough and accurate assessments. Qulaysec’s team of experienced professionals brings a wealth of knowledge and a human touch to their engagements. This in turn helps foster collaboration and deliver actionable insights.
Technicians at Qualysec can detect flaws that fraudsters could abuse. After these flaws have been found, Qualysec collaborates with the organization to establish a plan to address them and boost the company’s overall security posture. Among the several services available are:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI /ML Pen-testing
Hence, choose Qualysec for comprehensive and reliable cloud penetration testing. Also, their penetration testing guide will help you make informed decisions and understand the various factors that impact the cost. Hence, protect your assets and enhance your security posture by choosing us.
Key Features
- Over 3,000 tests to detect and root out all types of vulnerabilities.
- Capable of detecting business logic errors and gaps in security.
- Ensures zero false positives through manual pen testing.
- Compliance-specific scans for SOC2, HIPAA, ISO27001, and other relevant standards.
- Provides in-call remediation assistance from security experts
Conclusion
Preparing your company for a cybersecurity audit is an essential step in fortifying your organization’s security posture. By understanding the significance of cybersecurity audits, leveraging the expertise of the cybersecurity industry, and adopting proactive security measures like penetration testing and cloud security assessments, your company can stay one step ahead of cyber threats. Prioritizing cybersecurity safeguards your sensitive data, preserves customer trust, and positions your company as a reliable and secure partner in today’s digital landscape.
Qualysec has a successful track record of serving clients and providing cybersecurity audit across a range of industries such as IT. Their expertise has helped clients identify and mitigate vulnerabilities, prevent data breaches, and improve their overall security posture.
When it comes to comprehensive cloud penetration testing, Qualysec is the organization to go with. Their cost of VAPT guide helps clients make informed decisions by understanding the various factors that affect the cost by clicking here.































































































































































































































































































































































































































































































































0 Comments