Common threats cloud application security should counter are code injections, supply chain attacks, session hijacking, ensuring uptime, protecting users, and data theft. The security of an Application is ensured by deploying several security measures and tools to protect applications in the software life cycle right from design, testing, deployment, and so on.
Cloud application security is different from securing on-premises applications, coming with challenges beyond that of traditional application security.
Cloud environments are well distributed and the cloud provider normally maintains and secures the underlying infrastructure. In fact, cloud environments are well distributed and shared by nature, and cloud provider normally maintains and secure the underlying infrastructure.
Security challenges for teams developing and operating cloud-native applications will include access and authorization across multiple devices and users, misconfiguration of cloud resources, securing previously unsecured cloud data in transit, and more.
Cloud Application Security: Importance and Benefits
Cloud application security is significant because it protects sensitive data and applications from cyber threats that could lead to breaches, loss of data, and other negative consequences. With the fact that more and more organizations are moving their data and applications to the cloud, such assets must be secured.
The benefits of cloud application security include:
- Increased protection: Offers of cloud app security include measures such as encryption, IAM, and network security to avoid cyber attacks and access to sensitive data.
- Compliance: Widespread compliance needs are imposed by HIPAA, SOC 2, and PCI DSS on the industries and organizations, and because of this. Through cloud app security organizations can meet needs and avoid fines and costs.
- Improved performance: The reduction of risks of breaches causes slowdowns and even outages, and cloud application security measures can help cloud application efficiency.
- Cost reduction: By taking security measures on cloud apps, they can reduce data breaches as well as other cybersecurity-related incidents in order to save them from losing large sums of money through lost revenue, damaged reputation, and recovery processes.
Cloud app security solutions provide better insights into organizations’ cloud environments and how their security risks are being projected.
9 Cloud Application Security Threats
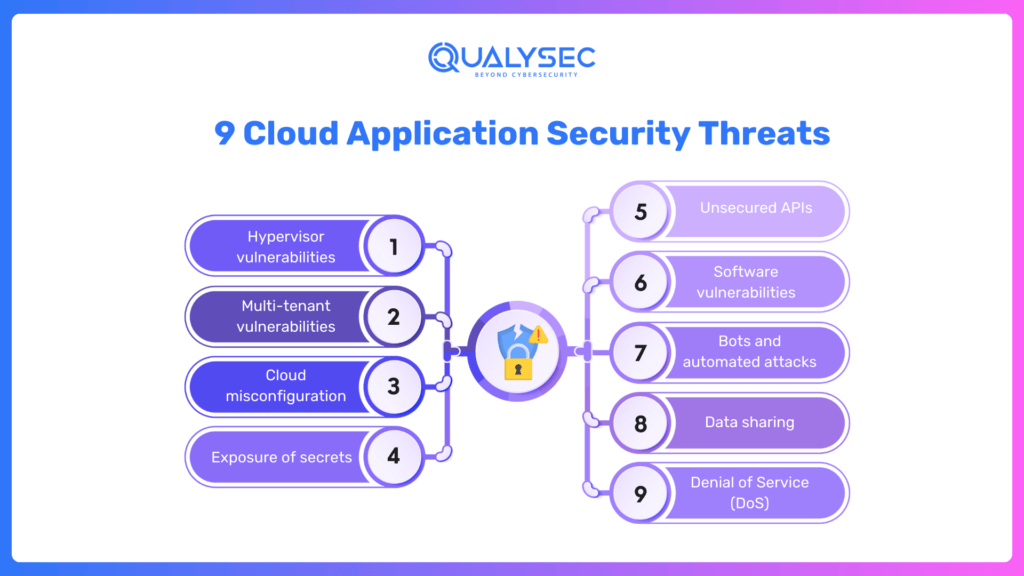
Some of the key threats to cloud-based applications are as follows:
- Hypervisor vulnerabilities: the infrastructure used by the cloud provider could have vulnerabilities, which may be highly severe because of the central role hypervisors play in cloud systems. The cloud providers frequently scan hypervisor code, fuzz test hypervisors, and closely monitor hypervisor logs to prevent exploitation.
- Multi-tenant vulnerabilities- cloud infrastructure shares hardware and software resources between multiple “tenants”. Weaknesses in the network might exist that could be bridged by an attacker upon compromising one tenant’s cloud environment to laterally access another tenant’s. Imperfect logical isolation between tenants.
- Cloud misconfiguration – configuration errors, oversights, or intentional misconfiguration performed by malicious insiders can pose risks to cloud-based systems. Applications, cloud resources such as compute instances or storage buckets, and supporting systems such as access controls, secrets management, network policies, and data encryption are all vulnerable to misconfiguration.
- Exposure of secrets – applications, scripts, automated tools, and other machine identities often rely on privileged credentials called “secrets”, such as passwords, certificates, API keys, and SSH keys. Once secrets are exposed, attackers or unauthorized users can gain access to protected services and resources.
- Unsecured APIs pose a significant threat within cloud environments, where APIs facilitate extensive automation of both infrastructure and application processes. The exposure of these unsecured APIs to public networks creates a substantial risk, as they can be exploited by attackers to disable resources, deactivate security measures such as encryption, and provide unauthorized access to sensitive information.
- Software vulnerabilities – modern software applications can have thousands of components and dependencies, many of them open source. Software with untested components may contain severe vulnerabilities that can be exploited by attackers. Supply chains could also contain zero-day vulnerabilities that are not yet known to security researchers and software vendors.
- Bots and automated attacks – the threat actors use bots and automated scanners to perform a range of malicious activities, from scanning for known vulnerabilities in exposed services and cracking passwords to launching massive attacks attempting to shut down entire systems. Automated attacks often target cloud services and web-facing applications.
- Data sharing – cloud apps make data easy to share using URLs. This feature helps streamline enterprise collaboration but exposes digital assets to greater risks and the chance of unauthorized or malicious users accessing this data.
- Denial of Service (DoS) attacks involve a method whereby malicious actors inundate a website, cloud application, or an entire network with excessive service requests. Consequently, the affected application may experience significant slowdowns or may become completely inoperable. It has been observed that attackers frequently target not only specific applications but also public cloud services.
What Cloud Application Security Options Are Available?
Here are some of the cloud application security options available:
1. Cloud Access Security Broker (CASB)
The disadvantage of going for the cloud services option is that you cannot have access to all infrastructure layers. You, therefore are not privileged to see or get control of all your assets at any time. A software component CASB that operates as an enforcer solves this problem.
CASBs position themselves between the infrastructure of a cloud vendor and a cloud consumer and enforce access and data permission policies. You can install CASBs either in the cloud or on-premises or even both while enforcing multiple types of policies.
For instance, you can enforce security policies including authorization and authentication, encryption and tokenization, logging and credential mapping as well as malware detection and prevention.
2. Cloud Workload Protection Platform (CWPP)
Most organizations use at least some cloud resources and often use a mix of on-premises and cloud resources. But most organizations are also avoiding vendor lock-in and managing costs by using more than one cloud offering, ending up in hybrid or multi-cloud environments.
Cloud Workload Protection Platforms (CWPPs) allow complex cloud environments to be better protected through consistent security and management of workloads across clouds. These tools typically centralize management and define security policies, maintain visibility across environments, and may include extended security controls. Capabilities that are commonly provided by CWPP systems include system integrity monitoring, vulnerability management, system hardening, and host-based segmentation.
3. Cloud Security Posture Management (CSPM)
Organizations need to have consolidated visibility and be able to enforce consistent security and compliance controls to protect multi-cloud Infrastructure as a Service (IaaS) environments, especially cloud-hosted Kubernetes for containerized applications. CSPM solutions help organizations by scanning the cloud configuration settings and access controls and continuously monitoring these settings and controls for cloud security risks.
A CSPM can track, monitor, and log cloud-related problems like cloud service configurations, security settings, compliance, and cloud governance. Moreover, capabilities include monitoring and analytics, inventory and asset classification, cost management, and resource organization.
4. Cloud Infrastructure Entitlement Management CIEM
A new category, CIEM was announced by Gartner on the 2020 Cloud Security Hype Cycle. CIEM solutions support the implementation, enforcement of, and best practices for identity and access management tools from providers across cloud providers, a system that is becoming increasingly complex and dynamic.
CIEM solutions offer organizations identity and access governance controls, which are created to reduce excessive cloud infrastructure entitlement and enforce least privilege access controls. They also can streamline controls for least-privileged access implemented across dynamic and distributed cloud environments.
Cloud Application Security Best Practices
1. Discover and Asses Cloud Apps
Every application or workload you are running on the cloud increases its attack surface. It might look like any one of these applications provides an opening point for attackers, so keep track of each and every one of them deployed by your organization.
Once you have a list of cloud applications, assess them by identifying their security features and known vulnerabilities, comparing them to compliance requirements and your security policies, and prioritizing and remediating issues. Repeat this process for new applications deployed in the cloud.
2. Implement and Benchmark a Cloud Security Framework
Cloud security frameworks give organizations an understanding of best practices and practical suggestions that would guide organizations as they strive to deal with security risks in the cloud. For instance, The Center for Internet Security delivers security benchmarks that come along with detailed best practices by most major cloud providers like Amazon Web Services, Microsoft Azure, Google Cloud Platform, IBM Cloud, Oracle Cloud Infrastructure, and Alibaba Cloud.
3. Cloud Security Architecture
You can design a cloud security architecture that outlines your security configurations, policies, and privileges to ensure that your infrastructure is secure. Ideally, this design should be done before migrating to the cloud, and it should encompass all aspects, including development, operations, deployment, and upgrades.
Your cloud security architecture should cover several major aspects of the infrastructure, namely identity and access management, data protection, monitoring and visibility, threat detection, cloud governance, compliance with the relevant regulations, and security measures placed for the physical components of the infrastructure.
Robust Cloud Application Security with Qualysec
If your business uses cloud-based applications, the idea of a cloud app security program should already top your head. Whether your group just recently started protecting cloud data and applications or has an existing strategy for cloud app security, knowing that your information is safely protected is of utmost importance to building a secure working environment.
Such solutions are a great start at leveraging the right processes and policies, but it’s what’s needed to prevent such data exfiltration as well as loss in a multiple cloud environment with different forms of cloud applications.
90% of companies have implemented DLP, CASB, UEBA, or IRM solutions to help protect against insiders exfiltrating data. Consolidate your data protection for cloud applications with Qualysec. Qualysec offers an intelligent data protection solution that automatically detects data leaks to untrusted cloud apps, blocks unacceptable exfiltrations, and tailors security’s response based on the offender and the offense. Secure your cloud applications with Qualysec’s cutting-edge solutions.
Frequently Asked Questions (FAQ)
Q1: What is the shared responsibility model?
In cloud app security, responsibility sharing between the cloud service provider and the customer exists. The provider must secure the underlying infrastructure, while the customer’s responsibility lies in securing applications, data, and user access. The exact split depends on the cloud service model implemented: IaaS, PaaS, or SaaS.
Q2: What is the difference between cloud security vs. application security?
Cloud security deals with the security of data, applications, and infrastructure in a cloud computing environment, addressing special challenges like shared responsibility and multi-tenancy. Cloud application security specifically targets software applications’ security, independent of where they are hosted, by identifying and remediating vulnerabilities and risks in the application’s code, design, and runtime environment. Both are important for any robust cybersecurity posture, particularly in cloud environments where the applications and data are hosted from remote locations.
Q3: What is the public cloud?
A model in which providers make computing services like storage, development and deployment environments, and applications available to the public over the internet for public access both by the people and the organizations to get on-demand computing services in the IT industry. They are useful for cloud-based applications that need resources on demand.






























































































































































































































































































































































































































































































































0 Comments