In today’s digital world data breaches have become essential. With the growing need to protect users’ data from cyber threats, firms now need to conduct penetration testing using penetration testing tools to protect their data and maintain trust. Penetration testing involves ethical hackers simulating attacks on a computer network to find vulnerabilities.
This process is essential but, it is important to conduct the assessment using a proper penetration testing tool that suits the firm’s security framework. This blog highlights the best penetration testing tools pros use while conducting penetration testing.
What Is Penetration Testing?
Penetration testing is a testing process involving ethical hackers, who manually try to find vulnerabilities that can potentially harm the applications or network of the businesses. The testers use the best penetration testing tools and their hacking expertise to identify system vulnerabilities. This also ensures that the security posture is strong and responds when a simulated attack is performed. If ethical hackers bypass the security barrier, they identify a security flaw. At the end of the test, the testers generate a report that includes all the flaws found, along with their remediation methods.
Penetration testing services are important for businesses, especially for small businesses as their security system is often weak. A cyberattack can hamper the entire operation of the business. Data breaches can lead to the loss of personal information stored on the business’s systems and reputational damage.
Do you want to see a penetration testing report? Click the link below and check how the details of a pentest report can help with your business’s success!
Latest Penetration Testing Report

How Penetration Tests Work?
During penetration testing, the testers simulate an attack on the computer network and the security posture to find flaws and vulnerabilities. While performing this test, the pen testers follow various steps necessary for successfully conducting a penetration test. These steps include:
| Step | Description |
|---|---|
| Planning and Reconnaissance | Define scope and goals, gather information about target systems. |
| Scanning | Perform static and dynamic analysis to identify potential vulnerabilities. |
| Gaining Access | Exploit identified vulnerabilities to gain unauthorized access using techniques like SQL injection and XSS. |
| Maintaining Access | Ensure ongoing access and escalate privileges to understand the impact of prolonged attacks. |
| Analysis and Reporting | Document findings, assess impact, and provide remediation recommendations. |
| Remediation and Retesting | Implement fixes, then retest to ensure vulnerabilities are resolved and no new issues exist. |
| LOA and Security Certificate | The testing company finally issues a letter of attestation (LOA) and a security certificate for the partners and stakeholders o the company. |
Key Factors To Consider When Choosing PenTesting Tools
Choosing the best penetration testing tools for the right framework is important. There are various tools available which offer various services that one might need and one might not need. Here are some factors that need to be considered before choosing a penetration testing tool:
1. Scope and Coverage
It is always necessary to ensure the tool that has been chosen needs to covers the types of systems and vulnerabilities relevant to the firm’s environment and requirements.
2. Ease of Use
It is also important that the tool being used is easy to use has a simple interface and is efficient. The tools also need to provide easy documentation of the vulnerabilities.
3. Accuracy
While choosing tools, it is important to choose one with high accuracy. A high accuracy can be determined by checking whether the tool provides low false-positive and false-negative rates. This ensures reliable results.
4. Customization
A tool needs to be easily customizable as it could be used for testing specific needs and scenarios.
5. Integration
It is important for the firm as well as for the tester to ensure that the tool can be integrated with the needs of the existing security framework.
6. Reporting
Reporting is essential for any penetration test. Selecting a tool that provides comprehensive, clear, and actionable reports for remediation efforts is essential.
7. Cost
Considering all the above factors is important, but the ultimate focus should be on the investment and cost of the tool being chosen. It is advisable to evaluate the tool’s cost against the budget and its capabilities.
8. Support and Updates
While choosing a tool it is important to ensure that the tool has strong vendor support and regular updates to keep up with evolving threats.
9. Scalability
It is always recommended to choose tools that can grow with the firm’s requirements.
Types of Penetration Tests
When choosing penetration testing for businesses or firms, it is important to choose which type of penetration test is suitable and effective. Various firms have different requirements, so here are the various penetration tests that a firm can choose from:
| Type of Penetration Testing | Description |
|---|---|
| Application Penetration Testing | Tests web apps, mobile apps, and other software for vulnerabilities like SQL injection and XSS. |
| Network Penetration Testing | Tests company networks and devices by exploiting weaknesses in firewalls, VPNs, and network devices. |
| Cloud Penetration Testing | Evaluates the security of cloud services, infrastructure, and configurations to identify vulnerabilities. |
| API Penetration Testing | Tests the security of APIs by simulating attacks on authentication, data exposure, and misconfigurations. |
| IoT Penetration Testing | Identifies vulnerabilities in IoT devices, communication protocols, and associated apps/interfaces. |
Qualysec has a good history of helping clients and giving cybersecurity services in many industries like IT. Their skills have helped clients find and fix vulnerabilities, stop data breaches, and make their overall security better. Choose Qualysec to secure your business today!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
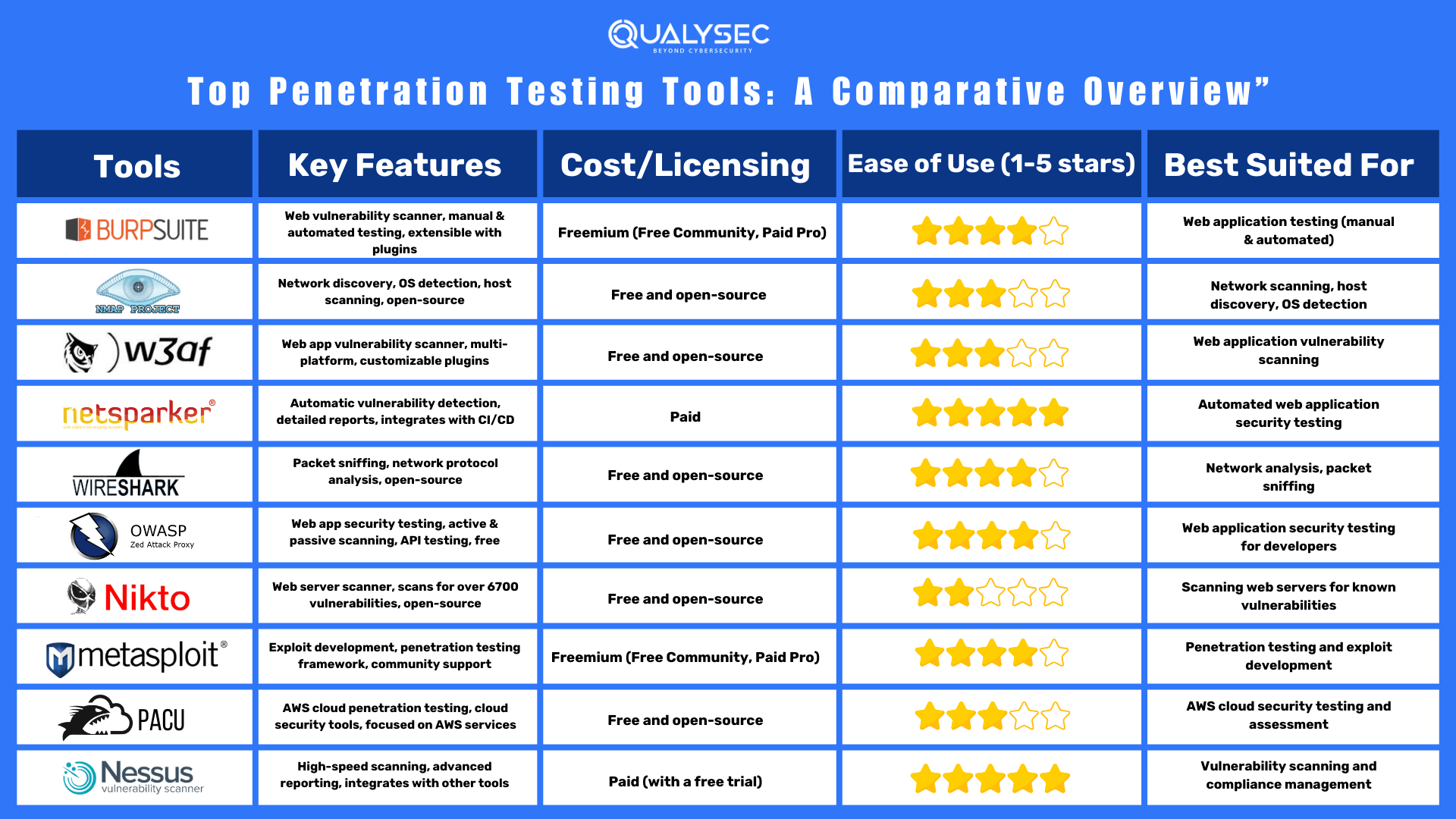
Top 10 Penetration Testing Tools
Cybersecurity experts often use penetration tools during manual or automated penetration testing, making them essential for finding vulnerabilities. Here are the top 10 penetration tools that pros use:
| Sl. No. | Tool | Description |
|---|---|---|
| 1 | BurpSuite | An application testing tool that helps identify vulnerabilities and potential security risks in web applications by intercepting and analyzing HTTP/S traffic. |
| 2 | NMap | NMap (Network Mapper) is a security scanner that scans networks to determine online hosts and services. |
| 3 | W3AF | W3AF is a web application attack and audit framework designed to secure web applications. |
| 4 | Netsparker | Netsparker is an automated web application security scanner that identifies vulnerabilities such as SQL injection and cross-site scripting (XSS) in websites and web applications. |
| 5 | Wireshark | Wireshark is a network protocol analyzer used to investigate security issues and detect network errors. |
| 6 | OWASP ZAP | OWASP ZAP is an app scanner for testing web applications, providing security automation options. |
| 7 | GitHub Nikto | GitHub Nikto is a vulnerability scanner that scans web servers for dangerous files and outdated software. |
| 8 | Metasploit | Metasploit is an open-source modular penetration testing framework that is used to identify, exploit, and validate vulnerabilities in systems, helping cybersecurity professionals strengthen their defenses against potential attacks. |
| 9 | Pacu | Pacu is an open-source cloud security tool designed to help identify and exploit vulnerabilities in Amazon Web Services (AWS) environments. |
| 10 | Nessus | Nessus is a widely-used vulnerability scanner that helps identify and remediate security issues in systems and networks |
Best Penetration Testing Tools – A Comparative Overview
Reasons Why Penetration Testing Is a Necessity
Penetration testing is designed to eliminate dangerous security flaws. Vulnerabilities can still exist due to various reasons such as complex coding, evolving threats, and human error. A penetration test provides an evaluation of vulnerabilities that exist due to various reasons mentioned above.
Pen testing can help an organization in several key ways:
- Find Weaknesses in Systems: Penetration testing identifies vulnerabilities and weaknesses within an organization’s software, networks, and systems that could potentially be exploited by malicious actors. This includes both known vulnerabilities and newly discovered ones that standard security measures might miss.
- Determine the Robustness of Controls: By simulating real-world attacks, pen tests assess the effectiveness of existing security controls and measures. This helps organizations understand how well their defenses hold up under attack and identify areas that need improvement.
- Support Compliance with Data Privacy and Security Regulations: Many industries are subject to strict data privacy and security regulations such as PCI DSS, HIPAA, and GDPR. Organizations use penetration testing to ensure they meet regulatory requirements by providing evidence of proactive security measures and identifying any compliance gaps that need addressing.
Conclusion
It is essential to protect user data from cyber threats. This is essential in today’s digital age with continuous expansion where new threats have become common. Penetration testing is an essential tool for organizations that need to strengthen their security posture.
During a penetration test, this process highlights potential weaknesses along with a deeper understanding of the vulnerability and its impact on the network or application. Using the best penetration testing tools can highly benefit the company in improving its security posture.
FAQs
Q. What Are the leading penetration testing tools?
A: Among the various penetration testing tools available, you’ll find options like Metasploit, NMap, Burp Suite, and Nessus. The tools are used to find vulnerabilities in a computer network or the application where penetration testing is being performed.
Q. What is the main goal of penetration testing?
A: The primary objective of penetration testing, often referred to as pen testing, is to identify security vulnerabilities in a system, network, or application.
Q. How frequently should an organization conduct penetration testing?
A: The frequency of penetration testing depends on several factors, including the organization’s industry, regulatory requirements, and the evolving threat landscape. However, organizations should conduct penetration testing at least once a year.
Top Company Choose Qualysec for their Pentesting need

































































































































































































































































































































































































































































































































0 Comments