Millions of businesses worldwide use Amazon Web Services (AWS) to build and deploy different types of applications. Being a leading cloud platform, AWS provides various cloud computing services including cloud storage, databases, and various data analytics and AI applications, along with multiple deployment and automation services. As a result, the security of AWS services is now a top priority and AWS penetration testing is leading the way.
The most recent AWS breach occurred in May 2022 when a security company discovered over 6.5 terabytes of exposed data on servers belonging to Pegasus Airlines. According to an official report by Amazon, cybercrime damage costs are expected to reach $10.5 trillion in 2025.
In this blog, we will learn about AWS penetration testing, why it is important for businesses, and its different aspects. Because AWS is a third-party data center, penetration testers need to follow specific instructions and comply with AWS restrictions.
What is AWS Penetration Testing?
AWS penetration testing is the process of simulating real-world cyberattacks on an AWS infrastructure to find vulnerabilities in its security measures. Penetration testers or pentesters use techniques that real hackers use to exploit security flaws present in the AWS platform.
The result of AWS pretesting is a report that includes the vulnerabilities found during the process, their severity of impact, and steps to fix them. Penetration testing on AWS should be performed regularly to ensure your security measures are strong enough to protect the sensitive data and information stored in it.
Why AWS Penetration Testing is Important for Businesses
Cloud environments are quite complex, and several security issues can be difficult to detect using standard cloud security measures. Here are a few reasons why AWS penetration testing matters and why every business should perform it:
Neglecting Client’s Share of Responsibility Model
AWS uses a shared responsibility model where the cloud customers are responsible for securing their workloads and data. In most cases, organizations have poor security measures over their security responsibilities in the cloud. Hence, penetration testing is needed to find any weaknesses present and take necessary steps to prevent unauthorized access.
Missing Authentication, Permissions, or Network Segmentation
Many AWS resources do not have multi-factor authentication, proper network segmentation (using AWS security groups), or provide excessive permissions. Penetration testing helps to identify these security gaps in a large cloud deployment. In addition to that, it also helps to categorize and remediate these security gaps.
Compliance Requirements
Organizations that are under compliance standards like PCI DSS, HIPPA, SOC 2, etc. must ensure that their AWS resources meet these requirements. For this, it is mandatory to perform internal audits of cloud assets, including penetration testing.
Looking for a top penetration testing provider for your AWS environment? Qualysec has the best testers who use the latest tools and techniques to find different ways that can hamper your business. Contact us now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
AWS Shared Responsibility Model
AWS security testing follows a shared responsibility model. Amazon distinguishes between two types of security:
Security of the Cloud (Amazon’s Responsibility)
This refers to the security of the AWS cloud platform itself, including all AWS services and the cloud platform. Amazon is responsible for securing the cloud platform and regularly conducts tests with internal or external security engineers. Customers are not allowed to perform penetration testing on this aspect of cloud security.
Security in the Cloud (Customer’s Responsibility)
This refers to the security of resources or assets deployed by an organization on the AWS platform. These responsibilities lie with the company or resource owner, who must ensure that applications, assets, and systems are securely configured. Generally, organizations are allowed to conduct penetration testing to verify these aspects of a secure deployment.
What is Allowed to Test in AWS?
Amazon allows customers to perform penetration testing on AWS assets. However, there are certain terms and conditions on what you can and cannot test across the platforms.
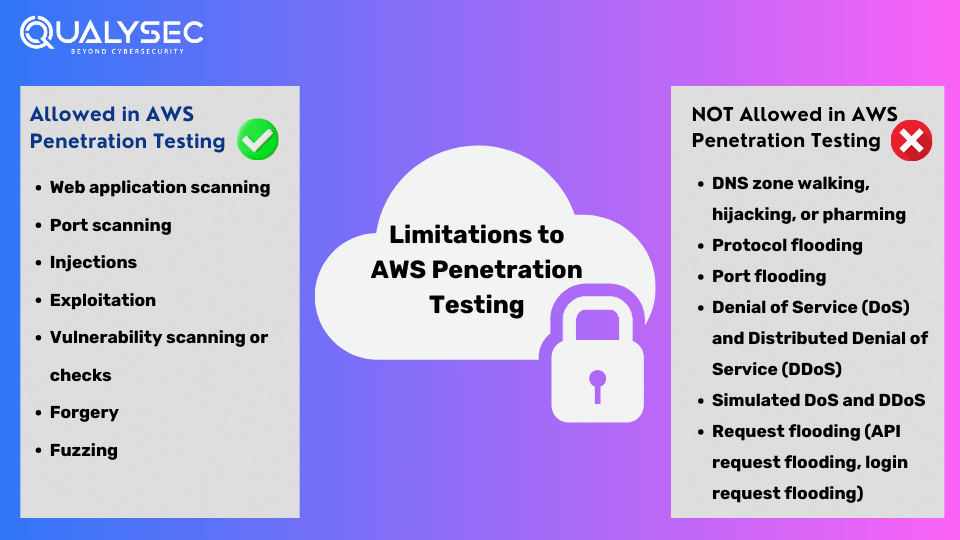
Here’s what is allowed in AWS penetration testing:
-
- Web application scanning
- Port scanning
- Injections
- Exploitation
- Vulnerability scanning or checks
- Forgery
- Fuzzing
A Detailed Summary:
-
- Allowed: Security tools that remotely check AWS assets to identify software names and versions. For example, banner grabbing. This aims to compare against vulnerable versions for denial-of-service (DoS) attacks.
- Allowed: Security tools or services that temporarily or permanently crash a running process on AWS assets for local or remote exploitation. However, it is not allowed for resource request flooding or protocol flooding.
You can conduct these security tests remotely on AWS assets, locally on virtualized assets, or between AWS assets.
What is Not Allowed to Test in AWS?
AWS allows you to conduct security assessments like penetration testing to check your security measures. However, AWS also ensures that these tests do not affect other AWS users or the quality of the AWS services.
Here’s what is NOT allowed in AWS penetration testing:
-
- DNS zone walking, hijacking, or pharming
- Protocol flooding
- Port flooding
- Denial of Service (DoS) and Distributed Denial of Service (DDoS)
- Simulated DoS and DDoS
- Request flooding (API request flooding, login request flooding)
Customers are responsible for verifying and validating that any security test performed by the customer or someone on their behalf follows these policies. Those who violate this policy will be held responsible for any damages to AWS or AWS customers caused by their security testing activities.
Prerequisites for AWS Penetration Testing
Define the following aspects before you conduct penetration testing on AWS assets:
-
- The scope of the penetration test, which includes the target system
- The type of penetration test to be performed
- Requirements of the penetration test, which should be mutually agreed upon by the stakeholders and the pentesting contractor
- A protocol that the penetration tester should follow in case they discover a vulnerability
- A schedule for the penetration test
- Written approval by system owners for pentesters to conduct the test
How to Perform AWS Penetration Testing
Performing AWS penetration testing requires careful planning and execution. However, it is equally important to ensure thorough security assessments with minimal disruptions.
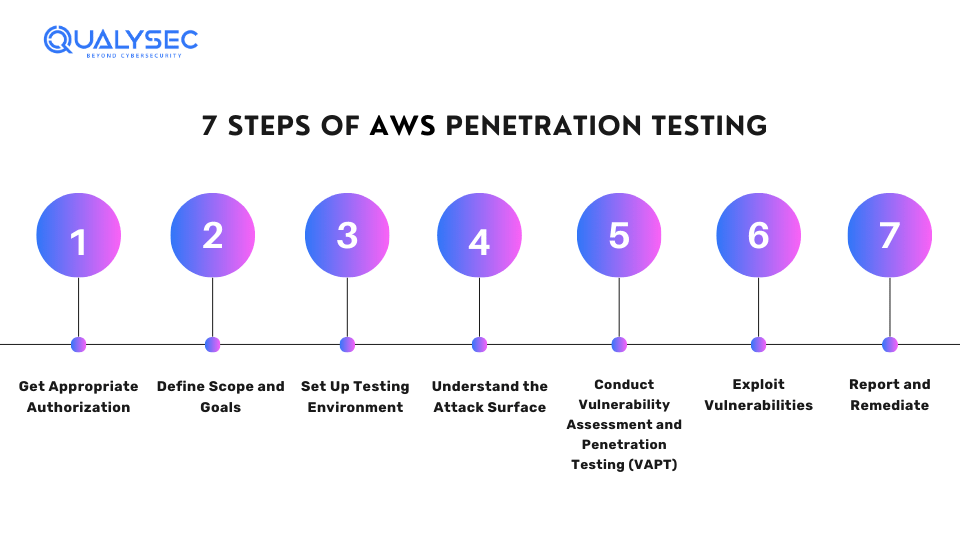
Here are the basic steps of performing penetration testing on AWS:
Step 1: Get Appropriate Authorization
Before conducting any security testing, get written permission from the AWS account owner or organization. This may require you to contact AWS support (if you are seeking to test non-approved services) or follow your organization’s specific security policies.
Step 2: Define Scope and Goals
Define which systems, applications, and AWS services you need to test. Consider any compliance rules or confidential data that needs protection. In addition to that, learn more about how to prepare for a penetration test.
Step 3: Set Up Testing Environment
Make a separate testing environment in AWS, which is different from the production environment to prevent accidental disruptions. This may include setting up virtual machines, networks, and security groups exclusively for the pen test.
Step 4: Understand the Attack Surface
Gather as much information as you can about the AWS environment you are going to test. This involves identifying services, subnets, instances, S3 buckets, Identity and Access Management (IAM) roles, and other possible weak points. Furthermore, you can use techniques like network scanning, vulnerability scanning, and social engineering.
Step 5: Conduct Vulnerability Assessment and Penetration Testing (VAPT)
The main goal of AWS penetration testing is to find vulnerabilities present in the AWS environment. You can find weaknesses in various areas such as IAM policies, S3 bucket permissions, and EC2 instance configurations. For example, you might examine AWS CloudTrail logs to track user activity and uncover potential security risks.
Step 6: Exploit Vulnerabilities
Once you detect the vulnerabilities, you need to exploit them to determine their impact. This might involve exploiting weak access controls, misconfigurations, or vulnerabilities specific to certain AWS services. However, you need to ensure that you target only your resources and do not affect other AWS users.
Step 7: Report and Remediate
The penetration testers make a detailed report that outlines the vulnerabilities found and the steps to remediate them. Further, you can share this report with the system owner or administrator to make the necessary fixes.
Have you ever seen an AWS penetration testing report? If not, here’s your chance. Quickly click below and download a sample report now!
Area of Focus for AWS Penetration Testing
Here are a few key areas that the penetration testers should focus on during penetration testing. As a result, it will help them find vulnerabilities and potential security risks within the AWS resources.
Identity and Access Management (IAM)
Penetration testers should test whether:
-
- Service accounts have unrestricted permissions
- Keys exist in the root account
- Users have multiple keys
- The root account is used for routine tasks or automation
- SSH and PGP keys haven’t been refreshed
- Accounts are inactive
- Multi-factor authentication is in place
Logical Access Controls
The penetration testing should focus on the following:
-
- Checking if tasks are properly assigned to resources
- Testing that AWS account credentials are safe
- Ensuring controlled access to AWS processes and sensitive resources
S3 Buckets
Amazon S3 (Simple Storage Service) buckets are vital to prevent data exposure and unauthorized access. Testers should focus on whether:
-
- security features like authentication and encryption are on for buckets.
- Only let authorized users do operations like GET, PUT, and DELETE.
- Turn on security checks like versioning and logging for buckets.
Database Services
-
- Here, the penetration tester should focus on whether:
- The access is limited to known IP addresses
- The applications are safe from SQL injection or command injection vulnerabilities
- The data is backed up and the backups can be successfully restored.
- Sensitive resources are deployed across various availability zones (multi-AZ)
Conclusion
Performing AWS penetration testing is crucial to secure your cloud infrastructure. Organizations can enhance their cloud security and protect sensitive data by following a structured process and using the right tools and techniques. However, it is important to act ethically, stay within legal limits, and collaborate with system owners to fix the vulnerabilities found. AWS is a third-party service provider, which is why we need to be responsible while conducting penetration testing if we aim to strengthen the overall security measures.
Also Explore: Top AWS penetration Testing Companies
FAQs
Q: What is penetration testing on AWS?
A: AWS Penetration testing is designed to simulate real attacks on AWS services to identify and fix vulnerabilities present in them that could lead to possible cyber threats. As a result, it aims to enhance the overall security of the cloud environment.
Q: Is permission required from AWS for all penetration testing?
A: You don’t need approval from AWS to conduct penetration tests against or from resources on your AWS account. However, there are certain limitations on what you can and cannot test on the platform.
Q: Who conducts AWS penetration testing?
A: Generally, a third-party penetration testing provider is the best choice for conducting AWS penetration testing. They have the necessary skills, expertise, techniques, and experience to perform comprehensive penetration tests.






























































































































































































































































































































































































































































































































0 Comments