With the growing popularity of Software as a Service (SaaS) applications, an increasing number of clients are seeking SaaS security testing advice and asking for a technical examination. Many firms are worried about the security of SaaS applications as they adopt this technology, and they are seeking a security analysis that detects any threats.
This is a wise choice. As SaaS adoption has grown, much of the data that was formerly housed in on-premises systems is now increasingly being stored in the cloud by SaaS companies on behalf of their customers.
This increases the need for enterprises to evaluate the security strengths and hazards of any SaaS service. While we strongly advocate for a comprehensive strategy, in this blog, we will focus on how to do a SaaS security analysis and what.
Understanding SaaS Security Testing
The process of discovering and addressing vulnerabilities in SaaS applications is known as SaaS application security testing. Security testers employ a variety of ways to identify possible security flaws, including security scans, manual testing, and evaluating application source code for common faults that unauthorized parties can exploit.
Furthermore, a dependable SaaS security team is essential for businesses that employ SaaS apps. This is due to the fact that SaaS providers typically keep a huge quantity of sensitive data, including personally identifying information and credit card details. As a result, they are a prime target for malicious actors.
The Importance of SaaS Security Testing
Security testing is used to discover and manage hazards. Attackers can exploit security flaws, resulting in data breaches, money loss, or other negative consequences for your firm. Continuous security monitoring procedures can help you avoid such hazardous situations.
Cloud computing services, such as Software as a Service (SaaS), are rapidly being used by businesses to cut costs, enhance efficiency and agility, and gain a competitive edge. While the benefits of adopting cloud services are obvious, there is also an increased risk of cybersecurity risks. Cloud service companies manage massive amounts of data from several clients, making them attractive targets for hackers.
Furthermore, there are security vulnerabilities unique to SaaS. If an attacker gains access to a cloud provider’s servers, they may be able to access all of the company’s data and apps in one fell swoop.
Is your business looking for a penetration testing service provider to guide your cybersecurity? Don’t worry! Please reach out to our experts for a free chat today. We’ll help uncover and address any vulnerabilities in your business infrastructure.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
The Components of SaaS Security Management
To further understand how to handle SaaS security, examine the three fundamental architectural components of an application:
Client Connection Security
It is critical to monitor client connections to your SaaS system. To determine the breadth of each user’s risk, your security team must understand their authentication, rights, and behaviors within and across business-critical apps. Furthermore, in order for your security team to have easy access to this data, it must be aggregated and normalized from each application into a single, simply understood format. This is critical for expanding the zero-trust principle of “never trust, always verify” beyond identity providers and into SaaS services.
Application Security
The SaaS apps that are central to your organization are fundamentally distinct and complicated systems, complete with the complexities and high-level operations that one would expect from an operating system. Securing these apps necessitates a thorough grasp of each platform, its structural weaknesses, and challenges unique to your context. Continuous monitoring of the application security posture is crucial here, including both application settings and user privileges.
SaaS security posture management should entail not only understanding the status of your controls and privileges but also monitoring the actions linked with them in order to detect gaps or uncover concerns that aren’t accessible via the application API.
Integration Security
Third-party apps are integrated into core applications by SaaS users and administrators to extend functionality, automate workflows, interface with other services, or even play their favorite games. Once permitted, these connections retain their rights and access to the core program indefinitely—a vulnerability that, if left unchecked, may pose a major security concern. An attacker can hack even vetted third-party programs, offering a backdoor into core applications. They fall outside of the zero-trust architecture without ongoing monitoring and threat detection to validate the integrations.
What are the Risks in SaaS Security?
Companies such as Microsoft have recently had severe data security breaches. With such recent instances fresh in the minds of SaaS providers and consumers, it stands to reason that remaining current on the highest dangers would be a priority. Here are the top risks in SaaS security you should know about:
Misconfigurations
Misconfigurations arise when adequate procedures to guarantee cloud security are not performed. This results in compromised data security on both the SaaS provider’s and the customer’s end. Complex hierarchies in SaaS systems can create a bigger arena for such misconfigurations to occur. They can lead to malware, ransomware, and phishing assaults, all of which can end in data breaches and theft.
Inadequate compliance and regulation
To maintain comprehensive cybersecurity operations, organizations must ensure regulatory compliance and certification with safety regulations. Even if your organization follows internal compliance procedures, relying on non-compliant SaaS vendors may expose you to non-compliance risks. To mitigate this risk, your security team should review and analyze SaaS vendors’ compliance with industry standards and rules on a regular basis. Failure to do so may result in data breaches, large fines, and reputational damage to your company.
Data storage and loss
Cloud-based data storage is vulnerable to data loss or corruption as a result of network issues, device failures, and calamities. To avoid hazards, businesses should thoroughly analyze their SaaS storage providers. When storing data, they should choose reliable cloud service providers and robust data encryption. Implementing data backup techniques, constantly monitoring retention policies, and concentrating on regulatory and legal compliance are essential measures for preventing data loss while keeping data integrity.
Click here to read more about the SaaS Application Risks and Mitigation Process.
Types of Security Testing in SaaS Applications
Many important sorts of testing procedures must be used for SaaS solutions to guarantee that the primary components of the SaaS are working properly:
Functional Testing
Functional testing of your SaaS product ensures that the application performs as expected. This sort of testing is frequently performed in a staging environment by executing manual tests according to previously set test plans and considering the end user’s wants and expectations.
API Integration Testing
The capacity of any SaaS service to handle API calls is critical to its success. When a third-party application developer uses your API to create their applications, it provides value to your product. As a result, it is critical to evaluate all API interfaces for dependability, safety, usability, performance, and the quality of API documentation.
Penetration Testing
It is designed to detect technical flaws and vulnerabilities in deployed systems or applications. Penetration tests can be done manually with the given information using gray-box approaches. Implementing a comprehensive user access checklist, such as a basic UAR checklist, is critical for regulating system interactions, eliminating vulnerabilities, and improving security.
How is SaaS Security Testing Done?
A good cyber security testing services provider knows the drill of testing a SaaS application. Furthermore, they will provide you with all the necessary processes with thorough guidance on the pentesting process. Here’s a guide to the stages performed to secure your SaaS application:
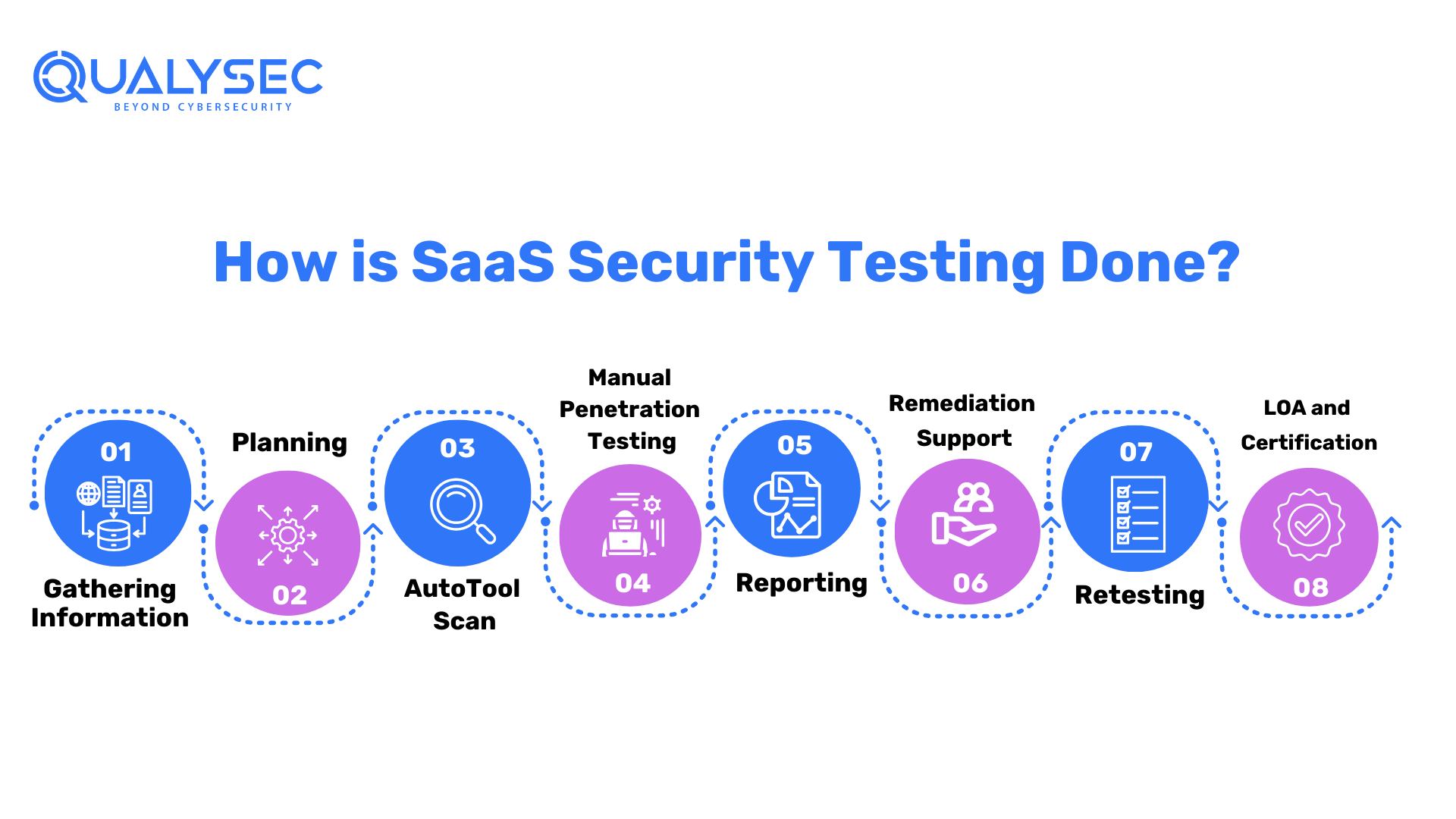
Gathering Information:
The initial step in SaaS application security testing is to gather as much information as possible. This includes a two-pronged approach: utilizing readily available information from your end, as well as utilizing numerous ways and tools to get technical and functional insights. Schematics for architecture, network topologies, and any existing security measures may be provided. Understanding user roles, permissions, and data flows is critical for building an effective testing strategy.
Planning
The penetration testing organization begins the process by carefully defining the objectives and goals. They delve extensively into the technical and functional complexity of the application. Furthermore, this extensive investigation allows testers to alter the testing strategy to target specific vulnerabilities and threats in the SaaS system.
A comprehensive penetration testing plan is created, outlining the scope, methodology, and testing criteria. Furthermore, to guide the testing process, the firm provides a high-level checklist. They acquire and prepare the essential files and testing instruments. This method includes configuring testing settings and checking script availability to ensure a smooth and successful assessment.
Auto Tool Scan
During the penetration testing process, especially in a staging environment, an automated and intrusive scan is necessary. This scan comprises utilizing specialized testing tools to seek vulnerabilities on the application’s surface level carefully. The automated tools mimic prospective attackers by crawling through every request in the application, uncovering potential weaknesses and security gaps.
By running this intrusive scan, the testing organization proactively finds and patches surface-level vulnerabilities in the staging environment, acting as a protective measure against potential assaults. This strategy provides not only a thorough review but also quick rectification, boosting the application’s security posture before it’s deployment in a production environment.
Manual Penetration Testing
The organization does extensive manual penetration testing that is perfectly tailor to your SaaS requirements and security standards. This one-of-a-kind technique allows for a thorough examination of potential vulnerabilities throughout the application, including:
- Injection Testing
- Server Configuration Review
- Input Validation Testing
- Data Tampering
- File Testing
- Sensitive Information Discloser Testing
- Encryption Testing
Test Check: Seeking for full-proof SaaS Application Penetration Testing? Get in touch with our professional pen testers and test your application right away. Schedule a Free Call Today!
Reporting
To ensure that possible risks are properly recognized, the team methodically analyzes and categorizes vulnerabilities uncovered throughout the review. Furthermore, a senior consultant conducts a high-level penetration test and thoroughly evaluates the result.
This assures the greatest degree of quality in testing methodologies as well as reporting accuracy. This detailed documentation is a helpful resource for understanding the application’s security condition. A thorough reporting strategy guarantees that stakeholders have valuable insights into the application’s security status as well as practical suggestions for a strong security posture.
Want to check how a comprehensive report can guarantee your SaaS application’s security? Download our sample report here!
Latest Penetration Testing Report

Remediation Support
If the development team requires assistance in replicating or decreasing found vulnerabilities, the reputable testing company provides extensive consultation calls. Penetration testers with in-depth understanding of the detected vulnerabilities encourage direct participation in order to assist the development team in efficiently assessing and responding to security concerns. This collaborative approach guarantees that the development team receives competent guidance, enabling for the smooth and rapid resolution of vulnerabilities to improve the application’s overall security posture.
Retesting
Following the development team’s completion of vulnerability mitigation, a critical stage of retesting occurs. Pen testers do extensive testing to confirm the efficacy of the medicines utilized. The final report is extensive and contains:
- History of Findings
- State Assessment
- Proof and Screenshots
LOA and Certificate
A trustworthy firm goes above and beyond certification by giving a Letter of Attestation, which is an important document. This letter backs up data from penetration testing and security assessments, serves several functions:
- Level of Security Confirmation
- Showing Stakeholders Security
- Fulfillment of Compliance
Furthermore, the testing company will provide a Security Certificate, which will enhance your ability to represent a secure environment, reinforce confidence, and meet the expectations of various stakeholders in today’s dynamic cybersecurity landscape.
Did You Know?
You can also make QualySec’s Pentest Certificate publicly verifiable, allowing your clients and partners to validate it. It aids in the establishment of openness and trust for your company.
Want to learn more? Click here!
What are the Disadvantages of Not Performing SaaS Application Pen Testing?
Organizations might be exposed to numerous risks and vulnerabilities if Software as a Service (SaaS) application penetration testing is not performed. The following are some of the drawbacks of not completing SaaS application penetration testing, along with explanations:
- Security flaws Go Unnoticed: Security flaws in SaaS applications may go undetected if regular penetration testing is not performed. As a result, the system is vulnerable to assault by attackers, who might compromise critical data or interrupt services.
- Increased Risk of Data Breach: Unidentified security flaws allow attackers to exploit the system and obtain unauthorized access to sensitive data. In addition, this can result in data breaches, jeopardizing the security and integrity of user data.
- Failure to Meet Compliance Requirements: Many sectors and regulatory frameworks require firms to undergo regular security assessments, including penetration testing. Noncompliance with these regulations might result in legal penalties and fines.
- Lack of Advanced Threat Preparedness: Cyber dangers are continually developing, and attackers are getting more adept. Furthermore, organizations that do not do regular penetration testing may be ignorant of the most recent vulnerabilities and attack tactics, leaving them unable to fight against modern threats.
- Financial Losses: Security events can result in considerable financial losses, including incident response expenses, system recovery costs, and potential legal proceedings. In addition, investing in penetration testing is a preventative step to reduce the likelihood of such financial losses.
- Incident Response Planning Flaws: Penetration testing frequently shows flaws in incident response strategies. Organizations may fail to recognize flaws in their capacity to identify, respond to, and recover from security incidents in a timely and effective manner if they do not do testing.
- Customer dissatisfaction: Customers want their data to be handled securely. Furthermore, client confidence can erode by a security event caused by a lack of penetration testing, resulting in client churn and challenges in obtaining new customers.
In an increasingly digital and linked world, penetration testing SaaS applications assist firms in identifying and addressing security risks, protecting sensitive data, and maintaining the confidence of consumers and stakeholders.
Also Explore: The Ultimate Guide to SaaS Security Services for Every Business
Best Practices for SaaS Application Security
Here are some of the best practices that are a must-know when providing SaaS security testing services:
- Checklist for SaaS Security
A security company develops a strong security culture that specifies your security needs through the use of a SaaS security checklist. The checklist components may differ depending on the nature of the app. Nonetheless, it should be evaluated and modified on a regular basis, since priorities might shift and new risks emerge. Clarifying your requirements makes it easier to find a provider that meets your requirements.
- Map the Data
Mapping, categorizing, and monitoring all data is crucial for providing top-tier protection. Even if the data is in transit, usage, or rest, SaaS developers must observe it and take the required precautions to ensure its preservation. A thorough grasp of your data assists in identifying possible risks and weaknesses.
- Data Removal Policy
Enforcing a tight data deletion policy is a serious commitment that certain firms make while safeguarding the security of their customers. Customers have control over their data thanks to data deletion rules. SaaS security providers may also ensure compliance with applicable rules and regulations while maintaining their clients’ confidence.
- Identity and Access Management Controls
Identity and Access Management (IAM) technologies demonstrate that users are who they claim to be. SaaS users need to be able to integrate with IAM tools. Furthermore, enterprise users do not want to type a new password every time they visit a different portion of an enterprise-wide application. A sophisticated access control system that determines who accessed what and when is a critical component of any IAM system.
- Monitoring and Logging
It is critical to record all access attempts to the SaaS system, both successful and unsuccessful. The same is true for any data changes. Furthermore, this type of action is critical for minimizing data breaches and developing future security plans.
QualySec Technologies- The Best SaaS Security Testing Company
There are several tasks and actions that a SaaS development team must do. That is why it is critical to select the one you can fully trust to provide more than 100% of what you require to maintain your business safe and hassle-free. This is where QualySec comes in.
Our skilled staff is more than capable of implementing the finest SaaS security standards stated above, as well as others. Our extensive testing knowledge will give you appropriate security alternatives based on the duties done by your SaaS, your preferences, and your area of expertise.
QualySec’s pentest provides both an automatic vulnerability scanner and manual pentesting capabilities for SaaS security testing. You may use our in-house tools as well as commercial tools like Burp Suite, Netsparker, etc. to secure SaaS applications. With that, our pen testers have extensive knowledge and power of manual testing which gives and benefit of zero false results.
We have successfully secured 250+ applications in the last 3 years of our establishments and have 100+ global partners in 20+ countries with a record of zero data breaches. QualySec is the only Indian company providing process-based penetration testing.
We help businesses fulfill compliance requirements like GDPR, SOC2, ISO 27001, etc. with our professional guidance and advanced penetration testing methods. Fill out this form to safeguard your SaaS application today!
Conclusion
From enhanced scalability and simplicity of integration to lower costs and better accessibility, SaaS offers advantages that outweigh its increased vulnerability to security issues. The payoff is that security issues should not be taken lightly.
You can begin securing your SaaS by learning about the most frequent dangers and then analyzing your setup with a detailed checklist. In addition, if you combine this with knowledge of multi-tenancy, isolation schemes, and data protection, you’ll be well on your way to avoiding costly security blunders and infractions.
We at QualySec, have successfully assisted SaaS firms in identifying and repairing significant risks in their SaaS infrastructure. We can assist you in SaaS security testing. Let’s discuss.
FAQs
What is SaaS in cybersecurity?
The methods and processes put in place to safeguard the data and applications hosted by a SaaS provider are referred to as SaaS security. In addition, encryption, authentication, access restrictions, network security, and data backup and recovery are common examples.
What are the best practices for SaaS?
Customer-centric design, regular updates, rigorous security measures, smooth integration possibilities, transparent pricing structures, and rapid customer support are all examples of best SaaS practices. Furthermore, scalability, data protection, and user experience should be prioritized. Solicit and act on consumer input on a regular basis to achieve continual development.
What does SaaS stand for?
Software as a Service (SaaS) refers to software programs that access via the Internet without the need for downloads. Also, users subscribe to remote-hosted apps that are accessed via web browsers, removing the need for maintenance. It is both convenient and cost-effective.
What to look for in SaaS security?
Assess SaaS security by examining data encryption, secure authentication systems, industry compliance, frequent security audits, and incident response protocols. Furthermore, check the openness of the vendor, data backup protocols, and the opportunity to alter security settings. In addition, prioritize a strong security posture to protect critical data and maintain business continuity.































































































































































































































































































































































































































































































































0 Comments