Professional hackers employ an organised process called a pen test methodology to mimic actual cyberattacks and find weaknesses in an infrastructure or system, enabling businesses to fortify their safety precautions.
Key Purpose Of Pen Test Methodology
Pen testing attempts to replicate how criminals can attempt to take advantage of a program’s vulnerabilities.
- Find Weaknesses: The objective is to find security gaps that might be exploited for information theft or illegal access.
- Evaluate Safety Movement: Pen tests assist companies in identifying their present safety advantages and disadvantages.
- Boost Protection: Companies might take action to fix risk factors and raise their level of safety by discovering them.
Various Stages Of A Pen-Test
Although particular approaches may differ, an average pen test typically consists of the following stages:
- Scale and Design: This explains the purposes, reach, and objective of the penetration test.
- Monitoring: Acquire information regarding the objective infrastructure or institution through investigation. Determine possible shortcomings and weaknesses through vulnerability assessment.
- Abuse of power: Try to take advantage of vulnerabilities that have been found while adhering to the parameters.
- After the attack: Keep the network accessible (if at all permitted) and collect more data. Communication: Keep records of discoveries, including weaknesses, their seriousness, and repair suggestions.
“Explore our recent guide on different Phases of Penetration Testing!
Different Types Of Pen Tests
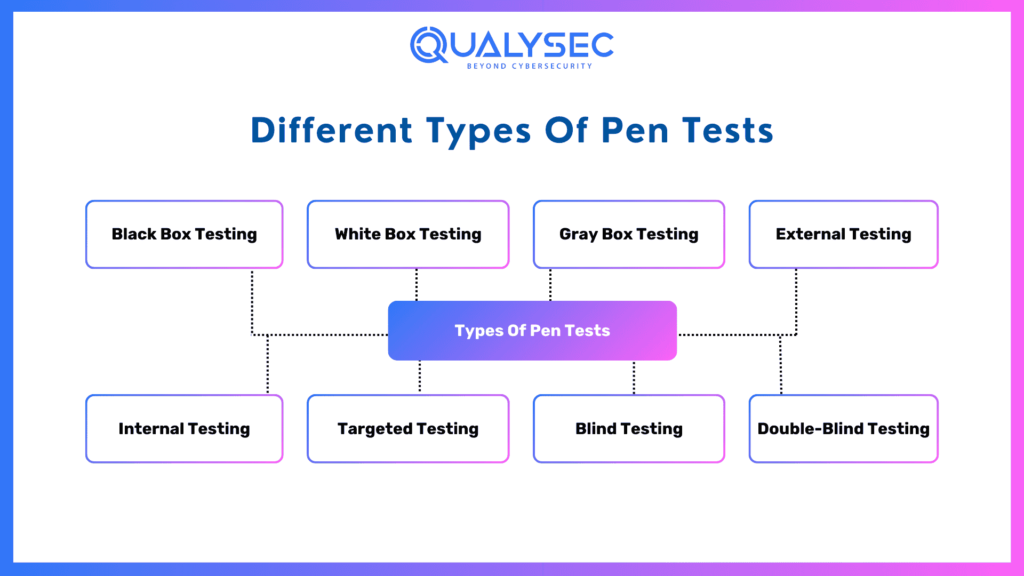
- Black Box Testing- An auditor who has no knowledge of the system before or network is mimicking an external attacker.
- White Box Testing- A testing individual who has complete knowledge of the system and/or network can study these from an internal perspective.
- Gray Box Testing- Compromising knowledge in the network or system from incomplete to thorough knowledge of the system.
- External Testing- In searching for things that would be considered vulnerabilities, an external viewpoint is taken.
- Internal Testing- This testing results in an analysis of vulnerabilities from an internal perspective.
- Targeted Testing- Testing that is directed towards a specific target.
- Blind Testing- Testing with no prior knowledge of the test network or system.
- Double-Blind Testing- When neither the tester nor the organisation is aware of the test being conducted.
Latest Penetration Testing Report

The Core Principles of Pen Test Methodology
1. Uniformity
These approaches offer a structured procedure for methodical pen testing to guarantee its efficacy and yield trustworthy outcomes. By contrasting previous outcomes and sustaining notable growth, it assists businesses in monitoring their security efforts.
2. Observance
Through the particular and comprehensive testing needed for each regulation, these approaches assist enterprises in achieving regulatory obligations such as GDPR, HIPAA, SOC 2, ISO27001, etc.
3. Thorough Risk Evaluations
These techniques assist companies in carrying out thorough and useful attacks that address every potential facet and scenario. This assists in developing mitigation plans and offers a comprehensive picture of the company’s safety status.
Conclusion
Penetration Testing Methodologies are crucial to managing a company’s safety precautions. Businesses can fulfil legal obligations, uphold safety regulations, and increase confidence among stakeholders by implementing these strategies.
Selecting the appropriate approach for your company is crucial to guaranteeing a comprehensive evaluation of every component. Schedule a meeting with our cybersecurity experts for pen testing.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
FAQ
What is a methodology for pen testing?
The set of procedures and rules used to execute a penetration test is known as a penetration testing methodology.
What Makes Penetration Techniques Crucial?
Since it offers an easy road to stick to throughout a pentest, pen testing techniques are crucial as they increase the process’ effectiveness and efficiency.
Which five penetration testing techniques are the most popular?
The peak five methods for penetration testing are ISSAF, OWASP, NIST, PTES, and OSSTM.































































































































































































































































































































































































































































































































0 Comments