Information security compliance is a proven way that ensure your organization’s sensitive data is protected from security incidents. Think about how much information an organization handles daily. From emails, employee records, and customer transactions, each of these are critical to the business and need to be secured.
According to Forbes, 353 million people were affected by data breaches in 2023 alone. Additionally, according to IBM, the average cost of a data breach is said to be USD 4.45 million.
So, to save organizations from costly breaches and penalties, various regulatory bodies have created data protection laws that they need to comply with. In this blog, we are going to discuss these compliances and how they can be achieved.
What is Information Security Compliance?
Information security compliance means adhering to industry-specific laws and standards that ensure sensitive data is protected. These standards or rules are established by a third party, which businesses need to comply with, or else face legal fines and penalties, along with loss of reputation.
Compliance requirements differ according to the industry, location, and data type. For example, in the US, healthcare providers are required to comply with the Health Insurance Portability and Accountability Act (HIPAA), while businesses that manage credit card details should meet the Payment Card Industry Data Security Standard (PCI DSS).
Organizations can achieve this compliance and protect their sensitive information from unauthorized access and data breaches by conducting a series of assessments, such as vulnerability scanning, penetration testing, and routine audits.
Why is Information Security Compliance Important?
Apart from the obvious benefit that it ensures the safety of an organization’s data, information security compliance also helps protect the company’s reputation and maintains the legitimacy of its operations, which can ultimately impact the company’s revenue.
According to PwC, 85% of customers said they won’t do business with a company that cannot guarantee data security. While large enterprises can handle some reputational damage, it can be challenging for small or medium-sized businesses to overcome them.
So, by complying with the information security standards, organizations can improve their current security measures that not only protect the data but also help to enhance it.
1. Protect Sensitive Data
Information security compliance programs provide some of the most effective strategies to protect an organization’s sensitive data. This may include implementing encryption, access control measures, and firewalls.
Many organizations use specialized compliance platforms to support these efforts. For example, exploring some of the OneTrust alternatives can help businesses find the right solution for their needs.
2. Avoid Non-Compliance Fines and Penalties
Certain industries and regions impose significant fines, criminal charges, and other penalties for not complying with data protection laws. For example, the European Union data privacy and security law fines up to €20 million or 4% of the organization’s global annual revenue for not complying with GDPR.
3. Build Customer Trust
Businesses want their new and existing customers to trust them, but if they lose control of customer data, that trust can be easily destroyed. Organizations must ensure that they have adequate security measures, including security testing, to keep their confidential information safe and information security compliance is the best way to do that.
4. Create a Competitive Advantage
A compliance certificate proves that an organization commits to investing in the security of its customer data. This is especially necessary for highly regulated industries, such as fintech and healthcare. It also helps the investors and customers trust your brand more, giving you a competitive advantage.
What are the Compliance Standards for Information Security?
There are hundreds of standards for information security worldwide. However, here are a few major ones:
1. SOC 2
SOC 2 or Service Organization Control Type 2 is created by the American Institute of CPAs (AICPA), for service organizations, which outlines how organizations should manage client data. They need to follow the Trust Services criteria, which include security, availability, processing integrity, confidentiality, and privacy.
2. HIPAA
HIPAA or Health Insurance Portability and Accountability Act was established by the US Department of Health and Human Services (HHS). It provides guidelines to protect private patient health information (PHI). The HIPAA Privacy Rule guarantees the secure transmission of health information to promote quality healthcare.
3. GDPR
GDPR or General Data Protection Regulation is one of the major data protection laws of the European law governing online privacy. According to this standard, any organization that handles an EU resident’s data follows the strict guidelines mentioned. Additionally, those who collect and manage this data are also required to protect it against misuse and exploitation.
4. ISO 27001
Released by the International Electrotechnical Commission (IEC), the International Organisation for Standardisation (ISO) is one of the most recognized international standards for information security. It gives businesses the knowledge they need to protect their most valuable data, such as customer information, financial records, and intellectual property.
What are the Legal Requirements of Information Security Compliance?
The legal requirements of information security compliance change depending on the relevant standard and the jurisdiction. However, here are some general requirements.
1. Data Protection Laws
Data protection laws regulate the collection, use, transfer, and disclosure of personal information and its security. People are given access to their data, companies that protect it are given accountability requirements, and in case of improper or harmful processing of the data, remedies are provided.
2. Data Breach Notification Laws
It outlines who the compliance rules apply to, such as individuals, organizations, or authorities, and what constitutes a breach. These rules mandate that the organization that experienced a breach is mandated to notify the individual whose data was compromised, in addition with all other important parties.
3. Data Retention and Destruction
Data retention means keeping various kinds of data for a specified amount of time. The practice of data destruction (sifting and shredding) is no longer valuable to the organization. These data security policies govern how personal data is gathered, preserved, or erased.
4. Contractual Requirements
Organizations having contractual agreements with clients, business partners, or suppliers might be imposed with specific information security standards. These agreements could have policies related to security audits, incident response, data confidentiality, and protection.
What are the Different Types of Information Security?
These are the primary types of information security that organizations implement to protect a variety of data in different domains.
- Network Security: Protects external networks from threats and malicious activities. Involves implementing security measures such as firewalls, intrusion detection systems, and security monitoring tools.
- Application Security: Focuses on keeping software and APIs free of threats and vulnerabilities. Involves implementing authentication, encryption, and secure coding practices.
- Endpoint Security: Protects end users, such as laptops, smartphones, and tablets against attacks. Involves implementing endpoint detection and response (EDR) tools, web content filtering, and application control.
- Identity and Access Management (IAM): Checks who has access to what information and ensures that only authorized users can access sensitive data.
- Cloud Security: Protects data, applications, and services stored and accessed in cloud environments. Includes measures such as data encryption, access controls, and regular security audits.
- Cryptography: Uses techniques like encryption to protect the privacy and integrity of data in transit and at rest. One cannot read information without an encryption key.
How to Implement Information Security Compliance?
Information security compliance involves different steps to ensure that your data is safe from potential threats. Here are 8 major steps:
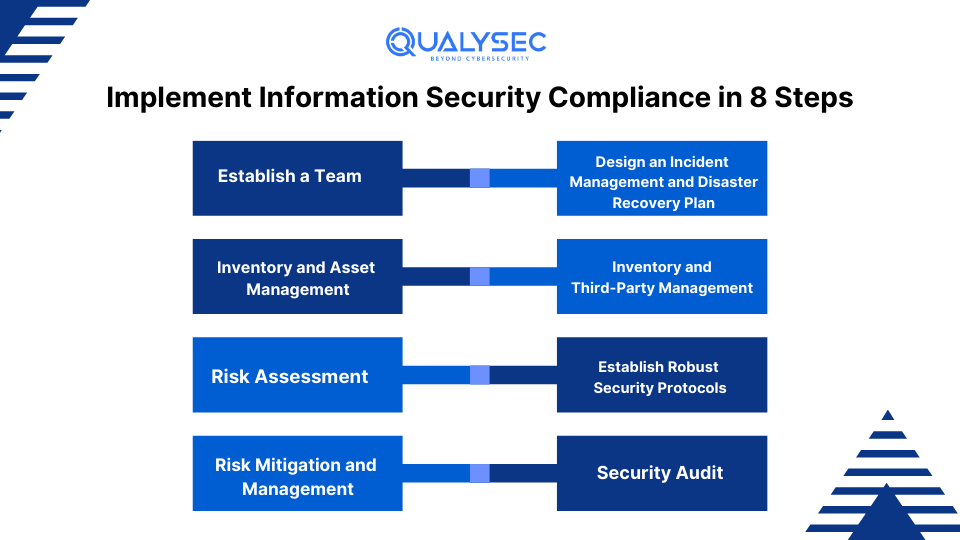
1. Establish a Team
Assemble a skilled team to lay a foundation for your security program, including executives for strategic planning and experts for daily operations. As a result, this ensures a balanced and effective approach to securing your organization’s data.
2. Inventory and Asset Management
Take inventory of all company assets, including hardware, devices, applications, networks, and databases, to ensure everything with sensitive data is secured. in addition, assign owners and categorize these assets by importance to prioritize data protection effectively.
3. Risk Assessment
Identify and prioritize potential threats to your company by listing and ranking them based on likelihood and impact. Conduct a security risk assessment to assess existing vulnerabilities in processes and technologies to determine which areas are more at risk and develop strategies to address them.
4. Risk Mitigation and Management
Decide how to handle identified risks, whether by reducing them with measures like firewalls, transferring them through insurance or third parties, or accepting them if the potential losses are manageable. Prioritize addressing significant dangers to prevent irreversible consequences.
5. Design an Incident Management and Disaster Recovery Plan
Develop an Incident Management and Disaster Recovery Plan to ensure your organization is prepared for any security incident or natural disaster. This proactive planning will help you respond effectively to crises, protecting your data and systems.
6. Inventory and Third-Party Management
Manage third-party vendors and other outside parties with access to your data by taking inventory and prioritizing them based on risk. Regularly monitor and update this list to uncover and address potential security threats, ensuring your business’s assets remain secure.
7. Establish Robust Security Protocols
Implement strong security protocols, including technical measures such as firewalls and antivirus software, and non-technical controls like policies and physical security measures. Additionally, establish a security policy that guides access controls, passwords, and backups to maintain a secure environment.
8. Security Audit
Hire a third-party company to perform security audits, including vulnerability assessments and penetration testing, to identify and fix security weaknesses. Also, conduct audits against global security standards like ISO 27001 or PCI DSS and perform internal audits to evaluate controls, policies, and risk management.
Want information security compliance? Do penetration testing with Qualysec and secure your data from unauthorized access and breaches. Also, get expert help and actionable insights to improve your security measures. Book a meeting now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Difference Between IT Security and IT Compliance
While IT security and IT compliance are closely related, they differ in quite a few aspects.
| Aspect | IT Security | IT Compliance |
| Definition | Protects systems and data from threats. | Ensures adherence to laws, regulations, and standards. |
| Focus | Confidentiality, integrity, and availability of information. | Meeting regulatory and legal requirements. |
| Approach | Proactive and continuous | Reactive and periodic |
| Objective | Prevent unauthorized access and breaches. | Avoid legal penalties and achieve certification. |
| Methods | Firewalls, encryption, access controls, etc. | Documentation, audits, and reporting. |
| Outcome | Reduced risk of cyberattacks and data breaches. | Achieving legal and regulatory compliance. |
| Examples | Implementing multi-factor authentication and encryption. | Complying with GDPR, HIPAA, SOC 2, ISO 27001, etc. |
Conclusion
For organizations that handle sensitive customer data and intellectual property, they must have adequate security measures to prevent data breaches. This is what achieving information security compliance does to your business. By following the guidelines of the specific industry standard your business is relevant for, you can not only protect sensitive information, but also enhance your overall security, avoid legal penalties, and build trust among your customers and stakeholders.
FAQs
Q: What are the 4 pillars of information security?
A: The four pillars of information security are:
- Security reminders
- Protection from malicious software
- Log-in monitoring
- Password management
Q: What is information security policy compliance?
A: Information security policy (ISP) is a set of rules and procedures that ensures all organizations meet minimum IT security and data protection measures. It also helps in building customer and stakeholder trust.
Q: How often should I perform compliance audits?
A: Compliance audits should be performed at least once a year to stay one step ahead of potential threats. You can also perform a compliance audit if your region or industry has a new standard.
Q: Who can perform an information security compliance audit?
A: A third-party security audit company is the best choice to perform an information security compliance audit. Additionally, they can provide other services that will help enhance your data security measures.












![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)
































































































































































































































































































































































































































































































0 Comments