CMMC compliance pentesting ensures businesses working with the US Department of Defense (DoD) meet specific cybersecurity standards to protect sensitive information. The DoD established the Cybersecurity Maturity Model Certification (CMMC) on December 26, 2023, so that all contractors and suppliers follow the same processes across several maturity levels.
Since cyber threats are continuously evolving and getting more sophisticated, they pose a significant risk to the Defense Industrial Base (DIB) and national security. This is where penetration testing becomes useful, as it helps identify and mitigate security vulnerabilities in apps and networks that could result in cyberattacks.
Do you know? By 2025, it is expected that cyberattacks and breaches will cost the global economy $10.5 trillion annually.
In this blog, we will cover everything, from understanding the CMMC framework to the steps involved in CMMC compliance pentesting.
Let’s start!
What is CMMC compliance?
The Cybersecurity Maturity Model Certification (CMMC) compliance framework outlines the security measures a business or defense contractor needs to maintain to protect sensitive information. Under CMMC, any business that handles Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) should achieve the compliance levels, to become eligible for defense-related work.
The Defense Industrial Base (DIB) includes a large network of contractors, service providers, and suppliers that work with the DoD and handle sensitive information, making them a prime target for cyberattacks. The CMMC compliance is fairly new and ensures that these contractors and suppliers maintain a strong cybersecurity posture to protect the information.
CMMC Maturity Levels
Initially, there were 5 levels of CMMC certifications, level 1 being “basic” and level 5 being “highest”. However, with CMMC 2.0, these levels have been modified and currently, there are 3 levels of CMMC certifications that businesses/contractors can achieve.
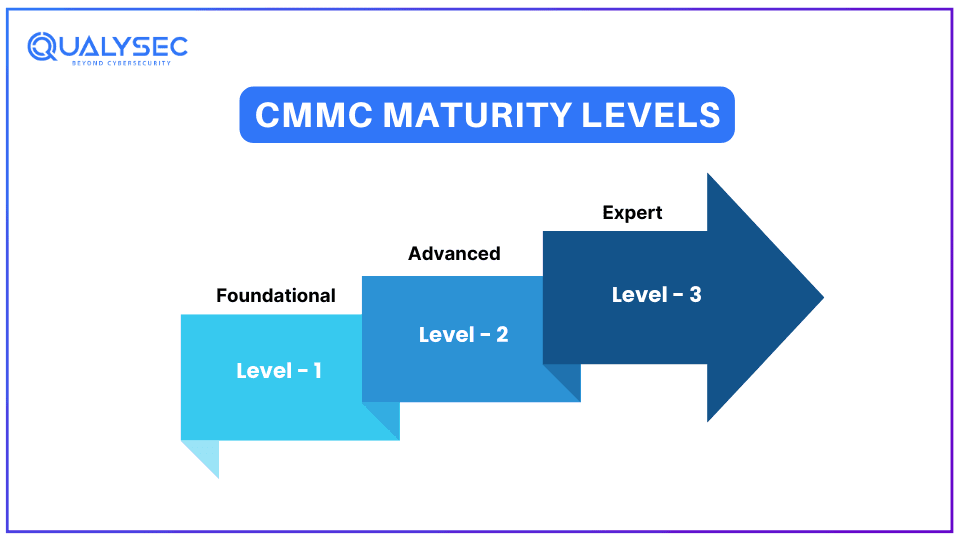
Level 1 – Foundational
This is what most companies should have already achieved with their digital assets. This includes basic security measures, such as password hygiene and antivirus software. There are 17 such CMMC compliance requirements at this level. Level 1 CMMC certification is generally for DoD contractors that handle Federal Contract Information.
Level 2 – Advanced
There is a total of 110 CMMC compliance requirements at this level, including physical access control, risk management, cybersecurity incident response, and system integrity. Level 2 CMMC certifications are for contractors handling Controlled Unclassified Information (CUI).
Level 3 – Expert
The highest CMMC certification level includes the company’s proactive methods to detect and mitigate cyber threats before they begin. Additionally, they should have controls and processes to audit IT infrastructure, identify security gaps, and fix them. Companies having Level 3 certification also fulfill Levels 1 and 2. They are usually assessed by the government’s Defense Contract Management Agency.
Whether you work with the government or not, you should try to achieve at least level 2 compliance because it will make your business secure against potential threats. You can take the help of a good penetration testing company to assess your security measures and suggest where you need to improve.
What is CMMC Compliance Pentesting?
Penetration testing is a requirement to achieve CMMC compliance. CMMC compliance pentesting involves simulating cyberattacks on the company’s applications and networks to identify security vulnerabilities. This helps the contractors or businesses willing to work with the DoD, find and fix security issues before they face data breaches or other security incidents.
The goal of CMMC compliance pentesting is to provide a clear picture of the business’s current security status. Regular pentesting is important to maintain a strong security posture and ensure ongoing compliance with CMMC requirements.
By conducting CMMC pentesting, businesses can showcase their commitment to cyber security and become eligible to work with the US DoD. This not only ensures their own security but also contributes to the overall security of highly confidential national defense information.
Why do you Need CMMC Compliance Pentesting?
CMMC compliance pentesting is essential for businesses that are working or want to work with the United States Department of Defense (DoD).
- Meet CMMC Level Requirements: Each CMMC maturity level has different cybersecurity requirements. Pentesting helps ensure that your organization meets the necessary standards for your certification level.
- Meet DoD Requirements: To work with the DoD, you must comply with specific security standards. Regular pentesting helps you meet these requirements and stay eligible for future contracts.
- Identify Compliance Gaps: Pentetsing helps uncover vulnerabilities and gaps in your security measures. It also highlights areas that need improvement to achieve full CMMC compliance.
- Prepare for CMMC Audits: By conducting regular CMMC compliance pentesting, you prepare for CMMC audits by ensuring your security measures are up-to-date and compliant with certification standards.
- Improve Own Security Posture: To meet CMMC compliance, one needs to have strong security measures. In this process, you enhance your own security posture for the safety of your applications and network.
- Build Trust: By doing pentesting, you show that you are committed to cybersecurity. This helps build trust with the DoD, stakeholders, customers, and other partners.
What are CMMC Compliance Requirements?
Earlier we discussed all three levels of CMMC compliance and what you need to achieve them. The CMMC compliance requirements are hugely based on the NIST (National Institute of Standards and Technology), especially its SP 800-171 set of guidelines. These guidelines govern everything from Section 3.5 (authorization and authentication) to Section 3.10 (physical protection).
To work with DoD, there are several general steps required to achieve CMMC compliance, such as:
CMMC Compliance Requirements
CMMC Level – 1: Create and Maintain
- An incident response document and process
- A vulnerability management document and process
- A patch management system
- Access controls to IT systems and data
- Physical controls for these systems
- Secure communications
- And more
Level – 2: Monitor and control
- System vulnerabilities
- Attempts to gain unauthorized access to systems and data
- Communications at the applications, network, and system layers
- Cybersecurity training for end-users with access to these systems
- IT systems even during acquisition, development, and maintenance
- And more
Level – 3: Implement and maintain
- Company-wide up-to-date cybersecurity protocols
- Identity and access controls for devices, systems, and end-users
- An effective threat detection and mitigation program
- Continuous monitoring of all digital systems and data
- And more
What is the CMMC Security Rule?
The Cybersecurity Maturity Model Certification (CMMC) compliance program is aligned with the DoD’s information security requirements for DIB partners. It is designed to ensure that the vendors of the DoD have the necessary security measures to protect highly sensitive national information.
The CMMC 2.0 Compliance Program has 3 Key Features
- Tiered Model: CMMC states that the companies entrusted with the national security information must meet the Level 2 (advanced) CMMC certification requirements, depending on the type and the sensitivity of the information.
- Assessment Required: CMMC assessment allows the DoD to verify whether the contractor has clear cybersecurity standards.
- Implementation through Contracts: Once CMMC is fully implemented, some DoD contractors who handle sensitive unclassified DoD information, will need to achieve a specific CMMC-level certification to be eligible for contract awards.
What are the Steps Involved in CMMC Compliance Penetration Testing
CMMC compliance penetration testing steps start from defining the scope to getting the letter of attestation. Here are all eight steps:
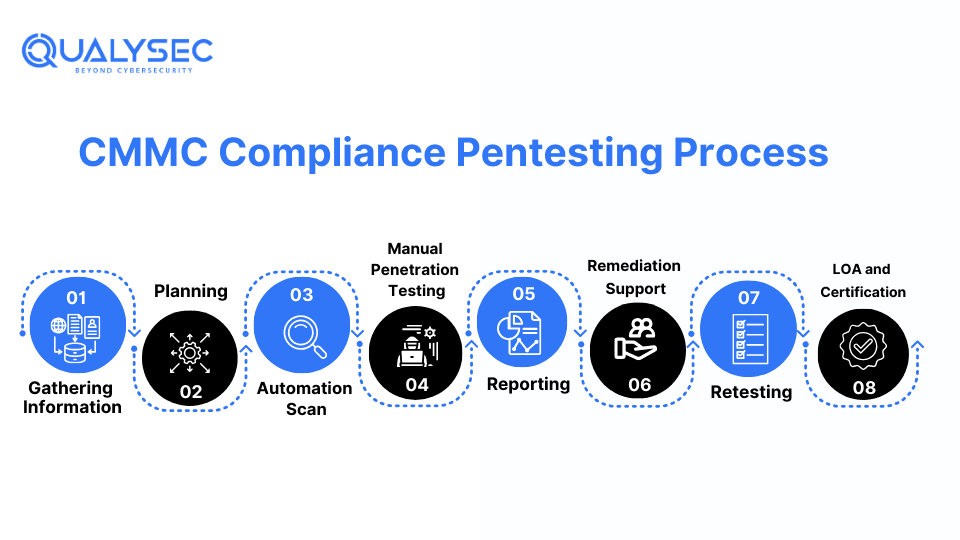
- Define scope: The first step involves defining what areas and vulnerabilities that are to be tested for CMMC compliance.
- Information Gathering: Then the testing team gathers as much information about the application or network that is to be tested.
- Automated Vulnerability Scanning: The testers first use automated vulnerability scanners to detect common vulnerabilities.
- Manual Penetration Testing: Then the testers use manual techniques to verify the scanner results and uncover hidden vulnerabilities.
- Reporting: All the findings of the test are documented in a detailed report that includes the total vulnerabilities identified, their impact, and suggested remediation methods.
- Remediation: The development team uses this report to fix all the identified vulnerabilities. If needed, the testing team will help them with remediation.
- Retest: The testing team will retest the application after remediation to verify the number of vulnerabilities fixed and those that were not fixed.
- Letter of Attestation (LoA): Finally, the testing company will issue a LoA, which is the summary of the entire pen test. This document helps with the CMMC compliance.
Want to see a real-world pen test report? Click the link below and download one right now!
Latest Penetration Testing Report

How to Choose the Right Penetration Testing Provider for CMMC Compliance?
Consider these factors before choosing the right penetration testing provider for CMMC compliance:
- Verify Experience: Look for pen test providers with experience in CMMC compliance and a strong track record in testing different digital assets, such as applications, APIs, networks, etc.
- Check Certifications: Ensure the provider has relevant certifications and expertise for CMMC compliance, such as certified ethical hackers or security experts.
- Assess Their Approach: Understand their testing methods and the tools they use to make sure they align with CMMC requirements.
- Review References: Check references or case studies to see how they’ve helped other businesses achieve CMMC compliance.
- Check for Smooth Communication: Choose a pen test provider who communicates clearly and provides detailed reports on their findings and remediation recommendations.
Conclusion
CMMC compliance pentesting is important for businesses that want to work with the Department of Defense (DoD). CMMC compliance requires the vendor/contractor to have adequate security measures in their systems to protect sensitive Federal Contract Information (FCI) or Controlled Unclassified Information (CUI).
Penetration testing is the best process to find vulnerabilities present in the systems and make necessary security patches. Additionally, regular pentesting helps maintain CMMC compliance and protects the data against breaches.
Choose Qualysec to get the best pen test experience and accurate results that will help you achieve CMMC compliance easily. Click the link below and talk to our security expert now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
FAQs
Q: What is CMMC?
A: Cybersecurity Maturity Model Certification (CMMC) is a U.S. Department of Defense (DoD) program that requires a contractor to have adequate security measures to protect sensitive information.
Q: Why is CMMC Compliance important?
A: CMMC compliance is important to work with the U.S. Department of Defense (DoD) and protect sensitive Federal Contract Information (FCI) or Controlled Unclassified Information (CUI).
Q: What is the difference between ISO 27001 and CMMC?
A: CMMC focuses more on protection controlled unclassified information (CUI) that belongs to the US government, residing in your system. However, with ISO 27001, the organization selects controls based on risk management and risk assessment.
Q: What are the benefits of CMMC Compliance Penetration Testing?
A: There are several benefits of CMMC compliance penetration testing, such as:
- Fulfill CMMC compliance requirements
- Become eligible to work with the US DoD
- Protect sensitive government information
- Enhance your own security measures
- Gain the trust of customers, partners, and stakeholders






























































































































































































































































































































































































































































































































0 Comments