Depending on the security needs and the service provider, a vulnerability assessment cost ranges between & $1,000 to $5,000 per assessment. However, this can vary quite a bit as there are several factors involved. Since the frequency of cyberattacks has significantly increased in the past few years, the demand for vulnerability assessment and penetration testing has also increased.
4 out of 5 companies are now performing penetration testing on their software as their vulnerability assessment. These companies care about their digital assets and want them safe from cyber threats. While the rest are still vulnerable to various cyberattacks.
In this blog, we are going to discuss what are the factors affecting vulnerability assessment cost and how one can choose the best vulnerability assessment service provider.
What is Vulnerability Assessment?
Vulnerability assessment is a testing process that identifies as many security defects as possible in applications, networks, and other digital systems. It also helps determine the severity level of the found vulnerabilities along with solutions to fix them.
Vulnerability assessment usually involves automated scanning tools and manual testing techniques to identify security weaknesses. Organizations of any size or individuals who face constant cyberattacks can benefit from vulnerability assessments. However, large organizations or enterprises that store huge amounts of user data will benefit most from this security analysis.
Factors Influencing the Vulnerability Assessment Pricing
By knowing the factors that influence the vulnerability assessment cost, organizations can allocate their budget effectively. Here are the four crucial factors that affect the cost of vulnerability assessments:
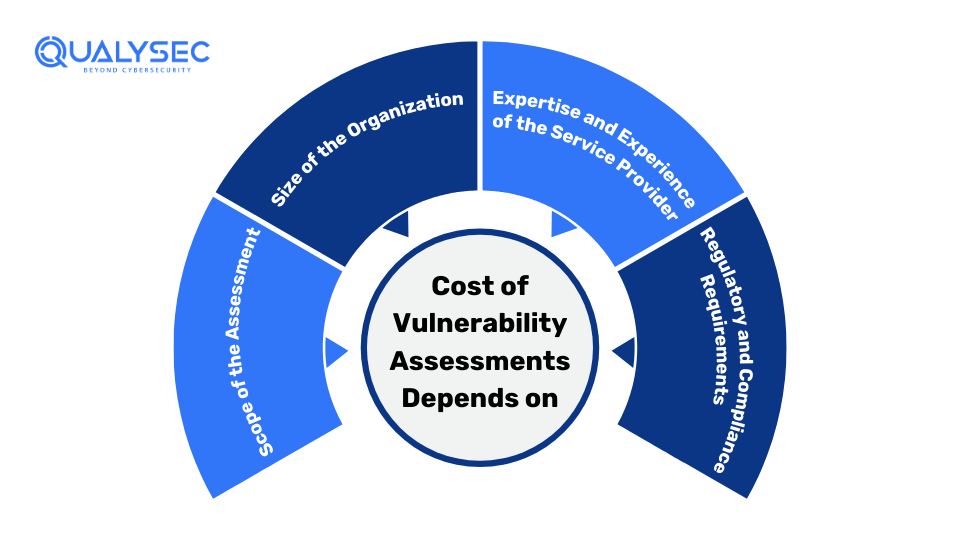
1. Scope of the Assessment
A comprehensive assessment that covers all aspects of an organization’s IT infrastructure, such as applications, networks, and databases, will naturally cost more than assessing just a single system or application.
The more extensive the assessment is, the more time, resources, and expertise it requires. Additionally, the depth of the assessment, for example, whether it includes advanced testing techniques like penetration testing or just automated vulnerability scanning, also impacts the cost. Organizations need to design their assessment’s scope to get accurate cost estimates.
2. Size of the Organization
Larger organizations or enterprises have more complex and extensive IT infrastructure, which requires more resources and time to assess thoroughly. This includes large numbers of applications, networks, and devices to evaluate.
On the other hand, smaller organizations or startups have fewer complex systems, which may incur low costs due to less scope. Additionally, larger organizations may need more frequent vulnerability assessments to ensure better security, which can further increase the vulnerability scan cost.
3. Expertise and Experience of the Service Provider
Highly experienced vulnerability assessment service providers with specialized skills often charge more fees due to their ability to offer in-depth and accurate assessments. Their advanced knowledge can detect vulnerabilities that less experienced providers might not determine.
Furthermore, experienced providers may also provide additional services such as actionable and detailed remediation plans and ongoing support. This may add value to the assessment but increases the cost. Organizations should be prepared for associated costs if they hire top-tier professionals.
4. Regulatory and Compliance Requirements
Certain industries, such as healthcare, finance, or government sectors make it mandatory for organizations to follow their security standards. This means adhering to rules like PCI DSS, HIPAA, or GDPR. To achieve these regulations, organizations need to perform regular vulnerability assessments.
To comply with these requirements, one needs specialized assessments, detailed reporting, and sometimes third-party security audits. As a result, it increases the cost. Additionally, not complying can result in significant fines, which makes regular assessments a necessary expense. The more complex the compliance landscape, the higher the average cost of vulnerability assessment.
Want to see what a vulnerability assessment report looks like? Tap the link below and download a free sample report right now!
Latest Penetration Testing Report

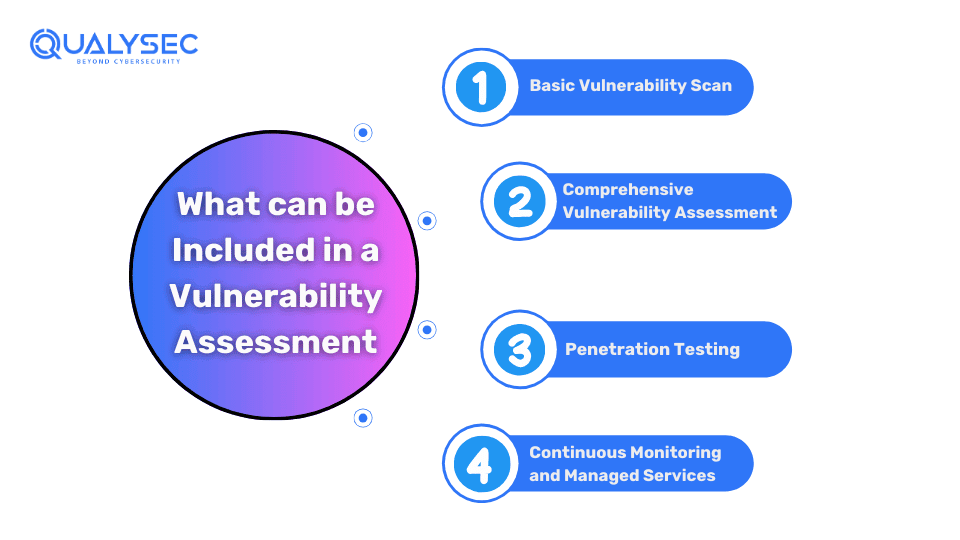
Cost Breakdown of Vulnerability Assessments in 2024
Organizations need to know where exactly the vulnerability assessment cost is associated to have a clear picture. Here are four areas that are linked to vulnerability assessment:
1. Basic Vulnerability Scan
A basic vulnerability scan helps identify common/known vulnerabilities in an organization’s network, systems, and applications. It is typically automated and provides a snapshot of potential security issues. The cost for this type of assessment is relatively low compared to more comprehensive services, as it requires less time and expertise.
Basic scans are suitable for smaller organizations or those with limited budgets. They offer a starting point for improving security but may not identify deeper, more complex vulnerabilities that require manual testing and more advanced techniques.
2. Comprehensive Vulnerability Assessment
A comprehensive vulnerability assessment includes both automated scans and manual testing techniques to identify a broader range of vulnerabilities. This assessment covers networks, applications, databases, and other critical systems, providing a thorough evaluation of the security posture and overall vulnerability management.
The cost is higher than a basic scan due to the extensive scope and the involvement of security professionals who analyze the findings and recommend remediation steps. This type of assessment is essential for medium to large organizations or those with complex IT environments.
3. Penetration Testing
Penetration testing, or pen testing, involves simulating real attacks to identify vulnerabilities that could be exploited by malicious actors. This assessment is highly detailed and requires skilled security professionals (called ethical hackers) to perform both automated and manual tests. Pen testers attempt to breach security defenses using various techniques that mimic real-world attack scenarios.
The cost is higher than both basic scans and comprehensive assessments due to the intensive nature of the assessment and the expertise required. Penetration testing provides a realistic view of an organization’s security weaknesses, making it crucial for high-risk environments and industries looking to enhance their security measures.
4. Continuous Monitoring and Managed Services
Continuous monitoring and managed services provide ongoing security to detect and respond to vulnerabilities in real-time. This service includes regular vulnerability scans, security assessments, and active monitoring of systems and networks. The cost is typically higher due to the continuous service and the resources involved.
Managed services often include incident response, threat intelligence, and compliance management, which offer a comprehensive security solution. This option is ideal for organizations that want proactive security measures, ensuring they can quickly address emerging threats and maintain a strong security posture year-round.
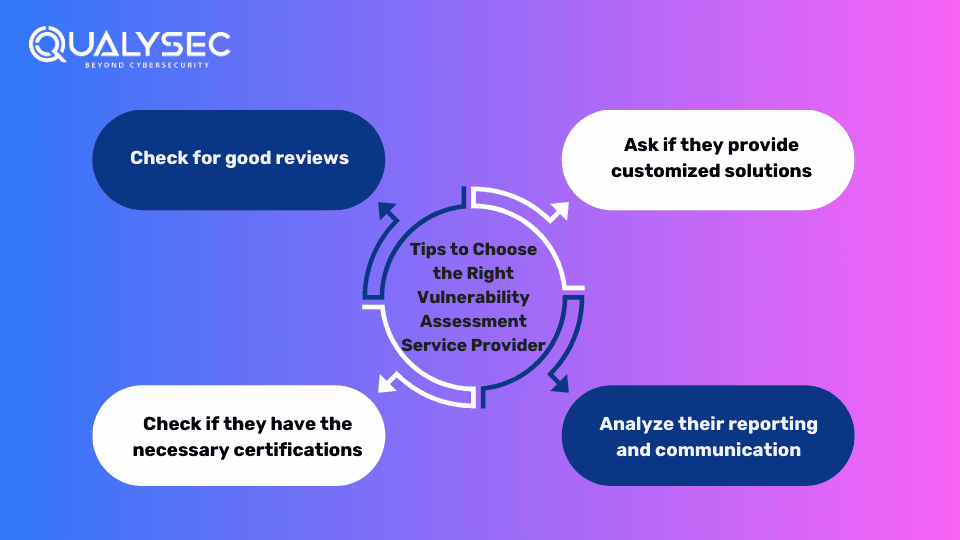
How To Choose the Right Vulnerability Assessment Service Provider
The right vulnerability assessment provider can help identify and mitigate potential risks effectively. Organizations should use the tips given below to find a provider that suits their security needs the best:
1. Reputation and Reviews
When choosing a vulnerability assessment service provider, start by researching their reputation and reading reviews from other clients. A provider with a strong reputation is more likely to offer reliable and effective services. Look for testimonials and case studies on their website and check independent review platforms for genuine feedback.
Positive reviews and a solid track record in the industry indicate that the provider has successfully helped other organizations enhance their security. Additionally, consider reaching out to past clients for their experiences. This information will give you confidence in the provider’s ability to meet your security needs.
2. Certifications and Expertise
Ensure the provider’s team has relevant certifications, such as CISSP, CEH, or OSCP, which demonstrate their knowledge and expertise in cybersecurity. A provider with certified experts is better equipped to identify and address complex vulnerabilities.
Additionally, look for a provider with extensive experience in your industry, as they will understand the specific security challenges you face. A well-qualified team can offer more accurate vulnerability scanning services and effective remediation strategies. This will provide peace of mind that your organization’s security is in capable hands.
3. Customized Solutions
Avoid providers that use a one-size-fits-all approach, as your security requirements may differ significantly from other organizations. The provider should be willing to understand your specific environment, goals, and challenges, and develop a tailored assessment plan accordingly.
Customized solutions ensure that the assessment is comprehensive and relevant, which addresses all critical areas of your IT infrastructure. This personalized approach provides more effective vulnerability identification and remediation, ultimately enhancing your organization’s overall security posture.
4. Transparency and Communication
The provider should clearly explain their assessment process, findings, and recommendations. Regular updates and open communication help you stay informed about the progress and any issues that arise during the assessment. A transparent provider will provide detailed reports that are easy to understand, and outline found vulnerabilities, their potential impact, and suggested remediation steps.
Effective communication ensures that you are fully aware of your organization’s security status and can make informed decisions. Choosing a vulnerability scanning and pen testing service provider that values transparency and maintains open lines of communication creates a trustworthy and collaborative partnership.
Want to conduct top-notch vulnerability assessments at the best price? Choose Qualysec for your security needs! We are a leading vulnerability assessment and penetration testing (VAPT) service provider that has helped over 110 clients secure more than 450 applications. Talk to our cybersecurity expert now for your needs!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
It is important to know that cost is not the only factor in vulnerability assessments. Factors like organization size and scope of the assessment also hold significant roles in determining the effectiveness of assessments.
The vulnerability assessment cost also depends on the type of services you choose (whether only scanning or manual testing) and the compliance needs. You need to select the right provider by researching them thoroughly. With cyber threats evolving rapidly, organizations must take active steps to keep their digital assets safe.
FAQs
Q: How much should a vulnerability assessment cost?
A: A vulnerability assessment should cost between USD 1,000 – USD 5,000. However, this price may vary depending on the complexity of the target system and assessment needs.
Q: How much does a cyber security risk assessment cost?
A: Based on the complexity of the system, a cyber security risk assessment should cost $5,000 to $50,000 in the US market. Moreover, the deeper the assessment, the higher the cost, but it will also result in a better security posture.
Q: How much does pen testing cost?
A: Usually, pen testing costs a company $1,000 – $5,000 for a simple application. But this price changes if the application or system is more complex and requires multiple testing services.














![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)
































































































































































































































































































































































































































































































0 Comments