iOS application penetration testing helps app manufacturers of iOS platforms find security vulnerabilities and enhance their security. iOS is one of the most popular operating systems in the world and has a reputation for being safe for its users. However, with technological advancement and attackers getting more skilled, new vulnerabilities are arising in iOS applications.
As per security research, 76 popular iPhone apps (widely used by users) were found vulnerable to data interception attacks. Since these apps are downloaded by millions worldwide, just imagine the scale of data breaches and losses in the event of a successful attack.
With that being said, regular penetration testing can help iOS app manufacturers prevent untimely attacks. In this blog, you are going to learn more about iOS application penetration testing, its many benefits, and how it is done.
What is iOS Penetration Testing?
iOS penetration testing simulates real attacks on iOS apps to check their security and identify vulnerabilities. Attackers exploit these vulnerabilities to get into the app’s architecture either to steal data or manipulate functions.
In iOS penetration testing, the testers evaluate the application’s design, code, configurations, and implementation to identify security flaws. Though Apple’s security structure is one of the best, it is still hackable. Regular pen tests can ensure you stay miles ahead of cyber threats that can harm your apps, and eventually your Apple device.
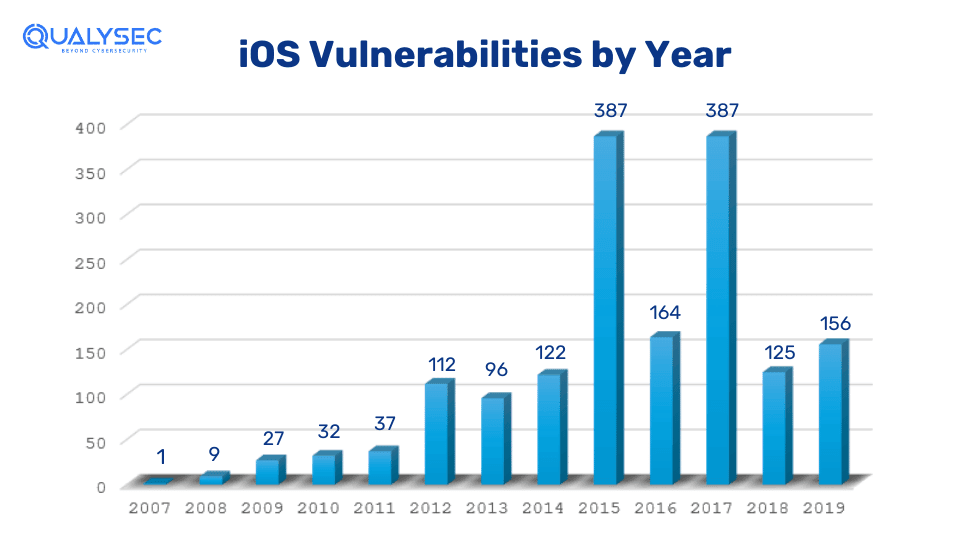
Importance of iOS Application Penetration Testing
The purpose of iOS app penetration testing is to reveal potential vulnerabilities in iOS applications and address them before attackers get hold of them. The process includes using automated tools and extensive manual penetration testing techniques.
Insecure iOS applications are dangerous for developers and users alike since data leaks can potentially harm both. This is especially true for iOS as the increased popularity of Apple devices (iPhones, iPads, Apple Watch, etc.) has lured attackers to breach their security for sensitive information.
Benefits of iOS Application Penetration Testing
iOS penetration testing helps you find those vulnerabilities that can lead to potential cyberattacks. Along with this, the ios security testing process offers more benefits for the iOS ecosystem, such as:
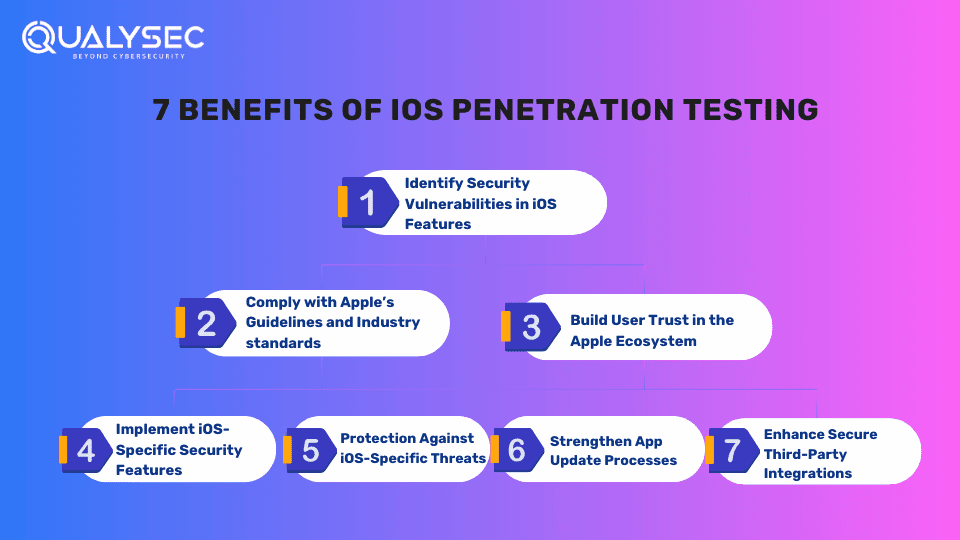
1. Identify Security Vulnerabilities in iOS Features
iOS application penetration testing or iPhone pentesting helps discover security vulnerabilities specific to iOS features, such as Touch ID, Face ID, and secure enclave. By identifying these weaknesses early, developers can promptly address them before they are exploited.
2. Comply with Apple’s Guidelines and Industry standards
Penetration testing ensures iOS apps comply with Apple’s strict security guidelines and App Store requirements. Adhering to these guidelines ensures the app is approved and remains in the App Store. This compliance not only creates a smoother review process but also assures users that the app meets the security standards set by Apple.
Additionally, many industries have strict security laws for apps that store user data, such as PCI DSS, HIPAA, ISO 27001, etc. Not complying with these requirements can lead to legal problems and fines. Penetration testing helps ensure these compliance needs are met with ease.
3. Build User Trust in the Apple Ecosystem
Apple boasts about its high-quality security standards and a cyberattack can break this trust. Users are more likely to download and use apps that they believe are secure, and penetration testing can help them gain this trust. Additionally, by demonstrating that you value user data safety, you can retain more users, maintaining a reputation within the Apple community.
4. Implement iOS-Specific Security Features
iOS apps often use platform-specific security features like App Transport Security (ATS) and Keychain services. Penetration testing checks if these features are properly implemented or not. By securing network communication and data storage, iOS application penetration testing prevents unauthorized access and secures users’ sensitive information.
5. Protection Against Specific Threats
iOS applications might face specific threats, such as iOS trustjacking, iOS single app mode escape, and XNU arbitrary code execution. Penetration testing uncovers vulnerabilities that can be exploited by these attacking methods. Additionally, developers can secure their apps in a better way from unauthorized modifications and intellectual property theft.
6. Strengthen App Update Processes
Penetration testing also identifies vulnerabilities in the app update process. This ensures that app updates do not introduce new security threats. By securing the update process, developers can ensure that new features and patches are safe for the users. As a result, it maintains the app’s security over time, keeping it resilient against emerging threats.
7. Enhance Secure Third-Party Integrations
iOS apps often integrate with APIs and third-party services. These integrations sometimes bring new vulnerabilities that can directly affect the app’s performance and expose it to cyberattacks. By thoroughly testing the app, developers can ensure these third-party integrations do not introduce security vulnerabilities.

What are the Steps of iOS Pentesting
iOS pentesting is a bit more complicated than Android pentesting due to the complex architecture of iOS apps. However, the basic process remains the same.
- Information Gathering: The testing team gathers as much information as possible about the iOS app that’s being tested. This helps them know more about the app’s architecture and plan accordingly.
- Planning/Scoping: The testers then define the scope of the pen test. This includes the vulnerabilities they are going to target, the tools they are going to use, etc.
- Automated Vulnerability Scanning: 1st the testers will use automated scanners to find vulnerabilities present in the app. This is a quick and effective way to find known security weaknesses.
- Manual Penetration Testing: Then the testers use their human expertise and techniques to manually identify and exploit vulnerabilities. This additionally helps in finding vulnerabilities missed by the tools.
- Reporting: The findings of the pen test are documented in a report. It includes the vulnerabilities found, their impact level, and actionable recommendations for remediation.
- Remediation: The report is shared with the development team, which they use to address the vulnerabilities found. If they need to, the testing team may help them locate the vulnerabilities.
- Retest: After remediation, the testers will retest the app to check whether the remediation patches were successfully added or not. Then they provide a final report containing the summary of the test.
- LoA/Security Certificate: Finally, the testing team will issue a letter of attestation (LoA), which proves that you have successfully performed penetration testing. This certificate is used to showcase shareholders and for compliance needs.
Would you like to see a real iOS penetration testing report? Click the link below and download a sample report that belongs to one of our existing clients!
Latest Penetration Testing Report

Choosing the Best iOS Application Penetration Testing Company
When it comes to protecting iOS apps from cyber threats, choosing the right penetration company is key. Here’s what to look for when picking a team that knows about Apple’s security, APP Store rules, and all the tricks attackers might try.
1. Experience and Expertise
Look for a testing company with extensive experience and expertise in iOS penetration testing. Check if they have previously tested similar apps in their track record. Experienced testers are more likely to identify potential vulnerabilities effectively.
2. Certifications and Credentials
Choose a testing company that has certified pen testers or ethical hackers with relevant credentials. Common certifications include Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and Certified Information Systems Security Professional (CISSP). These certificates ensure that the tester is trained and adheres to industry best practices.
3. Comprehensive Testing Methods
Since iOS pentesting not only includes testing the app code but also the network and APIs, ensure the testing company uses comprehensive testing methods that cover all aspects of iOS application security. This may include network security, static and dynamic analysis, and testing for iOS-specific vulnerabilities.
4. Detailed Reporting and Retest
The iOS app penetration testing company should provide detailed reports that should outline the vulnerabilities found, their severity, and recommendations for remediation. Additionally, they should be willing to retest the app to check whether the remediation patches were successful and there are no remaining vulnerabilities.
5. Client Reviews and References
Ask for references and check client reviews of the testing company before you jump to conclusions. Testimonials and feedback will give you a sneak peek into how the company operates. Speaking with previous clients of the company can provide valuable insights into how the company resolves security issues in iOS applications.
Want to protect your iOS apps from emerging cyber threats? Perform iOS application penetration testing with Qualysec Technologies. We follow a process-based testing approach where we use both automated scanners and manual testing techniques. We have worked with over 110 clients some of which are among Fortune 500. Click the link below and talk to our penetration testing expert now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Top 5 iOS Penetration Testing Tools
While there is a range of iOS penetration Testing Tools available, these 5 are the most used ones by penetration Testers:
- MobSF: Mobile Security Framework (MobSF) is an all-in-one tool for automated security testing of iOS applications. It provided detailed analysis and vulnerability reports.
- iMAS: iMAS offers various open-source tools for securing and testing iOS applications to ensure they are resilient against various security threats.
- Cydia: Cydia is a package manager for jailbroken iOS devices that allows users to install apps and tools not available on the App Store. It is very useful for security testing.
- Frida: Frida is a dynamic instrumentation toolkit used for debugging and testing iOS applications. It helps security researchers understand app behavior in real-time.
- Burp Suite: It is a powerful vulnerability scanner that can be used to test iOS applications by intercepting and analyzing network traffic to find security issues.
Conclusion
iOS application penetration testing is a crucial part of cybersecurity that helps secure apps from emerging cyber threats. By conducting regular penetration tests, developers can identify and address potential security flaws. Along with that ensure their apps remain secure and comply with industry regulations. Since the number of Apple users is increasing exponentially, so does the iOS-specific vulnerabilities. Regular iOS penetration testing is now not a luxury but a need.
FAQs
Q: How are iOS apps tested?
A: Penetration testers or ethical hackers test the iOS app’s design, code, configurations, and implementation to identify security vulnerabilities that can lead to cyberattacks.
Q: Why is iOS Penetration testing necessary?
A: iOS penetration is necessary to find and fix vulnerabilities that could harm user data and system integrity on iOS devices. Additionally, it builds trust among shareholders and customers.
Q: What is the iOS penetration testing methodology?
A: The iOS penetration testing methodology has 8 crucial steps:
- Information gathering
- Planning/scoping
- Automated vulnerability scanning
- Manual penetration testing
- Reporting
- Remediation
- Retesting
- LoA or security certificate






























































































































































































































































































































































































































































































































0 Comments