Web application security involves the actions taken to safeguard web applications from dangers like data breaches, unauthorized access, and malicious attacks. It uses various methods and tools to protect the confidentiality, integrity, and availability of web application resources and data including Web Application Security Testing Checklist. The main features are the authentication mechanisms, the encryption protocols, the input validation, and the secure coding practices.
Besides, penetration testing and vulnerability scanning are used to detect and solve security vulnerabilities. Continuous monitoring, regular updates, and user awareness training are the keys to maintaining strong web application security as cyber threats evolve. In this blog, we are going to discuss the 10 best web application security testing checklists that every organization should consider.
Importance of Security Testing in Web Applications
Security testing is essential for web applications due to several reasons:
1. Risk Mitigation:
Web application security testing is crucial for identifying and mitigating the flaws and weaknesses that cybercriminals can exploit. By detecting these issues early in the development process, teams can eliminate the risks and prevent security breaches that could potentially lead to data theft, financial loss, or reputational damage. Not conducting such testing leaves your web applications vulnerable to these threats.
2. Compliance Requirements:
Many industries and jurisdictions have regulations requiring security measures for web applications, such as GDPR in Europe and HIPAA in the healthcare sector. These regulations often mandate the implementation of specific security controls and regular testing of these controls. Security testing ensures that web applications comply with these standards by identifying and addressing any security vulnerabilities. By doing so, fines and legal penalties for non-compliance can be avoided.
3. User Trust and Reputation:
Users expect their personal information to be protected when using web applications. Security breaches can lead to the loss of trust and reputation of an organization. Through security testing, businesses not only ensure the security of user data but also demonstrate their dedication to protecting user data. This commitment to security can help build trust and a good reputation among users.
4. Cost Savings:
Addressing security issues early in the development lifecycle is significantly more cost-effective than dealing with them after deployment. Security testing is a proactive method of identifying vulnerabilities before they are exploited, thereby reducing the potential costs of security breaches, such as regulatory fines, legal fees, and revenue loss. By prioritizing security testing, you can save significant costs in the long run, making it a wise investment.
5. Continuous Improvement:
Security testing is not a one-time activity but a continuous process. It involves the constant evaluation of the security posture of web applications, enabling organizations to stay on top of new threats and changing attack vectors. By integrating Web Application Security Testing Checklist into the development process, teams can keep upgrading their web applications’ security and fit in with the ever-changing security landscape. This ‘continuous improvement’ approach ensures that your web applications are always one step ahead of potential threats.
Do you want to protect your web app against cyber threats? Connect with experts at QualySec, who offer innovative application security testing services. Our comprehensive approach includes penetration testing, vulnerability scanning, and continuous monitoring to ensure the highest level of security for your digital assets. Secure your digital assets now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Common Web Application Security Threats
Some of the common web application security threats are:
1. SQL Injection (SQLi):
This is when an attacker enters the malicious SQL code into the input fields, which the database executes. Thus, this can cause unauthorized access to sensitive data, data manipulation, and, in some instances, total control over the database.
2. Cross-site Scripting (XSS):
XSS is a technique that involves the injection of malicious scripts into web pages viewed by other users. These scripts can take over user sessions, deface websites, steal cookies, and do other malicious things.
3. Cross-site Request Forgery (CSRF):
CSRF takes advantage of a site’s trust in a user’s browser. Attackers make users do things on a website without their agreement by abusing the fact that the site trusts requests from the user’s browser.
4. Insecure Direct Object References (IDOR):
This weakness is caused by an application exposing its internal implementation objects, like files, directories, or database keys, to users. Attackers can manipulate these references to get unapproved data or do unauthorized actions.
5. Remote Code Execution (RCE):
RCE gives attackers the ability to run any code on a targeted system. This can result in total compromise of the system, including data theft, unauthorized access, and further exploitation.
6. Insufficient Logging and Monitoring:
This is when an application does not adequately record security-related events or cannot monitor the activities to reveal suspicious ones.
7. Insecure Cryptographic Storage:
This means keeping confidential information like passwords or payment card details in a way that is not secure, such as using a weak encryption algorithm or storing plaintext passwords.
8. Failure to Restrict URL Access:
Applications usually show URLs to third parties that can get into the sensitive data. It is necessary to authenticate and authorize the users before they are allowed to access these URLs. Failing to do this can lead to unauthorized access to sensitive information.
9. Cross-Origin Resource Sharing (CORS) Misconfiguration:
CORS is a security characteristic that regulates how web applications can access the resources of other domains. The mistakes in the setup of CORS policies can result in security gaps like data leakage or access to resources without authorizations.
10. Using Components with Known Vulnerabilities:
Numerous applications are based on third-party libraries, frameworks, or components. The components that are not regularly updated with security patches will be the ones targeted by the attackers, and thus compromise the application.
Web Application Security Testing Checklist
The comprehensive web application security testing checklist is as follows:
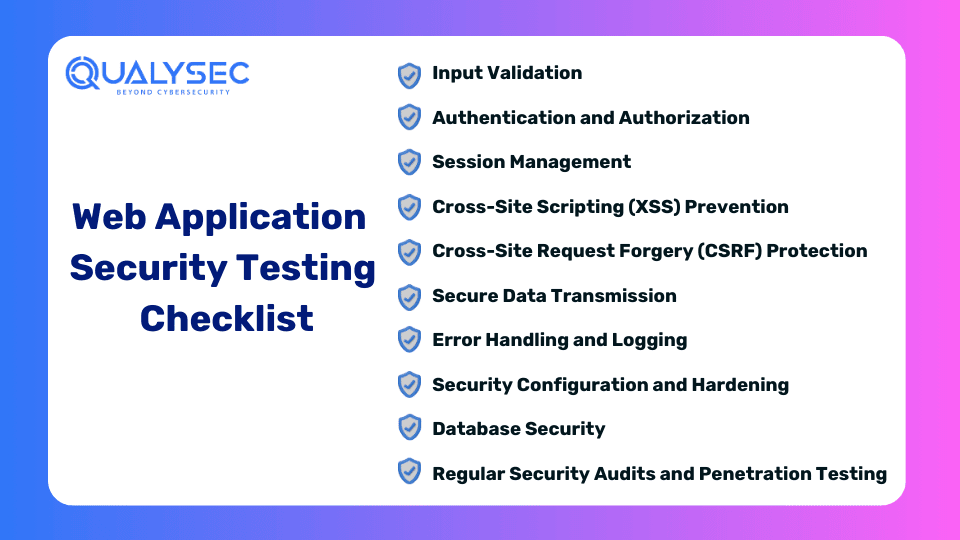
1. Input Validation:
-
- Check every input field for validation on both the client and server to prevent any injection attacks such as SQL injection, XSS, etc.
-
- Parameterized queries for the database communication are a way of ensuring they will work.
-
- Validate file uploads to avoid and, hence, prevent malicious file uploads.
2. Authentication and Authorization:
-
- Apply vital parameters hashing algorithms such as bcrypt.
-
- Introducing multi-factor authentication (MFA) for sensitive operations is a must.
-
- Check and revise the access control periodically to make sure the least privilege is being followed.
3. Session Management:
-
- Follow secure session management techniques such as random session IDs, expiration, etc.
-
- Create some methodologies to stop session fixation and session hijacking.
-
- Seek the means of storing session data securely and refrain from using client-side storage for sensitive information.
4. Cross-Site Scripting (XSS) Prevention:
-
- To tackle XSS attacks, the Content Security Policy (CSP) must be implemented.
-
- Clean the content created by the user and remove any harmful scripts.
-
- Translate the output to be less XSS vulnerable when showing the user information.
5. Cross-Site Request Forgery (CSRF) Protection:
-
- The generation of anti-CSRF tokens is used to confirm the source of the requests.
-
- Usage of the Same Site attribute for cookies should be the strategy to avoid CSRF attacks.
-
- The same principle applies to AJAX requests; hence, the CSRF protection should also be incorporated.
6. Secure Data Transmission:
-
- Employ HTTPS with TLS to maintain the security of communication.
-
- Don’t use SenderIDs in URLs to send sensitive data.
-
- Set the HTTP security headers such as Strict-Transport-Security (HSTS), X-Frame-Options, etc.
7. Error Handling and Logging:
-
- Not showing detailed error messages to users in production environments is good advice.
-
- The logged security-related events are just for the security show and to enable the incident response.
-
- Dredge up the logs occasionally and check for any suspicious activities.
8. Security Configuration and Hardening:
-
- There is a need to turn off the services and features that are not required.
-
- Staying with the latest software and libraries while fixing the security holes as soon as they are created is the best way to ensure the safety of the information.
-
- Join the security best practices for server and database configurations, and you will accomplish the goal.
9. Database Security:
-
- Limit the database access privileges to the minimum required by a particular user or group.
-
- The routine backup and encryption of sensitive data at rest is one of the common issues in the project.
-
- By applying encryptions, which protect the databases connecting via TLS and the robust authentication system, the database’s security is the highest, which is especially needed in the domain of financial and online banking systems.
10. Regular Security Audits and Penetration Testing:
-
- Organizations often conduct security audits to discover and fix weaknesses.
-
- Carry out penetration testing, which is the imitation of actual attacks to check the security of the web application.
-
- Be up-to-date on the latest threats and then amend security protocols accordingly.
Want to see how a penetration testing report helps with web app security? click the link below and find out!
Latest Penetration Testing Report

Conclusion
Protecting web applications through systematic security testing, including the use of a Web Application Security Testing Checklist, is the top priority in the current digital world. Through the early detection and fixing of flaws in authentication, session management, data transmission, and other possible areas, organizations can minimize the chances of data breaches and, at the same time, adhere to the regulations. In addition, focusing on continuous improvement with regular audits and penetration testing is a way to be resilient against evolving cyber threats.
By following the web application security best practices comprehensively and creating a culture of vigilance, businesses protect the user’s trust and reputation and get substantial cost savings in the future. Adopting strong security measures is not only a requirement but also a strategic need to ensure the security and availability of web applications in a constantly changing threat environment.
FAQs
Q. Which tool is used to test the security of web applications?
A. Web application security testing is usually done with the help of tools like OWASP ZAP (Zed Attack Proxy), Burp Suite, or Acunetix. These tools help detect vulnerabilities such as SQL injection, cross-site scripting (XSS), and more.
Q. How do you ensure web application security?
A. Web application security is ensured by input validation, secure coding, regular security audits, HTTPS, access controls, protection against common vulnerabilities like XSS and SQL injection, and keeping up with patches and security updates.
Q. Why security is essential in web applications?
A. Security in web applications is essential to protect sensitive data, prevent unauthorized access, and shield against cyber threats. It guarantees the security, privacy, and accessibility of information, thus building user confidence and compliance with the regulations.
































































































































































































































































































































































































































































































































0 Comments