One of the major risks businesses are facing worldwide is hackers exploiting vulnerabilities that exist in their IT infrastructure. As technology and interconnectivity are growing, the landscape of cyber threats is also growing. To avoid hackers getting inside your internal network and using it for their gain, businesses need to perform regular security penetration testing.
Penetration testing is where cybersecurity professionals use a hacker-style approach to find vulnerabilities that could lead to various cyberattacks. Cybercrimes have increased a whopping 600% since the beginning of the pandemic, which is why 85% of the US and European organizations have increased their penetration testing budgets.
In this blog, we will learn about security penetration testing, what are its types, and why it is important for businesses globally.
What is Security Penetration Testing?
Security penetration testing or pentesting is the process of strategically hacking into your system or network to identify as many vulnerabilities as possible. Cybersecurity professionals or ethical hackers perform these tests with the full authorization of the client.
Penetration testers use various tools and techniques to test the security measures of your IT infrastructure and check weak points through which real hackers can enter. After the testing, they generate a report on the vulnerabilities they found and the steps to fix them. In fact, in some cases, they offer advice to the developers in the fixing process.
Security testing services has been around since the 90s, but with the rise of connectivity recently, its need has grown exponentially. More and more businesses are conducting penetration testing as a major part of their cybersecurity.
Are you also worried about data breaches and hackers stealing your information? Click this link and our cybersecurity expert will contact you shortly!
https://qualysec.com/contact-us/
Importance of Security Testing Services
Protecting your organization and digital assets isn’t the only reason to conduct penetration testing. With regular pen tests, you can reduce cyber risk, protect customer data, satisfy client/stakeholder requirements, comply with industry regulations, and maintain the organization’s image and reputation. Security vulnerability testing is is essential for identifying and addressing potential weaknesses before they can be exploited by malicious actors.
Additionally, you should perform penetration testing if you:
-
- Suspect new security risks
- Develop or update a new company network or software
- Move your office or network, or relocate to a fully remote work environment
- Set up a new internal data storage location, or relocate existing data
- Were recently attacked by hackers
- Implement a new end-user policy or program
Benefits of Conducting Regular Security Penetration Testing
As per a recent global survey, 93% of organizations have faced at least one data breach in the past 3 years. If this isn’t a reason to conduct penetration testing, here are a few compelling reasons:
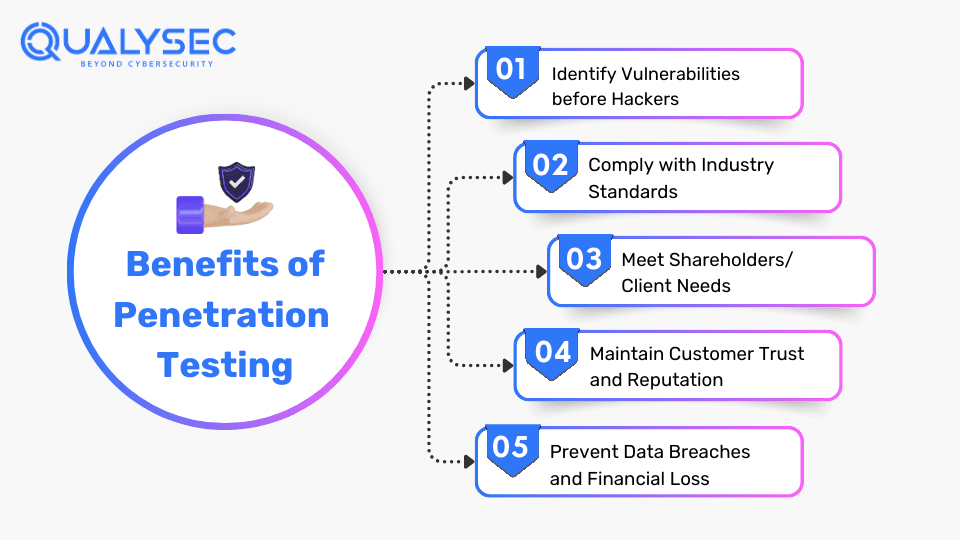
Identify Vulnerabilities before Hackers
Hackers or cybercriminals are always looking for ways to get inside your system. In fact, if they find just one vulnerability in your security measures, they can use it for unauthorized access and data theft. Security vulnerability testing helps you discover these vulnerabilities before they get into the hands of a hacker. As a result, you can promptly fix them before any significant damage is done.
Comply with Industry Standards
Many industries have made it mandatory for businesses to conduct security testing to protect customer data. These regulations include HIPAA, PCI DSS, SOC 2, GDPR, etc. However, many businesses don’t comply with these regulations and face legal penalties with huge fines. By conducting penetration testing, organizations can achieve these compliances and avoid consequences.
Meet Shareholders/Client Needs
Recently, most shareholders and clients have been demanding security testing certificates before they conduct business with you. This is because they want to ensure that their data and information are safe with you. With a penetration testing certificate, you can assure them that you have successfully conducted security testing on your products or services and that it is safe to do business with you. Additionally, having a pentest certificate will also attract more leads and clients.
Maintain Customer Trust and Reputation
Customers are sharing their confidential information with your website, for example, personal and financial details, and expect it to be secure. With the pentest certificate, you can assure them that their data is safe, additionally attracting more customers.
Once your business reputation is hampered, it is very difficult to gain the same trust. Even a single data breach or a small cyberattack can significantly damage your reputation in the industry. So, protect your business reputation by conducting regular cyber security penetration testing on your digital assets.
Prevent Data Breaches and Financial Loss
Hackers or cyber criminals who hack into your system mainly have two motives – steal sensitive data or finances. Every day some or other company is getting hacked and facing severe losses. Penetration testing will help you discover weak points through which hackers can enter your system. By fixing these issues, you can prevent data and financial loss.
Want to conduct penetration testing to secure your business? Click the link below and book an appointment. Our experts will be there with you shortly!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Types of Security Penetration Testing
There are several types of penetration testing that an organization performs as per their requirement, products, services, and needs. some of the most common and extensively required security penetration testing include:
Web Application Penetration Testing
Due to the huge expansion of web applications, more and more resources are being spent on developing this software. Additionally, regular configurations are being done so that they work seamlessly on new digital landscapes. However, this has opened up to an array of newfound cyber threats.
Considering that some web applications store confidential information, it is even more critical to secure them all the time. Hence, web application penetration testing. It secures your web apps by identifying vulnerabilities way early before hackers do it for their gain.
Mobile App Penetration Testing
The Apple Store and Google Play Store combinedly have over 6 million apps. Nearly every person on earth uses a mobile phone, with almost all of their personal and financial details stored in it. As a result, mobile apps are now the prime target for cybercriminals. The primary purpose of mobile app penetration testing is to enhance the app’s security and protect user data.
Network Penetration Testing
The primary goal of network penetration testing is to find vulnerabilities in an organization’s networks, servers, firewalls, and other network devices. Since all the devices and the internet are connected through a network, hacking them can help cybercriminals get inside a wide range of devices. Hence, organizations should make it a priority to conduct regular pen tests for their networks and related devices if they want to secure their business.
Cloud Penetration Testing
Cloud platforms like Microsoft Azure and Amazon Web Services (AWS) offer individuals and organizations the opportunity to store, innovate, and streamline business operations. If you are using cloud services, it is inevitable for you to perform cloud penetration testing if you want your cloud data to be secure. Additionally, it will help assess your cloud assets about how strong their defenses are against various security risks.
IoT Device Penetration Testing
Internet of Things (IoT) devices are a web of interconnected devices that communicate and exchange data via the Internet. For example, Amazon Alexa, Google Home, baby monitors, smart lighting, etc. These devices are mainly used in homes, businesses, and critical infrastructures, and store massive amounts of sensitive data. IoT penetration testing helps find any existing security flaws within these devices that hackers could use for data theft and other malicious activities.
Security Penetration Testing Process
While the security penetration testing process varies from company to company, the basic process remains the same.
Information gathering
Pen testers gather as much information about the testing area as possible.
Define goals
Testers set proper goals and aim for the outcome of the penetration test.
Automated scans
Testers use different types of automated Security testing tools to scan for vulnerabilities on the surface level.
Manual penetration testing
The testers manually test each part to find hidden vulnerabilities that hackers could exploit.
Reporting
They present an initial report that includes all the found vulnerabilities and steps to fix them.
Remediation
The testers help the developers of the company to fix the security issues.
Retest
The pen testers again test the It environment to check whether the remediation plans actually worked or not.
LOA and Certificate
Finally, they present the letter of attestation and a security certificate that proves the organization has completed penetration testing.
Never seen what a real penetration testing report looks like? Well, here’s your chance. Click the link below and download a sample report now!
Latest Penetration Testing Report

Conclusion
With cyber threats increasing at a rapid rate and hackers finding new ways to get inside your systems, cybersecurity is now more needed than ever. By identifying vulnerabilities before malicious actors exploit them, security penetration testing reduces the risk of data breaches and financial losses. Moreover, it ensures compliance with industry regulations, meets shareholder and client demands, and maintains trust among customers.
Various types of security testing, including web application, mobile app, network, cloud, and IoT device testing, cater to different aspects of cybersecurity, addressing the diverse needs of modern businesses. Through a structured testing process, from information gathering to remediation and retesting, organizations can enhance their defenses and obtain the assurance needed to navigate today’s complex digital landscape with confidence.
FAQs
Q: What is penetration test in security?
A: Penetration test in security is where cybersecurity professionals use a hacker-style approach to find vulnerabilities in the existing security in the IT infrastructure.
Q: What are the 3 types of penetration tests?
A: The main 3 types of penetration tests that vary based on information provided to the testers are:
-
- Black box pentesting
- White box pentesting
- Gray box pentesting
Q: Why is penetration testing important?
A: Penetration testing is important to find weak points in applications or networks that hackers could exploit for their gain. Penetration testing can prevent data breaches, financial loss, and loss of reputation, and helps comply with industry standards.
































































































































































































































































































































































































































































































































0 Comments