A SOC Service or Security Operation Center is a team of highly qualified IT security professionals that protect an organization by monitoring, detecting, analyzing, and investigating various cyber threats. SOC service in cybersecurity refers to examining signs of security incidents in networks, operating systems, servers, endpoint devices, applications, and databases.
Additionally, SOC is a regulatory law governed by the American Institute of Certified Public Accountants (AICPA). Organizations need to comply with this law if they want to provide service to other organizations. This compliance is achieved by the organization by conducting a cybersecurity audit or penetration testing on the applications or networks.
| SOC Service improves the organization’s ability to prevent cyber threats by 43%. |
In this blog, we are going to discuss the benefits of SOC, the key functions of SOC, and how to choose providers of SOC as a service. We will explain how SOC helps protect your business from cyber threats and why it is important.
What is a Security Operations Center or SOC Service?
Simply put, the Security Operations Center (SOC) is a team of professionals who are responsible for the security of an organization’s critical assets like intellectual property, personnel data, business systems, and brand integrity. The SOC service team analyzes data feeds, sets rules, identifies anomalies, improves response strategies, and monitors emerging vulnerabilities in each environment.
Since modern technology systems in organizations run 24/7, SOCs usually function around the clock, sometimes taking the help of expert third-party security providers.
Before establishing a SOC, organizations should create a comprehensive cybersecurity strategy that aligns with their business goals and challenges. While many large organizations have an in-house SOC, others choose to outsource it to third-party managed security service providers.
What Does a SOC Do?
The main goal of the SOC is security monitoring and alerting. This includes gathering and analyzing data to detect suspicious activities and enhance the organization’s security. Threat data is collected from firewalls, intrusion detection and prevention systems, security information and event management (SIEM) systems, and threat intelligence sources. Alerts are sent to the SOC team as soon as any anomalies, unusual patterns, or other signs of compromise are identified.
Here is a detailed description of the role of a SOC in an organization:
- Asset Discovery: The SOC ensures all hardware, software, tools, and technologies that are used in the organization are thoroughly monitored for security incidents by acquiring deep awareness about them.
- Behavioral Monitoring: The SOC analyzes the technology infrastructure continuously for abnormalities. It uses both reactive and proactive measures to ensure irregular activities are promptly detected and addressed.
- Maintaining Activity Logs: The SOC team logs all activities and communications taken across the enterprise. These activity logs allow the SOC to trace and identify past actions that may have led to a security breach.
- Alert Ranking: All security incidents are not the same. Some incidents pose a bigger threat to the organization than others. The SOC ranks each incident based on its severity and prioritizes the most critical alerts.
- Incident Response: When a security compromise is detected, the SOC team executes incident response procedures to address the threat.
- Investigating Root Cause: after an incident, the SOC investigates when, how, and why it occurred. Using the log information, the SOC tracks the root cause of the problem and thus prevents future incidents.
- Compliance Management: The SOC team members follow the organizational policies, industry standards, and regulatory requirements to ensure compliance.
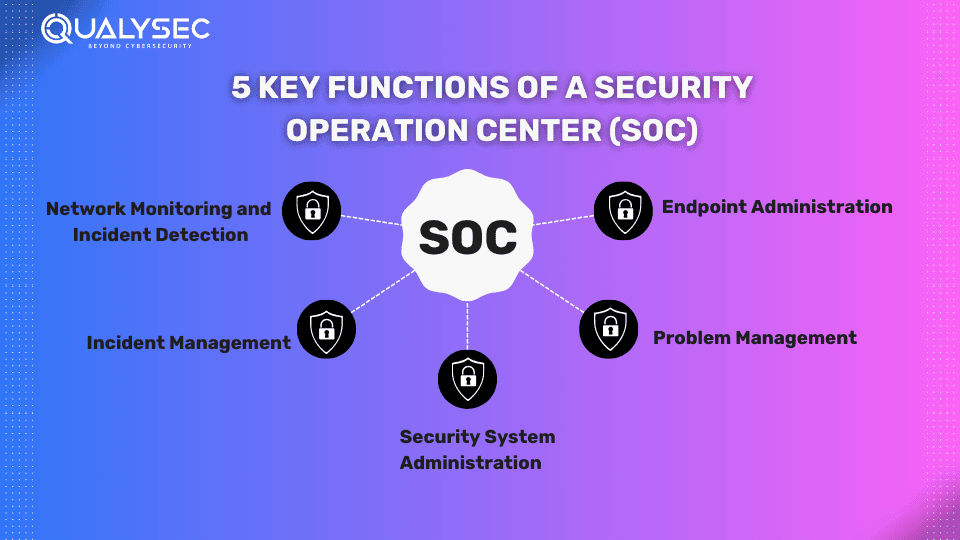
5 Key Functions of a Security Operation Center (SOC)
SOCs investigate and monitor all those systems and functions involved in the organization’s security. Here are the top 5 functions of a SOC:
1. Network Monitoring and Incident Detection
Network monitoring is done 24/7, detecting suspicious activity through security tools that watch network traffic and device activity. These tools may include:
- Antivirus
- Intrusion prevention systems (IPS)
- Data loss prevention systems (DLP)
- Security information and event management (SIEM) systems
If any unusual event log is detected, the SOC service team will be immediately alerted to respond and prioritize the incident. The incident is then treated as a part of normal operations or as a potential threat.
2. Incident Management
When an incident is identified, the SOC should follow a prescribed incident management process. This process typically involves:
- Documentation: Collecting information to understand the scope and type of the incident.
- Correct Action: Isolating or eliminating the risk to minimize the impact and prevent it from recurring.
- Investigation: Identifying the root cause to understand its source and implement necessary controls to close or limit security gaps.
- Closure: Ensuring the incident is properly documented and resolved, with updated processes or controls to prevent recurrence.
3. Problem Management
Problem management is a process of understanding and managing the root causes of incidents to prevent future problems. By using a structured approach, the SOC services should eliminate service-affecting issues and prevent problems before they occur. As a result, it helps the organization to continuously improve its security posture.
4. Endpoint Administration
This function offers a centralized, real-time view of enterprise devices and their security status. A SOC can use endpoint and infrastructure security tools to:
- Detect and prevent issues
- Administer devices remotely
- Deploy patches and updates
- Adjust configurations and rules
These operations ensure that enterprise devices remain up to date with security standards and stay ahead of evolving threats.
5. Security System Administration
This function involves collaborating with internal stakeholders, process owners, and third-party providers to implement and maintain security tools and ensure compliance. Key actions include:
- Updating and testing virus definitions and configurations.
- Testing and deploying new security controls and tools.
- Taking corrective actions based on firewall or IPS alerts.
What Are the Benefits of a SOC?
When implemented correctly, a SOC provides a wide range of benefits, such as:
- Continuous monitoring and analysis of system activity.
- Enhanced incident response.
- Faster detection of compromises.
- Reduced downtime.
- Centralized management of hardware and software assets for a holistic, real-time approach to infrastructure security.
- Improved collaboration and communication.
- Reduced direct and indirect costs related to managing cybersecurity incidents.
- Increased trust from employees and customers, making them more comfortable sharing confidential information.
- Greater control and transparency in security operations.
- A clear chain of control for systems and data is crucial for prosecuting cybercriminals effectively.
Top 8 SOC Challenges
As already mentioned, SOC members have a lot of responsibilities. Now we will mention the fundamental challenges SOC service teams face regularly:
1. Trouble with Assembling the Right Team
The SOC team’s biggest challenge is assembling a skilled team. The team contains various roles such as threat hunters, managers, engineers, and architects. Each position must be filled by appropriately skilled individuals to ensure effective operation.
2. Lack of DBA Support Services
Database Administration (DBA) support services manage and secure crucial databases. However, finding skilled experts in this field is challenging, limiting the pool of qualified candidates.
3. Increasing Security Alerts
The high number of security alerts can overwhelm analysts, risking the oversight of critical issues. SOC teams need to spend more time addressing both minor and major security concerns.
4. Budget Constraints
Companies often try to curb budgets, but cutting spending on cybersecurity is risky. Increasing investments in security is essential to protect against the growing threat of cyberattacks.
5. Cybersecurity Threats are Faster than Defenses
Cyber threats are increasing rapidly, with thousands of attacks occurring daily. Members of SOC service must monitor continuously to keep up. Additionally, including threat intelligence can help manage this issue.
6. Constant Upgradation
Technology must be updated regularly, with strategies and protocols frequently revised. This may require retraining staff to ensure they are prepared for new threats.
7. Choosing the Right Technology
Selecting the right technology, such as MDR, EDR, or SIEM, is crucial. The chosen technology should provide effective results and benefits, making it a worthy investment.
8. Maintaining Compliance
69% of security teams report that regulatory compliance is a significant part of their security budget. Compliance is crucial for SOCs, not only to avoid legal issues but also to show customers a commitment to security. One major challenge for SOC analysts is maintaining compliance while managing limited resources and budgets.
SOC Best Practices
A SOC team should perform these best practices for better organizational security:
1. Align Strategy with Organization Goals
It’s crucial to align security strategy with business goals. By prioritizing security efforts that support overall business objectives, organizations can protect customer data and maintain trust. For example, focusing on data security and privacy aligns to safeguard sensitive information and enhance overall security operations.
2. Use the Best Security Automation Tools
Utilizing advanced security automation tools streamlines threat detection and incident response. For instance, employing a robust SIEM system centralizes data analysis and facilitates efficient threat detection.
3. Implement Comprehensive Threat Intelligence and Machine Learning
Comprehensive threat intelligence and machine learning enhance analysis and response capabilities. AI technologies speed up decision-making and automate repetitive tasks, which then allows the SOC team to focus on complex security issues effectively.
4. Ensure Visibility Across the Entire Network
Complete visibility across the network enables proactive monitoring for suspicious activity and potential vulnerabilities. Network monitoring tools, combined with automation solutions such as SIEM, provide real-time insights and alerts to detect and respond to security breaches quickly.
5. Continuous Network Monitoring
Continuous network monitoring detects and responds to security incidents promptly, minimizing their impact. By establishing a baseline of regular network activity and regularly updating monitoring systems, the SOC team then maintains effective network security.
6. Address Vulnerabilities through Penetration Testing
Organizations can appoint third-party penetration testing firms to work with the SOC team to identify and address vulnerabilities present in the applications and networks. Look for a testing firm that provides both automated and manual penetration testing to get comprehensive vulnerability management.
Want manual and automated penetration testing services? Qualysec Technologies offers the best process-based penetration testing for organizations to find present vulnerabilities, along with complying with the SOC types 2 industry regulation. Click the link below and talk to our cybersecurity expert!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
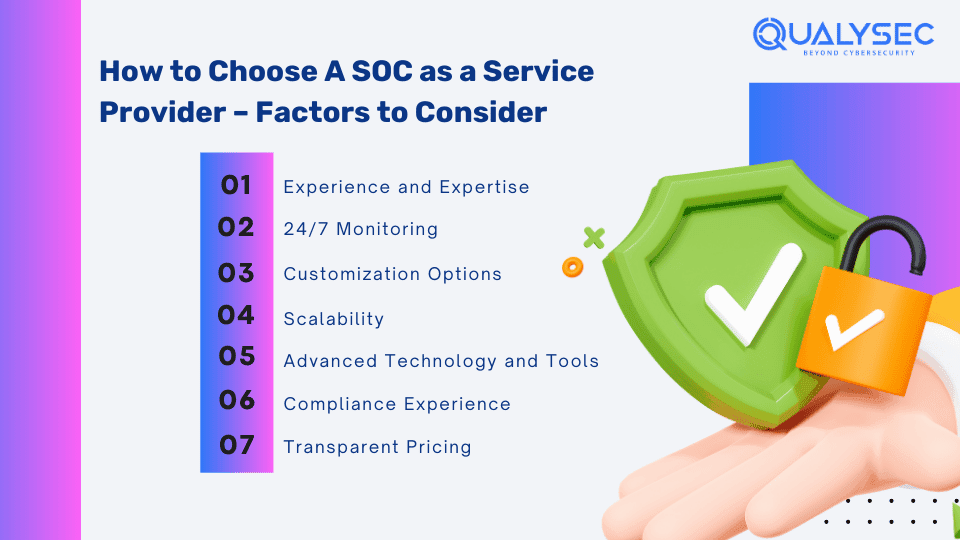
Factors to Consider When Choosing A SOC as a Service Provider
While organizations can have an in-house SOC team to manage their security, it can be often resource-intensive and expensive. A Security Operations Centre (SOC) as a Service (SOCaaS) is a third-party provider that has all the expertise and tools to check, detect, and respond to cyber threats. Here are a few factors to consider before you choose the right SOCaaS provider:
1. Experience and Expertise
Choose a SOC as a service provider with a proven track record in cybersecurity, equipped with skilled professionals updated on the latest threats and experienced in incident management. Ensure they understand your industry and size so that they offer tailored solutions for your unique needs.
2. 24/7 Monitoring
Select a SOCaaS provider that offers round-the-clock soc monitoring to quickly detect and respond to cyber threats. Their team should be capable of real-time incident response and also provide comprehensive reports and analysis.
3. Customization Options
Seek a provider capable of customizing services to your organization’s specific requirements. They should work with you to detect unique security risks and then create a plan that addresses your specific needs.
4. Scalability
Choose a SOC service provider that can scale its services as your business grows. Further, they should have the resources and ability to adapt to increase security incidents and meet your needs as you grow.
5. Advanced Technology and Tools
Ensure the SOC provider utilizes advanced technology and tools like SIEM for real-time data analysis and automated response capabilities for rapid threat detection and mitigation.
6. Compliance Experience
Go provider in managed SOC services that are experienced in compliance with industry standards like HIPAA, PCI DSS, and GDPR. Ensure they provide necessary reports and audits for regulatory adherence.
7. Transparent Pricing
Look for a provider that offers transparent and competitive pricing. Make sure you understand what’s included in their services such as incident response, threat intelligence, and reporting. It will help you make an informed decision.
Conclusion
Security Operations Centers (SOCs) are crucial for protecting organizations from cyber threats. Also, it is important to align SOC strategies with business goals and use reliable automation tools. When choosing a SOC provider, consider factors like experience, 24/7 monitoring, customization, scalability, technology, compliance, and pricing.
Cybercriminals are never going to take a break, and neither should you. Hence, invest in the right SOC service provider and secure your business from evolving cyber threats.
FAQs
Q: What is a SOC service?
A: Security operations center (SOC) services improve the organization’s threat detection, response, and prevention capabilities by combining cybersecurity operations and technologies.
Q: What is the main purpose of SOC?
A: The main purpose of a SOC team is to protect the organization from security incidents by monitoring, detecting, analyzing, and investigating cyber threats.
Q: Is SOC a managed service?
A: Yes, managed SOC, or SOC as a service is den by third-party firms who monitor their cloud environments, devices, longs, and network for threats.
Q: What are the three types of SOC?
A: There are three types of security operations center (SOC), such as:
- SOC 1: Focuses on financial reporting.
- SOC 2: Focuses on a broad range of data management practices.
- SOC 3: Provides a summary of the SOC 2 report that’s suitable for the general public.
Top Company Choose Qualysec for their Pentesting need











































































































































































































































































































































































































































































































0 Comments