AWS security audit ensures that this cloud environment is secure from all kinds of vulnerabilities. Amazon Web Services (AWS) is one of the most used cloud platforms by businesses. It offers a wide range of services, such as cloud computing, data storage, Amazon PPC tools, networking, database services, content delivery, and more. Since businesses rely heavily on AWS solutions, its security is non-negotiable.
One of the biggest AWS breaches happened in May 2022. A security firm discovered that over 6.5 TB of information was exposed from servers belonging to Pegasus Airlines. This is alarming, as the average cost of a data breach is said to be $4.45 million.
If you use AWS, then this blog is going to be very helpful to you. We are discussing how to do an AWS cloud security audit, how to improve security in AWS, and more.
What is AWS Security?
AWS security refers to the set of tools, policies, and features that make this public cloud provider safe from cyber threats. AWS itself offers several security measures to protect the cloud infrastructure and data stored in it. These tools include:
- AWS IAM – Identity access management
- AWS KMS – Key management service (for data encryption)
- AWS Shield – For protection against DDoS attacks
- AWS CloudTrail – For safe logging and monitoring
- AWS Config – For resource management
Along with Amazon, the customer is also responsible for the security of their data and resources. The “shared responsibility model” outlines the security responsibilities of both the cloud provider and the customer.
What is AWS Security Audit?
AWS also allows auditing of their services for better security management. AWS security audit is the process of reviewing the security measures and policies to ensure they are functioning and up to date as per the latest industry standards. Security auditors usually use automated tools with manual testing techniques to identify security vulnerabilities that could be exploited by attackers for unauthorized access.
AWS Security services, such as EM, DMS, and SNS are complex and often come with multiple functionalities. It can be challenging for organizations to manage these services without any errors. So, by performing an AWS security audit, organizations can detect the security issues present in AWS services and ensure the entire AWS infrastructure is free from vulnerabilities.
Additionally, a security audit helps an organization comply with the necessary regulatory requirements, such as PCI-DSS (Payment Card Industry Data Security Standard), HIPAA (Health Insurance Portability & Accountability Act), etc.
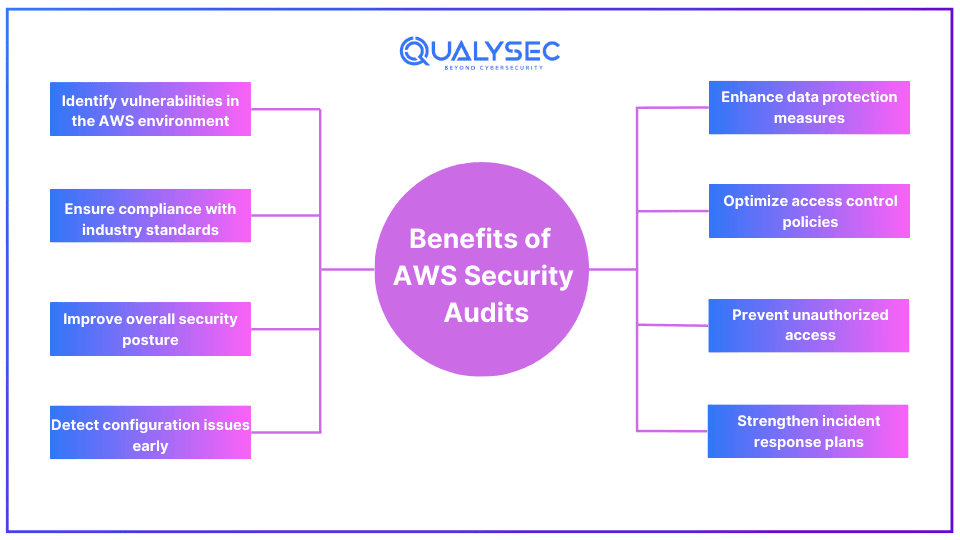
How to do an AWS Security Audit?
The best way to do an AWS security audit is by employing an independent third-party security auditing company. they have the necessary expertise, tools, techniques, and certifications to perform a comprehensive audit.
AWS security audit steps include:
- Information Gathering: The audit company will gather as much information as possible about the organization’s AWS infrastructure.
- Planning/Scoping: The auditors will define what areas to check in the cloud, what AWS security tools & techniques are going to be used, and how much time it’s going to take.
- Automated Vulnerability Scanning: The audits will first use automated tools to scan the AWS environment for known vulnerabilities.
- Manual Penetration Testing: Then the auditors perform manual penetration testing to deeply analyze the environment and uncover vulnerabilities, along with those missed by the tools.
- Reporting: The summary and findings of the audit are documented in a report and shared with the client. The report includes the total vulnerabilities found, their level of impact, and remediation steps.
- Remediation: The client uses this report to fix all the vulnerabilities identified during the AWS vulnerability assessment. If they need to, the audit team will help them locate these vulnerabilities in the cloud environment.
- Retest: After remediation, the audit team will retest the environment to confirm that patches were applied and also no vulnerabilities remain. A final report of this will be shared with the client.
- LoA/Security Certificate: In the end, the audit company will provide a letter of attestation (LoA), which is a security certificate that confirms a successful AWS cloud security audit. This certificate helps with compliance needs and builds trust among customers and stakeholders.
Ever seen a real security audit report? Tap the link below to download one right now!
Latest Penetration Testing Report

What is Security Compliance in AWS?
AWS security compliance helps customers understand that the necessary measures are in place to maintain security and data protection in the AWS cloud. Certain regions and industries make it mandatory for cloud services to have the required security measures. Both the cloud service provider and the customer need to comply with these standards to avoid legal problems. Additionally, customers feel more confident with a cloud service that complies, since it proves that it has up-to-date security measures.
The industry standards that AWS complies with are:
- SOC 1/ISAE 3402, SOC 2, SOC 3
- FISMA, DIACAP, and FedRAMP
- PCI DSS Level 1
- ISO 9001, ISO 27001, ISO 27017, ISO 27018
How to Improve Security in AWS?
As one of the largest cloud service providers in the world, AWS invests heavily to ensure its cloud platform is safe from all threats. However, most of its security is still left to the customers, especially when it comes to access control and data protection. Incorporating AWS penetration testing into your security practices is important. Here are 8 ways, you can improve your AWS security:
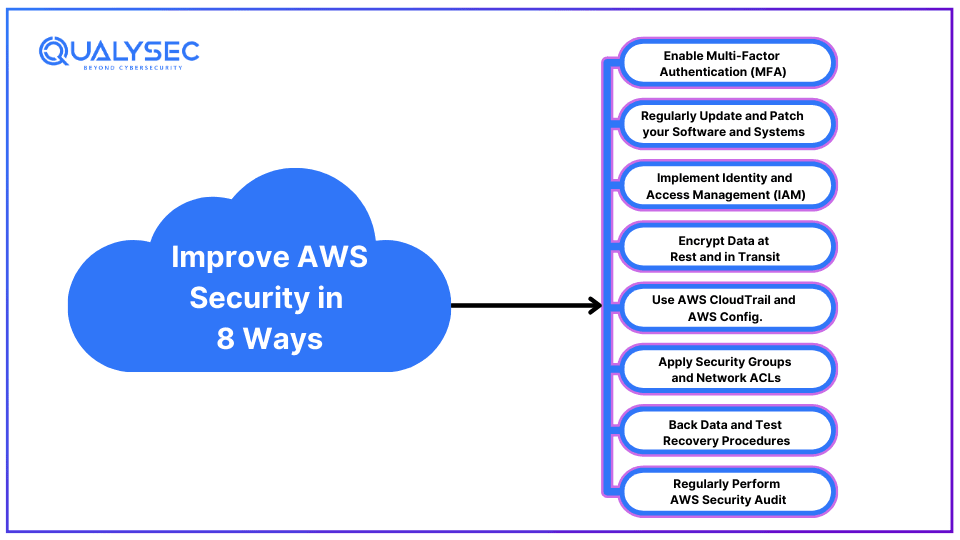
1. Enable Multi-Factor Authentication (MFA)
Implement MFA to add an extra layer of security for those who try to access the cloud. With MFA, users are given an additional verification code from a mobile device or an authenticator app. This helps reduce the risks of accounts being compromised. Additionally, ensure all cloud users have strong and unique passwords to prevent unauthorized access.
2. Regularly Update and Patch your Software and Systems
Keep all your software, applications, and operating systems up to date with the latest security patches. Regular updates fix known vulnerabilities and protect the cloud environment from potential threats. You can set up automatic updates or create a regular maintenance schedule to ensure all systems are secure.
3. Implement Identity and Access Management (IAM)
Use AWS Identity and Access Management (IAM) to control user permissions and access levels. Create policies that grant users the minimum, yet necessary, privileges for their tasks. This minimizes the risk of malicious actions and threats, such as “privilege escalation” that could compromise the AWS environment.
4. Encrypt Data at Rest and in Transit
Protect your valuable data stored in the cloud by encrypting it both when stored (at rest) and while transmitted (in transit). Use AWS services like AWS key management services (KMS) to manage the encryption keys. Encryption ensures that even if the data is accessed without authorization, it can’t be read unless you have the “key”.
5. Use AWS CloudTrail and AWS Config.
Enable AWS CloudTrail and AWS Config to monitor and log all activities in the AWS environment. These two services provide detailed records of configuration changes, API uses, and user activities. By regularly reviewing logs, one can detect suspicious activities, identify potential security issues, and comply with security policies.
6. Apply Security Groups and Network ACLs
Use AWS security groups and network Access Control Lists (ACLs) to control and manage the cloud traffic (both inbound and outbound). Security groups act like virtual firewalls for your instances, while ACLs provide an extra layer of network security. these services allow only good traffic into the cloud and block unauthorized access.
7. Back Data and Test Recovery Procedures
Regular backup data in the cloud using AWS backup solutions like Amazon S3, Amazon RDS, and AWS Backup. Ensure that the backups are stored securely and can be accessed in the event of data loss or corruption. Additionally, test the recovery procedures frequently to verify that the data can be restored quickly and effectively during an emergency.
8. Regularly Perform AWS Security Audit
Conduct regular security audits and assessments to identify and address vulnerabilities in the AWS environment. Take the help of third-party auditors to evaluate the security posture. Regular security audits ensure that all security measures are up to date and comply with the industry standards. As a result, it reduces the risk of breaches and attacks.
Using AWS cloud security solutions keeps your security strong and dependable.
Want to conduct a security audit? Qualysec has all the expertise, tools, talents, and knowledge to offer the best in the industry security audits for clouds and other digital systems. Click the link below and talk to our security expert right now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
A Case Study
Let’s discuss how Qualysec helped a leading tech company that decided to undergo a cloud security audit for its AWS environment.
Objective:
- To identify vulnerabilities in their cloud infrastructure, ensure compliance, and focus on data security and access controls.
Process:
- We first conducted automated vulnerability scanning to uncover known vulnerabilities.
- Then we performed manual penetration testing to uncover more hidden vulnerabilities and exploit them. This helped us to know which vulnerabilities are critical and can be used by attackers to gain unauthorized access.
Findings:
We found a total of 17 vulnerabilities, among which 5 were critical and 6 were high impact. A few critical vulnerabilities are as follows:
- Misconfigured S3 Buckets: Several S3 buckets were publicly accessible, which exposed sensitive data.
- Weak IAM Policies: There was a lack of role-based access controls, which allowed excessive permissions to users.
- Outdated Software: We detected a few outdated software versions that were vulnerable to known exploits.
Outcome:
We provided them with a detailed report that included a summary of the audit, vulnerabilities found, their severity, and remediation steps. As a result, the tech company addressed the security issues and achieved compliance for their businesses.
Conclusion
AWS security audit is important. Since the AWS environment stores sensitive data and carries out critical business operations, attackers are always looking for vulnerabilities that they could exploit. Regular security audits ensure all the security protocols are up to date and in place, comply with regulatory requirements, protect data, and build customer trust. Now that you know how and why AWS security audit is conducted, it’s time to take action.
FAQs
Q: What is an AWS Security Audit?
A: An AWS Security Audit is a thorough review of your AWS environment to identify security vulnerabilities, ensure compliance, and verify that best practices are being followed.
Q: Why is an AWS Security Audit Important?
A: An AWS Security Audit is important to protect your data and prevent breaches. Additionally, it ensures your cloud infrastructure complies with industry regulations and standards.
Q: How Often Should You Conduct an AWS Security Audit?
A: It’s recommended to conduct an AWS Security Audit at least once a year or whenever significant changes are made to your cloud environment to maintain security.




































































































































































































































































































































































































































































































































0 Comments