In today’s digital landscape, web applications have become an integral part of businesses, serving as gateways for users to access services and information. However, with the rise in cyber threats, it is crucial for organizations to prioritize web application security to protect sensitive data and maintain the trust of their users. This is where web application security testing plays a vital role. This blog post will delve into the significance of web application security testing and explore its various aspects.
What is Web Application Security Testing?
Web Application Security Testing is a process of assessing your web application’s web security software for flaws, vulnerabilities, and loopholes in order to prevent malware, data breaches, and other cyberattacks. Meticulous security testing reveals all hidden vulnerable points in your application that run the risk of getting exploited by a hacker.
Understanding Web Application Security Testing
Web application security testing involves a systematic evaluation of a web application’s vulnerabilities and weaknesses to identify potential risks. By conducting comprehensive security testing, organizations can uncover vulnerabilities before they are exploited by malicious individuals or groups. This proactive approach not only helps in safeguarding user data but also mitigates the risk of financial loss, reputation damage, and legal implications.
Neglecting Web Application Security Testing?
Here are some reasons why you should not ignore Web Application Security Testing:
Identify Flaws and Vulnerabilities in Your Application
Web application security testing helps in identifying flaws and vulnerabilities that attackers could exploit. Through comprehensive testing, organizations can proactively identify weaknesses such as SQL injections, cross-site scripting (XSS), cross-site request forgery (CSRF), and many others. By uncovering these vulnerabilities, organizations can take the necessary steps to patch them and enhance the overall security of their web applications.
Comply with Laws
Various industries have specific security and compliance regulations that organizations must adhere to. Web application security testing helps ensure compliance with these regulations, preventing potential legal issues and penalties. By conducting regular security testing, organizations can demonstrate their commitment to protecting sensitive data and maintaining regulatory compliance.
Analyze Your Current Security
Web application security testing provides an opportunity to analyze the current security measures implemented in your web application. It allows you to assess the effectiveness of your existing security controls and identify areas that require improvement. By evaluating your current security posture, you can make informed decisions about strengthening your defenses and mitigating risks.
Detect Security Breaches and Anomalous Behavior
Security testing helps in detecting security breaches and anomalous behavior within web applications. By monitoring and analyzing application logs, security testers can identify unauthorized access attempts, suspicious activities, and potential breaches. Timely detection of such incidents allows organizations to respond swiftly and minimize the impact on their systems and data.
Formulate an Effective Security Plan
Through web application security testing, organizations can gain valuable insights that aid in formulating an effective security plan. By understanding the vulnerabilities and risks specific to their web applications, organizations can prioritize security measures and allocate resources accordingly. This proactive approach helps in building a robust security strategy that mitigates potential threats and protects critical assets.
Who Performs Web Application Security Testing?
Web application security testing can be performed by internal security teams, external security consultants, or a combination of both. Internal security teams possess knowledge of the organization’s infrastructure and applications, while external consultants bring specialized expertise and fresh perspectives. The choice depends on factors such as budget, resources, and the complexity of the application being tested.
Common Terms Used in Web Security Testing
- SQL Injection: A code injection technique where malicious SQL statements are inserted into an application’s database query, potentially granting unauthorized access or altering data.
- Cross-Site Scripting (XSS): A vulnerability that allows attackers to inject malicious scripts into web pages viewed by users, enabling them to steal sensitive information or perform actions on behalf of the user.
- Cross-Site Request Forgery (CSRF): An attack that tricks authenticated users into unknowingly executing malicious actions on a web application in which they are authenticated.
How to Perform Web Application Security Testing Manually?
Performing web application security testing manually involves a systematic and in-depth evaluation of the application’s code, configurations, and user interactions. It includes techniques such as code review, penetration testing, security header and configuration testing, and manual analysis of vulnerabilities. Manual testing requires skilled security professionals who possess knowledge of various attack vectors and can simulate real-world scenarios to identify vulnerabilities and weaknesses.
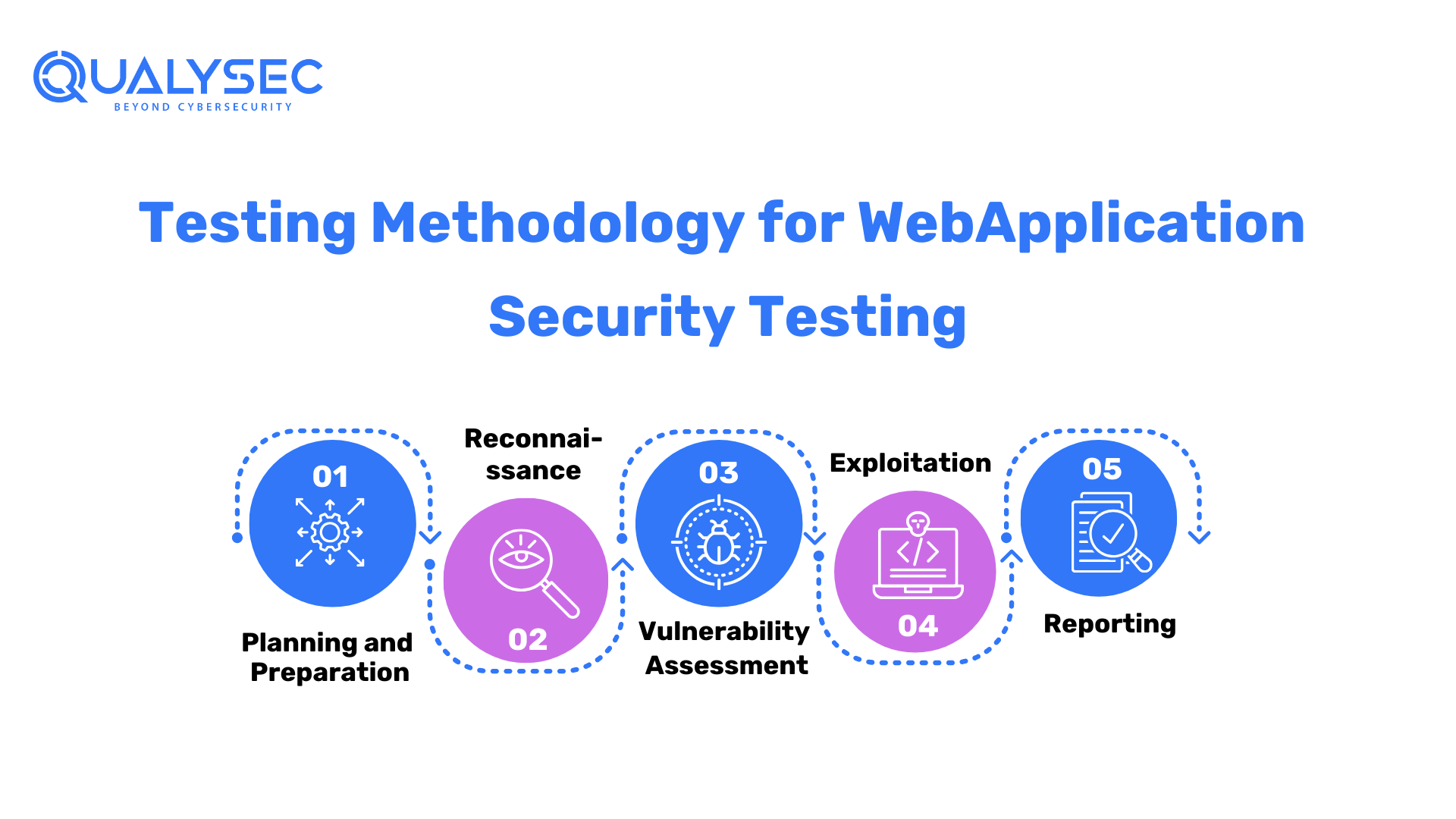
Testing Methodology for Web Application Security Testing
- Planning and Preparation: Define the scope, objectives, and resources required for the security testing process.
- Reconnaissance: Gather information about the target application, architecture, and potential vulnerabilities.
- Vulnerability Assessment: Identify and assess vulnerabilities using techniques such as vulnerability scanning, code review, and security configuration analysis.
- Exploitation: Attempt to exploit identified vulnerabilities to validate their severity and potential impact.
- Reporting: Document and report the findings, including vulnerabilities discovered, their potential impact, and recommended remediation steps.
What Are Web Security Testing Tools?
Web security testing tools automate various aspects of security testing, making the process more efficient and thorough. Some commonly used tools include:
- Burp Suite: A comprehensive web application testing tool that assists in scanning for vulnerabilities, intercepting and modifying requests, and analyzing application behavior.
- OWASP ZAP: An open-source web application security scanner that helps identify vulnerabilities such as XSS, SQL injection, and CSRF.
- Nmap: A network scanning tool that can be used to discover open ports and identify potential security weaknesses.
- Nessus: A vulnerability scanner that helps identify vulnerabilities in web applications, networks, and operating systems.
Qualysec’s Pentest Solution
Qualysec is a leading provider of cloud-based vulnerability and compliance management solutions. Their platform allows companies to conduct continuous monitoring, vulnerability assessment, and compliance management across their entire IT infrastructure.
Qualysec follows a comprehensive methodology that involves a combination of manual and automated testing techniques to ensure maximum coverage of vulnerabilities. They also provide detailed reports that include a prioritized list of vulnerabilities, along with recommendations for remediation.
They work closely with organizations to understand their unique needs.
Qualysec offers various services which include:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI /ML Pen-testing
The methodologies offered by Qualysec are particularly beneficial for businesses that must adhere to industry rules or prove their dedication to security to clients and partners. So, by opting for Qualysec as a Web Application Security Testing service provider, businesses can ensure the safety of their web applications.
Hence, choose Qualysec for a comprehensive and reliable vulnerability scanning report. Also, their penetration testing guide will help you make informed decisions and understand the various factors that impact the cost. Hence, protect your assets and enhance your security posture by choosing us.
Key Features
- Over 3,000 tests to detect and root out all types of vulnerabilities.
- Capable of detecting business logic errors and gaps in security.-
- Ensures zero false positives through manual pen testing.
- Compliance-specific scans for SOC2, HIPAA, ISO27001, and other relevant standards.
- Provides in-call remediation assistance from security experts
Conclusion
Web application security testing is an indispensable aspect of maintaining a secure digital environment. By identifying vulnerabilities, complying with laws, analyzing current security measures, detecting security breaches, and formulating effective security plans. So that organizations can proactively protect their web applications and the sensitive data they hold. Whether performed manually or with the aid of automated tools, web application security testing is a crucial investment in mitigating risks and ensuring the long-term success of your business in the digital realm.
There are several types of Web Application Security Testing Plans, Pen testing Solutions one might need, and vulnerability scanners, including network scanners, host scanners, application scanners, cloud scanners, and wireless scanners. Each with its own set of benefits and use cases. Additionally, both internal and external vulnerability scanners are necessary. These cover all devices and systems that are accessible from within and outside of an organization’s network. We are always ready to help, talk to our Experts and fill out your requirements.
Check out our recent article “ A Comprehensive Guide to External Network Security Audits”.
Frequently Asked Questions
Q: What is web application security testing?
Ans: Web application security testing refers to the process of evaluating and identifying vulnerabilities and weaknesses in web applications to ensure their security.
Q: Why is web application security testing important?
Ans: Web application security testing is crucial because it helps organizations identify vulnerabilities before they are exploited by attackers. By conducting security testing, businesses can mitigate the risk of data breaches.
Q: What are the common types of web application vulnerabilities?
Ans: Some common types of web application vulnerabilities include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), insecure direct object references, security misconfigurations, and authentication and session management issues.
Q: What should organizations do after identifying vulnerabilities through security testing?
Ans: After identifying vulnerabilities through security testing, organizations should prioritize and address them based on their severity. This involves implementing patches, fixing code vulnerabilities, enhancing security controls, and following best practices to mitigate the identified risks.
Q: How often should web application security testing be performed?
Ans: Web application security testing should be performed regularly and whenever significant changes are made to the application.


































































































































































































































































































































































































































































































0 Comments