In the era of cloud computing, organizations rely on the scalability and convenience of cloud-based systems for their data storage and infrastructure needs. However, with the increasing complexity of cyber threats, ensuring the security of cloud environments has become critical. Cloud penetration testing, commonly known as cloud pen-testing, is a proactive approach that helps identify vulnerabilities and strengthens the security posture of cloud-based systems. Let’s explore and understand why it is crucial in safeguarding your cloud infrastructure.
Cloud Penetration Testing: What You Should Know
- Understanding Cloud Penetration Testing
- The Importance of Cloud Penetration Testing
- Types of Cloud Penetration Testing
- Key Challenges in Cloud Penetration Testing
- Engaging Qualified Professionals for Cloud Penetration Testing
Understanding Cloud Penetration Testing:
What is Cloud Penetration Testing?
It is a systematic process of assessing the security of cloud-based systems, applications, and infrastructure. It involves simulating real-world attacks to identify vulnerabilities, misconfigurations, and weaknesses that malicious actors could exploit. By conducting these tests, organizations gain valuable insights into their cloud security vulnerabilities and can take appropriate measures to mitigate risks.
Objectives and Methodology of Cloud Penetration Testing
The primary objective of cloud penetration testing is to proactively detect vulnerabilities before they are exploited by attackers. This process involves several steps, such as reconnaissance, scanning, exploitation, and post-exploitation analysis. By emulating real-world attack scenarios, penetration testing enables organizations to identify weak points and evaluate the effectiveness of their security controls.
Shared Responsibility Model in Cloud Security
In cloud environments, the responsibility for security is shared between the cloud service provider and the customer. The provider is responsible for securing the underlying infrastructure, while the customer is responsible for securing their applications and data. Understanding this shared responsibility model is crucial for its effectiveness, as it helps identify the scope of security assessments and ensure comprehensive coverage.
The Importance of Cloud Penetration Testing
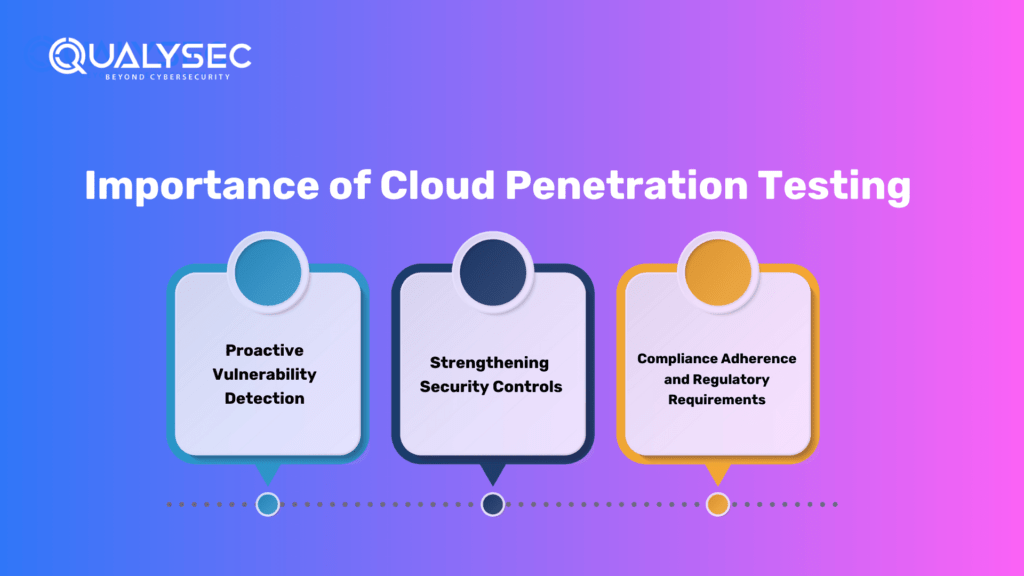
Proactive Vulnerability Detection
It allows organizations to proactively detect vulnerabilities and weaknesses in their cloud environments. By identifying these issues before attackers do, organizations can remediate them promptly, minimizing the risk of data breaches, service disruptions, and unauthorized access.
Strengthening Security Controls
Cloud penetration testing evaluates the effectiveness of security controls implemented in the cloud infrastructure. It assesses authentication mechanisms, encryption protocols, access controls, intrusion detection systems, and other security measures. By identifying weaknesses in these controls, organizations can strengthen their security posture and ensure robust protection of their cloud-based systems.
Compliance Adherence and Regulatory Requirements
Many industries have specific regulatory and compliance requirements that organizations must adhere to when handling sensitive data in the cloud. Cloud penetration testing helps organizations meet these requirements by identifying security gaps and ensuring the implementation of appropriate safeguards. It allows organizations to demonstrate their commitment to data privacy and security, avoiding potential legal and reputational consequences.
Types of Cloud Penetration Testing
Black Box Testing:
Black box testing involves simulating real-world attacks without prior knowledge of the cloud infrastructure. Testers act as external attackers, attempting to exploit vulnerabilities using publicly available information. This approach provides a realistic assessment of the organization’s security posture, as it reflects the perspective of potential adversaries.
White Box Testing:
In white box testing, testers have complete knowledge of the cloud environment, including architecture, configurations, and access controls. This approach allows for a more targeted assessment, focusing on specific areas of concern. It enables organizations to evaluate the effectiveness of their internal security controls and implementation.
Gray Box Testing:
Gray box testing is a hybrid approach that combines elements of both black box and white box testing. Testers have partial knowledge of the cloud environment, representing a scenario where some information is available to potential attackers. This approach provides a balanced assessment, considering both external and internal perspectives.
Key Challenges in Cloud Penetration Testing:
Dynamic Nature of Cloud Environments
Cloud infrastructure is highly dynamic, with resources being provisioned and de-provisioned on demand. This dynamic nature makes it challenging for testers to maintain visibility and accurately assess the security posture of the environment. It requires continuous monitoring and updating of penetration testing strategies to keep pace with the changes.
Shared Responsibility Model Complexity
The shared responsibility model in cloud security adds complexity. Organizations must understand the division of responsibilities between the cloud service provider and the customer. Coordinating and aligning security measures between both parties is crucial to ensure comprehensive coverage and effective security assessments.
Scalability and Complexity of Cloud Infrastructure:
Cloud environments can be vast and complex, with multiple interconnected services and large-scale deployments. Ensuring comprehensive coverage during penetration testing can be challenging, especially when dealing with a massive volume of data and intricate infrastructure configurations. It requires robust testing methodologies and expertise in cloud-specific vulnerabilities and attack vectors.
Engaging Qualified Professionals for Cloud Penetration Testing:
Importance of Expertise and Specialized Knowledge
Cloud penetration testing requires expertise in cloud platforms, security protocols, and attack vectors specific to cloud environments. Engaging qualified professionals or reputable cloud security service providers ensures that comprehensive testing methodologies are applied, vulnerabilities are accurately identified, and appropriate remediation recommendations are provided. Expert knowledge and experience contribute to the effectiveness and efficiency of the testing process.
The Best Cloud Penetration Testing Expert: Qualysec
Qualysec, A Cybersecurity company founded in 2020 is a leading cybersecurity provider. Qulaysec is also known for its renowned cutting-edge technology and expertise in cybersecurity assessments. With a team of skilled professionals, Qulaysec offers a comprehensive range of services, including various vulnerability assessments and penetration testing.
What sets Qulaysec apart is its commitment to staying ahead of the curve in terms of emerging threats and advanced hacking techniques. They employ state-of-the-art tools and methodologies to ensure thorough and accurate assessments. Qulaysec’s team of experienced professionals brings a wealth of knowledge and a human touch to their engagements. This in turn helps foster collaboration and deliver actionable insights.
Technicians at Qualysec can detect flaws that fraudsters could abuse. After these flaws have been found, Qualysec collaborates with the organization to establish a plan to address them and boost the company’s overall security posture. Among the several services available are:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI /ML Pen-testing
Hence, choose Qualysec for comprehensive and reliable Cloud Penetration Testing in India. Also, their penetration testing guide will help you make informed decisions and understand the various factors that impact the cost. Hence, protect your assets and enhance your security posture by choosing us.
Key Features
- Over 3,000 tests to detect and root out all types of vulnerabilities.
- Capable of detecting business logic errors and gaps in security.
- Ensures zero false positives through manual pen testing.
- Compliance-specific scans for SOC2, HIPAA, ISO27001, and other relevant standards.
- Provides in-call remediation assistance from security experts
Benefits of Collaborating with Reputable Cloud Security Service Providers
Collaborating with reputable cloud security service providers offers several advantages. These providers possess specialized knowledge and experience in cloud security, keeping abreast of the latest threats and vulnerabilities. They employ advanced testing methodologies, tools, and techniques to identify vulnerabilities and provide actionable insights for enhancing cloud security. Engaging experts reduces the burden on organizations, allowing them to focus on their core business while ensuring robust protection of their cloud infrastructure.
Conclusion
Cloud penetration testing is a critical practice for organizations relying on cloud-based systems to protect their data and infrastructure. By understanding the fundamentals, its importance, types, and challenges, organizations can proactively identify vulnerabilities, strengthen security controls, and meet regulatory requirements. Engaging qualified professionals or reputable cloud security service providers further enhances the effectiveness of cloud penetration testing efforts, ensuring a robust and secure cloud environment. Through continuous testing, organizations can mitigate risks, safeguard their digital assets, and stay ahead of evolving cyber threats in the cloud.
Qualysec has a successful track record of serving clients across a range of industries such as IT. Their expertise has helped clients identify and mitigate vulnerabilities, prevent data breaches, and improve their overall security posture.
When it comes to comprehensive cloud penetration testing Qualysec is the organization to go with. Their cost of VAPT guide helps clients make informed decisions by understanding the various factors that affect the cost by clicking here.







































































































































































































































































































































































































































































































0 Comments