Last year, a data breach of an organization cost $4.45 million on average, with over 2,365 cyberattacks globally. This is a 72% increase since 2021.
If you are running a business that operates digitally, you might be the next victim of a cyberattack. To prevent this, you need to conduct a vulnerability assessment and penetration testing (VAPT) on your IT infrastructure. Performing VAPT testing on your network, applications, and other digital assets will help you identify potential vulnerabilities and enhance your current security measures.
In this blog, you will learn about VAPT testing, why businesses need it, and what are its processes. If you want to continue your business operations smoothly, this blog is going to help you!
What is VAPT Testing?
Vulnerability assessment and penetration testing (VAPT) is the process of finding and exploiting all possible vulnerabilities in your IT infrastructure, with a final goal to mitigate them. VAPT is done by cybersecurity specialists or ethical hackers who are experts in offensive exploitation.
Simply put, businesses hire VAPT companies to hack their own systems in order to find security flaws before real hackers do. It also helps organizations to comply with various industry standards throughout the year.
The VA in VAPT – vulnerability assessment involves specialists using automated tools to find potential vulnerabilities on the surface level. Followed by PT – penetration testing is a comprehensive testing process that involves ethical hackers manually trying to find vulnerabilities that real hackers could exploit for unauthorized access and data breaches. Together, they offer an in-depth analysis of your current security strengths and suggest methods to improve them.
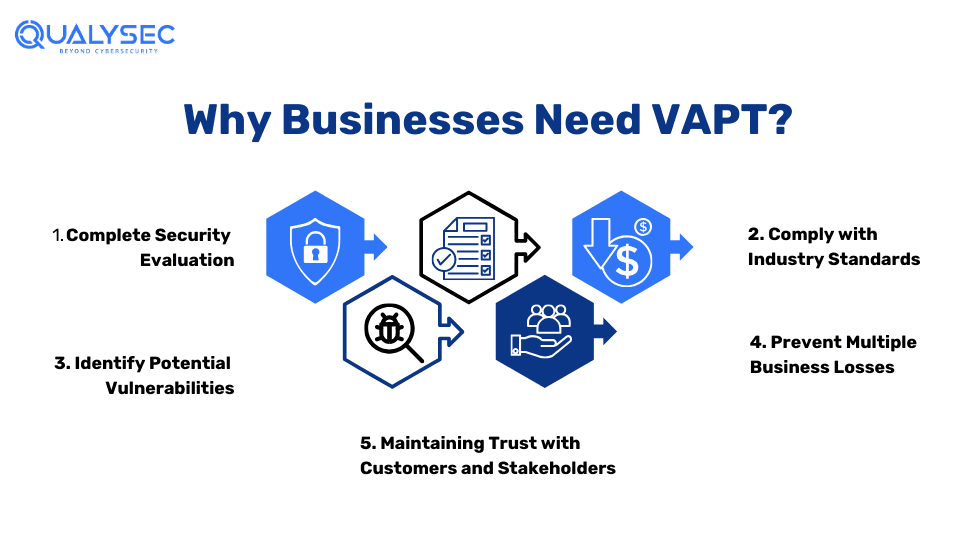
Why do you Need VAPT Testing?
Conducting VAPT testing regularly has tons of benefits for your business. Here are some important ones:
1. Complete Security Evaluation
Combining vulnerability assessment and penetration testing offers a multifaceted approach that helps you evaluate the current security measures of your IT structure. It shows how resilient your network and applications are against cyberattacks and where the security flaws lie.
2. Identify Potential Vulnerabilities
VAPT involves using automated tools and manual penetration testing methods whose sole purpose is to find where the vulnerabilities are present. Additionally, VAPT service providers also provide methods to fix those vulnerabilities. As a result, businesses can secure their sensitive data and digital assets before real hackers breach them.
3. Comply with Industry Standards
Many industry regulations and compliance standards require organizations to perform regular security testing on their applications to keep customer information safe. Not complying with these standards would result in legal penalties and fines. VAPT reports help ensure you meet these requirements with ease. Some of the most popular compliances are GDPR, PCI DSS, SOC 2, ISO 27001, HIPAA, etc.
4. Prevent Multiple Business Losses
Cybercriminals attack businesses for mainly two purposes – steal data or steal finances. Sometimes also to disrupt business operations. Hackers will easily infiltrate your systems and get what they want if there are any weak points. As a result, the losses could be huge amounts of sensitive data and millions of dollars.
5. Maintain Trust with Customers and Stakeholders
Even a small breach in your business can break the trust of your customers and stakeholders. By conducting VAPT testing, you can show your commitment to data and asset security. As a result, it builds confidence among your customers and vendors that their data is safe from online dangers.
Do you also want to test your business applications and network for vulnerabilities? Qualysec Technologies provides process-based VAPT services that will keep your organization secure from evolving cyber threats Contact now and get amazing offers!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
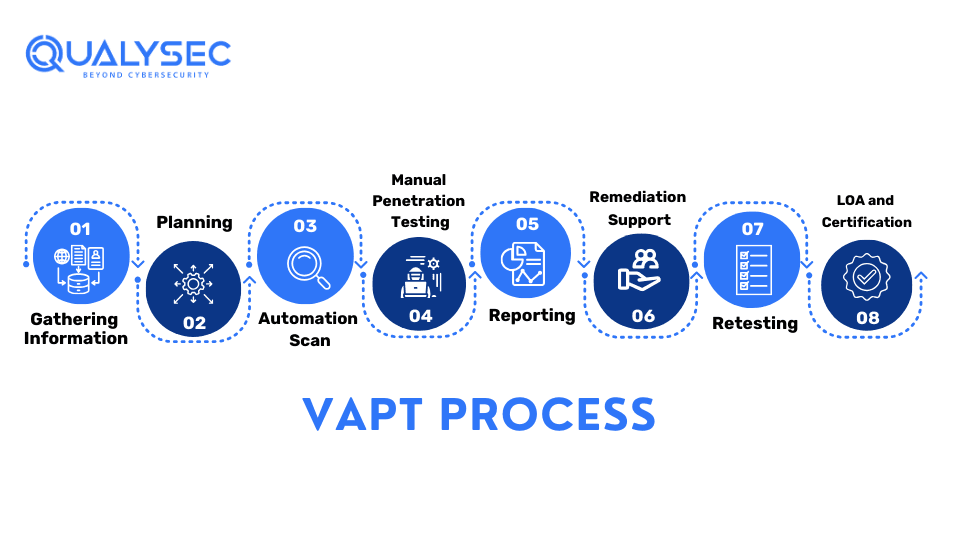
What is the VAPT Testing Process
While different VAPT service providers have their specific ways of conducting, the basic process remains the same. The VAPT process starts with gathering information about the test environment and ends with report submission. Here is the entire process:
1. Information Gathering
The 1st step of VAPT testing involves gathering as much information about the application or system being tested, either from the client itself or publicly available web pages.
2. Planning
In the 2nd step, the VAPT service provider defines the test’s scope, goal, and strategy. The cybersecurity specialists will then tailor their approach to target specific vulnerabilities and cyber threats to find security weaknesses.
3. Automated Vulnerability Scans
Here the VAPT provider will use automated tools to scan the application to find vulnerabilities on the surface level. This is a quick process of finding vulnerabilities. However, since automated tools follow a specific scanning script, this method may not provide you with all the vulnerabilities present.
4. Manual Penetration Testing
This is the stage where in-depth security testing happens. In this stage, cybersecurity specialists or ethical hackers use manual techniques to simulate real cyber attacks on the test environment, to find potential vulnerabilities. Since it uses the human touch, it helps discover hidden vulnerabilities and security flaws.
5. Reporting
The report is the only thing the organization’s developers want, to secure the digital assets. The VAPT provider then documents all the vulnerabilities found in the process and even steps to fix them.
Want to see what an actual VAPT report looks like? Just click the link below and download one right now!
Latest Penetration Testing Report

6. Remediation
If needed, the VAPT provider can assist the developers with the remediation process online or through consultation calls.
7. Retest
This is something that organizations look for when choosing the best VAPT testing provider. After the organization has completed remediation, the testers retest the application to confirm whether the vulnerabilities are successfully eliminated.
8. LOA and Security Certificate
After the elimination of the vulnerabilities, the service provider, provides a letter of attestation (LOA) and security certificate. This proves that you have successfully conducted VAPT testing on your application, and it is now absolutely safe.
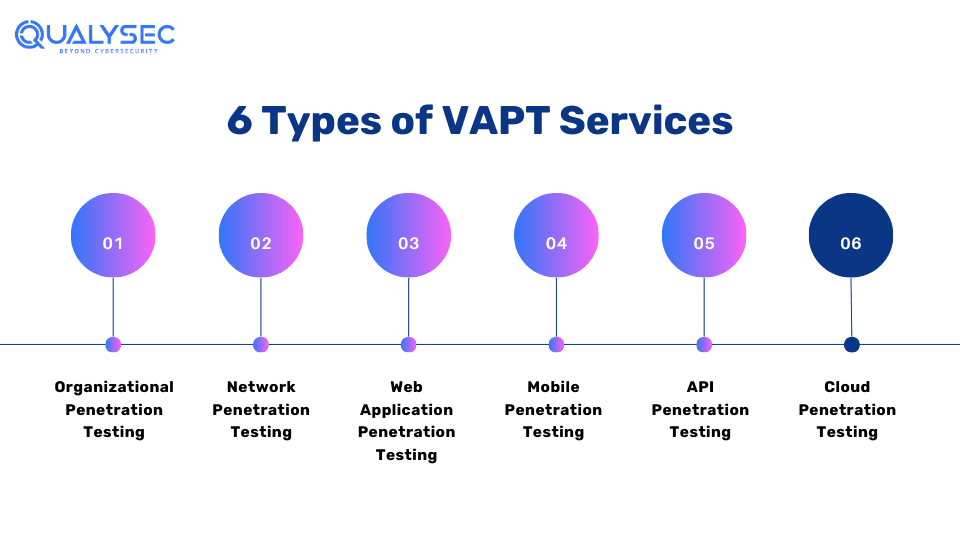
6 Common Types of VAPT Testing
1. Organizational Penetration Testing
Organization penetration testing is a comprehensive assessment that includes simulating real-world attacks on an organization’s IT infrastructure. For example, web and mobile applications, cloud, APIs, and networks. As a result, it helps strengthen the overall security of the organization.
2. Network Penetration Testing
Network penetration testing includes applying ethical hacking methodologies to check the overall network defenses against cyber threats. Pen testers map the network architecture, identify systems and services, and then use various automated tools and manual techniques to mimic real-world cyberattacks.
3. Web Application Penetration Testing
Web app penetration testing uses manual and automated methods to find weaknesses in the authentication, authorization, input validation, and business logic of web applications. They help find potential vulnerabilities in the apps before cyber attackers exploit them for their gain.
4. Mobile App Penetration Testing
Mobile app penetration testing uses multiple automated and manual techniques to detect vulnerabilities in a mobile application’s code, APIs, and data storage. Often pen testers focus on areas like insecure data storage (cleartext passwords), intercepting sensitive data in transit, flaws in inter-app communication or API integrations, and exploiting business logic vulnerabilities, to identify vulnerabilities.
5. API Penetration Testing
API penetration testing mimics real-world attacks on the application programming interfaces (APIs) to find vulnerabilities like broken authentication, Injection flaws, IDOR, and weak authorization. Pen testers may use various techniques to identify exploitable business logic vulnerabilities, such as payment gateway manipulation.
6. Cloud Penetration Testing
Cloud VAPT testing checks vulnerabilities in the cloud configurations, APIs, access controls, and storage mechanisms. Since most businesses use cloud services, it is a prime target of cybercriminals. As a result, cloud-based services should be protected if you want to protect your business from cyber threats.
How to Choose the Right VAPT Testing Provider in the USA
1. Assess your Security Needs
Before you choose a VAPT testing provider, assess your organization’s specific needs. Consider these factors:
-
- Size and complexity of your IT infrastructure
-
- Industry regulations you need to comply with
-
- Timelines
-
- Desired result of the VAPT testing
2. Check Methodology
Look for VAPT service providers that follow industry-approved methodologies such as the OWASP Testing Guide (OTG) or Penetration Testing Execution Standard (PTES). Inquire how they can tailor their methodologies to meet your unique security needs.
3. Check Certifications and Credentials
Check whether the VAPT provider has appropriate certifications, for example, CEH, OSCP, CISSAP, and CompTIA PenTest+. These certifications prove that they are expert in VAPT testing and are acquainted with industry-approved methodologies.
4. Compare Cost and Value
Compare the pricing structure of different VAPT providers and the service value they offer. Examine the expertise of the team, depth of testing quality and reporting, and remediation support. Do not always go for the cheapest provider. Go for the one that offers cutting-edge testing services with reasonable pricing.
5. Asses Reporting and Communication
Transparent reporting and effective communication are both important to understanding potential vulnerabilities and implementing necessary remediation methods. Ask for sample reports to check the clarity and details of their findings. Additionally, check how well they respond to your concerns and the communication channels they use.
Conclusion
With cybercrimes happening every minute of the day, the question is no longer whether to conduct VAPT testing, but rather which type of VAPT is best for you. Before you expand your business, conduct a comprehensive VAPT. As a result, it will help you strengthen your overall security posture, comply with industry standards, and maintain your reputation among customers.
Additionally, choose a VAPT service provider who goes beyond cybersecurity basics. Check their testing capabilities, the array of VAPT services, methodologies, and retesting capabilities. Regular VAPT testing can be a simple investment, but the ROI is definitely worth it!
FAQs
Q: What is done in VAPT testing?
A: VAPT or vulnerability assessment and penetration testing, is a security testing exercise that identifies vulnerabilities in an application, network, cloud, APIs, and more. Additionally, both the VA and PT have unique strengths and are often done collectively for a comprehensive security analysis.
Q: What is the difference between vulnerability assessment and penetration testing?
A: Vulnerability assessment uses automated tools to find vulnerabilities in an IT infrastructure. On the other hand, penetration testing uses manual testing techniques to simulate real attacks to find vulnerabilities. Furthermore, vulnerability assessment may generate false positives as it is bound by a fixed script of the automated tool, but penetration testing offers accurate results due to the human factor.
Q: How much does a VAPT cost?
A: The cost of VAPT depends upon the complexity and number of the tested environment. However, you can expect the cost to be within the range of $1,00 to $2,000 for simple networks. Additionally, it can vary from $4,000 to $5,000 for organizations with complicated IR structures.
Q: Who can do VAPT testing?
A: Typically, cybersecurity companies that specialize in VAPT services should conduct the testing. Since they have certified ethical hackers who are experts in industry-approved methodologies, they can accurately find vulnerabilities in your digital assets.






























































































































































































































































































































































































































































0 Comments