Network is an integral part of every organization that does its business online. However, the interconnectivity nature of networks also means that they are vulnerable to cyberattacks. One way to ensure the security of the network is through network penetration testing. It involves simulating real-world attacks on the network to find and fix any vulnerabilities present in it. Regular network testing is very important to keep the network safe from constantly evolving cyber threats.
As per Forbes, the total cost of cybercrime damages is expected to reach 10.5 trillion by the end of 2025. According to recent studies, 54% of the cyberattacks were on networks and their applications, which is expected to increase in the upcoming years.
This blog is a detailed guide to network penetration testing, which will cover its importance, along with its methodology, tools, and more. As a result, you will have a brief idea of what network penetration testing is and why you should invest in it.
What is Network Penetration Testing?
Network penetration testing or network pentesting is a cybersecurity practice in which cybersecurity professionals simulate attacks that real hackers or malicious actors do. This helps in finding vulnerabilities and security flaws present in the network’s security defenses.
Networks are very complicated, consisting of a combination of WAN, LAN, and Wi-Fi, in addition to a lot of endpoints and devices like servers, computers, mobile devices, and Internet of Things (IoT) devices. They also contain security technologies like firewalls and intrusion prevention systems (IPS).
Any of these components could have a potential vulnerability that hackers could exploit and gain unauthorized access to the network. The main purpose of network penetration testing is to check how secure the current network security is and identify security gaps before a real cyberattack occurs.
How does network penetration test work?
It works by:
- Information Gathering: First, testers collect details about the network, like IP addresses and system setups.
- Vulnerability Scanning: Then, they scan for security weaknesses using specialized tools.
- Exploitation: Next, testers attempt to exploit any found vulnerabilities to access the network.
- Post-Exploitation: After gaining access, they assess the impact and try to move further within the network.
- Reporting: Finally, they document all findings and suggest ways to improve security.
Importance of Network Penetration Testing
Every organization wants their network to be secure from cyber threats and network penetration testing is one of the best ways to ensure that. Here are a few points why it is important for organizations to conduct penetration testing for their networks:
Identify Network Vulnerabilities
Penetration testing helps identify security vulnerabilities in the network before an attacker or hacker exploits them for their gain. It also provides tips to fix the found vulnerabilities. By identifying and fixing vulnerabilities promptly, organizations can fix them before they become a security risk.
Improve Overall Security Posture
Network penetration testing provides valuable insights into the overall security posture of the network. It helps them identify what areas need improvement and where to make security investments.
Regulatory Compliance
Some industries like finance and healthcare must comply with certain regulatory standards like HIPAA and PCI DSS. These regulatory standards can be achieved with regular penetration testing. It is necessary to comply with these standards because if you do not, it could lead to financial penalties and reputation damage.
Protect Sensitive Data
Arguably the most important reason for organizations to implement network penetration testing is to protect themselves from data breaches. In fact, a small weakness in the network has the potential to leak sensitive data of the organization, affecting customer trust and violating various rules and regulations. Penetration testing is a helpful way to assess possible levels of security risks in the network and fix them.
Minimize Financial Loss
Successful cyberattacks can result in the leakage of account details while causing big financial losses for organizations. Network penetration testing helps find vulnerabilities and improves security defenses, reducing or even stopping financial damage from a cyberattack.
Maintain Company Reputation
Even a small case of a data breach or cyberattack on the network can damage the organization’s reputation, making customers lose trust in the business. Organizations should conduct regular network penetration testing because it shows that the organization takes network security seriously, which helps preserve its reputation.
Difference Between Internal and External Network Penetration Testing
There are basically two types of network penetration testing: external and internal. Internal penetration testing is focused on identifying vulnerabilities that can be exploited by internal threats like current or former employees. While external penetration testing helps in finding vulnerabilities that could be exploited by malicious actors outside like hackers.
| External Network Penetration Testing | Internal Network Penetration Testing |
| Identifies vulnerabilities from the viewpoint of external attackers like hackers. | Identifies vulnerabilities from the viewpoint of internal attackers like employees. |
| Mostly outsourced, resulting in a cost-effective testing process. | Requires an in-house security team to conduct the tests, therefore expensive. |
| Requires extensive planning and is done only a few times. | As the security team is present in-house, less planning is required and can be done more frequently. |
| Focuses only on external threats and is less comprehensive. | More comprehensive, as an internal threat can hack the organization’s network security through both internal and external methods. |
Common Network Security Threats
There is a range of security threats that organizations face in this interconnected digital world. Here are some of the most popular and common network security threats that can be prevented by regular network penetration testing.
Malware
Malware refers to malicious or harmful software designed to damage or disrupt systems and applications. Common types of malware include viruses, ransomware, spyware, trojan horses, worms, bots, keyloggers, etc. Cyberattacks spread malware through email attachments, malicious websites, or software downloads.
Phishing
Phishing is a type of cyberattack where the attacker impersonates a trusted individual. In fact, they trick users into sharing sensitive information like login details or financial info. Phishing attacks can happen through email, social media, or messaging apps.
Distributed Denial of Service (DDoS) Attacks
The goal of a DDoS attack is to make a website or network unavailable by flooding it with traffic. This is typically done through a botnet, which is a network of computers that are infected with malware and can be remotely controlled by the attacker.
Advanced Persistent Threats (APTs)
These are highly sophisticated cyberattacks where attackers gain unauthorized access to a network and remain undetected for a long time, in fact, sometimes even for months or years. These attackers use various techniques like social engineering and malware to gain access to the network. Once inside, they continue to steal sensitive data or target specific systems.
Unlike other cyberattacks, APTs are customized to target a specific organization and industry. Attackers use information through reconnaissance activities to create a customized strategy that’s hard to detect and mitigate. But with regular network penetration testing, you can easily find the entry points through which these attackers gain access.
Drive-by Downloads
Drive-by downloads refer to a type of malicious software that gets downloaded and installed when a user visits a malicious website or clicks on a malicious link. The malicious software is installed without the knowledge and consent of the user. Usually, drive-by downloads are used to distribute malware like
Domain Name System (DNS) Attacks
DNS attacks target the systems that translate domain names into IP addresses. These attacks can have significant consequences as they can disrupt the organization’s ability to access vital resources or compromise sensitive data.
There are different types of DNS attacks, such as:
- DNS spoofing: In this, the attacker manipulates the DNS cache to redirect users to a malicious website instead of the intended one.
- DNS Cache Poisoning: Here, the attackers inject false DNS information into a DNS server’s cache to redirect users to a malicious website.
- DNS Amplification: in this type of DNS attack, attackers exploit a DNS server to amplify the size of a DDoS attack, making it difficult to counter.
- DNS Tunneling: This attack involves concealing data in DNS queries and responses, enabling attackers to bypass firewalls and other security measures.
Network Penetration Testing Process
Depending on the industry, the process may vary but the core strategy of penetration testing stays the same. Here are the steps involved in network pen testing.
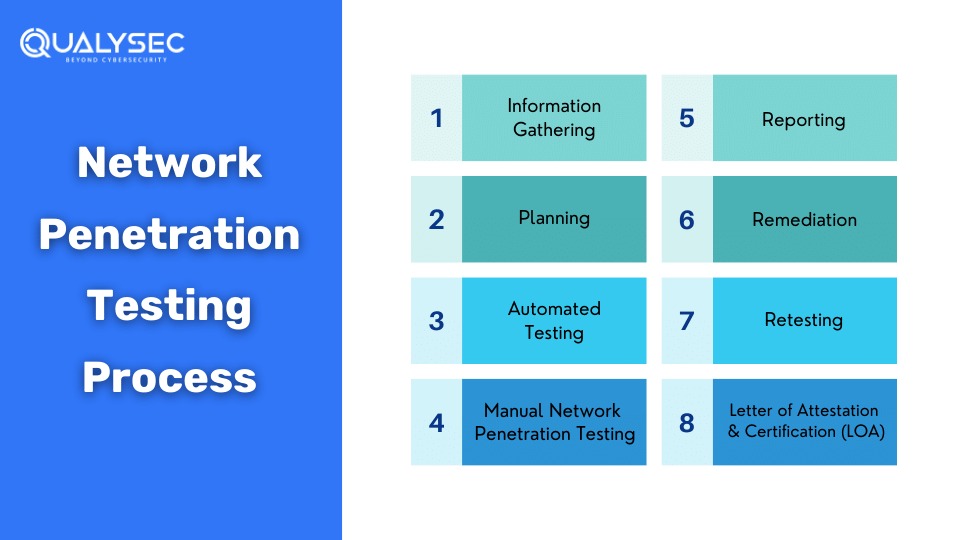
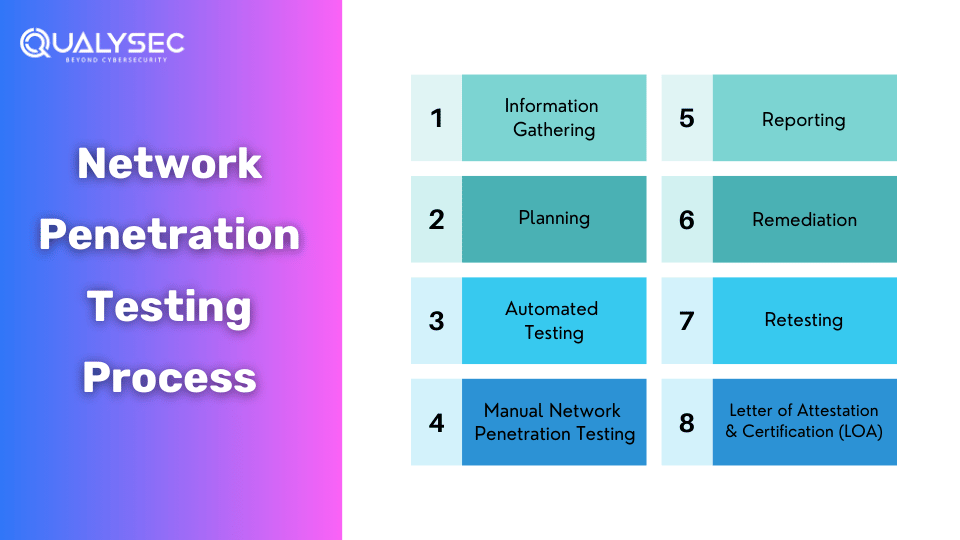
Information Gathering
Gather as much information as possible about the network. The organization will provide all the knowledge and permissions for the network to the testing team. This information helps the testing team understand the target environment better and prepares them to search for vulnerabilities. The testing team usually interacts with the target network to gather all the necessary information. For this reason, it is an easier and more detail-oriented approach.
Planning
After all the necessary information is gathered, the network penetration testing team establishes clear goals by getting deep into the network’s technicality. With proper research and strategies, they customize their methods to target specific cyber threats and vulnerabilities in the network.
A well-informed penetration testing strategy is designed which describes the scope, methodologies, and testing criteria. Along with that, the organization may also provide a high-level checklist to guide the pentest team through their process.
Automated Testing
Testers use specialized automated tools to identify vulnerabilities present in the network. These tools simulate real attacks and discover potential security flaws. In fact, automated scans are very effective in finding and mitigating surface-level vulnerabilities in the staging environment.
However, automated tools are not enough to find all the vulnerabilities present. They also might miss vulnerabilities and may generate false positives. Though automation scans help determine potential weaknesses, manual penetration testing is also required to find security flaws in depth.
Manual Network Penetration Testing
The most effective way to find security flaws in a network is by implementing manual network penetration testing. Unlike automated scans, manual penetration testing requires human expertise to identify vulnerabilities that automated tools might miss. Manual pentesting is conducted by highly skilled cybersecurity professionals, also called ethical hackers.
Qualysec Technologies’ Manual Network Penetration Testing Includes:
- Network mapping
- Port scanning
- Network enumeration
- Network traffic analysis
- Wireless network testing
- Firewall and IDS/IPS testing
- Sensitive information finding
- Network device exploration
- Network segmentation testing
Test Analysis
After all the testing methods are done, the assessment team analyses the findings and categorizes them as per their severity and likelihood of happening. This helps organizations prioritize the security risks and allocate their resources to mitigating higher risks first.
Reporting
The penetration testing company will make a detailed report of the network penetration testing. The report will include a summary of the tests conducted, the vulnerabilities found, and tips to mitigate them.
Want to see what a network penetration testing report looks like? Download a copy of our sample report right here and get a brief idea!
Latest Penetration Testing Report

Remediation
Usually, the remediation process involves creating a plan of action to mitigate the vulnerabilities found during the testing. On request, the penetration testing team will help the development team mitigate the vulnerabilities found through consultation calls. In fact, in most cases, the organizations ask for direct communication to fix the security flaws detected during the testing. This joint effort allows a smooth remediation of vulnerabilities and improves the network’s overall security posture.
Retesting
After all the vulnerabilities are mitigated, the testing team then retests the network and its components. They re-evaluate the target network to ensure that all the remediation efforts are effective and that all the vulnerabilities are successfully eliminated. After the retests are completed, the testing company will provide a final report of all the activities.
Letter of Attestation (LOA) and Certification
Along with the report, Qualysec will also provide a Letter of Attestation (LOA) and a security certificate. These certificates will help the organization in showcasing that its network is secure and meets all the necessary security demands. The LOA will include the following details:
- Confirmed security level
- Security details for stakeholders
- Compliance completion
Tools Used by Qualysec to Conduct External Network Penetration Testing
There are a variety of tools that testers can use to conduct penetration testing. Professionals at Qualysec Technologies use these tools to get accurate results for external network penetration testing.
- Nessus: A vulnerability scanning tool used to identify vulnerabilities present in the network.
- Nmap: A network exploration and security auditing tool.
- Wireshark: A packet sniffing and analysis tool used to monitor network traffic and its behaviour.
- Nikto: A vulnerability scanning tool used to scan web servers for security vulnerabilities.
- Metasploit: A penetration testing tool used to probe vulnerabilities in networks and servers.
- Angry IP Scanner: A port scanner used to analyze business networks.
- Open SSL: An application software library that provides secure communication over computer networks.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
With the increasing number of cyber threats and the impact of cyberattacks, it is essential to ensure your network is secure against vulnerabilities. This is where Qualysec Technologies can help you. Our comprehensive external network penetration testing services can help you detect the security flaws in your network. We also provide necessary steps to mitigate found weaknesses in the network.
Our team of expert cybersecurity professionals, who are well-versed in penetration testing methods use advanced tools and techniques to conduct in-depth testing that simulates real-world attacks. We will provide you with a detailed report on the security gaps we find, along with recommendations for remediation. With our comprehensive network security penetration testing services, you can rest assured that your network is secure against evolving cyber threats and risks.
FAQs
Q: Is network penetration testing important?
A: Yes. Since a network connects different businesses and facilitates data flow, it is a major target for cyberattacks. Network penetration testing helps identify and fix vulnerabilities through which these cyberattacks can happen.
Q: What is the difference between internal and external pentest?
A: External pentests find vulnerabilities that external malicious actors or hackers exploit. Internal pentests discover vulnerabilities that internal actors like employees exploit.
Q: What are the methods of external network pentesting?
A: There are typically 3 approaches to external network pentesting:
- Black box pentesting: Testers have no critical knowledge of the tested environment.
- White box pentesting: Testers have all the knowledge of the tested environment.
- Grey box pentesting: Testers have limited knowledge of the tested environment.
Q: What are the common network penetration testing tools?
A: Some of the common tools used in network penetration testing are:
- Nessus
- Nmap
- Wireshark
- Nikto
- Metasploit
- Angry IP Scanner
- Open SSL




































































































































































































































































































































































































































































































0 Comments