Data breaches are becoming more frequent, affecting industries like fintech, IT, healthcare, and banking. No organization is completely safe. According to the latest reports, the average cost of a data breach increased to $4.45 million in 2023, a 2.3% rise from 2022. Meanwhile, critical infrastructure businesses faced even higher costs, reaching $4.82 million on average per breach. To counter these cyber threats, companies rely on Vulnerability Assessment and Penetration Testing (VAPT Testing)—a comprehensive security testing approach that identifies and mitigates vulnerabilities before attackers exploit them.
In this blog, we will explore VAPT in detail: its methodology, importance, and how businesses can benefit from it.
What is VAPT?
Vulnerability Assessment and Penetration Testing (VAPT) is a structured cybersecurity process designed to detect, analyze, and address vulnerabilities in systems, networks, and applications. It combines two key approaches:
- Vulnerability Assessment (VA): Focuses on identifying security weaknesses in a system.
- Penetration Testing (PT): Simulates real-world attacks to determine how exploitable those weaknesses are.
Method & Goal of VAPT
VAPT helps organizations stay ahead of cyber threats by proactively identifying and fixing security gaps before they can be exploited. The process involves:
- Vulnerability Assessment: Scanning tools and manual techniques are used to detect vulnerabilities.
- Penetration Testing: Ethical hackers simulate real-world attacks to assess how these vulnerabilities can be exploited.
With the rise of AI-driven cyberattacks and automated hacking tools in 2025, VAPT has become even more critical. Businesses need to test their defenses regularly to ensure resilience against evolving threats.
Why is VAPT Important?
VAPT helps businesses:
- Prevent data breaches: By fixing vulnerabilities before hackers can exploit them.
- Meet compliance requirements: Regulations like GDPR, PCI-DSS, HIPAA, and ISO 27001 mandate security testing.
- Protect brand reputation: A data breach can lead to financial and reputational damage.
- Avoid financial losses: Cyberattacks can cost millions in damages and fines.
With increasing regulatory scrutiny in 2025, noncompliance with security standards can result in severe penalties, making VAPT a necessity for businesses of all sizes.
Difference Between Vulnerability Assessment and Penetration Testing (VAPT)
|
Vulnerability Assessment |
Penetration Testing |
|
Identifies and categorizes security vulnerabilities. |
Actively exploits vulnerabilities to assess security risks. |
|
Uses automated tools to scan for weaknesses. |
Uses ethical hacking techniques to mimic real cyberattacks. |
|
Provides a prioritized list of vulnerabilities. |
Identifies the attack path a hacker might take. |
|
Suitable for regular security assessments. |
Best for in-depth security evaluations after a vulnerability assessment. |
By integrating both approaches, businesses can ensure a robust cybersecurity posture that keeps their systems and data protected.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
What Are the 8 Significant Types of VAPT Services?
- Web Application Penetration Testing
- Mobile Application Penetration Testing
- Cloud Application Penetration Testing
- IoT Penetration Testing
- API Penetration Testing
- Desktop Application Penetration Testing
- AI/ML Penetration Testing
- Network Penetration Testing
What is the VAPT Methodology?
There are 3 different methods or strategies used to conduct VAPT, namely; Black box testing, white box testing, and gray box testing. Here’s what you need to know about them:
1. Black Box Testing
A black box penetration test provides the tester with no knowledge about what is being tested. In this scenario, the pen tester executes an attacker’s plan with no special rights, from initial access and execution until exploitation.
2. White Box Testing
White box testing is a type of testing in which the tester has complete access to the system’s internal code. He has the appearance of an insider. The tester understands what the code expects to perform in this type of testing. Furthermore, it is a method of testing a system’s security by examining how effectively it handles various types of real-time assaults.
3. Gray Box Testing
The tester is only provided a limited amount of information during a grey box penetration test, also known as a transparent box test. Typically, this is done with login information. Grey box testing can assist you in determining how much access a privileged person has and how much harm they can cause.
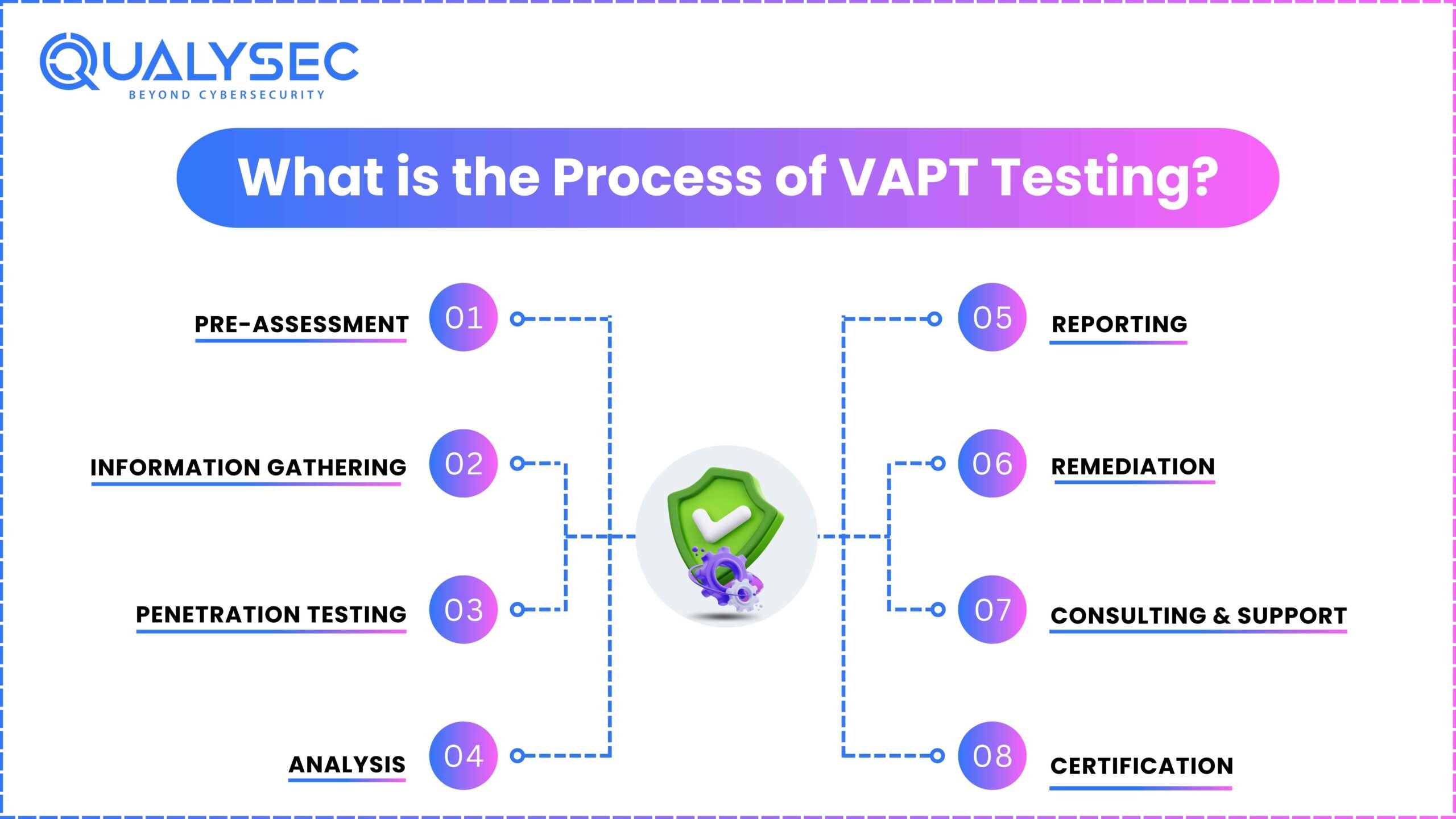
What is the Process of VAPT Testing?
Vulnerability Assessment and Penetration Testing (VAPT) follows a structured approach to identify and fix security flaws. Below is a step-by-step breakdown of the process:
1. Pre-Assessment
Before starting, the security team defines the scope, objectives, and rules of the test. This involves:
- Understanding the system’s architecture, purpose, and potential risks.
- Setting up the testing environment.
- Getting required approvals and access credentials.
2. Information Gathering
The security team collects technical and non-technical details about the system. This includes:
- Scanning for public and internal information related to the system.
- Understanding the technology stack, APIs, and third-party integrations.
- Conducting reconnaissance to map out possible attack points.
3. Penetration Testing
Testers simulate real-world cyberattacks to find security weaknesses. The key areas tested include:
- Authentication & Access Control – Checking login mechanisms, session management, and user roles.
- Data Storage & Transmission – Evaluating encryption and data protection measures.
- Business Logic Flaws – Testing for logic errors that hackers can exploit.
- API & Third-Party Integrations – Assessing risks from connected services.
- Automated & Manual Testing – Using security tools alongside expert-driven testing for deeper insights.
4. Analysis
Each vulnerability is assessed based on three key factors:
- Likelihood of Exploitation – How easy it is for an attacker to exploit the flaw.
- Impact on Business & Users – Confidentiality, integrity, and availability risks.
- Severity Rating – Categorized using OWASP, CVSS, and real-world attack impact.
5. Reporting
The penetration testing team provides a detailed VAPT report that includes:
- A summary of vulnerabilities and their severity levels.
- Technical details on how each issue was discovered.
- Recommended fixes with step-by-step remediation guidance.
- Compliance alignment (e.g., ISO 27001, SOC 2, GDPR, PCI-DSS, FDA).
6. Remediation & Retesting
Developers fix the vulnerabilities based on the recommendations. Security testers retest to confirm that:
- Fixes are properly implemented.
- No new security risks have emerged.
- The system is now more secure.
7. Consulting & Support
Post-testing consultation helps teams understand:
- How to strengthen security in future updates.
- Secure coding best practices.
- Compliance measures for ongoing protection.
8. Certification & Attestation
After successful testing and remediation, companies receive:
- A VAPT Security Certificate confirming compliance.
- A Letter of Attestation proving the system was tested against the latest cybersecurity standards.
Why is This Important in 2025?
With evolving cyber threats like AI-driven attacks, API breaches, and supply chain vulnerabilities, VAPT is no longer optional—it’s a necessity. Businesses that undergo regular security testing ensure data protection, regulatory compliance, and customer trust in an era of heightened cybersecurity risks.
Why Vulnerability Assessment and Penetration Testing (VAPT) is Essential in 2025
Cyber threats have grown more sophisticated than ever before. As we move through 2025, businesses of all sizes face an alarming rise in AI-powered cyberattacks, ransomware schemes, and previously unknown “zero-day vulnerabilities“. These threats can cripple an organization’s operations within minutes, leading to devastating financial and reputational consequences. This is where Vulnerability Assessment and Penetration Testing (VAPT) becomes not just important, but absolutely critical for business survival.
1. Uncovering Hidden Security Weaknesses Before Attackers Do
Every digital system has vulnerabilities – it’s simply a matter of whether you find them first or hackers do. VAPT serves as your organization’s proactive security checkup, thoroughly examining your networks, applications, cloud environments, and connected devices to identify weaknesses that could be exploited. This includes discovering misconfigured servers that accidentally expose sensitive data, outdated software with known security flaws, weak password policies that make brute force attacks easy, and hidden backdoors in your web applications.
What makes VAPT particularly valuable is that it doesn’t just identify theoretical vulnerabilities – penetration testing actually attempts to exploit these weaknesses just like a real attacker would. This approach reveals which vulnerabilities pose genuine risks to your business operations. Without regular VAPT, you’re essentially operating blind, unaware of the digital doors you’ve left unlocked until criminals walk right through them.
2. Preventing Financially Devastating Security Breaches
The financial impact of cyberattacks has reached staggering levels in 2025. Consider that the average cost of a data breach now exceeds $5 million according to recent industry reports, with ransomware attacks often demanding payments in the hundreds of thousands just to restore access to your own systems. Beyond the immediate extortion demands, businesses face regulatory fines, legal fees from customer lawsuits, forensic investigation costs, and the enormous expense of rebuilding damaged IT infrastructure.
Perhaps even more damaging are the indirect costs – the loss of customer trust that can take years to rebuild, the competitive advantage lost when intellectual property is stolen, and the operational downtime that can paralyze revenue streams. VAPT acts as an insurance policy against these catastrophic outcomes by systematically identifying and eliminating attack vectors before they can be exploited. The relatively small investment in regular security testing pales in comparison to the potential financial ruin a single successful attack can bring.
3. Meeting Ever-Tightening Compliance Requirements
The regulatory landscape for data protection and cybersecurity has become significantly more stringent in 2025. Laws like GDPR, HIPAA, PCI DSS, and various new state-level privacy regulations don’t just recommend security testing – they mandate it. Financial penalties for non-compliance have increased dramatically, with GDPR violations now potentially costing companies up to 4% of their global annual revenue. New SEC regulations require public companies to disclose cybersecurity incidents within just 72 hours of discovery, making robust preventative measures more important than ever.
VAPT provides documented proof that your organization takes cybersecurity seriously and complies with these critical regulations. The detailed reports generated during testing serve as evidence of due diligence, which can be invaluable during audits or in the unfortunate event of a breach investigation. In many industries, having up-to-date VAPT documentation is now as essential as maintaining proper financial records.
Related Guide: Compliance security audit – Explore now!
4. Protecting Your Most Valuable Asset: Customer Trust
These days, customer data is both your most valuable asset and your greatest liability. High-profile breaches continue to dominate headlines, and consumers have become increasingly wary about who they trust with their personal information. A single security incident can erase years of carefully built reputation in an instant, with studies showing that nearly 60% of customers will abandon a business after it experiences a data breach.
Modern VAPT goes beyond just checking technical boxes – it ensures that every aspect of your customer data handling meets the highest security standards. This includes verifying that sensitive information like credit card numbers and personal details are properly encrypted, that your authentication systems can’t be easily bypassed, and that your APIs don’t accidentally expose private data. In an era where “secure by design” has become a customer expectation rather than a luxury, VAPT provides the assurance that your systems truly protect what matters most.
5. Maintaining Business Continuity in the Face of Rising Threats
Cyberattacks today aren’t just about stealing data – they’re increasingly designed to disrupt business operations entirely. The ransomware epidemic has evolved into what security experts now call “triple extortion,” where attackers not only encrypt your data but also threaten to leak it publicly and notify your customers about the breach unless multiple payments are made. Even more alarming is the growing trend of attackers deliberately targeting backup systems to prevent recovery.
Regular VAPT testing specifically looks for these types of operational vulnerabilities. It identifies whether your disaster recovery systems are properly isolated from your main network, tests whether critical systems have adequate redundancy, and verifies that security monitoring can detect intrusion attempts before they cause widespread damage. For many businesses, the cost of just one day of downtime now exceeds what an entire year of comprehensive security testing would cost.
6. Keeping Pace With an Evolving Threat Landscape
Perhaps the most important thing to understand about cybersecurity in 2025 is that it’s not a destination – it’s a continuous journey. The techniques that worked against hackers last year may be completely ineffective today. Artificial intelligence has become a double-edged sword, with cybercriminals now using AI to generate highly targeted phishing emails, discover new vulnerabilities, and even create malware that evolves to avoid detection.
This is why VAPT can’t be treated as a one-time project. Effective security requires regular reassessment as new threats emerge and as your own systems change. Many organizations now incorporate VAPT into their DevOps cycles, testing every major update before it goes live. Others schedule quarterly or biannual comprehensive assessments to ensure nothing slips through the cracks. The most security-conscious enterprises maintain continuous monitoring combined with periodic in-depth penetration testing.
Who Needs VAPT in 2025? The Answer is Everyone
While all businesses benefit from security testing, some industries face particularly acute risks:
- Financial institutions and FinTech companies must comply with strict PCI DSS standards while protecting highly sensitive financial data
- Healthcare organizations responsible for protected health information (PHI) under HIPAA regulations
- E-commerce platforms processing thousands of customer payments daily
- SaaS providers whose compromised APIs could expose multiple clients simultaneously
- Government agencies defending against increasingly sophisticated state-sponsored attacks
However, it’s crucial to understand that small and medium businesses are no longer “too small to target.” Automated attacks don’t discriminate by company size, and research shows that over 60% of SMBs that suffer significant cyberattacks go out of business within six months. In today’s threat environment, considering VAPT an optional expense is like deciding not to lock your store’s doors at night because you’re “just a small business.”
Determining the Right VAPT Frequency for Your Organization
How often you should conduct security testing depends on several factors:
- High-risk industries (finance, healthcare, critical infrastructure): At least quarterly assessments, with continuous monitoring in between. Any major system changes should trigger additional testing.
- Medium-risk businesses (e-commerce, SaaS, professional services): Comprehensive testing every six months, with vulnerability scanning in the interim periods. More frequent testing if handling large volumes of sensitive data.
- Low-risk organizations (brochure websites, small local businesses): Annual in-depth testing at minimum, with automated vulnerability scans quarterly. Immediate testing following any significant website or system changes.
It’s worth noting that these are general guidelines – your specific risk profile might warrant more frequent testing. Many organizations are now moving toward continuous security validation approaches that provide ongoing assurance rather than point-in-time assessments.
The Bottom Line: VAPT is Non-Negotiable for Modern Businesses
In 2025, the question isn’t whether you can afford to implement regular VAPT – it’s whether you can afford not to. The consequences of inadequate cybersecurity have become too severe to ignore, with potential impacts ranging from seven-figure regulatory fines to complete business failure. More than just a technical safeguard, VAPT has become a fundamental component of responsible business operations, risk management, and corporate governance.
The good news is that VAPT has also become more accessible than ever. Modern testing methodologies provide clearer, more actionable results, and many providers offer flexible engagement models to suit different budgets and needs.
Why QualySec Remains the Leading Choice for VAPT Testing in 2025
QualySec has consistently proven itself as a top-tier provider of Vulnerability Assessment and Penetration Testing (VAPT) services. Their approach combines cutting-edge technology with expert human analysis to deliver actionable insights that strengthen your digital defenses.
1. Comprehensive VAPT Services for Modern Threats
QualySec offers six core testing services designed to address today’s most critical security challenges. Their web application testing uncovers vulnerabilities like SQL injections that could compromise customer data. For mobile apps, their experts examine both iOS and Android platforms for data leakage risks. IoT testing now covers 5G-connected devices, while their cloud security assessments include Kubernetes environments. API tests have been enhanced with automated fuzz testing, and network penetration tests now use AI to simulate advanced attack scenarios.
2. The QualySec Difference: Beyond Automated Scans
What truly sets QualySec apart is their balanced methodology. While many competitors rely solely on automated tools, QualySec’s security experts manually verify every finding, eliminating false alarms that waste valuable time. Their reports don’t just list problems – they provide clear remediation guidance tailored to your technical team’s skill level. The addition of blockchain-verified certificates in 2025 offers tamper-proof proof of your security posture for compliance needs.
3. Tailored Security for Organizations of All Sizes
From startups needing cost-effective solutions to enterprises requiring advanced threat simulations, QualySec adapts their services to each client’s specific needs. Their collaborative approach ensures developers receive security findings in formats that integrate smoothly with their workflow. For compliance-driven organizations, their updated reporting framework automatically maps vulnerabilities to regulatory requirements like GDPR and HIPAA, significantly simplifying audit preparation.
4. Proven Protection You Can Trust
With hundreds of successful engagements across multiple industries, QualySec has demonstrated their ability to protect sensitive systems against real-world threats. Their 2025 expansion into red teaming services provides high-risk industries with even more rigorous testing options. The combination of technical excellence, actionable reporting, and ongoing support makes them the preferred choice for businesses serious about cybersecurity.
Taking the Next Steps Toward Better Security!
Organizations looking to validate their security posture can start with QualySec’s sample reports to understand their testing depth. Their consultation process helps identify the most critical systems needing evaluation first. By choosing a provider that offers both detection and remediation support, companies can transform their security from reactive to proactive. Book a meeting now!
Latest Penetration Testing Report

Conclusion
Finally, VAPT testing, with its strong methodology, plays a critical role in assuring business security and resilience. It enables enterprises to discover and correct vulnerabilities, protect sensitive data, and strengthen their defenses against changing cyber threats.
VAPT testing is critical since it not only safeguards a company’s reputation and financial stability but also assures compliance with legal and regulatory standards. It is now time to act and strengthen your organization’s cybersecurity.
Don’t wait for the next cyber-attack to knock on your virtual door; instead, take proactive steps to protect your company’s future. Contact us immediately and let QualySec’s skilled team guide you to a safer, more secure, and resilient digital world.
Don’t leave your company’s future to chance; start your cybersecurity journey now!
FAQs
1. What is VAPT Report in Cybersecurity?
A VAPT report, or Vulnerability Assessment and Penetration Testing report, is an important document in the field of cybersecurity. It summarizes the findings of a thorough evaluation and testing procedure designed to discover vulnerabilities in an organization’s computer systems, networks, or applications. The document describes probable security flaws, their severity, and mitigation solutions for the identified vulnerabilities. The VAPT reports are critical for firms looking to improve their cybersecurity posture and defend themselves from possible threats and assaults.
2. What is the Use of VAPT?
VAPT is primarily examines and improves the security of an organization’s digital assets. VAPT aids in the detection of vulnerabilities, flaws, and security holes in computer systems, networks, and applications. It also uses penetration testing to replicate real-world attacks in order to assess the organization’s capacity to withstand cyber threats. Organizations may undertake VAPT to proactively detect and fix security concerns, decrease the risk of data breaches, and enhance their cybersecurity defenses, ultimately securing sensitive information and retaining customer and stakeholder confidence.
3. What is the VAPT Test?
VAPT is an abbreviation for Vulnerability Assessment and Penetration Testing. It is a type of security testing used to uncover security flaws in an application, network, endpoint, or cloud. Both Vulnerability Assessment and Penetration Testing have distinct advantages and performs in tandem to obtain comprehensive analysis. Vulnerability Assessment checks digital assets and alerts firms to any weaknesses. A penetration test exploits system vulnerability and identifies security holes.
4. What are the Four Phases of VAPT?
The four steps of the security testing technique are as follows and also reflect the steps involved in a vulnerability assessment:
- Planning: Defining the scope, objectives, and goals of the security testing, as well as selecting the proper testing methodologies and tools, are all part of this early step.
- Discovery: During this stage, security testers use techniques such as scanning and reconnaissance to obtain information about the target system, such as possible vulnerabilities and weaknesses.
- Attack/Testing: During this phase, attempts are made to exploit the vulnerabilities in order to assess the system’s vulnerability to assaults. Penetration testing, vulnerability scanning, and ethical hacking are all possibilities.
- Reporting: Following testing, a complete report is created summarizing the findings, vulnerabilities, their severity, and recommendations for risk mitigation and security improvement.
5. What is the methodology of VAPT report?
A VAPT report’s methodology generally includes the following steps:
- Preparation: Define the assessment’s scope, objectives, and norms of involvement.
- Discover vulnerabilities: and flaws using tools and procedures like scanning and data collecting.
- Exploitation: is the process of simulating real-world assaults in order to exploit vulnerabilities and assess system defenses.
- Analyze: the degree of vulnerabilities as well as their possible impact on the company.
- Reporting: Deliver a complete report that includes findings, suggestions, and mitigation techniques to improve security.
6. Which Tools Are Used for VAPT?
Vulnerability Assessment and Penetration Testing (VAPT) uses a variety of technologies to examine and improve cybersecurity. Among the best VAPT tools for effective penetration testing are:
- Metasploit: is a well-known penetration testing framework.
- Nmap: is a network mapping tool used to find open ports and services.
- A network protocol analyzer is Wireshark.
- Burp Suite is a tool for checking the security of online applications.
- OpenVAS is a vulnerability scanner that is open source.
- A web application security scanner called OWASP ZAP.
Watch the video to get more insights!
































































































































































































































































































































0 Comments