Network infrastructure is the backbone of modern organizations, enabling seamless operations, communication, and data flow. But with such reliance on interconnected systems, the risks of cyberattacks are higher than ever. This is why network infrastructure security is essential.
From protecting against unethical hackers to ensuring compliance with data privacy regulations, network security measures safeguard your organization’s digital ecosystem. But what are the types of network infrastructure security measures available, and which should you focus on for maximum protection?
This blog discusses the key types of network infrastructure security, offering a breakdown of the essential tools and strategies to bolster network defenses.
What Is Network Infrastructure Security?
Before we explore the specific types, let’s quickly define what we mean by network infrastructure security.
Network infrastructure security refers to the tools, processes, and policies designed to protect a business’s critical networking devices, including routers, firewalls, switches, and servers, from unauthorized access, misuse, or attacks. Whether you’re managing an enterprise-scale operation or running a small business, strong network security safeguards your sensitive data and ensures business continuity.
A trusted network security provider plays a key role in implementing and monitoring these protections.
“Read the ultimate guide on network security assessment.
Types of Network Infrastructure Security
Here are the principal types of network infrastructure security and how they function.
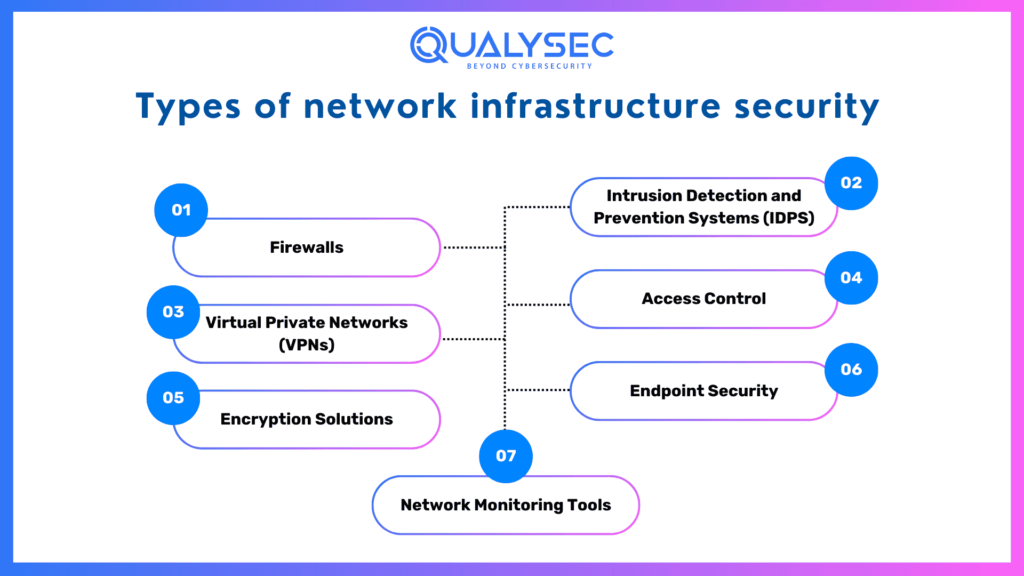
1. Firewalls
Firewalls act as the first line of defense in network security. They monitor and control incoming and outgoing traffic based on predetermined security rules. Think of a firewall as a virtual gatekeeper, ensuring only trusted data packets enter your network.
Types of Firewalls
- Hardware Firewalls: Physical devices placed between your network and external networks.
- Software Firewalls: Installed on individual devices like computers or servers.
- Cloud Firewalls: Hosted in the cloud and used to protect distributed networks.
Firewalls prevent cyber threats such as malware, unauthorized access, and Distributed Denial of Service (DDoS) attacks. They are fundamental in maintaining perimeter security for your network infrastructure.
“Discover more about penetration testing in network security.
2. Intrusion Detection and Prevention Systems (IDPS)
An Intrusion Detection and Prevention System actively monitors a network for suspicious activities or policy violations. Once a threat is detected, it takes action to block or neutralize it.
Two Key Components
- Intrusion Detection System (IDS): Detects and alerts admins to possible threats.
- Intrusion Prevention System (IPS): Automatically takes action to block or contain threats.
Using IDPS prevents cybercriminals from exploiting vulnerabilities in your network infrastructure. This layer strengthens defense mechanisms by actively countering real-time threats.
“Learn about network security audits here.
3. Virtual Private Networks (VPNs)
VPNs create a secure, encrypted connection between devices over the internet, ensuring sensitive data remains confidential during transit. For businesses with remote working policies, VPNs are indispensable.
Common Use Cases
- Securing remote employee connections to a corporate network.
- Protecting data exchanged between branch locations.
- Safeguarding communications while using public Wi-Fi.
A robust VPN strengthens network security by reducing the risk of data interception and man-in-the-middle (MITM) attacks.
4. Access Control
Access control limits who can access specific devices, applications, and data within your network. Rather than giving blanket access to all users, this model enforces the principle of “least privilege.”
Tools and Methods
- Authentication Systems: Multi-factor authentication (MFA) safeguards sensitive data.
- Role-based Access Control (RBAC): Assigns user access based on job roles.
- Biometric Security: Uses physical credentials like fingerprints or facial recognition.
By using access control mechanisms, organizations reduce the chances of insider threats and unauthorized access to critical network components. Explore more about network VAPT.
5. Encryption Solutions
Encryption converts sensitive information into unreadable ciphertext using algorithms, which makes it unusable to hackers without the decryption key.
Types of Encryption
- End-to-End Encryption (E2EE): Secures data from sender to recipient.
- Data at Rest Encryption: Encrypts stationary data stored on servers or databases.
- TLS Encryption: Secures data in transit over networks (e.g., HTTPS websites).
With data breaches making headlines every week, encryption ensures sensitive customer and business information is safe—even if data gets intercepted.
6. Endpoint Security
Endpoints include all network-connected devices, such as laptops, smartphones, or IoT gadgets. Endpoint security tools secure these devices to prevent entry points for cyberattacks.
Endpoint Protection Tools
- Antivirus Software: Detects and removes malicious files.
- Device Management Solutions: Enforces security policies on all endpoints.
- Threat Intelligence Platforms: Monitors potential vulnerabilities on devices.
Securing endpoints prevents phishing, ransomware attacks, or compromises stemming from weak personal device security. Learn more about network security testing here.
7. Network Monitoring Tools
Network monitoring tools ensure real-time visibility into your entire network infrastructure. By continuously inspecting traffic and alerting IT teams of irregularities, these tools prevent unnoticed breaches.
Features to Look For
- Anomaly detection
- Real-time traffic analysis
- Performance reporting
Continuous network monitoring keeps your infrastructure resilient while helping your IT team stay safe from evolving threats.
“Read a detailed guide on network penetration testing.
Latest Penetration Testing Report

How QualySec Stands Out as a Network Security Provider
When it comes to securing your network infrastructure, cutting-edge tools and expertise make all the difference. That’s where QualySec comes in. With a strong track record as a trusted network security provider, QualySec specializes in creating tailored security solutions for businesses.
Below are some reasons that make QualySec invaluable for your organization’s network defense:
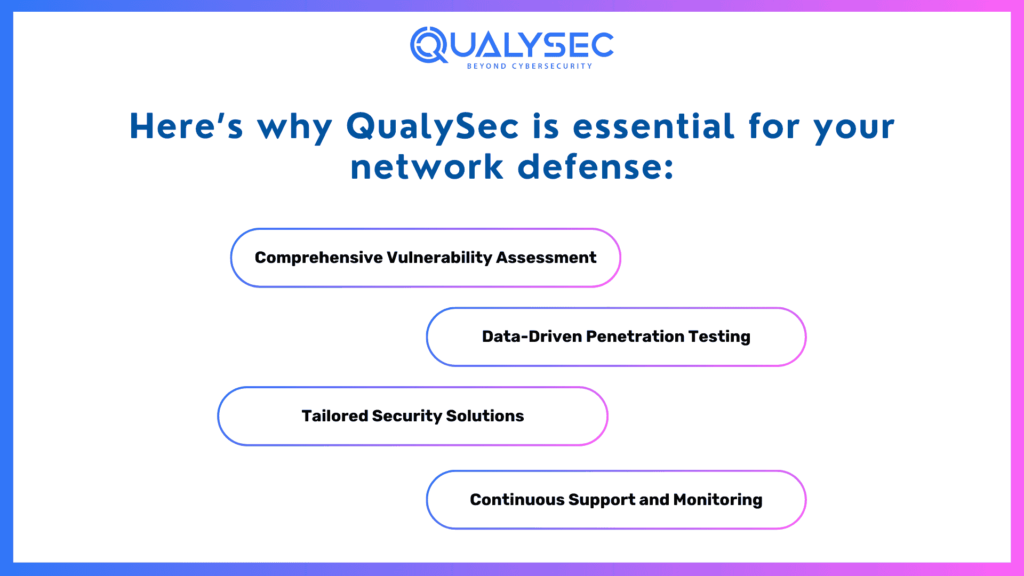
- Comprehensive Vulnerability Assessment: QualySec’s vulnerability assessments evaluate your network for security gaps, such as unpatched firmware, easily exploitable entry points, and configuration issues. This helps businesses identify and fix vulnerabilities before they become costly problems.
- Data-Driven Penetration Testing: Go beyond standard diagnostics with QualySec’s advanced penetration testing. Using a data-driven approach, their experts simulate real-world cyberattacks to proactively uncover weaknesses in your network systems. Detailed reports offer actionable recommendations to bolster your defense mechanisms.
- Tailored Security Solutions: No two businesses are the same, and neither are their network security needs. Whether it’s a small organization needing basic protection or an enterprise requiring a multi-layered strategy, QualySec offers personalized solutions to safeguard networks effectively.
- Continuous Support and Monitoring: Cyber threats evolve and QualySec ensures your defenses do too. With continuous support, monitoring, and expert guidance, QualySec provides peace of mind that your network stays secure 24/7.
The costs of neglecting network security can stretch beyond monetary losses. Data breaches, reputational damage, and operational disruptions are just a few examples of the fallout that can occur without adequate safeguards in place.
Successfully implementing various types of network infrastructure security measures, firewalls, endpoint detection systems, encryption, and beyond, requires expertise. Partnering with a specialized network security provider like QualySec ensures your business remains resilient in the face of evolving cyber threats.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Secure Your Network with QualySec Today!
Don’t leave your network vulnerable to threats. QualySec’s team of experts can help you build an impenetrable defense through vulnerability assessments, penetration testing, and customized solutions.
Take the first step toward securing your business. Contact QualySec now to learn more.












































































































































































































































































































































0 Comments