Cloud solutions are being used more in the country than ever before. More than 85% of enterprises aim to be fully in the cloud by 2025. The country’s data center market is expected to increase at a rate of 13% CAGR up to 2025. Still, the industry’s rapid growth creates new risks. Almost 84% of Philippine organizations were affected by breaches in 2024, and 32% said they reported incidents in the Philippines, who want to learn how to secure cloud infrastructure security. It describes what cloud infrastructure security entails, suggests practices that comply with the Philippines’ rules, such as the Data Privacy Act, highlights regional issues, and advises companies on what to consider when selecting a cloud security service.
What Is Cloud Infrastructure Security?
All the steps, technologies, and processes that keep server, storage, database, networking, and application security in cloud environments are collectively known as cloud infrastructure security. Both the security of on-site data centers and that of virtual systems utilized on AWS, Microsoft Azure, and Google Cloud are included in it.
In contrast to the traditional setup, cloud server security is based on a model where some responsibilities are shared. As a consequence, cloud providers are responsible for the security of hardware, storage, and the global cloud infrastructure. Once information, applications, and records are in the cloud, the business must take responsibility for them by ensuring their security.
Key elements involved in how to secure cloud infrastructure include:
- Identity and access management (IAM)
- Data encryption (in transit and at rest)
- Continuous threat monitoring and alerting
- Regular vulnerability assessments and penetration testing (VAPT)
- Compliance with data protection laws like the Philippines’ Data Privacy Act
Securing all layers of the cloud stack enables a business to prevent unauthorized access, thereby protecting against data breaches and service outages.
Why It’s Critical in the Philippines
The stakes for cloud security service are particularly high in the Philippines, where regulatory enforcement and cyber risks are both on the rise.
- Regulatory Pressure: The Data Privacy Act of 2012, implemented by the National Privacy Commission (NPC), requires all companies processing personal data to adopt proper organizational, physical, and technical controls. Failure to do so not only causes reputational damage but also risks costly fines and criminal liability.
- Remote Work Revolution: Remote and hybrid work patterns have become the new norm in tech startups and established industries since the outbreak. This decentralization operation adds additional points and access points to the network, significantly increasing the attack surface.
- Local Threat Landscape: The Philippines has experienced a significant surge in cyberattacks targeting both public and private sectors. Ransomware attacks on hospitals, phishing scams against e-commerce sites, and local enterprises face mounting pressure to secure their digital landscapes.
- Cloud-Specific Vulnerabilities: Many companies are using cloud-hosted CRMs, e-learning software, or e-commerce applications without implementing specialised security management. This dependence makes cloud infrastructure a prime target for cybercriminals.
These risks in context are compelling for Philippine-based organizations to go beyond elementary security controls and adopt a more formal, audit-ready process for protecting cloud infrastructure security.
Explore our insights on Infrastructure Security in Cloud Computing
10 Best Practices to Secure Cloud Infrastructure
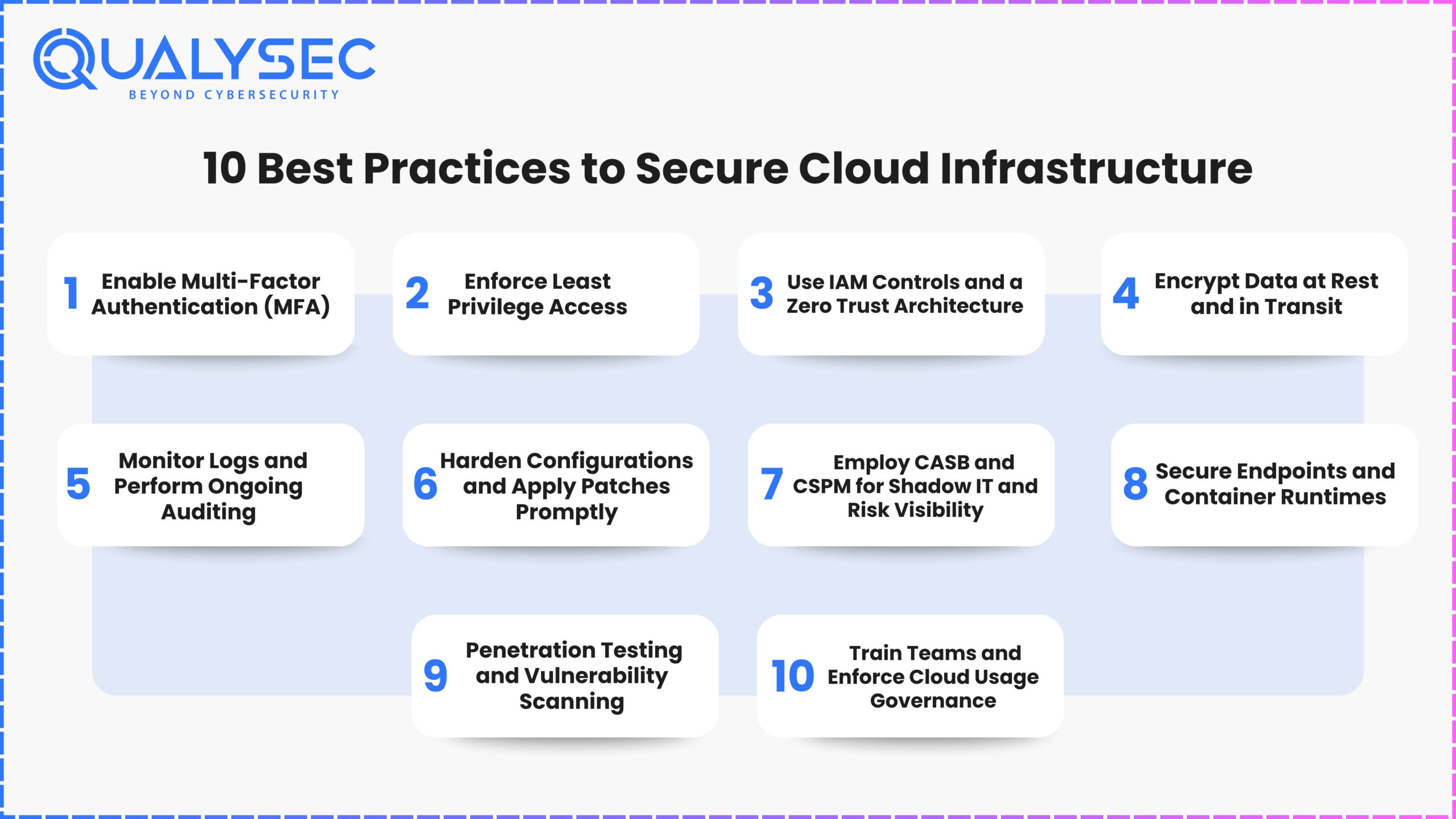
In the Philippines, with the rapid digital transformation of industries such as fintech, healthcare, and ecommerce, cloud infrastructure security is an imperative. The next 10 cloud infrastructure security best practices were derived from expert opinions on platforms such as Cisco, CrowdStrike, Medium, and Spot.io and have been tailored to meet both global standards and local conditions.
1. Enable Multi-Factor Authentication (MFA)
No account, particularly admin or DevOps, must be based on only a password. Authenticator apps are preferable to SMS because of the increasing risk of SIM swap fraud in Southeast Asia.
2. Enforce Least Privilege Access
Refrain from granting sweeping access to new employees or cross-functional teams. For BPOs and high-turnover startups, quarterly automated access reviews help eliminate legacy permissions.
3. Use IAM Controls and a Zero Trust Architecture
All identities, whether human or machine, need to be verified and authorized. Role-based access using AWS IAM or Azure AD is required. All internal traffic must be treated as untrusted until it is authenticated.
4. Encrypt Data at Rest and in Transit
Under the Philippine Data Privacy Act, encryption is now required. Encrypt stored data using AES-256 and data in transit using TLS 1.2 or later to safeguard customer data and stay compliant.
5. Monitor Logs and Perform Ongoing Auditing
Employ centralized logging tools such as AWS CloudTrail or GCP Cloud Security Audit Logs. Complement these with real-time alerts for detecting suspicious activity, such as attempts to access from outside Southeast Asia.
6. Harden Configurations and Apply Patches Promptly
Default settings are commonly used as an attack vector. Implement CIS benchmarks on operating systems and containers. For companies still using legacy systems, establish a patch schedule to mitigate vulnerabilities.
7. Employ CASB and CSPM for Shadow IT and Risk Visibility
Cloud Access Security Brokers can identify unauthorized tools being utilized by employees. Cloud Security Posture Management tools help monitor misconfigurations within multi-cloud setups, particularly for hybrid teams that utilize AWS and Azure.
8. Secure Endpoints and Container Runtimes
Laptops and mobile clients connecting to cloud platforms should be secured with EDR agents such as CrowdStrike Falcon or SentinelOne. Implement container runtime protection using tools like Sysdig to safeguard workloads.
9. Penetration Testing and Vulnerability Scanning
External penetration testers can emulate actual attacks against APIs, cloud functions, and access policies. Frequent vulnerability scans will identify problems before attackers can exploit them.
10. Train Teams and Enforce Cloud Usage Governance
Most breaches are the result of human error. Train employees to recognize phishing, limit file-sharing access, and track third-party SaaS applications integrated into your cloud environment.
Common Mistakes to Avoid
Even strong companies can get caught up in minor issues that compromise their cloud security. Most of the time, these problems arise because of being overconfident, having bad visibility, or using incorrect ways of thinking about cloud-native security.
1. Neglecting IAM hygiene
Giving away too many privileges, ignoring access to departed users, and relying solely on a few passwords are widespread mistakes. Most of the time, shadow identities are overlooked until regular audits are conducted in CI/CD.
2. Delaying or skipping patches
It is not uncommon for organizations to delay or verlook patches for containers, Kubernetes clusters, and SaaS applications, as they can cause disruptions. Unfortunately, it does not take long for attackers to find known vulnerabilities using bots after news of them is made public.
3. Relying only on perimeter defenses
Firewalls and VPNs are useful against internet threats, but you should watch for problems within your network from any rogue activity or password problems. Not all clouds come with threat detection based on behavior, which might leave you unaware of some significant dangers.
4. Lack of a governance cycle
Since cloud infrastructure security evolves constantly, a governance cycle may be missing. Leaving tools installed, test environments unattended, and executing permissions unnecessarily tend to increase risks. If API usage, configurations, and access are not regularly audited, more problems are likely to develop.
5. Misunderstanding the shared responsibility model
Most companies do not realize that the shared responsibility model requires them to handle some security. It is the providers who secure the infrastructure, while you are responsible for managing the rest, such as apps that access data and cloud data security.
These problems should be monitored more frequently than just once a year to be avoided. To ensure security, you must continually monitor your environment, implement security measures during development, and rectify misconfigurations as soon as they are identified.
Latest Penetration Testing Report

How Qualysec Protects Your Cloud
The Philippine company has its unique combination of compliance, infrastructure, and threat landscape needs for securing the cloud environment. Qualysec fills these gaps with services designed not only to international standards but also to the country’s very own regulatory and operational circumstances.
1. Cloud Penetration Testing & Vulnerability Scans
Qualysec mimics actual attack vectors to reveal configuration defects, API exposures, and identity mismanagement in cloud-native deployments. In addition to simply enumerating vulnerabilities, their comprehensive reports include prioritized remediation steps, supported by a business impact analysis.
Check out our detailed guide on Cloud Pen-Testing and Cloud Vulnerability Management .
2. Configuration Review & Zero Trust Consulting
Cloud systems often experience default settings, over-granting of access rights, or flat network designs. Qualysec conducts in-depth configuration reviews to establish security baselines and assists companies in transitioning to a zero-trust architecture, thereby reducing internal movement risk in the event of a breach.
3. Incident Readiness Response & Alignment with LGPD
As data privacy laws, such as the Philippines’ Data Privacy Act and Brazil’s LGPD, become increasingly applicable to cross-border SaaS activities, Qualysec constructs incident response models that align with these regulations to ensure organisations are capable of responding within mandated timeframes and processes.
4. CI/CD Integration and Security Automation
Qualysec integrates security natively into the development cycle. Through automated secret discovery, container scanning, and policy enforcement in pipelines, their solution helps DevOps teams deploy quickly without compromising security.
Through a concentration on actionable insights, regional compliance, and scalable automation, Qualysec keeps your cloud infrastructure resilient, compliant, and well-protected.
Conclusion
Cloud Infrastructure Security is more than just adherence to global best practices. It involves considering local laws, newer regional threats, and the unique architecture of your business environment. From multi-cloud configurations to compliance with the Philippines’ Data Privacy Act, every level of your cloud must have careful, ongoing protection.
Require professional assistance to evaluate and improve your cloud security posture?
Collaborate with Qualysec, the Philippines’ most trusted cloud security assessment, penetration test, and risk mitigation partner for enterprises.
Schedule a free consultation today to discover gaps, eliminate risks, and stay one step ahead of threats.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Frequently Asked Questions (FAQ)
1. How do you keep cloud infrastructure secure?
Ans: Organizations need to build their cloud infrastructure security in several different layers. One should always utilize identity access controls and configure systems properly; however, it’s also necessary to continue monitoring, use real-time alerts, employ encryption, protect endpoints, and conduct regular vulnerability checks. You should ensure that security is integrated into every action taken in the cloud, from initial setup to ongoing management and expansion.
2. What is cloud infrastructure security?
Ans: Cloud infrastructure security is about using specific rules, technologies, and methods to secure information and various applications in the cloud. It prevents unauthorized use, prevents data loss, and ensures the system’s reliability while adhering to industry- or area-specific compliance rules.
3. How do you maintain cloud infrastructure?
Ans: It covers more than just monitoring your server to ensure it is running correctly. It requires reviewing access logs, adjusting user access rights, promptly installing updates, regularly replacing passwords, verifying configuration changes, checking compliance status, and conducting regular security audits. Organizations should review their cloud security from time to time to handle any new dangers or updates to the network.















































































































































































































































































































































0 Comments