Amazon Web Services (AWS) is the market leader in cloud computing and drives businesses deeply with scalable computing capabilities, storage and rank networking capacities. Nevertheless, since organizations are still migrating workloads to AWS, security remains a top priority. Penetration testing is essential and has proven historically to turn up patterns of attack that malicious actors may have observed but not yet launched, changing their development. This is a complete guide to Amazon web services penetration testing in 2025 by Qualysec Technologies, covering the significance and methodology of the AWS penetration testing, and how we can help you secure your AWS environment.
What is Amazon Web Services Penetration Testing?
AWS pen testing is a process of testing one’s AWS cloud environment to find loopholes that hackers can exploit to penetrate it. Services like this help to identify misconfigurations, insecure IAM policies, exposed storage and more vulnerabilities that attackers could exploit. Shared Responsibility Model validates that Amazon secures the infrastructure and the customer is responsible for their applications and data. A penetration test (or pen test) allows security to ensure cloud services such as EC2, S3, RDS, Lambda and API Gateway are secure without revealing the weaknesses that they found.
Testers use tools like Pacu, CloudSploit, and ScoutSuite to perform automated vulnerability scans and manual exploits similarly. Penetration testing is possible in some areas of service for those activities but denied in others, such as denial of service (DoS) and malware testing. The reasons for regular AWS penetration testing include compliance with security standards such as ISO 27001, HIPAA, and PCI DSS.
Why Amazon Web Services Penetration Testing?
Amazon Web Services (AWS) is one of the biggest cloud platforms, empowering businesses worldwide with flexibility, scalability, and security. But with more and more organizations bringing their treasure and critical workloads to AWS, the number of cybersecurity threats has increased too. Organizations are always a target for cybercriminals, whose goal is to take advantage of vulnerabilities and without active security measures can end up with data breaches, noncompliance and financial loss.
Amazon web services penetration testing is an important security practice that helps identify potential vulnerabilities before attackers can exploit them. This entails ethical hacking methodologies to simulate real-life cyber attacks to find and resolve security cracks.
Here are the top reasons why penetration testing is applied to AWS –
Finding Security Gaps in Configuration of the Cloud
Misconfiguration is one of the most common security risks in AWS. It’s not uncommon that the same organizations leave S3 buckets publicly accessible, do not enforce strict IAM policies or misconfigured security groups. Penetration testing is to find out these weaknesses and ensure that cloud resources are safe and secure.
Preventing Data Breaches
Organizations routinely store sensitive customer and business data in AWS environments. If attackers compromise this information, it may lead to financial loss, reputational damage, and legal consequences, but taking proper care helps avoid these complications. Penetration tests can help secure the data from breaches, and organizations can achieve this by simply conducting a well-organized penetration test.
Ensuring Compliance with Security Regulations
Many industries need to comply with strict security frameworks like ISO 27001, HIPAA, PCI DSS, GDPR, and NIST. AWS penetration testing is useful in the context of tackling these regulations because of AWS’s help in identifying vulnerabilities that could otherwise result in noncompliance. They demonstrate due diligence by regularly distributing their security assessments.
Validating Security Controls
AWS has built-in security controls i.e. AWS WAF (Web application firewall), Security Groups, IAM policies and CloudTrail logs. Still, simply employing them will not suffice. However, penetration testing verifies that these security mechanisms succeed and can resist real-world attack scenarios.
Enhancing Incident Response Readiness
When a cyber-attack targets an organization, it must take swift action to stop the threat. AWS penetration testing enables security teams to determine their capacity to handle incidents through simulated attacks. This improves their ability to detect and respond to threats and thus will be able to mitigate them effectively.
Decreasing the Possibility of Insider Threats
Not all cybersecurity threats are external attacker threats: employees, contractors and third-party vendors can be just as dangerous to your company. IAM roles, access privileges, and user behaviour are evaluated with Amazon web services (AWS) penetration testing to ascertain if access to data is at risk and that user permission is excessive.
Protecting Web Applications and APIs
Web applications and APIs enable most AWS-based services. Yet, such applications are vulnerable to attacks such as SQL injection, cross-site scripting (XSS), and broken authentication. AWS penetration testing provides an evaluation of web applications for weaknesses and helps in their strengthening of security.
Avoiding Financial Loss and Downtime
Data theft and theft of other related information can lead to hefty financial losses. Regulatory fines and operational downtime are other effects of a security breach. AWS penetration testing forewarns businesses of a wide range of vulnerabilities and mitigates the damage resulting from exploitation.
“Related content: Read our guide to Cloud Penetration Testing“
Amazon Web Services Penetration Testing Methodology
The structured approach of Amazon web services penetration testing helps to assess the cloud security and finding out for the vulnerabilities is followed. The methodology is composed of several phases to assess a broad range of an AWS environment.
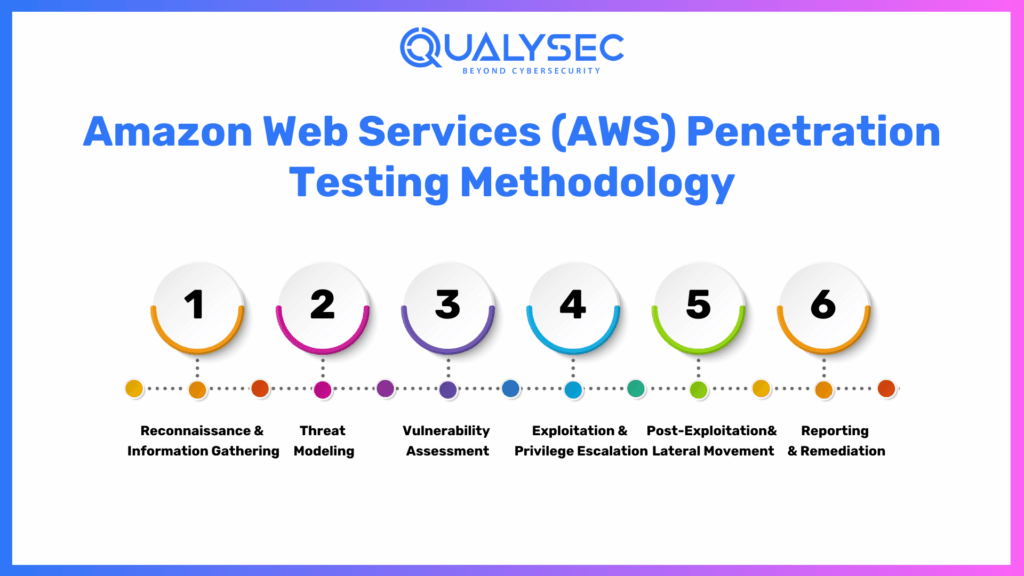
Reconnaissance & Information Gathering
Before launching an attack simulation, ethical hackers do certain tests on the AWS environment. This includes:
- Find publicly accessible AWS services such as S3 buckets, EC2 instances, and API Gateways.
- Analyzing specific DNS records using the subdomains as well as SSL/TLS configurations.
- Viewing AWS Identity and Access Management (IAM) policies to know about user roles, privileges and possible misconfiguration.
- Scan exposed secrets, credentials, or accessible access controls.
In this phase, the aim is to gather as much information as you can about the target AWS environment, but won’t go through it directly.
Threat Modeling
After collecting information security testers will develop a threat model which will tell what kinds of potential attack vectors are in place. This phase includes:
- Studying the cloud architecture to find out the data flow between AWS services.
- Determine the privilege escalation risks with IAM roles and permissions.
- Scanning the third-party integration and APIs for security weak points.
- Examine network security group and firewall rules and determine misconfigurations that would enable unauthorized access.
By applying threat modelling to vulnerabilities, one can prioritize them based on risk and potential impact.
Vulnerability Assessment
During the Amazon web services penetration testing phase, the penetration testers use automated and manual tools to detect security flaws like:
- It scans through all AWS services for misconfigurations like (public S3 buckets, open security groups, and outdated software on EC2 instances).
- API endpoint identification, without authentication, may be possible to inject in.
- Checking roles and permissions if an IAM policy is over-privileged.
- Looking for AWS access keys and credentials that were leaked into public repos.
- ScoutSuite, CloudSploit, and AWS IAM Access Analyzer are popular vulnerability scanning tools that can be used.
“You might like to explore: AWS Security assessment services“
Exploitation & Privilege Escalation
Once ethical hackers identify a vulnerability, they try to gain unauthorized access to the system by exploiting it. This includes:
- Escalating privileges within the AWS environment due to insecure IAM configurations.
- Implementing Server-Side Request Forgery (SSRF) attacks to get restricted services.
- Attempts to penetrate through EC2 instances to gain unauthorized access and attacks on container escape using AWS Fargate.
- Checking for ingress and egress of data and privilege escalation across insecure API endpoints.
Security vulnerabilities are exploited to help determine the impact in the real world.
Post-Exploitation & Lateral Movement
After gaining an entry point, attackers will then go on to try and move laterally through the AWS environment.
- S3 buckets contain sensitive files that are being accessed.
- Fetching from AWS Secrets Manager or environment variables.
- Making use of compromised IAM roles to allow you to also have access to certain services on AWS.
- The creation of such rogue IAM users that’d be used in future are persistence mechanisms.
This part assumes what an attacker could get if they hack into the AWS infrastructure.
Reporting & Remediation
Upon completion of the penetration test, the findings from the assessment are documented in a full report including:
- The list of discovered vulnerabilities is grouped according to the severity of their effects.
- Steps taken during an exploit and the effects of that.
- Specifics on how to remediate against failure of the security practice.
- Adding plans to retest to make sure vulnerabilities have been fixed.
This final piece of AWS does help users of AWS to be better off with their cloud security posture making them more secure and preventing future attacks.
Download an AWS penetration testing report here!
Latest Penetration Testing Report

How Qualysec Technologies Can Help with AWS Penetration Testing
Amazon Web Services (AWS) is a very important cloud platform, and to secure the AWS environment, it is necessary to continuously monitor as well as perform proactive security assessments. There are much more complex cyber threats cropping up all the time and AWS penetration testing is an important practice for organizations. Amazon web services penetration testing by Qualysec Technologies enables businesses to find and patch their security vulnerabilities and guard against this for a secure cloud cybersecurity stance.
Comprehensive AWS Security Assessment
Qualysec Technologies performs its AWS penetration test in a manner that exposes the vulnerabilities present in your cloud infrastructure. We review the AWS Identity and Access Management (IAM) policies, security groups, APIS endpoints and configurations on servers across the board. Given this, we analyze the security weakness of an Amazon S3 bucket, an AWS Lambda function, and an EC2 instance and we try to detect it before those malicious actors can exploit it.
Cloud Compliance & Regulatory Support
Many industries prescribe compliance frameworks like GDPR, HIPAA, PCI DSS, and ISO 27001. Qualysec assists businesses in aligning AWS security with industry best practices, making sure that their business sticks to regulatory standards. Our penetration testing reports provide actionable insight to remediate compliance gaps and help them to fulfil the audit requirement.
Advanced Threat Simulation
We simulate real-world cyber attacks to test the AWS endpoint’s security resilience. At the API, we do privilege escalation tests, API abuse simulations, cloud misconfiguration exploitation, and lateral movement analysis in AWS. By taking an active stance in this, businesses can learn what attackers might try to do to access their cloud infrastructure.
Secure Configuration Review
Misconfigured AWS services commonly cause data breaches. For AWS, we review the configurations to see that they follow the principle of least privilege – key AWS configurations like IAM roles, security group rules, and firewall settings, to protect the permission granted to your account. We review your cloud storage (S3 buckets), your database permissions and your network access controls to as far as possible limit the security risks.
Actionable Remediation & Expert Guidance
Unlike many other vendors, at Qualysec we do not only uncover the vulnerabilities – we do also deliver the remedial steps. Get reports of security flaws in-depth, with risk levels and step-by-step advice on how to secure AWS.
Continuous Cloud Security Monitoring
Security threats on AWS always evolve and a one-time penetration test is not enough. Looking into the future, Qualysec continues to provide ongoing security monitoring solutions so that the organization can detect and deal with threats in actual time.
“Learn more in our detailed guide to AWS cloud security services“
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
Companies that use cloud services cannot ignore Amazon Web Services penetration testing as a crucial security practice. The nature of cyber threats is becoming increasingly sophisticated, and as a result, organizations must approach alarmingly, identifying and fixing security vulnerabilities within their AWS environment. Businesses can strengthen their AWS infrastructure against possible attacks by following the best practices, using the eligible tools and partnering with security experts like Qualysec Technologies.
Doing AWS penetration testing today will save you from security breaches and staying compliant in 2025 and beyond. Seek the professional help of Qualysec Technologies to perform a comprehensive security assessment! Schedule a meeting now!















































































































































































































































































































































0 Comments