In the current regulatory and threat-intense environment, penetration test report samples provide not only technical texts. They are evidence of the cyber-sense of Singapore-based businesses that work in a framework of regulations imposed by the Personal Data Protection Act (PDPA).
As cloud adoption in Southeast Asia develops, with a forecast of $40.32 billion by 2025 (IDC), and 85 percent of IT and business services are already cloud-based in Asia-Pacific (ISG), the area of concern is growing. In Singapore, where both AWS and Azure are launching local data centers and accelerating the digital shift, regulatory pressure is also on the rise. Even one not properly configured may lead to non-compliance, fines, or a reputation loss.
That is when a professional penetration testing report comes in handy. The way you report on vulnerabilities and the level of detail provided can play a significant role in influencing compliance, technical remediation, and executive decisions made, whether you are a FinTech startup gearing up to receive audits or a healthcare provider looking to determine your vulnerability auditing against the PDPA.
What Is a Penetration Test Report?
The penetration test report is an official document that includes the outcomes of such virtual attacks performed on your systems. It contains the vulnerabilities identified, their analysis to determine their severity, and a resolution that can be implemented to mitigate risk.
Who Uses It?
- CISOs and Security Leaders: To evaluate the present security state and implement smart investment choices.
- CTOs and Engineering Heads: To learn gaps in the technical environment that could then affect the infrastructure performance and resilience.
- DevOps Teams: To find the misconfigurations and insecure deployment practices quickly.
- Compliance and Risk Officers: They assist with the audits and the regulatory submissions (PDPA, etc, ISO 27001, PCI-DSS).
Why It’s More Than Just a Checklist
- It is beyond filling forms. An effective report also sorts out the vulnerable points that must be worked on and why.
- It allows risk-based decision making as opposed to blind patching, time, and disruption.
- In the regulated industry within Singapore, it becomes part of an official document on due diligence and verification of security.
CTA: Download Our Pentest Report Sample to See What a Professional Assessment Looks Like
Key Components You’ll Find in Professional Penetration Test Report Samples
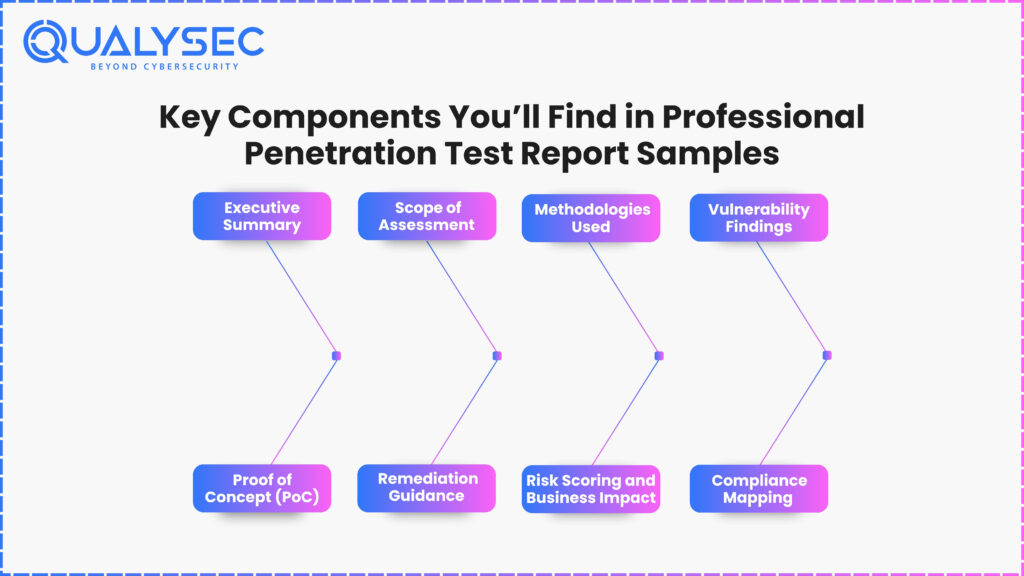
A good penetration test report not only provides a list of the vulnerabilities. It provides the security executives and technology staff with decision-making information to toughen up infrastructure, accommodate compliance, and focus investments. This is what a detailed and properly organized report must comprise:
1. Executive Summary
Leadership team brief, non-technical summary. It underscores the number of critical vulnerabilities identified, the possible business impact (e.g., risk of exposing customer data), and the risk posture. As an example, “3 of 12 findings present a high threat of harmful impact on the data confidentiality according to the guidelines of PDPA.”
2. Scope of Assessment
Defines exactly what was tested. This could include:
- AWS EC2 instances across 2 regions
- Azure Blob storage configurations
- Internal APIs for transaction validation
- User roles and permissions within IAM
It also mentions what was excluded (e.g., third-party SaaS tools), ensuring clarity.
3. Methodologies Used
Details the ethical hacking standards followed, such as:
- OWASP Top 10 for web applications
- NIST SP 800-115 for network security testing
- CREST for red team simulations
This helps you ensure the test aligns with both technical expectations and audit requirements.
4. Vulnerability Findings
Each issue is described with precision and backed by evidence. For instance:
- Critical – Open S3 bucket storing user ID proofs
- High – Broken authentication on the admin login endpoint
- Medium – Outdated TLS protocol on public API
- Low – Clickjacking vulnerability on login page
Each entry includes affected systems, how it was discovered, and real-world implications.
5. Proof of Concept (PoC)
Actual screenshots, intercepted payloads, or command outputs demonstrating exploitation. For example, a screenshot showing access to confidential employee records via misconfigured permissions.
6. Remediation Guidance
Clear, prioritized, and platform-specific fixes. Instead of vague suggestions, it provides:
- AWS CLI commands to restrict public S3 access
- Azure portal steps to adjust RBAC roles
- Sample secure headers for web apps
It’s written so DevOps teams can implement it without external assistance.
7. Risk Scoring and Business Impact
Uses CVSS 3.1 scores, mapped to business units. Example: “A vulnerability in the payments API (CVSS 9.8) can lead to revenue loss due to unauthorized transactions.” It ties technical risk directly to business operations.
8. Compliance Mapping
Aligns findings to regulations like ISO 27001 Annex A.12, SOC 2 CC6.1, or Singapore’s PDPA Clause 24. This helps compliance teams prepare for audits with mapped action items.
CTA: Talk to Our Experts to Learn What Goes into a Compliant Report
What Makes a Great Penetration Test Report?
Every pentest report is not just the same. The most successful ones not only give information, they inspire change. When you are assessing the samples of reports, the following qualities are what may set the difference between a good and a bad report:
1. Balanced Language for Technical and Non-Technical Teams
An excellent report gets written in a way that a security engineer and the CISO can take action. Whereas a developer receives potential technical fixes on a line-by-line basis, on the other end of the phone, decision-makers are told summaries fashioned on lines of business risk, compliance, and priority.
2. Clear, Actionable Remediation Path
Instead of vague recommendations like “review access policies,” a strong report includes platform-specific fixes, code snippets, command-line instructions, and testing validation steps. It turns findings into next steps.
3. Zero False Positives
Proper reports do not overwhelm the teams with pointless alerts. Every discovery is presentable, replicable, and has a concrete effect in the real world. This is time-saving, prevents alert fatigue, and makes teams address what is important.
4. Support for Engineering Workflows
The report must provide your existing systems with output formats, ex, integration into JIRA to create tickets, OR JSON/CSV export into CI/CD tools such as GitLab or Jenkins. This leaves it ready to effortlessly transfer to the development or DevSecOps teams.
5. Tailored Insights Based on Industry
Standardized reports fail to hit the target. Quality assessments capture the individual threat profile and compliance requirements of your industry. As an example, Softbank Interview will consider the delivery of FinTech APIs with more API rate limiting and KYC data leakage reporting, whereas Healthcare clients will receive a report on PHI security and HIPAA compliance.
CTA: Curious how these phases and reporting best practices come together in real engagements? Read this blog from Qualysec to understand the full penetration testing lifecycle and how detailed reporting plays a vital role at every stage.
Singapore-Specific Considerations
Penetration testing companies in Singapore does not merely focus on being technically accurate, but focuses on being regulatory aligned. Local businesses should also make sure that all reports correspond to regional compliance schemes and auditing procedures.
1. Alignment with PDPA and MAS-TRM Guidelines
The Personal Data Protection Act (PDPA) of Singapore insists on accountability and protection of personal data in all the lifecycle stages of the data. In the meantime, MAS-TRM issued by the Monetary Authority of Singapore requires profound risk analysis, especially of financial institutions. A strong pentest report can assist in illustrating a proactive rather than reactive identification and treatment of risks, which is essential under either.
2. Tailored Reporting for Singapore’s Business Ecosystem
Templates used across the globe tend to overlook the regional security anticipations. Local businesses require reports that take into consideration how data is stored, processed, and accessed by the law in Singapore. This is inclusive of alluding to local data centers, how residency would take place, and how data sovereignty terms in client agreements are being met.
3. Support for Internal and External Audit Readiness
The report that is well structured assists IT and compliance departments in the case of internal audit and regulatory inspection. A report on the localized pen test offers sanity and credibility to authorities or clients when attempting to prove due diligence.
4. Strengthening Client Trust and Business Continuity
B2B clients are causing pressure on enterprises or startups to demonstrate their security posture. Cloud and network system Singapore-specific reports confirm that testing, monitoring, and alignment with best practices of cloud and network system practices are reinforced to boost long-term partnership and resilience planning.
CTA: Check out Qualysec’s advanced penetration testing services
Red Flags to Watch in Low-Quality Reports
Not all penetration test reports are created equal. Some fail to deliver clarity, value, or actionable outcomes. Here’s what to watch out for when evaluating subpar reports:
1. Generic Templates Without Context
When this report appears to be a paste job and has placeholders or does not refer to your physical infrastructure (e.g, it uses AWS region or app architecture), then you may not be specific to your environment.
2. No Evidence for Vulnerability Claims
Lacking or ambiguous screenshots, unedited log extracts, or unjustified results make it a challenge to confirm what indeed had been tested and what should be corrected.
3. Lack of Prioritization
A good report highlights which vulnerabilities need urgent action. If all issues are lumped together without impact assessment or risk ratings, your team won’t know what to tackle first.
4. Missing Testing Methodology
The reports that do not specify whether the authors implemented the well-known frameworks (such as OWASP or NIST) do not provide any starting point to rate the quality of test completeness or industry-specificity.
5. One-Size-Fits-All Remediation Advice
An indication of a red flag is when the fix recommendations are too generic (patch the system). Your DevOps or security teams require environment-specific advice that they will be able to carry out.
6. No Mention of Business Impact or Compliance Mapping
Especially in regulated sectors, reports should connect technical flaws to operational or compliance consequences. Absence of this link makes the report difficult to use during audits or board-level presentations.
7. Unstructured Format
A poorly organized report with no executive summary, unclear sectioning, or inconsistent labeling slows down response time and often causes more confusion than clarity.
CTA: Want to get deeper into pentesting standards and methodologies? Read this in-depth blog from Qualysec to learn how professional testers approach structure, scope, and reporting with precision.
Why Qualysec’s Reports Stand Out
Penetration test reports are not created with equal care. At Qualysec, we are interested in ensuring that all the reports are actionable, ready to audit, and fit for both executives and developers. The difference in ours is as follows:
- Singapore PDPA-aligned reporting: All reports will have controls that are aligned with the Personal Data Protection Act (PDPA), so businesses with cloud-first and data-driven approaches will be locally compliant.
- Clear executive summaries + dev-ready technical sections: Business non-technical users will have access to high-level information about the risk, whereas the technical users will have detailed information about vulnerabilities, along with reproduction and mitigation steps.
- Tailored to AWS, Azure, GCP environments: We tailor the report design and its conclusions to the cloud infrastructure that you run on, and there are no generic templates.
- Verified by certified pentesters (OSCP, CREST, etc.): All the reports are read by certified professionals having practical experience with red teams and production cloud evaluation.
- Zero false positive guarantee: All vulnerabilities are checked and then added to the report. Your team will not spend time having to pursue non-problems.
CTA: Download Sample Pentest Report for Singapore Businesses to see how we present findings that are both boardroom-ready and developer-friendly.
Conclusion
A penetration test report sample is not only a document. It is intellectual property. It provides evidence of due diligence, direction in technical knowledge, and client-regulator trust to companies in Singapore that have been negotiating compliance challenges such as PDPA and MAS-TRM.
Not every report brings the same value, however. A good report, made professionally, can make a difference between successful patching and unsolved risk management.
If you’re preparing for an audit, onboarding enterprise clients, or simply aiming to strengthen your cloud security and application security, having the right report matters.
Ready to see what a high-impact report looks like? Contact Qualysec today to schedule a consultation or request a sample report customized for your business in Singapore.
Frequently asked questions (FAQs)
Q1: Who typically uses a penetration test report?
Ans: CISOs, CTOs, DevOps engineers, and compliance teams use penetration test reports to quantify, assess, and prioritize security risks. They are also applicable to internal audits, client reporting, such as those stated in the Singapore PDPA and MAS-TRM regulatory checks.
Q2: How often should penetration tests be conducted in Singapore?
Ans: Penetration tests are normally held once a year or twice a year by most businesses. But in the case of fintech, healthcare, and cloud-native Singapore-based firms, a quarterly test schedule or a change in significant code or infrastructure would be a good idea.
Q3: What is the PDPA’s relevance to pentest reporting?
Ans: Personal Data Protection Act (PDPA) provides that personal data should be secured. Penetration test report assists in proving that appropriate technical measures exist and that weaknesses that impact data secrecy are overcome.
Q4: How long does it take to receive the final report?
Ans: Based on the depth, the majority of professional companies, such as Qualysec, would provide a report after the assessment within 510 business days, together with a client walkthrough experience.
Q5: Can the report be used during client due diligence or vendor audits?
Ans: Yes, a well-structured report with mapped compliance sections (e.g., ISO 27001, PDPA, MAS-TRM) is ideal for client assurance and vendor risk assessments, especially for B2B businesses operating in Singapore.
Q6: What should I do if I don’t understand some of the technical terms in the report?
A: Qualified vendors such as Qualysec have an executive summary, definition of severity, and also provide post-report sessions to provide explanations of results and mitigating strategies in business terms.












































































































































































































































































































































0 Comments