Imagine someone attempting to break into your home to test how secure it is. Now imagine your software, applications, and networks as that house. Penetration testing in software testing or pen testing, works similarly by hiring an ethical hacker who comes in (legally) to break in to find all the weaknesses before the bad guys do. It’s a business about staying one step ahead in the cybersecurity game.
Penetration testing is a process in software testing that ensures the security of systems against cyber threats. It’s not just about the technical aspect but also more of a strategy to ensure continued trust and avert costly breaches. Let us explore what penetration testing is, the types, techniques, benefits, and how it is done. This article will reveal why pen testing is a cornerstone in modern cybersecurity practice.
Penetration Testing: The Basics
So what is penetration testing in softeware testing? In simple words, it’s a mock cyberattack. The objective is to find vulnerabilities that hackers can exploit to gain unauthorized access to your software, network, or systems. It’s like running a fire drill, except this time, it’s hackers instead of flames.
So why bother?
- Proactive Defense: Weaknesses are rectified before hackers start exploiting them.
- Compliance: Most benchmarks such as GDPR and PCI DSS require regular pen testing.
- Peace of Mind: You can sleep at night knowing your system is secure, and so can your customers.
Pen testing is recommended by cybersecurity experts. In fact, most cybersecurity experts and authorities recommend pen tests as a proactive security measure. For instance, in 2021, the U.S. federal government urged companies to use pen tests to defend against growing ransomware attacks.
Not only big businesses need penetration testing; small businesses, startups, and even lone developers should. Cybercrime does not care if you are big or small. A single weakness can mean the difference between losing money, a reputation, or facing lawsuits.
“Related Read: Software Penetration Testing: A Complete Guide
How Does Penetration Testing Work?
Penetration testing, more or less, is a detective story. This detective would be the ethical hacker who needs to find every one of those secret vulnerabilities. Now, here comes the plot.
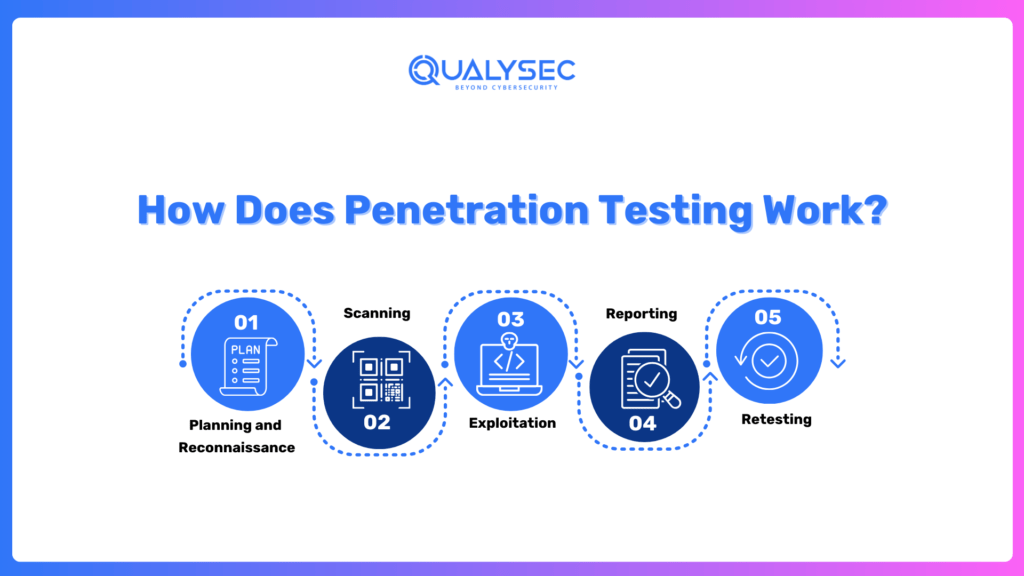
1. Planning and Reconnaissance
This is the reconnaissance phase. Here, testers research the target system—its architecture, technologies, and possible points of entry. It’s basically casing a joint before a heist. The more information testers have about the system, the better their chances of identifying vulnerabilities.
2. Scanning
After this, scanning takes place whereby automated tools scan the system to look for vulnerabilities. This could include:
- Static Analysis: In this analysis, one finds flaws in the code without running it.
- Dynamic Analysis: One shows how an application will run in real-time.
Scanners provide testers with a road map of what can be identified. Scanners check everything: open ports, software versions for known vulnerabilities, etc.
3. Exploitation
This is where things get interesting. Testers look for vulnerabilities as a hacker would, trying to inject bad code, bypass authentications, and even gain access to sensitive data. This test looks at the possibility of exploitation.
4. Reporting
Finally, the tester gathers his or her pentesting report in software testing. These are the results that contain the following:
- Vulnerabilities detected
- Risk levels associated with the vulnerabilities
- Suggestions for how they should be addressed.
The report becomes a guide for the organization on what to focus on and fix.
5. Retesting
After patching the vulnerabilities, it is good to retest. You wouldn’t fix a broken lock without checking that it works, would you? Retesting ensures that the applied fixes are effective and have not introduced new vulnerabilities.
Latest Penetration Testing Report

Penetration Testing Methodology
1. Black Box Testing
This is an approach where the tester is not aware of the system or network and simulates how an external attacker would feel to test the ability of an organization to identify and react to threats.
2. White Box Testing
Here, the tester will have full knowledge of the organization’s IT infrastructure, source code, architecture diagrams, and network configurations. This approach is best suited for rigorous testing of complex systems.
3. Gray Box Testing
This method is a mix of black-and-white box testing where the tester has partial knowledge of the system. This method could balance efficiency with reality.
4. Continuous Penetration Testing
Instead of doing frequent testing, this approach does continuous testing and assessment of the changing threats in real-time. Continuous testing is quite efficient in dynamic environments like cloud and DevOps pipelines.
Each of these types of testing has a purpose and is selected based on the needs of the organization and the nature of the system being tested.
Common Techniques Used in Penetration Testing
Pen testers have a bag full of tricks for unearthing vulnerabilities. The customized type of penetration tests in Software security testing that interest various organizations’ IT systems may be carried out. The majority types are the following:
1. Network Penetration Testing
It operates on internal and external networks and is applied to detect the vulnerability of open ports, protocols, and systems without a patch-up. It is highly sensitive to unauthorized access to classified data.
2. Web Application Penetration Testing
The scanning of web applications against SQL injection, XSS, and failure in terms of authentication and session management are considered general weaknesses.
3. Mobile Application Penetration Testing
It involves vulnerabilities in data, weak encryption, insecure APIs, and weak session handling within applications.
4. Social Engineering Penetration Testing
This tests the human element of cybersecurity; it utilizes phishing attacks, pretexting, and other means of manipulation to check a person’s level of awareness.
5. Cloud penetration testing
They create their cloud-based testing methodology that emerges due to misconfiguration, data storage that is not secured, and a lack of proper access controls. Such issues are becoming more and more critical with a higher adoption rate of clouds.
6. IoT and OT Penetration Testing
This malware attacks the IoT devices along with the OT systems that run parallelly with vulnerabilities such as unsecured firmware, default weak credentials, and unencrypted communication.
7. Physical Penetration Testing
This deals with the assessment of whether the access of data centers, server rooms, and other restricted facilities poses risks to potential unauthorized access in physical security controls.
Each of these attacks is designed to mimic a real attack scenario so that organizations realize where their defenses break down.
Tools of the Trade
Pen testers need the most powerful tools for the job. Some of the most popular ones include the following:
- Nmap: This one’s used for network discovery and mapping.
- Burp Suite: A favorite for web application testing.
- Metasploit: Framework for developing and testing exploits.
- OWASP ZAP: It’s one of the open-source tools for finding web vulnerabilities.
- Wireshark: For network traffic analysis.
Each has a function, such as detecting open ports, inspecting traffic, or even taking advantage of known weaknesses.
The Benefits of Penetration Testing in Software Testing
Why invest in pen testing? Here’s what you stand to gain:
- Enhanced Security: You are not merely finding weaknesses, but actively closing them. This only helps you bolster your defenses when actual attacks are perpetrated.
- Regulatory Compliance: Many industries require that penetration testing is conducted on a regular basis as part of the security standards of a firm.
- Trust Building: Customers and other stakeholders will have more trust in your systems being secure.
- Saves Money: Save you from potential financial and reputational damage by patching vulnerabilities before a breach occurs.
- Realistic Risk Assessment: Know exactly how vulnerable your system is and, based on the actual risks, prioritize fixes accordingly.
Penetration testing is not just an exercise in compliance but a culture of security within an organization.
Real-World Example: Why Pen Testing Matters
Let’s take a quick example. Imagine a popular banking app that is increasingly gaining popularity. A penetration tester discovers that an unprivileged user could transfer money by exploiting a vulnerability. If a malicious hacker exploits this, the bank will lose millions and, more importantly, customer trust.
Because of penetration testing, the bank fills the gap before exploitability, saves the day, and in return, it also saves the bank’s reputation. This anticipation behavior is exactly the reason by which secure organisations lead and mark the difference against others that shall face cyber assaults.
When Should You Conduct Penetration Testing?
Timing makes the difference here, and when penetration testing time should be caught:
- For each newly launched software: do its security check just before the roll out.
- Post Major Update: New functionality generally comes along with new vulnerability
- Schedule: Attack methods evolve and so should yours.
After a Security Incident: Understand what led to the breach and how not to make that mistake next time.
Having an ongoing security process with the added support of periodic schedules plus ad-hoc for critical updates makes sure the system is well-covered.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Overcoming Challenges in Penetration Testing
1. Resource Constraint
- Challenge: Smaller organizations do not have resources—time, personnel, or tools—to carry out penetration tests in depth.
- Solution: Focus on critical systems and high-risk areas first. Also, outsourcing to specialized cybersecurity firms can help maximize efficiency and impact.
2. Evolving threats
- Challenge: Cyber threats are evolving constantly, and attackers are inventing new techniques and exploiting previously unknown vulnerabilities.
- Solution: Penetration testing methodologies need to be updated, and current threat intelligence must be integrated into the testing strategies. Penetration testers must be provided with regular training so they can stay ahead of emerging attack vectors.
3. False Positives
- Challenge: Automated tools mistake non-malicious issues for vulnerabilities, and hence time and effort is wasted.
- Solution: Involvement of professional penetration testers who will inspect and validate the output to minimize false positives.
4. Security vs. Usability
- Challenge: Too much security could mean that systems become unusable.
- Solution: Achieve security while maintaining usability by fixing vulnerabilities only at identified vulnerable areas without impacting functionality.
5. Expensive
- Challenges: To gain in the entire system, systems especially larger systems would need a huge budget.
- Solutions: High-cost areas penetration is undertaken with an emphasis on critical system prioritization and treating other less sensitive systems cheaply and effectively, maybe with automated testing tools penetration.
Emerging Trends in Penetration Testing
Advances that counter cybercrimes are taking penetration testing to advanced levels. In the future, here’s what awaits.
- AI-Powered Penetration Testing: Penetration testing is now being integrated with artificial intelligence in order to find vulnerabilities more quickly and accurately. AI tools can simulate advanced attack patterns that traditional methods might miss.
- Continuous Penetration Testing: As DevSecOps is becoming increasingly popular, continuous pen testing is also being incorporated into the software development lifecycle. In this way, vulnerabilities are identified as early in the development cycle as possible.
- Cloud Security Testing: With the increasing number of organizations becoming cloud-centric, the need for pen testing of the cloud environment has increased. It includes discovering the vulnerabilities in configurations, access controls, and APIs of the cloud.
- IoT: The IoT devices also represent some new attack surfaces. The IoT-based pen testing verifies that all such interconnected devices cannot become liabilities concerning security issues.
- Automation Tools and Platforms :The pentesting automation testing tools have taken a route towards becoming very smart. Today, using those, an organization can run multiple frequent test runs without developing significant in-house talent.
“Explore all Advanced Penetration Testing Services here!”
Conclusion: Securing in Anticipation of Risk
Penetration testing in software testing is not just a technical exercise, but a proactive measure to protect one’s systems, data, and reputation. In that sense, the organization will lead cybercriminals and garner the trust of its stakeholders.
Be you a small startup launching the newest application, or a giant company managing very complex systems, it is crucially important for investing into your cyber security strategy, but only pen testing properly approached, equipped, and possessing appropriate expertise allows for the strengthening of defenses with subsequent, confident roaming around this dynamic world of cyber threats.
So are you ready to test your system’s mettle? Remember it’s better to find the cracks before someone else does.
Cyber threats are not limited to traditional software vulnerabilities. The rise of AI voice generators has introduced new security challenges, such as deepfake audio scams that can bypass authentication systems.
This anticipation behavior is exactly the reason by which secure organizations lead and mark the difference against others that shall face cyber assaults.


















































































































































































































































































































































0 Comments