What does a Cloud Security Assessment mean?
In the digital environment, which is more based on the cloud for business activities, security becomes crucial. A cloud security assessment is an all-encompassing defense strategy that is meant to secure valuable assets and systems in a cloud environment from attackers. By analyzing security measures, compliance adherence, and technological risks, organizations can detect the threats in advance and create a strong defense to prevent breaches.
Therefore, in this blog, we will learn the importance of cloud security assessment, and which company you should choose for this task.
Why conduct a cloud security assessment?
Performing cloud security assessment is very important as it helps to protect sensitive data and systems in the cloud. It assesses the level of security, compliance, and cloud technology risks. Therefore, by performing such evaluations, companies can find and handle security vulnerabilities and prevent data breaches.
Moreover, it assists in managing security settings and improves defenses against cyber threats. Hence, a cloud security assessment is essential to preserving the availability, confidentiality, and integrity of private data processed and stored in the cloud.
8 steps to execute Cloud Security Assessment
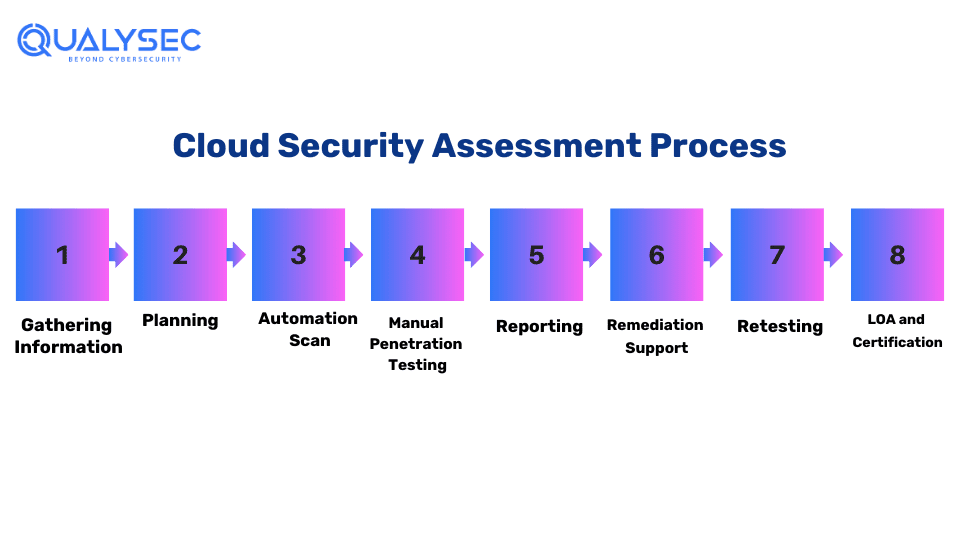
When conducting a cloud security assessment, the following procedures must be followed, that includes:
1. Collecting Information
The initial stage of cloud security assessment is information collection. This is where the security testing team collects as much information about the cloud environment as possible.
2. Planning
By thoroughly examining the detailed technicalities and capabilities of the cloud application, the security testers determined their goals and objectives. They specify which areas and vulnerabilities to target.
3. Automated Testing
Here, the testers use various automated tools to scan the cloud environment, such as Nessus, Burp Suite, etc. This process quickly scans the cloud platform and identifies surface-level vulnerabilities.
4. Manual Testing
In this stage, the testers use manual testing techniques to identify and exploit vulnerabilities present in the cloud. Since it involves human expertise, this step finds hidden and maximum security weaknesses in the cloud.
5. Reporting
The security testers generate an extensive, developer-friendly report at this stage that contains all the information regarding the vulnerability found and how to fix it.
Would you like to view the cloud security assessment report? You can click on the link below to download the sample report.
Latest Penetration Testing Report

6. Remediation
The developers use the test report to fix the vulnerabilities found. If needed, the testing team may also help the developers with remediation over consultation calls.
7. Retest
In this phase, testers retest the program to determine whether any problems still exist after the developer’s modification.
8. LOA and Security Certificate
Finally, the testing firm issues a letter of attestation (LOA) and the security certificates. Organizations use this security certificate to comply with industry regulations and build their brand image.
Explore the article on Qualysec’s Cloud Security services to learn how it helps you defend against cloud breaches.
Important Things to Consider Before Starting a Cloud Security Assessment?
Before starting a cloud security assessment, it is necessary to have a strong foundation. Here are some important points to consider:
1. Understand Cloud Architecture:
Before cloud security assessment, ensure that you have a full understanding of the cloud architecture being used. Various cloud service providers (AWS and GCP) have distinct architectures and security capabilities. Therefore, determining the specific architecture, which includes networking, data storage, and access controls, is a basic necessity for a thorough evaluation.
2. Identify Security Requirements and Compliance Standards:
Recognize the security requirements that are unique to your organization as well as any industry or regulatory compliance standards that should be adhered to (for example, GDPR, HIPAA, and PCI DSS). This will determine the direction and depth of the assessment since all the security issues will be transparently revealed.
3. Define Scope and Objectives:
It is essential to precisely outline the assessment’s purpose and goals so that all the vital domains of cloud security are examined. Consider the type of assets that are hosted in the cloud, the criticality of these assets, and the threats and vulnerabilities that may be present. Setting proper goals enables one to foresee what is the most important and makes assessment meaningful and effective.
4. Select Appropriate Assessment Tools and Techniques:
Select effective assessment procedures and technologies considering the identified security needs, compliance rules, and scope of the assessment. It might entail running vulnerability scans, penetration tests, configuration reviews, and compliance audits. Furthermore, a combination of automated tools with manual examinations is a way to produce a more comprehensive evaluation of cloud security.
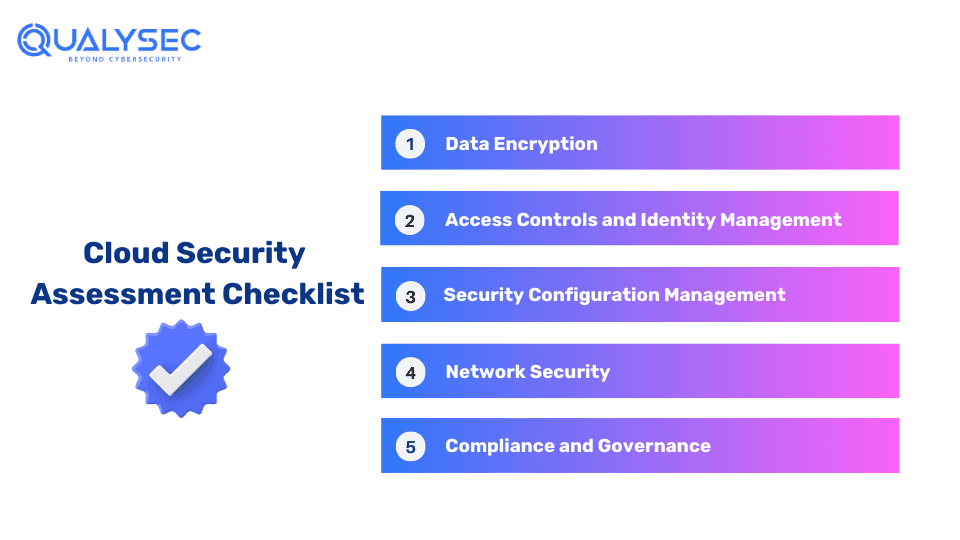
Cloud Security Assessment Checklist
The checklist for the cloud security assessment should include the following:
1. Data Encryption:
Evaluate the encryption protocols and mechanisms used for data in transit and at rest within the cloud environment. Ensure encryption standards are in alignment with industry best practices and regulatory requirements.
2. Access Controls and Identity Management:
Assess the efficacy of the access controls and identity management systems currently in use. This includes analyzing authentication methods for users, authorization mechanisms, and RBAC role-based access control to avoid unauthorized access to resources.
3. Security Configuration Management:
Review the configuration settings of cloud services and resources to find out if any misconfigurations could provide an opportunity for hacking. Moreover, test the security configuration that aligns with standardized benchmarks. Additionally, follows security best practices to minimize risks related to incorrectly configured services.
4. Network Security:
Evaluate the cloud network architecture and the security measures within the cloud environment. This implies analyzing the firewall rules, network segmentation, intrusion detection and prevention systems (IDPS), and identifying abnormal network events to stop unauthorized access and network threats.
5. Compliance and Governance:
Check compliance with the relevant rules, standards, and internal security laws. Create and implement the framework for monitoring, enforcing, auditing, and maintaining documentation governance structure for compliance mandates and accountability.
Why Should You Opt for Qualysec’s Cloud Security Assessment Solution?
Organizations are shifting their application workloads to the cloud to save expenses, enhance adaptability, and accelerate time to market. Therefore, with QualySec Technologies, you can increase output, dependability, and innovation without sacrificing cloud application security.
Additionally, Qualysec uses process-based penetration testing to provide personalized security solutions. A unique approach that guarantees that apps adhere to the finest industry requirements by utilizing a hybrid cloud security assessment methodology and a knowledgeable team with extensive testing experience.
With our comprehensive and developer-friendly pen testing report, we help developers address vulnerabilities. This report covers all the relevant information, beginning with where the vulnerabilities were discovered and concludes with a reference on how to patch them.
Would you like further details about how cloud security assessments are performed? Reach out to our knowledgeable security experts and arrange a consultation call.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
Protecting cloud infrastructure in today’s technologically advanced environment requires regular cloud security assessment. Furthermore, by thoroughly examining the cloud environment for any potential weak areas, organizations can protect their data and resources from malicious assaults.
To ensure continued development and strengthen the overall security of cloud-based systems, collaboration with reputable specialists, well-defined goals, and regular testing of the cloud infrastructure are essential. Additionally, by including cloud penetration testing in their cybersecurity plan, businesses may successfully reduce security risks and confidently use cloud computing.
FAQs
Q. What is a cloud assessment?
A. A cloud assessment is a process of assessing an organization’s preparedness, existing strategy, and potential advantages of moving toward cloud services. Moreover, the process usually entails examining infrastructure, applications, security, compliance, cost, and scalability to aid decision-making and planning.
Q. What is the purpose of cloud security assessment?
A. The purpose of cloud security assessments is to audit the system’s strength and all the possible ways that might lead to breaches, weak compliance, and potential risks. Through the examination of architecture, configurations, and controls, they strengthen cloud environments by providing confidentiality, integrity, and accessibility of data as well as resisting cyber threats.
Q. What is the scope of cloud security?
A. Cloud security involves securing the data, applications, and infrastructure for cloud platforms from unauthorized access, data breaches, and other cyber-attacks. Additionally, it involves implementing reliable methods to achieve the confidential, integral, and available assets stored and processed in the cloud.








































































































































































































































































































































0 Comments