Companies are continually seeking innovative ways to safeguard their web apps due to rising cyber threats. Web application penetration testing is one of these strategies, and it is now an integral component of any effective security plan.
Penetration testing, also known as Pen Test or Pen Testing, is becoming increasingly popular. According to reports, the pen testing industry is predicted to grow from $1.7 billion in 2020 to $4.5 billion by 2025. In this blog, we’ll discuss the top vulnerabilities in web applications and web app pentesting helps to mitigate them. But first, let’s start from the basics of web app pentesting.
Web Application Vulnerabilities: A Brief Overview
Any application defect an attacker can exploit to compromise a web application is called a web application vulnerability. Web applications are becoming increasingly significant in both business and personal life—exploiting a web application vulnerability testing can result in the loss of sensitive data, disruption of corporate operations, reputational harm, and legal exposure.
Continuous security testing is essential for identifying security flaws and protecting your firm. To address web application security vulnerabilities, a proactive strategy is required, including frequent security audits, code reviews, and safe development techniques and frameworks. Furthermore, using techniques such as firewalls and constantly upgrading software helps improve overall web application security.
Common Web App Vulnerabilities: The Top 10
Below are the most prevalent security concerns listed in Web application vulnerabilities OWASP Top 10. Developers may construct secure apps that protect their users’ data from attackers by creating code and performing rigorous testing with these concerns in mind.
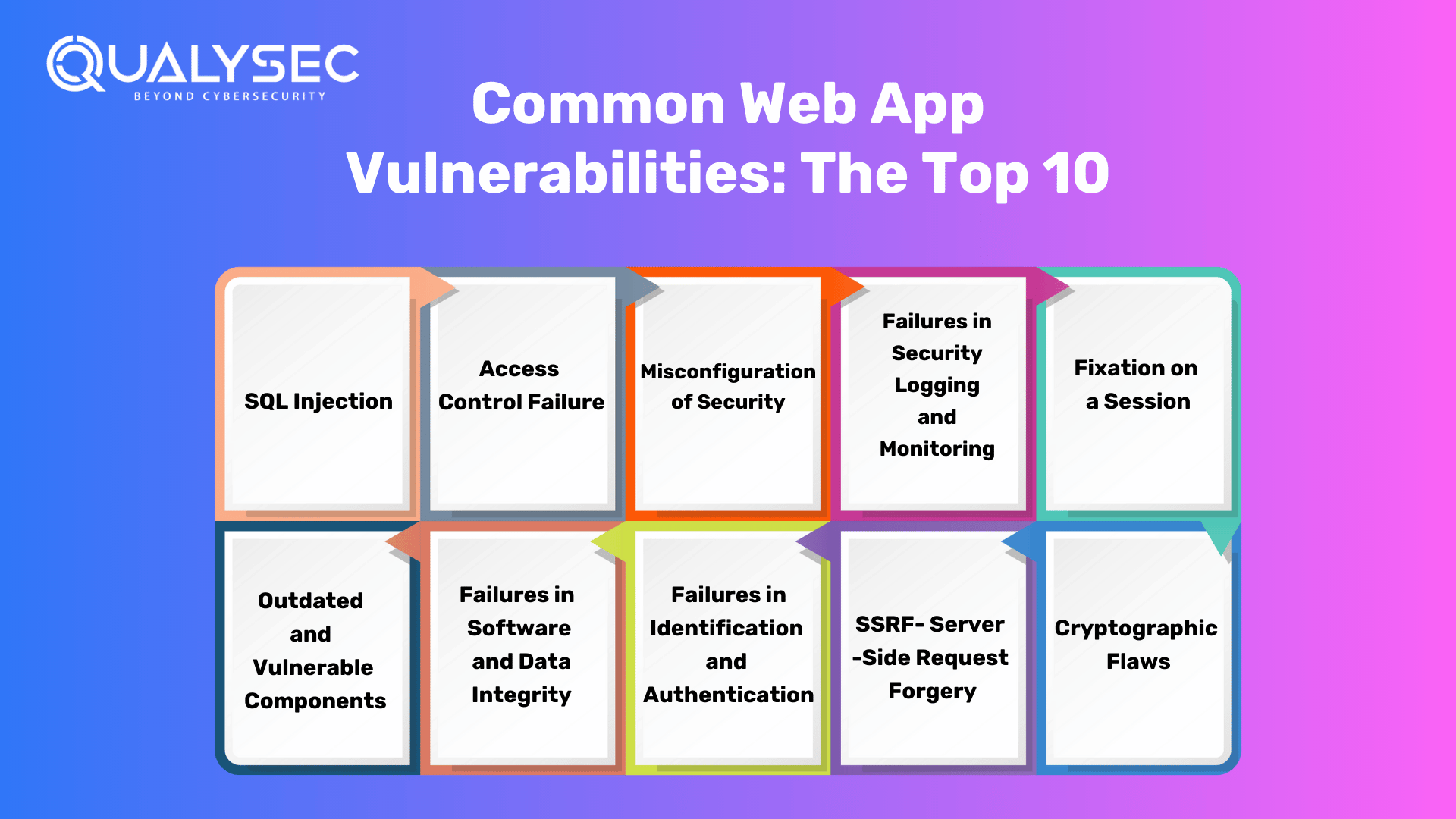
1. SQL Injection
Many applications utilize Structured Query Language (SQL) to manage database connectivity. Furthermore, SQL flaws allow attackers to input malicious SQL statements into databases to exfiltrate, change, or destroy data. Some hackers use it to get root access to the target application. SQL injection attacks are directed at servers that store sensitive data utilized by web applications or services. They are especially harmful when exposed to vital or sensitive data, such as user passwords and personal information. Using unsensitized user inputs is the most prevalent vulnerability that allows SQL injection attacks. Removing any element in user-supplied inputs that the server may utilize to run SQL code is critical.
2. Access Control Failure
If authentication and access control are not correctly established, attackers can easily grab everything they want. Unauthenticated or unauthorized users may get access to sensitive information and applications, as well as user privilege settings, due to access control weaknesses. Penetration testing can detect missing authentication but not the misconfigurations that result in the vulnerability. One advantage of the growing usage of Infrastructure as Code (IaC) technologies is the ability to discover configuration mistakes that lead to access control failures using scanning tools. Weak access controls and credential management difficulties in apps may be avoided using safe coding techniques and preventative actions such as shutting down administrative accounts and controls and employing multi-factor authentication.
3. Misconfiguration of Security
Application servers, frameworks, and cloud infrastructure are all highly customizable, and security flaws such as overly wide permissions, insecure default values left unmodified, or overly revealing error messages can give attackers simple routes to compromise programs. A 2023 report identified misconfiguration mistakes in 70% or more of apps that had created a new vulnerability in the previous year. Organizations should harden deployed application and infrastructure configurations regularly and scan all infrastructure as code components as part of a secure SDLC to prevent misconfiguration risks.
4. Failures in Security Logging and Monitoring
Adequate logging and monitoring are critical in discovering a breach early and, ideally, reducing the damage, and in incident forensics, to understand the breadth of the breach and the type of attack. More than simply producing data is required; enterprises must also have effective data collecting, storage, alerting, and escalation mechanisms. Organizations should also ensure that these procedures function properly; for example, employing Dynamic Application Security Testing (DAST) solutions should result in considerable logging and alerting events.
5. Fixation on a Session
A session fixation attack includes changing a user’s session ID to a certain value. Furthermore, depending on the target web application’s functionality, attackers may employ various approaches to modify session ID values. Two examples of session fixation tactics are cross-site scripting attacks and reusing HTTP requests. Without sufficient safeguards, every web application that authenticates users using sessions is subject to session fixation attacks. Web apps commonly use session IDs, although hidden form fields or URLs may also use them. The most common and easiest to hack are cookie-based user sessions. The majority of fixation attacks are directed at cookie-based sessions.
6. Outdated and Vulnerable Components
In recent years, supply chain vulnerabilities have become a serious problem, particularly when threat actors seek to incorporate malicious or susceptible code into widely used libraries and third-party dependencies. An organization may be exploited if it lacks insight into the external code utilized within its applications, including nested dependencies, and fails to examine it for dependencies. In addition, failing to deploy security updates to these dependencies on time may expose exploitable vulnerabilities to attack. A program, for example, may import a third-party library with its dependencies that may include known exploitable flaws.
7. Failures in Software and Data Integrity
The tools used to create, manage, and distribute software are becoming more prevalent attack vectors. A CI’CD pipeline that regularly builds, tests, and deploys software may also be leveraged to insert malicious code (or libraries), produce unsafe deployments, or steal secrets. As described above, modern applications rely heavily on third-party components frequently retrieved from third-party repositories. Organizations may reduce this risk by guaranteeing the security of both the build process and the components used. Malicious code or libraries can be identified by including code scanning and software component analysis stages in a software build pipeline.
7. Failures in Identification and Authentication
Malicious actors can impersonate other users thanks to ineffective identity management and authentication mechanisms. Hackers who exploit these flaws obtain access to sensitive data such as bank information or intellectual property. Application multi-factor authentication and effective identity and access management (IAM) procedures can help prevent vulnerabilities in this category. A crucial security practice is identifying and approving users and clients. Flaws in how an application enables access or recognizes users are serious vulnerabilities. While secure coding methods are the foundation of mitigation, technologies to identify and prevent credential stuffing and brute force attacks are also essential safeguards.
8. SSRF- Server-Side Request Forgery
Modern web apps frequently retrieve additional material or data from a remote resource. If an attacker has control over the destination resource and the application does not check the provided URL, a forged request may be delivered to the target location. Mitigating SSRF attacks involves:
- Adopting well-known techniques such as sanitizing user input.
- Employing explicit allow lists.
- Analyzing request replies before returning them to clients.
9. Cryptographic Flaws
The category of cryptographic failures was known as “sensitive data exposure” in the 2017 OWASP Top 10 Vulnerabilities. Because cryptography is employed to secure data resources, the new category name better represents the variety of issues. Weak SSL/TLS implementations, insecure password storage, and outdated and compromised encryption technologies are among the difficulties. Among the mitigation strategies are better encryption protocols and regular vulnerability evaluations. Older encryption applications should be phased out in favor of more modern ones.
Read More : Web Application Penetration Testing: A Comprehensive Guide
Web Application Penetration Testing: A Closer Look
A pen test, as the name implies, is a test that focuses primarily on a web application rather than a network or corporation as a whole. web application penetration testing is performed by launching simulated assaults, both within and outside, to get access to sensitive data.
We may use web application security testing to identify any security flaws in the complete web application and its components (including the source code, database, and back-end network). Furthermore, this allows the developer to prioritize the identified web app vulnerabilities and threats and devise mitigation techniques.
Is your business facing any of the vulnerabilities and seeking expert help? Don’t worry, Qualysec is here to help. Contact our expert Security Consultants to help you secure your applications!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
The Methodologies Used in Web App Pentesting
The technique is nothing more than a collection of Web app security industry recommendations for doing testing. Certain well-established and well-known methods and standards may be utilized for testing. Still, because each web application requires distinct tests, testers can design their methodology according to industry standards.
Some security testing methodologies and standards are as follows:
- The Open Web Application Security Project (OWASP)
- Open Source Security Testing Methodology Manual (OSSTMM)
- Penetration Testing Execution Standard (PTES)
- Information Applications Security Assessment Framework (ISSAF)
- A Web Application Hacker’s Manual
- SANS 25 Security Threats
What are the Advantages of Web Application Penetration Testing?
The number of web apps has grown dramatically over time. Many internet resources are spent developing software and figuring out how to make these apps work on different platforms. This newly discovered frontier, however, is always under attack by rogue hackers seeking personal benefit.
Because many web apps include sensitive data, they must always be maintained safe. Especially now that kids have access to the internet. As a result, web security testing as part of the Software Development Life Cycle (SDLC) process would be the best and most cost-effective strategy to combat any vulnerability.
Another reason hostile attackers might abuse the application and create a harmful scenario is programming errors. This can jeopardize all personal information or result in unauthorized access to critical applications.
The advantages of web application pentesting include satisfying compliance standards imposed by various sectors:
- It is useful to understand the robustness of your infrastructure.
- It assists in identifying vulnerabilities by detecting flaws in applications before an attack happens.
- Aids in the confirmation of security policies by examining current security policies for flaws.
Read More: The Power of Web App VAPT
What Steps Are Required to Perform Web Security Testing?
Penetration testing companies use a predefined approach to examine organizational infrastructure for vulnerabilities:
- Data Collection: Gather data using multiple techniques to determine user roles, permissions, and data flows.
- Planning includes determining objectives and targets, assessing technological difficulty, and developing a complete testing approach.
- Penetration Testing: Offer specialized manual testing services for in-depth study of web application vulnerabilities, emphasizing authentication and data management.
- Reporting: This includes detecting and categorizing vulnerabilities, performing a high-level test, and providing full documentation to customers and developers. Click below to check what a detailed and developer-friendly report looks like
Latest Penetration Testing Report

- Remediation Assistance: Through consultation calls, assist development teams in duplicating and minimizing vulnerabilities, assuring effective resolution.
- Retesting: Evaluate the efficacy of vulnerability mitigation after development.
- LOA and Certificate: Provide a Letter of Attestation and a Security Certificate to validate security levels, compliance, and stakeholder confidence
In addition, Qualysec provides a publicly verifiable Pentest Certificate to promote transparency and confidence in today’s cybersecurity context.
The Types of Pentesting: The Major Categories Performed
There are 2 major types of pentesting performed. These tests are carried out by professional pentesters, namely
Automated Penetration Test
Vulnerability scanning, often known as automated penetration testing, is a technique for finding vulnerabilities using penetration testing tools. It is simple to implement and saves a significant amount of time. Automated pentest detects typical security problems such as a missing update, faulty permission rules, and configuration flaws with astounding speed. It is simple to accomplish and requires little preparation and forethought.
Manual Penetration Test
Often known as penetration testing, it is a thorough examination of your security architecture by qualified security researchers. Manual pentests take many days to complete. It discovers critical issues frequently overlooked by scanners, such as business logic mistakes, loopholes, code faults, etc. Manual penetration testing also entails testing these vulnerabilities to see how they affect the application. It takes time and effort; therefore, it must be done infrequently.
Automated Pentesting or Manual Pentesting: Which is Recommended?
The unique goals, available resources, and nature of the target application influence the decision between automated and manual penetration testing. Here are a few things to consider:
Automated penetration testing solutions excel at scanning big networks and discovering common vulnerabilities while also delivering efficiency and scalability. They may, however, overlook complex or context-dependent issues that require human intuition and inventiveness to identify.
Manual penetration testing by professional, ethical hackers thoroughly analyzes an application’s security posture. In addition, human testers can detect complicated flaws, simulate sophisticated attack scenarios, and provide important insights into possible business hazards.
A hybrid approach of the two techniques, using automated tools for early reconnaissance and manual testing for further analysis, provides a solid and balanced strategy for ensuring a full security evaluation. Finally, the selection should be based on the unique demands and limits of the company undertaking penetration testing.
The Best in Business: Qualysec Technologies
In today’s digital world, when information security is a top priority, web application testing emerges as a critical approach for fortifying defenses and cultivating user trust. It is more than just securing vulnerabilities; it is about ensuring the confidence and trust of everyone interacting with these apps.
Qualysec Technologies plays a critical role in improving web application security. Our competence lies in performing Web Application Vulnerability Assessment and Penetration Testing (VAPT) on apps, drawing on extensive field experience.
For process-based penetration testing, we use a Hybrid testing method i.e., combine both manual and automated penetration testing. Our skilled staff, with considerable testing skills, guarantee that applications comply with the industry’s highest standards.
Qualysec is one of the best web application penetration testing companies in India providing a wide range of automated vulnerability scanning and manual testing, using a combination of in-house and commercial tools. We help enterprises navigate complex regulatory compliance environments like GDPR, SOC2, ISO 27001, and HIPAA.
What distinguishes us is our dedication to finding vulnerabilities and assisting developers in resolving them. Furthermore, our thorough pentesting report provides extensive insights ranging from the specific location of found vulnerabilities to step-by-step instructions on successfully addressing and mitigating them.
Choose QualySec , your trusted partner in web application security, where we focus on developing and sustaining user confidence through thorough and dependable testing.
Conclusion
Finally, web application penetration testing is critical for discovering and addressing any vulnerabilities that may jeopardize the security of online systems. The top penetration vulnerabilities identified in this blog highlight the broad and persistent dangers that online apps face.
Organizations may proactively increase their defenses against malicious actors aiming to exploit holes in their online apps by employing rigorous testing processes and cutting-edge tools. Furthermore, as new vulnerabilities emerge and attackers develop advanced approaches, the dynamic nature of cyber threats necessitates a continual and adaptable approach to penetration testing.
Furthermore, development teams must establish a security-conscious culture to promote secure coding methods and ensure that security concerns are integrated throughout the software development lifecycle. Implementing effective security measures becomes critical as organizations rely more on online apps to offer services and engage with customers.
Finally, the insights provided by penetration testing enable companies to strengthen their digital infrastructure, improve their overall security posture, and protect sensitive data from possible breaches in an ever-changing threat scenario. Choose Qualysec to shield your web applications today! Stay Secure!
FAQs
1. What is web Services penetration testing?
Web pen testing services entail determining flaws in the security of APIs and other online services. This protects the security of data and functionality communicated across systems, assisting in the prevention of illegal access and data breaches.
2. What is a web application vulnerability?
A web application vulnerability is a weakness or fault in the program’s coding or design that attackers might exploit. SQL injection, cross-site scripting (XSS), and insecure session management are common vulnerabilities that endanger data integrity and user privacy.
3. What is Web application security risk?
Web application security risks are potential threats and vulnerabilities that may jeopardize the confidentiality, integrity, or availability of data within an application. Unauthorized access, data breaches, and service outages are all risks, underscoring the importance of strong security measures to limit possible harm.
4. What are the common web vulnerabilities?
SQL injection, in which attackers modify database queries; cross-site scripting (XSS), which allows the insertion of malicious scripts into online pages; and weak authentication, which allows unauthorized access, are all common web vulnerabilities. Other vulnerabilities include cross-site request forgery (CSRF), security misconfigurations, and sensitive data disclosure, all needing careful mitigation.

















































































































































































































































































































































0 Comments