According to reports, 70% of firms do penetration testing to assist vulnerability management programs, 69% to assess security posture, and 67% to achieve compliance. Furthermore, a pen test is performed yearly or biannually by 32% of firms.
“Penetration testing on web application” is a critical method that assists organizations in identifying and correcting loopholes before attackers exploit them. Because of the increase in attacks, web application penetration testing is increasingly required for organizations to safeguard their applications and ensure the security of their critical data.
This blog will go over web application penetration testing in detail, including its definition, kinds, tools, and best practices. Continue reading to learn more.
What is Penetration Testing?
Penetration testing for online applications is an integral component of web application security. It is the technique of mimicking hack-style assaults in order to uncover possible vulnerabilities in online applications.
It assists firms in meeting security standards and laws such as PCI-DSS, HIPAA, GDPR, and others. Web application testing should be done on a regular basis to guarantee that the web apps are safe and up to date.
The goal of “web application penetration testing” is to identify and mitigate security issues in order to improve the overall security posture of the apps before they may be exploited by bad actors. This ensures that your data is safe and secure, while also guaranteeing that your brand is trusted by customers.
Why is Web Application Pentesting Important?
Penetration testing is at the forefront of the software development process, working persistently to disclose undetected flaws in an online site. Its significance cannot be emphasized in an age where digital dangers are not only widespread but also constantly developing.
The most prevalent term we hear when discussing security is vulnerability. So, what exactly is vulnerability? Vulnerability is a phrase used to describe defects in a system that might expose it to security threats.
- Finding Vulnerabilities
“Web application security testing” is critical in uncovering security holes before they become a target for attackers. It’s like a treasure hunt, with the wealth being possible vulnerabilities and the hunters being ethical hackers trying to locate these jewels before the pirates. In doing so, they not only defend the application’s integrity but also user confidence and data security.
In the digital era, user data has enormous value, and protecting it is not only an issue of trust but also of ethical obligation. Organizations establish strong digital castles by discovering and resolving vulnerabilities, which retain user trust and defend against the reputational harm that comes with security breaches.
- Legal and Compliance Requirements
More than just fortifying online defenses, penetration testing serves as a guide through the complex web of laws and compliance duties. Numerous rules and benchmarks, particularly the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), require enterprises to protect customer information with vigour.
Meeting compliance is far from a simple administrative effort; it signifies the development of a trustworthy digital character. Deviating from these standards causes not just reputational harm, but also hefty monetary fines and legal ramifications. The process of penetration testing is equivalent to a seafaring vessel being thoroughly inspected before setting sail.
What are the Common Types of Web App Vulnerabilities?
- Access control failure
Access controls specify how users interact with data and resources, such as what they can read and change. When a person can interact with data in ways that they do not require, they have a broken access control vulnerability.
- Authentication failure
Broken authentication flaws also target user access. Malicious actors, on the other hand, breach the information that certifies a user’s identity in this situation, such as by stealing passwords, keys, or session tokens.
- SQL Injection
Many applications utilize Structured Query Language (SQL) to manage database connectivity. SQL flaws allow attackers to input malicious SQL statements into databases in order to exfiltrate, change, or destroy data. SQL is used by some hackers to get root access to the target system.
- XSS (Cross-Site Scripting)
XSS attacks are frequently carried out by injecting code into input fields that the target page executes when users see the page (e.g., embedded JavaScript link). An XSS attack can jeopardize a business’s reputation by exposing user data without signaling a breach.
- RFI (Remote File Inclusion)
File inclusion in a web application refers to the “include” capability used by developers to move data from one file to another. File inclusion, on the other hand, is a serious vulnerability in online applications. It enables hackers to get access to sensitive information, run malicious code, and even engage in cross-site scripting.
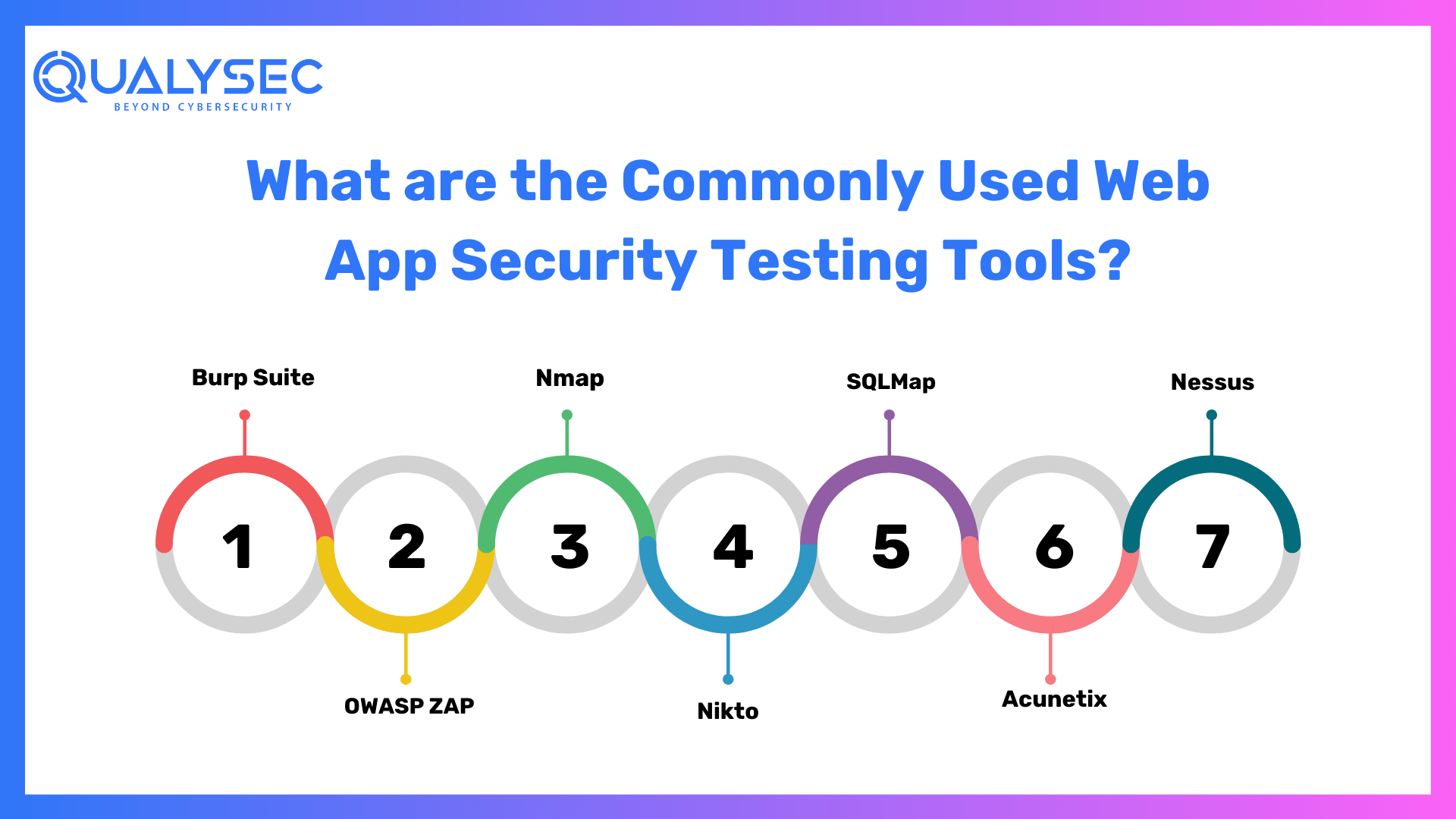
What are the Commonly Used Web App Security Testing Tools?
“Web application penetration” testing employs a number of techniques to evaluate the security of web applications, identify vulnerabilities, and assist companies in improving their online security. Among the best tools in the “web app pentesting checklist” are:
- Burp Suite: Burp Suite is a robust web vulnerability scanner and proxy tool for evaluating the security of web applications.
- OWASP ZAP: An open-source online application security scanner and proxy that aids in the discovery of vulnerabilities in web applications.
- Nmap: Nmap is a versatile network scanning tool for identifying open ports and services.
- Nikto: Nikto is a web server scanner that detects security vulnerabilities in online applications.
- SQLMap: SQLMap is a tool for discovering and exploiting SQL injection flaws in web applications.
- Acunetix: Acunetix is an online vulnerability scanner that looks for a variety of security flaws.
- Nessus: A comprehensive vulnerability scanning tool for detecting flaws in online applications and servers.
How to Do Penetration Testing for Web Application ?
Here are the steps to follow while performing the web application penetration testing checklist:
- Scoping:
It is critical to specify the scope of the assessment before commencing the testing procedure. This includes deciding which portions of your web application will be evaluated, as well as the time range and effort necessary. A well-defined scope ensures that testing is efficient and focuses on the most relevant areas.
- Manual Testing
Manual testing entails manually looking for weaknesses in your program. Security professionals examine the code, settings, and functionality of your program to uncover potential flaws that automated tools may overlook. Manual testing is critical for identifying complicated or one-of-a-kind vulnerabilities that require a human touch.
- Automation Scan:
While manual testing is necessary, automated scans are also beneficial. Testers fully scan your application using a combination of free-source and commercial solutions. These tools may rapidly discover common vulnerabilities and provide a baseline evaluation of the security of your application.
- Remove False Positives:
To ensure the accuracy of the assessment, testers go above and beyond to remove false positives. False positives are vulnerabilities that have been disclosed but do not exist. The team guarantees that the final report contains only valid security risks by rigorously evaluating and confirming the vulnerabilities. This attention to precision saves both time and resources for your team.
- Screenshots or Videos for Proof of Concept:
Visual evidence is frequently essential in assisting developers in understanding the reported vulnerabilities. Pen testers take images or record videos to offer a visual representation of the vulnerabilities, making it easier for the development team to understand and prioritize the concerns.
- Reporting:
Generating a thorough report after discovering and validating vulnerabilities, this paper describes all of the observed problems, their possible consequences, and the proposed solutions. It also provides critical security tips to help safeguard your application. This report is an excellent resource for your team to understand and manage security issues.
- Report Submission:
For your convenience, the professional report is given in both DOC and PDF formats. These formats are simple to share and may be used for internal conversations, stakeholder presentations, and future reference.
- Consulting & Support:
The testing team often provides a consultation call to guarantee the successful remediation of discovered vulnerabilities. The security professionals discuss the results and provide advice on how to address and fix the concerns during this call. This hands-on assistance is critical for your development team to efficiently make the necessary improvements.
- Retesting:
A retest is done after your development team has worked on correcting the vulnerabilities. This is an important step to ensure that all vulnerabilities have been effectively patched. It guarantees that the security measures used are effective and that the application is more resistant to possible attacks.
- Certification:
Some penetration testing companies offer a letter of attestation and a security certificate to provide assurance of the security measures employed. These papers demonstrate that your application has been rigorously tested and that the necessary security measures have been implemented.
NB: Learn how to perform penetration testing in our “web application penetration testing pdf” guide. Click here to discover the road map to pen testing.
What are the Best Practices for Performing Pen Test Web App ?
- Determine Plan and Budget
It may seem logical to want to test your complete environment, but the expense may persuade you otherwise. Consider your high and low-priority regions that require penetration testing. Your biggest weaknesses are in high-priority areas. Operating systems, application code, and configuration files are frequently identified as the top risk sites by pen testers, particularly in software development projects. Low-to-no-code apps for internal corporate activities have a lower priority.
- Locate the Best Pen Testers
When hiring pen testers, be sure to ask the proper questions and identify the relevant specialists for your target domains: for example, if you’re looking for API security, go no further than individuals who specialize in this industry. An expert will understand how systems are created as well as their frequent flaws, ensuring the success of any pen test by using all conceivable angles.
- Design Communication Plan
Communication is an important aspect of the web application security testing checklist . To guarantee a seamless procedure, establish communication channels between you, your team, and the penetration testing team. Hold frequent meetings to track progress, ask questions, and communicate other critical information. Choose a single point of contact on your team to be available during the exam for any crucial information and inquiries.
How Can QualySec Help You Fight Cyberattacks?
QualySec Technologies has assisted businesses in establishing teams of remote developers with industry experience and a product-oriented approach. Our testers are also happy to assist you in conducting web application penetration testing and gaining an in-depth understanding of potential vulnerabilities.
Why work with us? Here are the plenty of benefits you’ll get:
- Our specialized team of highly skilled and qualified cybersecurity specialists assures the protection of your digital assets.
- Comprehensive reports with practical suggestions to remedy weaknesses and increase your security.
- Our dependable support team is here to assist you in resolving security concerns and providing continuous assistance.
- Our seamless engagement with development teams guarantees that issues are resolved quickly.
- Our powerful technologies and approaches discover vulnerabilities accurately and without false positives.
- With daily status reports, you can stay up to current on developments.
- With a Letter of Attestation, you may check the security level, demonstrate security, and fulfill regulatory requirements.
- After completing vulnerability mitigation and retesting using a Security Certificate, get a publicly verifiable certificate.
- Standardized packages enable us to give the greatest quality service at a fair price, making testing accessible to businesses of all sizes.
- Scenario-based testing and review are part of our unique testing approach. As a result, there are more issues with no false positives.
- We diligently adhere to deadlines and maintain coherence throughout the whole process.
- Post-engagement services, no hidden expenses, and high-quality work enable us to form long-term relationships with our clients.
What sets us apart is our commitment to generating results of exceptional quality. QualySec’s accuracy is a game changer in an age where false alarms can result in costly overreactions. Furthermore, we are the indisputable leader due to our mix of experience, precision, and attention to the client’s success with both manual and automation testing approaches. QualySec is committed to maintaining client confidentiality. Every detail about the client’s product and interaction is kept absolutely secret.
Conclusion
Web apps are useful, cost-effective, and offer value. However, most systems are publicly accessible via the Internet, and data may be easily obtained by anyone willing to do some study. Furthermore, even the most sophisticated online applications are vulnerable to flaws in both design and configuration that hackers may discover and exploit.
As a result, the web “application penetration testing” roadmap should be prioritized. Before beginning your tests, you should do a lot of planning and preparation. You should also understand that Web Apps are very complex systems comprised of many technologies in use such as Web Server/Application servers, Web Application Frameworks or Languages, and so on, so it is critical to identify which technology is being used at the target web application.
FAQs:
- What are penetration testing tools?
Penetration testing tools are a collection of applications that assist you in testing the security of your system. They accomplish this by simulating the behaviors of malevolent hackers and then determining how your system would fare under such conditions. As a result, the purpose of penetration testing tools is to demonstrate how a hacker may obtain access to a system rather than to break into it.
- Is it possible to automate web application penetration testing?
It is possible to automate it, although it is not always essential or advised. When you want to perform a large number of tests quickly and effectively, an automated “web application penetration testing checklist” may be valuable. However, automated testing isn’t as comprehensive as manual testing—it’s more likely to overlook some vulnerabilities. If you’re using an automated program, make sure you’re monitoring its effectiveness and that it’s not ignoring issues that might lead to breaches.
- How can web application penetration testing help to keep networks safe?
Penetration testing may assist in keeping networks safe by identifying any weaknesses that hackers could exploit. The practice of detecting and successfully exploiting vulnerabilities in a system is known as penetration testing. This helps you to address any issues before a hacker discovers and exploits them.
- Why is web application penetration testing required?
“Penetration testing web” applications aid in the evaluation of your infrastructure. Any modifications to the infrastructure might expose a system to attack. Web application pen testing aids in identifying real-world assaults that may be successful in gaining access to these systems.
- How long does it take to pen test a web app?
A web application penetration security test typically takes 3 to 10 days to complete. The length is determined by the type of testing, the number of systems tested, and the barriers faced. Manual or automated testing is possible. Manual testing typically takes longer to complete than automated testing.





















































































































































































































































































































































0 Comments