Penetration testing, also known as ethical hacking, is a security assessment that involves simulating a real-world attack on a system to identify potential vulnerabilities. Penetration testing is an important aspect of cybersecurity and helps organizations identify weaknesses in their security defenses. In this blog, we will discuss the top penetration testing methodologies and standards.
But before exploring the top pentesting methodologies and standards, let us explore what is penetration testing methodology.
What is Penetration Testing Methodology?
Penetration testing methodology is a structured approach to performing a security assessment of a system, network, or application. It involves identifying vulnerabilities and weaknesses in the system and simulating real-world attacks to determine their potential impact.
What is a Penetration Testing Framework?
A penetration testing framework is a structured and standardized approach to conducting a penetration test. It provides a step-by-step process for identifying vulnerabilities and weaknesses in a system and determining their impact on the overall security of the system.
Penetration Testing Methodologies and Standards
Some various standards and methodologies ensure the penetration test is authentic and covers all important aspects. Some of them are mentioned below:
- OWASP
- PTES
- NIST
- OSSTMM
Open Web Application Security Project (OWASP) Penetration Testing Methodology
- The OWASP ( Open Web Application Security Project ) Penetration Testing Methodology is a comprehensive framework that covers all phases of a penetration test, from planning and preparation to reporting and follow-up. It includes steps such as information gathering, vulnerability scanning, exploitation, and post-exploitation.
Penetration Testing Execution Standard (PTES)
- PTES is a framework designed to standardize the penetration testing process. It includes seven phases: pre-engagement, intelligence gathering, threat modeling, vulnerability analysis, exploitation, post-exploitation, and reporting.
National Institute of Standards and Technology (NIST) Penetration Testing Framework
- NIST (National Institute of Standards and Technology (NIST) is a well-known standard for cybersecurity, and its penetration testing framework includes five phases: planning and preparation, discovery, attack, reporting, and cleanup.
Open Source Security Testing Methodology Manual (OSSTMM)
- OSSTMM ( Open-Source Security Testing Methodology Manual) is a methodology that focuses on the testing of security controls in physical, logical, and personnel security. It includes four phases: information gathering, threat modeling, vulnerability identification and exploitation, and post-exploitation.
In conclusion, there are several penetration testing methodologies and standards that organizations can use to identify vulnerabilities and improve their cybersecurity defenses.
Why are Penetration Testing Methodologies important?
Penetration testing methodologies are important because they help organizations identify potential security risks and vulnerabilities in their systems. This can help businesses prevent potential cyber-attacks and data breaches, as well as maintain the integrity and confidentiality of their data.
Common Steps in Penetration Testing Methodology
Once the audit universe is ready, testers are ready to move on to further stages in the pentesting methodology.
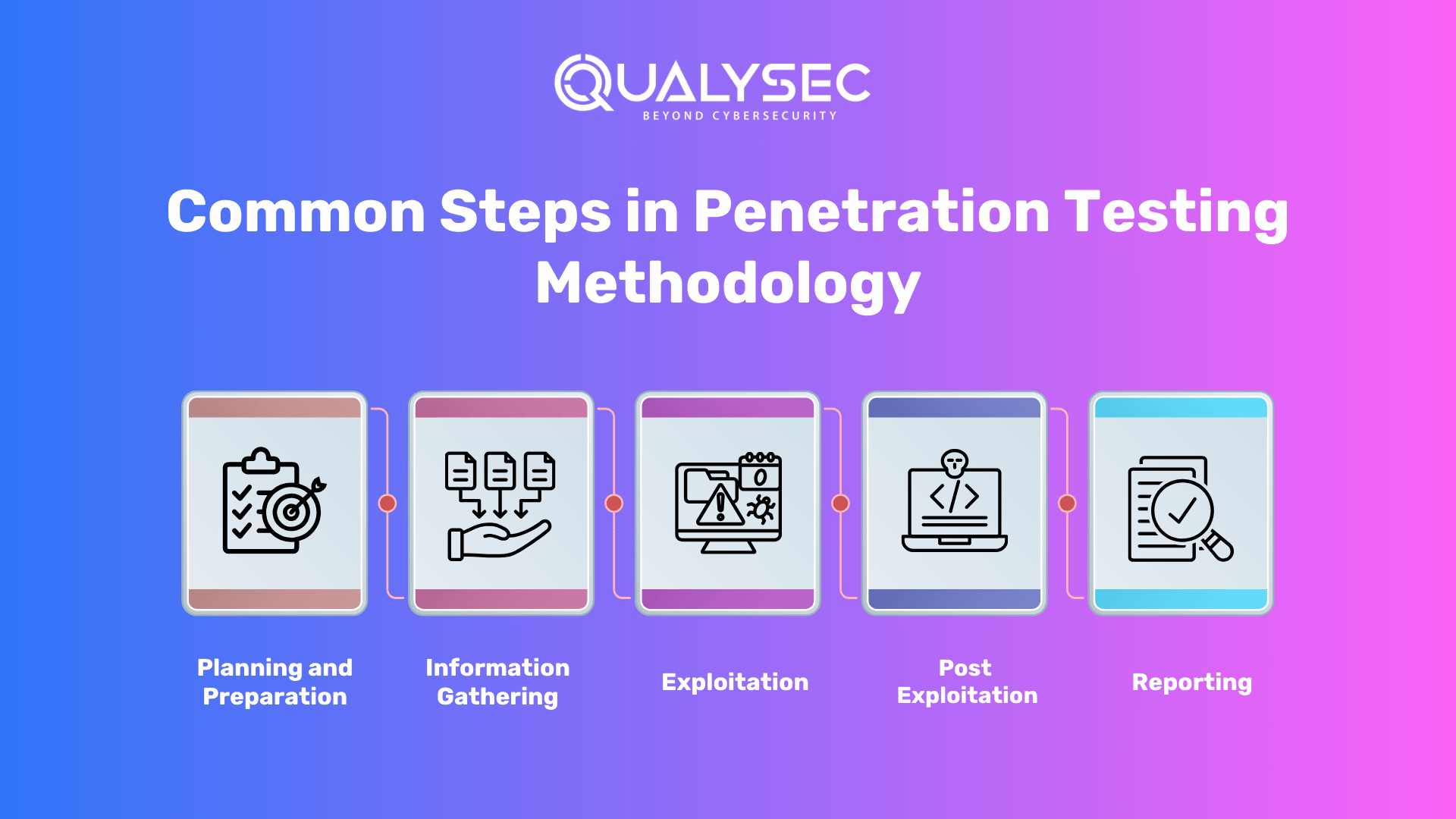
While there are several different penetration testing methodologies, most include several common stages, including:
- Planning and Preparation: This involves defining the scope of the test, identifying the objectives, and selecting the appropriate tools and techniques.
- Information Gathering: This involves collecting information about the target system or application, including IP addresses, domain names, and network topology.
- Vulnerability Scanning: This involves using automated tools to scan for potential vulnerabilities in the target system.
- Exploitation: This involves using manual and automated techniques to exploit identified vulnerabilities and gain access to the system.
- Post-Exploitation: This involves assessing the extent of the compromise and determining the potential impact on the overall security of the system.
- Reporting: This involves documenting the findings of the test and providing recommendations for improving the security of the system.
To see a pentesting report? Tap the link below and download one right now for free!
Latest Penetration Testing Report

Why Should you opt for Qualysec?
Qualysec is a leading provider of pen-testing and compliance management. Their platform allows companies to conduct continuous monitoring, vulnerability assessment, and compliance management across their entire IT infrastructure.
Qualysec follows a comprehensive methodology that involves a combination of manual and automated testing techniques to ensure maximum coverage of vulnerabilities. They also provide detailed reports that include a prioritized list of vulnerabilities, along with recommendations for remediation.
They work closely with organizations to understand their unique needs.
Qualysec offers various services which include:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI /ML Pen-testing
The methodologies offered by Qualysec are particularly beneficial for businesses that must adhere to industry rules or prove their dedication to security to clients and partners. So, by opting for Qualysec as an External Network Vulnerability Assessment service provider, businesses can ensure the safety of their web applications.
Hence, choose Qualysec for comprehensive and reliable testing methodologies. Also, their penetration testing guide will help you make informed decisions and understand the various factors that impact the cost. Hence, protect your assets and enhance your security posture by choosing us.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Qualysec: The Perfect Solution
- Comprehensive vulnerability scanner that evolves to meet pentest demands
- Detects vulnerabilities through over 3,000 tests
- Benchmarks cloud security against NIST, OWASP, and CIS standards
- Ensures compliance with major security regulations and laws including SOC 2, ISO 27001, GDPR, HIPAA, and PCI-DSS
- Gap Analysis identifies areas of security and performance that need attention
- Rescan capabilities verify the patching of vulnerabilities
- Prioritizes vulnerability fixes based on severity and ROI
- Enables seamless collaboration with development teams to resolve issues
- Detailed reports with actionable recommendations and POC videos facilitate effective patching
- Detects business logic errors and security gaps
- Ensures zero false positives through thorough vetting of vulnerabilities
- Provides a publicly verifiable certificate upon completion of vulnerability remediation and retesting
Summary
Penetration testing methodology must strike a balance between flexibility to accommodate the diverse needs of various organizations, while still providing a solid foundation to cover all critical areas and aspects.
In conclusion, penetration testing methodologies and frameworks are essential for identifying vulnerabilities and weaknesses in a system and determining their potential impact on the overall security of the system. By following a standardized approach, businesses can ensure a comprehensive and effective security assessment that can help prevent cyber-attacks and data breaches.
Additionally, both internal and external vulnerability scanners are necessary. These cover all devices and systems that are accessible from within and outside of an organization’s network. We are always ready to help, talk to our Experts, and fill out your requirements.
Check out our recent article on “ Top 25 Cybersecurity Companies “.
Frequently Asked Questions
Here are some frequently asked questions (FAQs) about penetration testing methodologies and standards:
Q. What is a penetration testing methodology?
Ans. A penetration testing methodology is a structured approach to performing a security assessment of a system, network, or application. It involves identifying vulnerabilities and weaknesses in the system and simulating real-world attacks to determine their potential impact.
Q. What is a penetration testing framework?
Ans. A penetration testing framework is a structured and standardized approach to conducting a penetration test. It provides a step-by-step process for identifying vulnerabilities and weaknesses in a system and determining their impact on the overall security of the system.
Q. Why are penetration testing methodologies important?
Ans. Penetration testing methodologies are important because they help organizations identify potential security risks and vulnerabilities in their systems. This can help businesses prevent potential cyber-attacks and data breaches, as well as maintain the integrity and confidentiality of their data.
Q. What are the common stages of penetration testing methodologies?
Ans. The common stages of penetration testing methodologies include planning and preparation, information gathering, vulnerability scanning, exploitation, post-exploitation, and reporting.
Q. What are some common penetration testing standards?
Ans. Common penetration testing standards include the Open Web Application Security Project (OWASP) Penetration Testing Methodology, the Penetration Testing Execution Standard (PTES), the National Institute of Standards and Technology (NIST) Penetration Testing Framework, and the Open Source Security Testing Methodology Manual (OSSTMM).

















































































































































































































































































































































0 Comments