Mobile applications are becoming a necessary component of our everyday life in the current digital era. Since mobile-first development is becoming more popular, it is essential to make sure these apps are secure and protect user data from cyber threats. A Mobile Application Security Assessment (MASA) is one of the best approaches to accomplish this.
Here, the blog will highlight the types of Security Testing to be done to prevent such threats from affecting Mobile Applications. You will explore the recommended solutions and tools that can automate mobile security assessment.
What is Mobile Application Security Assessment?
Mobile app security assessment is a process that evaluates the security system of mobile applications to identify vulnerabilities and weaknesses that could be exploited maliciously. This assessment ensures a mobile app strong and resilient to security risks.
Hence, the primary purpose of finding vulnerable points within a security system is to close chances for attackers to mitigate them.
Key Benefits of Mobile Application Security Assessment
A powerful attack can destroy everything from user data to brand image. As a result, it is of utmost importance to conduct mobile application security testing, as this will help protect your applications from any potential vulnerabilities. Some of the key benefits are:
1. Identify Security Vulnerabilities
Mobile app security audits help identify potential vulnerabilities that hackers could exploit for unauthorized access. Through a mobile app security assessment, they can uncover weak points in the app’s code, architecture, and design. By uncovering these weaknesses early, developers can implement necessary security fixes to ensure the app remains secure and less prone to cyberattacks.
2. Protect Sensitive User Data
A single data breach incident can be a huge setback for your business. Security assessment ensure that sensitive user data, such as personal information and financial details, are well-protected. This reduces the risk of data breaches and enhances user confidence in the app’s security measures.
3. Improve App Performance
Nobody likes a slow app or features that don’t work properly. Audits can reveal security issues that impact the app’s performance. Addressing these issues not only enhances security but also improves the app’s speed, reliability, and overall user experience.
4. Ensure Regulatory Compliance
Many industries have rules in place to protect user data online, such as PCI DSS, HIPAA, GDPR, ISO 27001, etc. Regular security audits help ensure that the app complies with these industry regulations and standards. This is crucial if you want to avoid legal issues and fines and maintain the app’s reputation in the market.
5. Attract More Users
Users are more likely to use those apps that are secure and perform like a breeze. Regular mobile app security assessments show that the company is serious about user safety, which helps in maintaining and building user trust. As a result, users will continue using the app and also recommend the app to their friends.
Methods for Mobile App Security Assessment
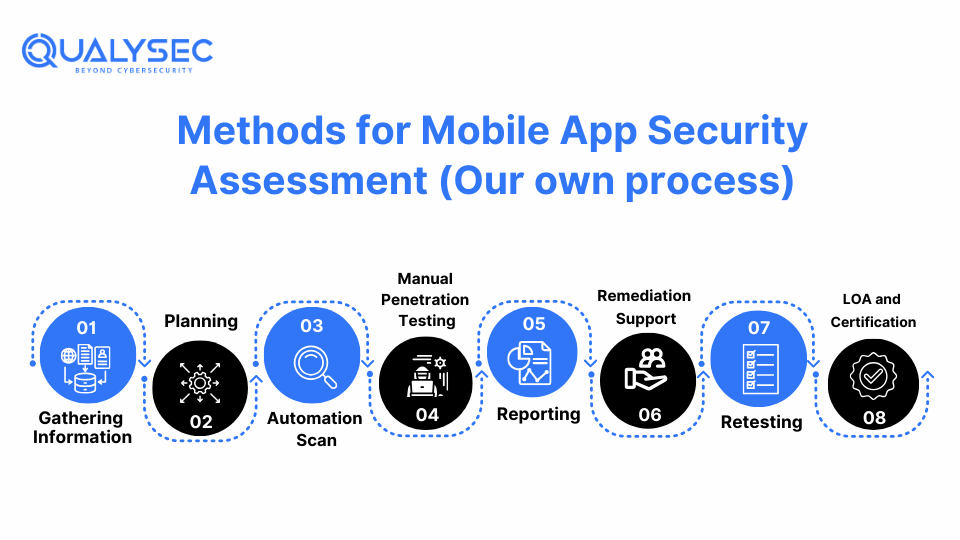
1. Information Gathering and Planning
This is the first step to gather all the information about the application and plans a checklist for conducting the mobile app vulnerability assessment.
2. Automated Tool Scan
Here, the plan is executed with the help of automated tools to find surface-level vulnerabilities. In this stage, you may find false positives.
3. Manual Testing
This stage is critical in pen testing. The pen testers perform security tests manually by going deep into the app to find and mitigate vulnerabilities. Here, you’ll get zero false positives.
4. Reporting
The pen testers now create a detailed and developer-friendly report that provides insights into all the vulnerabilities found, their severity, and reference on how to mitigate it
Do you want to see what the actual mobile application security assessment report contains? Click on the box below to download the one for you.
Latest Penetration Testing Report

5. Post-analysis remediation support
This is the stage where the developer works on fixing the vulnerabilities. The testing team will help the developer team if they need help through a consultation call.
6. Retesting
This phase is to test the application after the remediation so that testers find no further vulnerabilities, and the app is secure.
7. LOA and Certificate
This certificate of proof is provided by the testing company to ensure the application is secure for everyone’s use.
Best Practices for Mobile Application Security
The following are steps needed to overcome the cyber threats for mobile application security. Some of them have been explained below:
1. Employed Secure Coding Practices
Most common threats, such as SQL injections, cross-site scripting (XSS), or buffer overflows, can be prevented using secure coding standards.
2. Data Encryption
Encrypt stored and in-transit data for maximum security.
3. Enable Multi-Factor Authentication (MFA)
MFA is another reinforcing layer we implement to prevent users from threats and verify them during their login step-up. Multi-factor authentication (MFA) methods to identify the user.
4. Scheduled Security Audits
Regularly perform security audits to update you on new vulnerabilities that might occur.
Schedule a call with the experts to take advantage of the best mobile application security assessment services!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Tools and Techniques for Mobile App Security Assessments
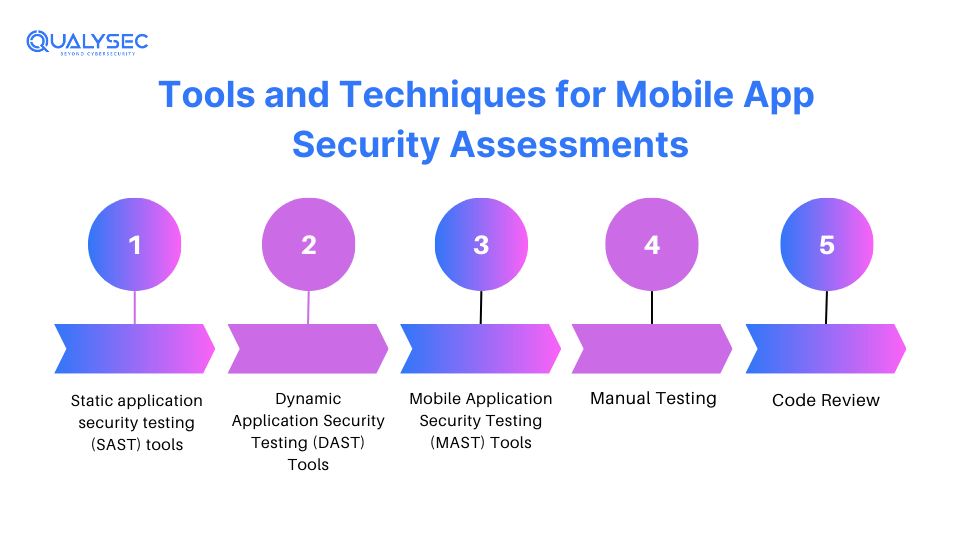
1. Static application security testing (SAST) tools:
The SAST tools scan the source code or binaries of the app to determine the presence of vulnerabilities. Some of them include Fortify, Checkmarx and Veracode. Additionally, it can identify problems like insecure coding, old libraries, and data leaks.
2. Dynamic Application Security Testing (DAST) Tools:
The DAST tools run on the actual runtime framework of an application to identify space-like vulnerabilities. Zed Attack Proxy (ZAP) and Burp Suite are the tools most commonly used. In addition to this, any common issues with security, such as SQL injection and cross-site scripting (XSS), can easily be identified via code review.
3. Mobile Application Security Testing (MAST) Tools:
They are tools designed to test the security of mobile applications and include functions specifically for mobile testing. For example: NowSecure, AppScan, Mobile Security Framework or MobSF. Thus, they offer security evaluation solutions like static, dynamic, and network protection evaluations
4. Manual Testing and Code Review:
Even though we have available automated solutions, sometimes more complicated risks require manual examination. Professionals in the field can outsmart technologies such as automatic tools because they are trained to detect specific patterns even when there is a loophole.
How to Choose the Right Mobile App Security Testing Company?
Choosing a best mobile application security assessment company is also a good way to keep the safety net wide. Given these factors, some of the key considerations were:
1. Experience:
Identify the various providers in the market that specialize in providing mobile app security assessment services. This could be technical teams with core experience on your platforms and technology.
2. References or Reviews:
Look for positive responses on recognized sites with what other clients are saying about them. The feedback that you get from your provider is important; people will not tell their competitors the truth. The third-party vendor that you would prefer should be able to provide references.
3. Compliance Level and Certificates:
This will help you determine if vendors comply with industry practices or have a specific certificate, mainly when your app deals with sensitive data-sensitive information. This is particularly important for healthcare facilities and other organizations that need security protection.
4. Price:
Companies often ask: what is the cost of a Mobile security assessment? Unfortunately, there is no single answer because a security assessment depends on the size and complexity of the company’s IT infrastructure.
Conclusion
Mobile applications attracts significant attention because of their vast number of users. Insecure storage and memory, unprotected supply chains, and flawed authentication are no less dangerous, as they may lead to data leakage and affect users’ trust in the application. To overcome the challenges you must need to do a Mobile Application Security Assessment.
Therefore, performing security scans automatically across the development cycle through continuous integration enables developers to detect and resolve issues faster. Thus, it makes the application more secure and the development cycle faster.
FAQs
1. Why is mobile app security important?
A. The security of the mobile application is essential because it deals with the user’s private and confidential information, including their data and funds. This also ensures app quality and usability by guaranteeing that the app serves users’ needs and is available whenever required.
2. What common vulnerabilities are found in mobile apps?
A. Some of the common vulnerabilities found in mobile apps are:
- Insure data storage
- Insufficient encryption
- Weak authentication
- Code tampering
3. What are the benefits of regular mobile app security assessments?
A. The benefits of regular mobile app security assessments are:
- Identify vulnerabilities
- Security up to date
- Maintain compliance
- Protect sensitive data
4. How often should mobile applications be assessed for security?
A. The rate of security assessment, however, depends on the application’s size, the type of data it processes, and the rate of upgrades. Generally, it is advisable to perform security assessments at least annually or when changes are made to the app. Moreover, with the development of new apps, their security should be checked properly before their launch.















































































































































































































































































































































0 Comments