Mobile applications have become the foundation of our digital lives in recent years, altering the way we communicate, work, and do business. However, the fast growth in mobile app usage has unintentionally revealed a key vulnerability: security concerns. Over 45% of reported data breaches in 2022 were caused by mobile applications, underlining the urgent necessity for robust security measures.
Mobile app penetration testing, often known as pen testing, is a methodical methodology for assessing the security of mobile applications. It entails replicating real-world assaults on an application in order to identify vulnerabilities that hackers or malevolent actors may exploit. The major goal of this testing is to proactively detect and resolve security flaws before hackers can exploit them.
Penetration testing is an essential safeguard in the world of business mobile applications. In this blog, we’ll go through the reasons why penetration testing for mobile app is important for businesses.
Understanding Mobile App Pen Testing
What is penetration testing?
Pen testing, often known as penetration testing, is a proactive way to evaluate the security of a system or application. It entails simulating cyber assaults in order to uncover possible vulnerabilities that bad actors may exploit. The primary purpose is to detect flaws before they may be exploited for illegal access, data breaches, or service disruptions.
Methodologies Used:
- Black-box Testing: In this technique, testers have no prior knowledge of the internal structure or architecture of the system. This simulates an external attacker attempting to get into the system without inside knowledge.
- White-box Testing: Unlike black-box testing, white-box testing requires testers to be intimately familiar with the system’s internal workings, including code, infrastructure, and architecture. This method provides for a more thorough evaluation of vulnerabilities.
- Gray-box Testing: This includes aspects of both black-box and white-box testing. Testers have a limited understanding of the system, simulating instances in which attackers may have minimal information.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Importance of Mobile App Penetration Testing
Security Risk:
Mobile apps confront a slew of unique security threats, including vulnerabilities that, if exploited, can have serious ramifications for businesses:
- Breach of sensitive user data: Mobile apps often handle sensitive user data. Inadequate encryption or unsecured data storage can result in unwanted access and, perhaps, data breaches.
- Unauthorized Access: Weak authentication techniques or incorrect session handling might allow unauthorized access to user accounts, putting their personal information at risk.
- Malware and phishing: Mobile applications can serve as entry points for malware or phishing assaults, especially if they connect to insecure networks or use vulnerable third-party libraries.
- Inadequate Encryption or Unsecured Network Communication: Inadequate encryption or unsecured network communication might expose sensitive data to interception during transmission, posing a data breach risk.
- Device Exploitation: Because mobile applications interact with different device functions, they may mistakenly access or modify device functionality if not adequately protected.
Impact on Businesses:
A breach or vulnerability in workplace mobile apps has far-reaching and far-reaching consequences:
- Reputation Damage: Breaches harm an organization’s brand, weakening confidence among consumers and stakeholders. It might take years to repair a ruined image.
- Customer Trust: Security breaches put customer trust in jeopardy, potentially leading to customer and revenue loss. Users are less inclined to use apps with a history of security flaws.
- Financial Consequences: In addition to the immediate financial losses caused by the breach, there are costs connected with legal bills, regulatory fines, and potential compensation to impacted parties.
- Operational Disruption: A breach can interrupt corporate operations, resulting in downtime, lost productivity, and even impacting the enterprise’s entire functionality.
Compliance with regulations:
Regulatory authorities need strong data protection and privacy procedures, making penetration testing important for compliance:
- GDPR (General Data Privacy Regulation): GDPR imposes stringent data privacy requirements on firms operating in the European Union. Penetration testing guarantees compliance by finding and correcting vulnerabilities that may result in data breaches.
- HIPAA (Health Insurance Portability and Accountability Act): HIPAA laws require the security of patient data in the healthcare industry. Mobile app pen testing aids in conforming to these requirements and safeguarding sensitive healthcare data.
- Industry Requirements and Best Practices: Different sectors have different security requirements that businesses must adhere to. Penetration testing ensures that mobile apps adhere to these requirements, protecting sensitive data and preserving industry confidence.
Reasons Why Businesses Need Mobile App Penetration Testing Services?
Here are the top reasons why businesses/enterprises need mobile app pen testing:
-
Preventative Actions:
Mobile app penetration testing serves as a proactive protection technique, detecting flaws before hostile actors exploit them. Simulating real-world assaults allows testers to identify flaws that attackers may exploit. This proactive method enables businesses to patch and harden these vulnerabilities in advance, dramatically lowering the risk of successful cyber assaults.
Furthermore, finding vulnerabilities early allows teams to put strong security controls and policies in place to avoid any intrusions. This technique not only protects the app but also strengthens the enterprise’s overall security posture.
-
Risk Reduction:
Penetration testing is a technique for strategic risk management. Enterprises may drastically decrease their exposure to possible security threats by detecting and resolving vulnerabilities. This approach aids in prioritizing security measures, effectively allocating resources, and resolving the most significant vulnerabilities that represent the most danger to the company.
Addressing these vulnerabilities directly reduces the risk of successful cyber assaults. This risk-mitigation method saves money by reducing the impact of security breaches on the enterprise’s operations, data, and reputation.
-
Better Reputation and Trust:
A safe mobile app reflects an organization’s dedication to data security and user privacy. Customers have a good view of the organization when they believe their data is protected within an app. As a result, a reputation for strict security procedures may considerably boost a company’s brand image and reliability.
Long-term success depends on establishing and sustaining trust among users and stakeholders. A safe app not only attracts new users but also keeps them, resulting in enhanced customer loyalty and favorable word-of-mouth recommendations.
-
Savings on costs:
Identifying and resolving vulnerabilities early on through mobile app penetration testing can result in significant long-term cost savings. The costs of a security breach, like as legal fees, regulatory fines, consumer compensation, and damage control, are frequently far more than the costs of constantly testing and safeguarding an app.
Investing in strong security measures, such as penetration testing, aids in the prevention of possible financial losses caused by breaches. It also assists in the prevention of operational interruptions, which can have a domino effect on an enterprise’s income and resources. Finally, the cost of proactive security measures is far cheaper than the cost of responding to a security incident.
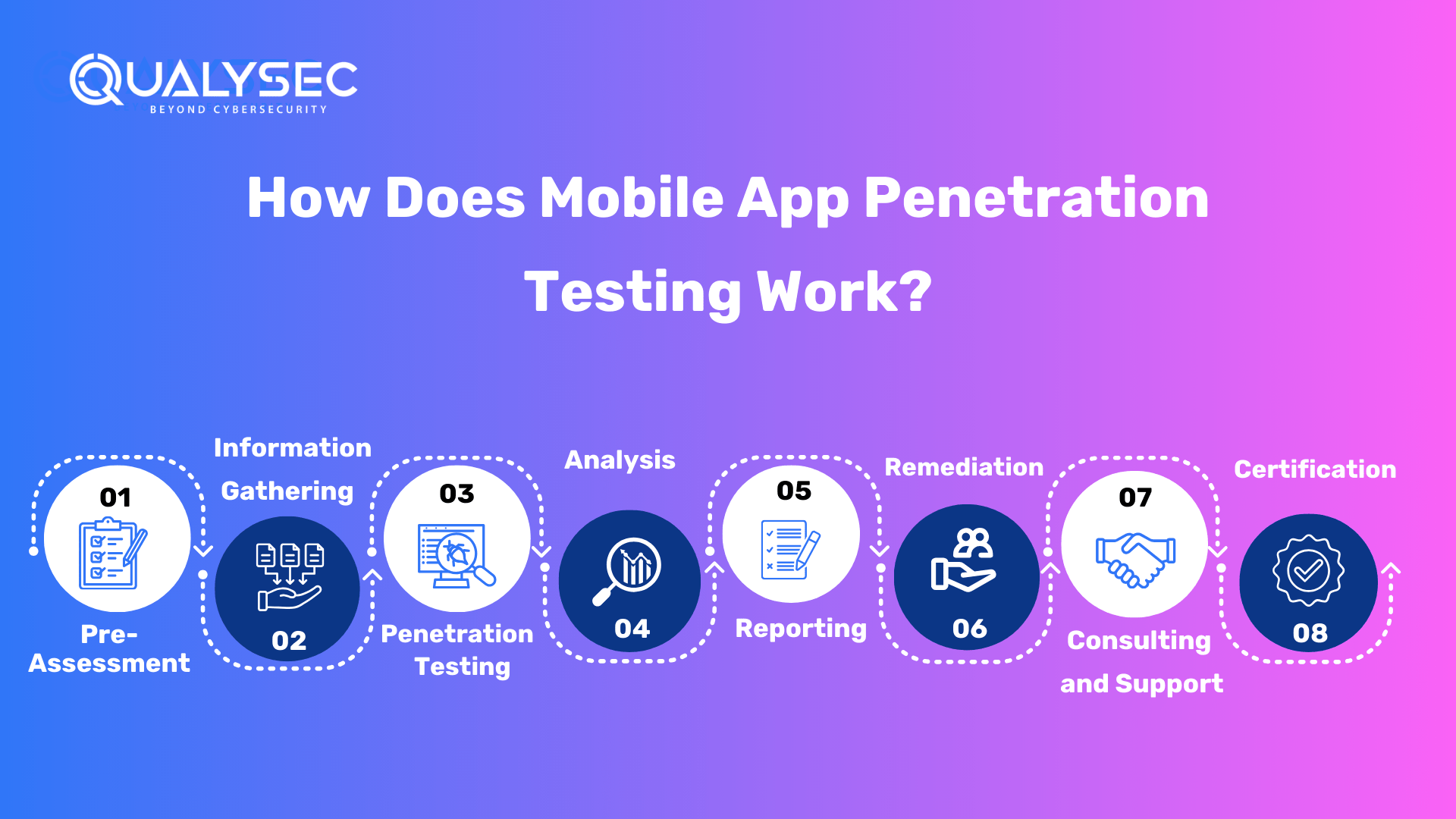
How Does Mobile App Penetration Testing Work?
-
Pre-Assessment
The testing team specifies the scope and objectives of the penetration test during the pre-assessment phase. They collaborate with the app’s owner or developer to understand the app’s goals, functions, and possible dangers. This step involves preparation and logistics, such as defining the testing environment, establishing rules of engagement, and getting any necessary approvals and credentials to execute the test.
-
Information Gathering
The testing company advocates taking a simplified method to begin the mobile app penetration testing procedure. Begin by using the supplied link to submit an inquiry, which will put you in touch with knowledgeable cybersecurity specialists.
They will walk you through the process of completing a pre-assessment questionnaire, which covers both technical and non-technical elements of your desired mobile application. Testers arrange a virtual presentation meeting to explain the evaluation approach, tools, timing, and expected expenses.
Following that, they set up the signing of a nondisclosure agreement (NDA) and service agreement to ensure strict data protection. Once all necessary information has been gathered, the penetration testing will begin, ensuring the security of your mobile app.
-
Penetration Testing
The testing team actively seeks to attack vulnerabilities and security flaws in the mobile app during the penetration testing process. This phase consists of a series of simulated assaults and evaluations to detect flaws. Testers can rate the app’s authentication procedures, data storage, data transport, session management, and connection with external services. Source code analysis, dynamic analysis, reverse engineering, manual testing, and automation testing are all common penetration testing methodologies a tester uses.
-
Analysis
Each finding’s severity is assessed individually, and those with higher ratings have a greater technical and commercial effect with fewer dependencies.
Likelihood Determination: The assessment team rates the likelihood of exploitation for each vulnerability based on the following factors:
Impact Analysis: The assessment team studies and assesses the impact of the exploit on the company and its customers in terms of confidentiality, integrity, and availability for each vulnerability that may be effectively exploited.
Severity Determination: The pen testing company gives severity ratings based on internal knowledge as well as widely used rating systems such as the Open Web Application Security Project (OWASP) and the Common Vulnerability Scoring System (CVSS). The severity of each discovery is determined independently of the severity of other findings. Vulnerabilities with a higher severity rating have a bigger technical and business effect and are less reliant on other flaws.
-
Reporting
Only if the security tester’s findings are properly recorded will they be useful to the customer. A good pentest report should include, but is not limited to, the following information:
- A concise description
- A scope and context description (e.g., targeted systems)
- Techniques employed information sources (either supplied by the customer or uncovered during the pentest)
- Prioritized results (for example, vulnerabilities organized using the DREAD categorization)
- Comprehensive results tips for repairing each flaw
Get a sample report of mobile app penetration testing.
-
Remediation
The last stage is dealing with the identified vulnerabilities and shortcomings. The mobile app developer or owner implements the report’s recommendations and works on remediation measures to improve the app’s security. This step may also include retesting to ensure that the discovered vulnerabilities are resolved and the app is more secure. The objective is to make the app less vulnerable to security risks while still protecting user data.
-
Consulting and Support
The testing team frequently gives a consultation call to ensure that found vulnerabilities are successfully remedied. During this session, the security specialists review the results and offer advice on how to address and resolve the issues. This hands-on support is crucial for your development team to implement the necessary modifications as quickly as possible.
-
Certification
Penetration testing companies provide a letter of attestation as well as a security certificate to ensure the security measures used. These documents confirm that your application has been thoroughly tested and that all relevant security measures are in place.
Read more about how mobile app penetration testing works.
What are the Challenges Pen Testing Company Faces?
- Device and Platform Diversity: Ensuring thorough test coverage is difficult due to the huge variety of mobile devices and operating systems. Testing across several devices and OS versions is necessary, but it is hard and time-consuming.
- Dynamic Environment: Mobile app ecosystems are very dynamic, with regular upgrades, new features, and changing user habits. Because of its dynamic nature, it is difficult to maintain consistent security procedures.
- Network Variability: Mobile apps deal with a wide range of network circumstances, from stable Wi-Fi to unstable cellular connections. Testing the app’s speed and security under different network circumstances complicates the procedure.
- Third-Party Integrations: Many mobile apps use third-party libraries or APIs, which each have their own set of vulnerabilities. Evaluating the security of these interconnections is critical but difficult.
What are the Best Practices for Performing Mobile App Pen Testing?
Here are some of the best practices for conducting mobile app penetration testing:
- Continual Testing: Rather than testing at specified milestones, a continuous testing method guarantees that programs are inspected for vulnerabilities frequently. This constant review aids in detecting and addressing vulnerabilities as they emerge, lowering the likelihood of a significant breach.
- Combination of Automated and Manual Testing: Use a combination of automated and manual testing. Automated technologies are more efficient and faster at discovering common vulnerabilities, but human testing is more effective at revealing nuanced, context-specific security issues.
- Collaboration Among Developers and Testers: Encourage collaboration among development and security testing teams. Developers must comprehend the security implications, whereas testers must grasp the app’s architecture and functionality. This partnership enables a more complete security strategy.
- Emulation and Virtualization: Use device emulators and virtualization to imitate different sorts of devices and operating systems. This method allows for testing in a greater range of scenarios without the need for actual instruments.
- Regular Security Training and Updates: Make certain that your personnel are up to date on the newest security trends and approaches. It is critical to keep team knowledge and abilities up to date in order to remain ahead of new dangers.
Future Trends of Mobile App Security
Here are some of the future trends you should know to keep up with the mobile security world:
- Utilization of DevSecOps
DevSecOps approaches are increasingly being used by businesses to design secure apps. DevSecOps is a technique that combines traditional software development best practices with security principles to assist enterprises in developing more secure and less vulnerable apps. For the time being, an estimated 30% of firms completely employ DevSecOps techniques. However, this figure anticipates to rise in the near future.
- OTA Update Security
Encrypting and authenticating OTA updates is the first step in securing them. Using the most recent encryption standards will protect against man-in-the-middle attacks, and verification methods such as cryptography will guarantee that updates are coming from trusted sources before installing them. These firms should utilize cryptography, encryption, and comparable technologies for all app store downloads and refuse to host programs that do not meet these criteria.
- Increased Demand for Proactive Security
More than $2 billion in cryptocurrencies has been stolen from mobile applications in the last year alone. With this danger real and imminent, organizations must prioritize mobile app security now more than ever. Businesses want built-in app security solutions that can identify and prevent attacks even before they occur. Organizations may decrease risk and customer service expenses by making proactive efforts today to improve the security of their mobile apps.
Why Choose QualySec for Mobile Security Testing?
QualySec Technologies stands as a reliable partner for complete security solutions when it comes to mobile app penetration testing. We provide incomparable value to our clients with a dedication to quality and a unique method of testing that avoids false positives while finding true concerns. Our services include:
QualySec is the top choice for organizations of all sizes because of our reasonable pricing, commitment to on-time delivery, and long-term relationship philosophy. We recognize the significance of confidentiality and treat your information with the utmost care.
We protect your mobile app from possible attacks by utilizing a skilled team of certified cybersecurity specialists, powerful tools, and daily status updates. When you pick QualySec Technologies, you’re not just getting a security partner; you’re also getting a piece of mind, dependability, and a dedication to the safety of your mobile app. For more details, reach us today!
Latest Penetration Testing Report

Conclusion
Mobile app penetration testing is more than simply a necessary security precaution; it is a strategic investment that protects businesses from a wide range of threats. It acts as a proactive shield, detecting vulnerabilities before attackers do, lowering risks, and improving an enterprise’s security posture.
Enterprises must prioritize mobile app penetration testing in their security strategy. Investing in strong penetration testing procedures increases the robustness and credibility of their mobile apps.
In this constant struggle, mobile app penetration testing is at the forefront, ensuring that businesses not only survive but prosper in a safe and trustworthy digital environment. Today, proactive vulnerability discovery is critical to secure the future of corporate mobile apps.
Get your apps secured by QualySec’s professional pen testers today! Click here to learn more!
FAQs
- Why is mobile app testing required?
If you don’t test mobile apps are not fully, there is a considerable risk of consumers experiencing major flaws on their devices, which may result in a negative user experience, especially for new users. Remember that first impressions are crucial to the success of any mobile app.
- What is the Purpose of Mobile App Pen Testing?
Pen testing (or penetration testing) is a security exercise in which a cyber-security specialist seeks to discover and exploit flaws in a computer system. The goal of this simulated attack is to find any weak points in a system’s security that attackers may exploit.
- Is there a Demand for Mobile Testing?
The worldwide mobile testing market was worth USD 7534.18 million in 2022 and it is predicted to grow at a 17.24% CAGR during the forecast period, reaching USD 195464.12 million by 2028.
- Is Mobile Testing Done Manually or Automatically?
Throughout the software development lifecycle, the optimal mobile app testing approach incorporates both human and automated testing. Both techniques have several advantages that may help you develop high-quality mobile apps quickly.


















































































































































































































































































































































0 Comments