Rapid growth in the digital economy in India also means more risks. Cyber attacks now affect financial institutions and healthcare systems by stealing data or demanding payments and these attacks are often more advanced and dangerous than before. Since organizations are now using clouds and increasing digital activities, they must take more than just traditional security tools. An information security risk assessment is the foundation for developing a protected IT environment. It assists businesses in spotting their biggest risks, learning how these risks may harm the business and dealing with them before they do serious harm.
The guide is created for Indian enterprises, startups and public sector organizations that prefer to approach cybersecurity anticipatorily instead of fixing the same issues again and again.
What Is an Information Security Risk Assessment?
An information security risk assessment is the process of identifying, analyzing, and prioritizing potential threats to your organization’s data and IT systems. It allows you to spot problems in your computer systems, connectivity and work habits and consider the possible outcomes and likelihood of attack.
A security risk assessment explores the circumstances around each vulnerability in contrast to a simple security scan. When a database has several layers of shields, a well-known issue might not be urgent. In addition, leaving customer data exposed through a web portal could make it a major risk.
The goal is not just to find risks, but to:
- Know how such risks could upset your activities or break important laws such as the IT Act, regulations from the RBI or HIPAA.
- Sort them according to their real impact on the business
- Give recommendations for reducing them
For these reasons, assessing risks forms the basis of any cybersecurity strategy, especially in regulated industries like BFSI, healthcare or government.
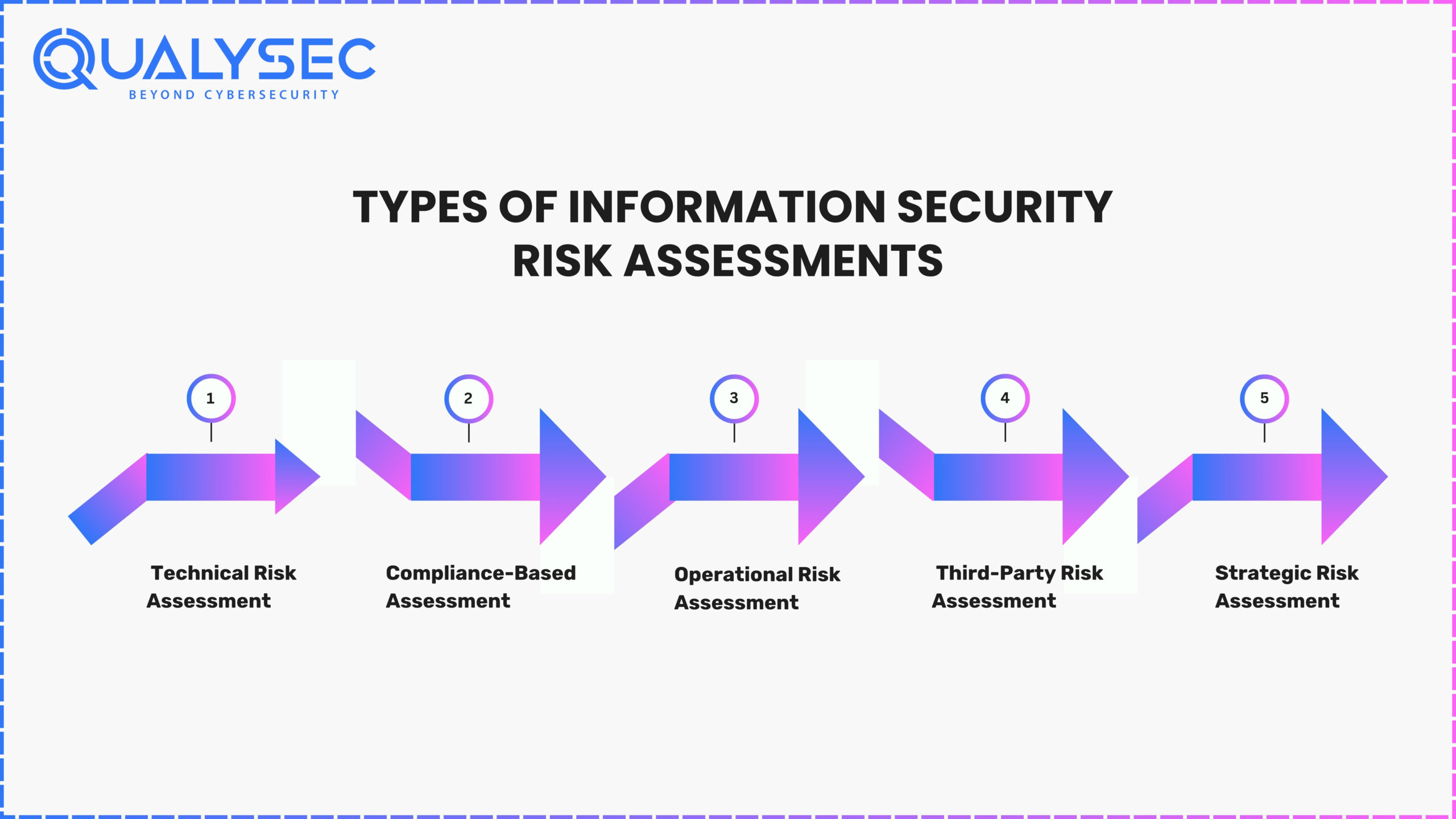
Types of Information Security Risk Assessments
A company’s industry, size and use of technology determine which risks it faces. So, there can’t be a single way to handle information security risk assessments. Most Indian enterprises usually use the following types of systems:
1. Technical Risk Assessment
Works on spotting weaknesses in programming, devices and IT systems. It requires reviewing how you set up your systems, who has access, the encryption rules and patch status.
Best for: Tech-heavy organizations or SaaS companies where infrastructure is central to operations.
2. Compliance-Based Assessment
Created to judge how well your processes and systems comply with the Indian IT Act, ISO 27001, guidelines by the Reserve Bank of India or HIPAA.
Best for: BFSI, healthcare, edtech, or any sector dealing with regulated data.
3. Operational Risk Assessment
Investigates risks linked to internal activities like mistakes with data, errors by employees and inadequate processes.
Best for: Medium to large enterprises managing large volumes of internal or data security risk assessment
4. Third-Party Risk Assessment
Examine the potential risks associated with vendor risk assessment, cloud providers, or other external services your organization trust on.
Best for: Any organization with a complex supply chain or reliance on third-party platforms.
5. Strategic Risk Assessment
Takes into account greater company risks, for example, mergers, new products or trying to expand into new markets. It joins information technology risk assessment to the future plans of the business.
Best for: Enterprises undergoing growth or restructuring phases.
Key Steps in Conducting an Information Security Risk Assessment
A good risk assessment method links the technology’s weak points to what harms could happen to the business. A clear framework helps Indian organizations, particularly those handling confidential user data or operating in controlled industries, to be careful and lawful.
Step 1: Asset Identification
List all the information assets in the organization. Examples are hardware, software, places where data is kept, network components and even third-party tools. You need to know which assets are important before proceeding in cyber security.
Step 2: Threat and Vulnerability Detection
Recognize malware, insiders and DDoS as possible threats. After that, relate the risks to the weaknesses in your systems, applications and processes. Nearly always, this step consists of scanning for vulnerabilities and interviewing the people in charge. This is an essential part of an application risk assessment and network security assessment
Step 3: Risk Analysis
Assess the probability that a risk will happen and how much damage it could do. Risk priorities can be identified by using qualitative (low, medium, high) or quantitative approaches (like financial cost). Now is the time to divide lower-level issues from major exposures.
Step 4: Risk Evaluation and Prioritization
Check if your risks are within the risk limits you have set for your organization. When talking about Artificial Intelligence (AI), it is important to consider the regulatory and business contexts. HIPAA risks might be more important to a healthcare provider than just having general IT problems.
Step 5: Mitigation Planning
Generate strategies that allow your organization to manage or get rid of identified risks. It may consist of fixing security holes, adjusting settings or updating the rules and training for employees.
Step 6: Documentation and Reporting
Collect your results and turn them into a simple report for the decision-makers. Ensure there is a summary of the project, clear technical risk listings and ideas for minimizing those risks. By documenting, the company is more ready for any future checks or audits.
Step 7: Continuous Monitoring
Risks keep changing as new threats and technology show up. After important IT changes or incidents, establish a routine to re-assess. If you constantly keep an eye on your network security, it will continue to fit your organization’s risk profile.
Common Challenges in Information Security Risk Assessments
Performing an information security risk assessment is not limited to running through a list of steps. Dealing with sensitive data often reveals more operational issues than what was expected for Indian businesses. Below is a list of the challenges seen most often:
1. Poor Asset Visibility
Not knowing all the systems, applications and data in a network leads to important risks being left out, mainly with cloud or a hybrid model.
2. Misalignment with Business Impact
Data and analyses are usually shared apart from business circumstances. An issue with a medium severity rating might result in critical risk if it is found in a payment gateway or patient records.
3. Excessive Dependence on Automated Tools
Scanning with machines is quick, though it tends to generate false alarms and overlook problems that require code logic analysis. In other words, this can result in unnecessary expenses or failed security.
4. Fragmented Remediation Processes
While teams get assessment results, they often do not have enough details, tools or training to handle the issues effectively. It leads to a larger number of outstanding risks.
5. Regulatory Oversights
Audits can cause problems for companies if their reports do not use RBI guidelines, CERT-IN directions or ISO 27001 during cybersecurity audits.
Latest Penetration Testing Report

How Qualysec Helps Indian Organizations Mitigate Risk
Qualysec uses a planned and detailed method for Indian companies to identify risks in information security according to local and regulatory rules, providing comprehensive information security and risk assessment services.
1. Business-Aligned Risk Prioritization
Qualysec doesn’t stop at finding security issues alone. They go through each problem, checking its business impact so you separate the important issues from the unimportant ones.
2. Manual + Automated Testing
Using a mix of automated techniques and thorough manual tests, Qualysec finds out about recognized vulnerabilities and tricky flaws in business processes.
3. Compliance-Ready Reports
The reports are designed to comply with Indian regulations such as ISO 27001, PCI DSS, HIPAA and guidelines from the RBI which helps during audits..
4. Actionable Remediation Support
You get details that go beyond the report. Team members offer advice for improvements, test options for a new outcome and give recommendations after the assessment.
5. Industry-Specific Experience
Being experts in India, Qualysec tailors its approach because it understands the unique risks in fintech, government and healthcare.
6. Clear Remediation Roadmaps
Every assessment ends with recommendations for fixing the problems, allowing IT or DevSecOps teams to address the issues.
You can also explore our in-depth guide on Vulnerability Assessment Methodology to understand how we work.
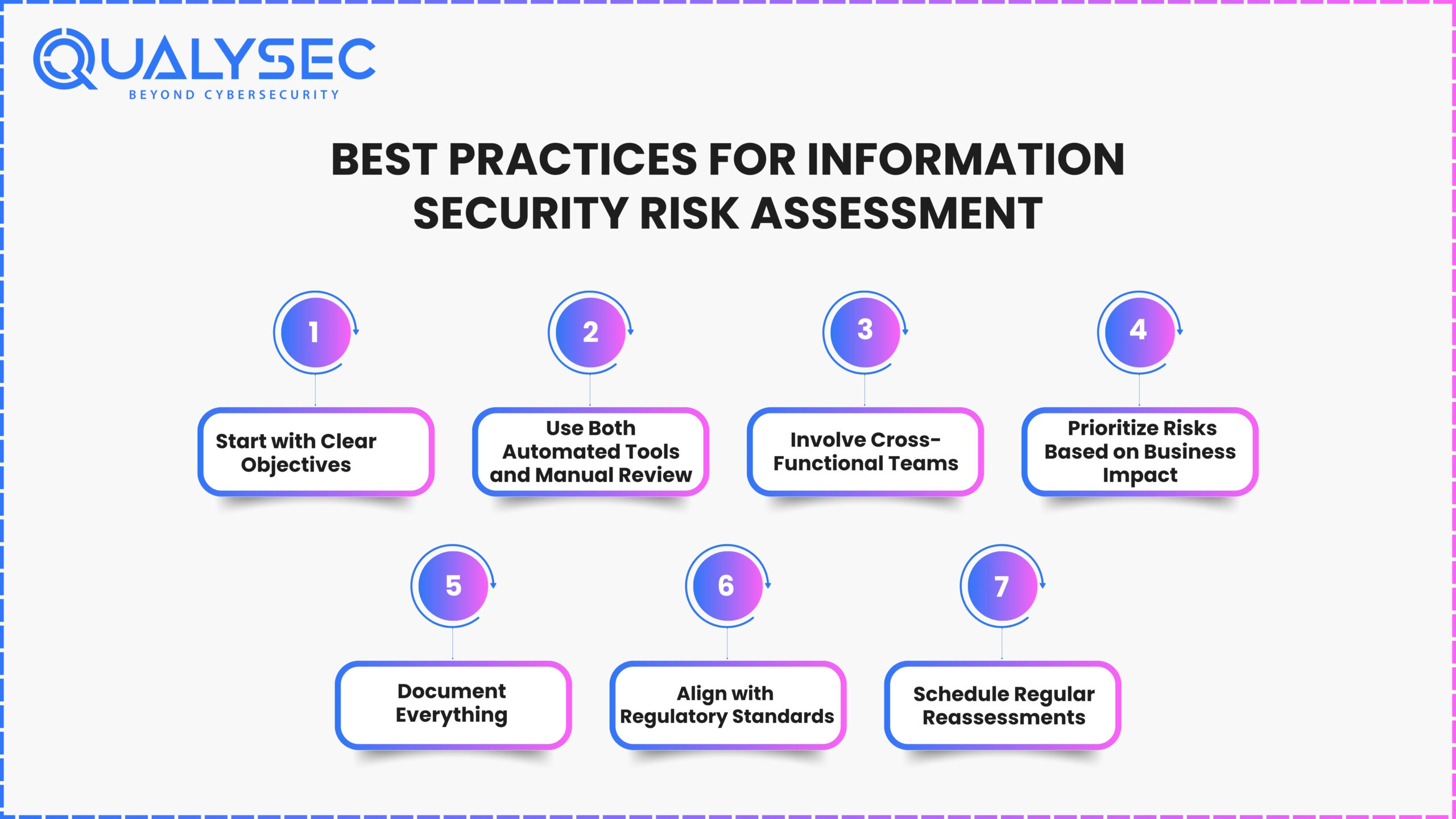
Best Practices for Information Security Risk Assessment
Doing a risk assessment only once is not enough. For long-term results and strength, practice the following ideas:
1. Start with Clear Objectives
Decide on the main goal for conducting the assessment. Did the company have to achieve compliance, want better security posture or respond to a recent incident? This allows the process to fit your circumstances.
2. Use Both Automated Tools and Manual Review
Although automated scanners are quick, they may overlook different risks. The manual review done by Qualysec helps by uncovering missing logic and high vulnerabilities in the code.
3. Involve Cross-Functional Teams
Let IT, compliance, business units and development teams be involved in the process. This makes certain that the company’s critical devices and data are looked after, especially for a thorough network risk assessment.
4. Prioritize Risks Based on Business Impact
The significance of risks can vary a lot. A single vulnerability on a public network may cause less harm than a problem in a large financial application.
5. Document Everything
Keep detailed logs of all assets, possible risks, how they will be handled and actions that need to be completed. It makes sure that both the organization and the future auditors will have the data they need.
6. Align with Regulatory Standards
Map your information security assessment to standards like ISO 27001, RBI Cybersecurity Framework, or HIPAA to stay audit-ready.
7. Schedule Regular Reassessments
Today’s threats are different and your infrastructure must keep up. Keep re-checking your evaluations, as changes brought by new updates or additional tools might bring more vulnerabilities to light.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
Just listing vulnerabilities after a system scan is not all that an information security risk assessment covers. It lets organizations in India know where they stand now, their risks and what actions to take before a threat leads to an incident. Because there are more digital systems being used, additional regulations and more elaborate attacks, businesses must carry out these assessments.
Proactive risk assessment helps startups, government bodies and enterprises in healthcare or retail to know what to do and how to do it to keep their digital assets protected.
Need help getting started?
Connect with Qualysec for a contextual, compliance-ready information security risk assessment tailored to your industry.
























































































































































































































































































































0 Comments