In 2025, we see cyber threats becoming a more advanced threat, particularly in Singapore. The Cyber Security Agency of Singapore (CSA) indicated a 22% increase in cybercrime compared to last year. Attacks like phishing, ransomware and data breaches are being made against both small and large businesses. As more businesses adopt a digital future, the risk of cybercrime increases. A single successful cyberattack can lead to severe revenue losses, downtime, or even legal complications. This is why conducting a cybersecurity threat assessment is critical. A cybersecurity threat assessment provides an independent evaluation of your systems to identify vulnerabilities, provide insight and establish safeguards to protect your systems and data.
What Is a Cybersecurity Threat Assessment?
Cyber threats are increasing rapidly and are also becoming increasingly sophisticated, particularly with the increasing number of companies transitioning to the digital space. Cybercrime accounted for almost 50% of reported crimes in Singapore in 2024, with phishing, ransomware and online scams being the most common types of cybercrime, according to the Cyber Security Companies in Singapore (CSA).
With many businesses moving to a cloud service, e-commerce platform or digital payment application, the threat of attacks will only increase. For small and mid-sized businesses, just one successful cyber-attack can lead to significant challenges such as lost money, damaging sensitive personal data, or creating interruptions in business operations.
This is why it is essential to perform periodic cybersecurity assessments and evaluations. These assessments and evaluations determine vulnerabilities and provide insights into the likelihood of suffered threats, and actions to take to remain protected.
In Singapore, which is an advanced technology-driven society where many businesses use interfaces and digital systems while fulfilling strict compliance regulations, it is important for all businesses, size and at any stage of development to remain proactive and ahead of cyber threats.
Why Is It Important for Singapore Businesses in 2025?
The amount of cyber threats in Singapore is increasing rapidly in 2025, according to the Cyber Security Audit Firms (CSA), there is a 20% increase in cybercrime threats. Common examples of attacks include phishing and ransomware, targeted at businesses of all sizes. With many businesses adopting more cloud services, artificial intelligence, and remote work comes with a greater chance of attack as well.
There are newer threats like AI-driven malware and insider threats, which are sometimes even harder to identify. A seemingly small event can lead to a catastrophic data breach, which is why you should regularly get an assessment of your cyber threats, especially if you are a business taking customer data, or you’re conducting online payments.
Common Types Of Cyber Threats To Watch Out For
Cyber attacks, both in terms of prevalence but also in terms of sophistication, are becoming increasingly common. Companies must remain vigilant. By recognizing that there are several different threats, and with the knowledge of which attacks are most prevalent, you can identify how to defend your systems and data before they are compromised.
Whether it is phishing emails, ransomware, or insider threats, recognizing those threats is the first step to being capable of building stronger security.
- Phishing is an email attack where users click on fake emails or attachments that prompt them to give out personal information.
- Ransomware locks the files of a business until the ransom is paid.
- Malware is software designed to damage, access, and control systems.
- Insider threats happen when employees misuse their access.
- DDoS attacks put enough traffic on your company website to crash it.
- Credential stuffing is an attack using a person’s stolen username and password to access their accounts.
Steps To Perform A Cybersecurity Threat Assessment
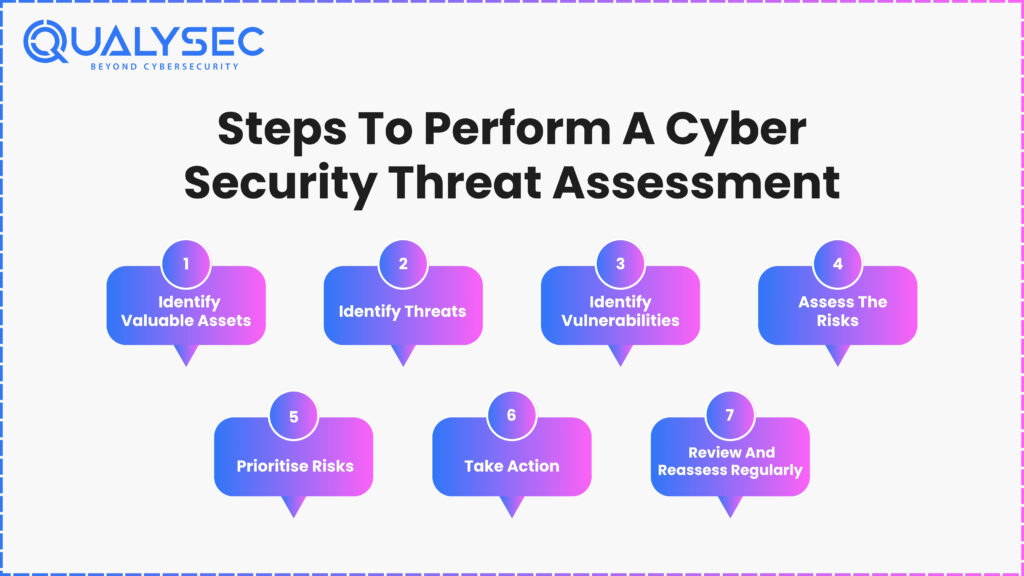
Conducting a cybersecurity threat assessment is an important step to mitigate cyber-attacks on your business. A cyber-security assessment helps to: understand vulnerabilities in your systems; identify threat types; and mitigate risk before any actual damage occurs. Whether your business is small or large, if you follow the correct steps, you can significantly reduce the risk of cyber attacks.
1. Identify Valuable Assets
Begin with your valuable digital assets. This includes customer data, emails, payment systems, and business applications. This step will provide you with insight into which assets you want to protect to the greatest extent.
2. Identify Threats
Consider what bad can happen. Potential threats include hacking, phishing, employee misuse, or even physical threats, such as natural disasters that affect data centers. Regularly reviewing news cycles and industry reports will ensure you are informed.
3. Identify Vulnerabilities
Review your weak points. Are your software and devices up to date? Are employees following safe practices while working online? Weak passwords and outdated systems leave doors open for threat actors.
4. Assess The Risks
Once you understand the threats and vulnerabilities, evaluate how likely each one is to occur and the impact that it could have. For example, a high probability of phishing combined with significant data loss equals a high risk.
5. Prioritise Risks
You won’t be able to treat all of these risks immediately. Prioritise the risks that are most significant to your business first. Use an easy rating scale: Low, Medium, High, or Critical.
6. Take Action
Implement sensible safeguards. Examples of reasonable security measures include multi-factor authentication (MFA), use of anti-virus tools, user training, and regular and consistent data backups. For a high risk to your organisation, act quickly.
7. Review And Reassess Regularly
Cyber risks are constantly evolving. Don’t just assess once. Continually re-evaluate your threat assessment every few months or every time you make a significant change to your systems. Being relevant is important.
Latest Penetration Testing Report

How To Manage Cyber Risk
Managing cyber risk is a crucial issue for any business in Singapore, regardless of its size and scope. When operations shift online, so too does the potential for a cyberattack. However, adopting best practices can help protect important data, systems, and customer trust. There are several easy measures you can take to minimise your cyber risk.
1. Create a Cyber Risk Management Policy
Develop a straightforward and transparent methodology that outlines how your company will effectively manage cyber threats. The company’s cyber security risk assessment policy should include the process for identifying, evaluating, and mitigating risks. Assign responsibilities so everyone understands who is accountable for which parts of the process.
2. Train Staff
Staff are often the first line of defence. By conducting regular employee training, the team will learn about common threats, such as phishing scams, and how to react to them safely. An informed team may reduce the risk of making avoidable errors.
3. Enable Secure Configurations
Never leave factory defaults in place. Always configure your software and hardware to enhance security. It should include elements such as strong passwords, encryption, and appropriate access controls to safeguard access to your systems, especially from unauthorized attacks.
4. Continuous Monitoring
Cyber threats can emerge at any time. Use an SIEM (Security Information and Event Management) tool to keep an eye on your network for unusual activities. If you can detect things early, then you can prevent or minimize damage.
5. Get Experts
Even if you do not have cyber experts in-house, you should still get help. You can collaborate with a local cybersecurity firm in Singapore to undertake an assessment of your systems and make improvements to your defences. Their expertise could save you time and hassle.
Conclusion
Cyber threats in Singapore are getting smarter, and no business is too small to be a target. Even one attack can cause serious damage. That’s why implementing regular cybersecurity threat assessment must always be done. They allow businesses to assess threats promptly, remediate those threats, and strengthen defences from any future threats. The most effective way to stop threats is to outsmart threats. Don’t allow a threat to compromise your business, data, clients or customers.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
FAQs
1. What is threat assessment in cybersecurity?
A cyber threat assessment is a systematic approach to identifying potential digital threats that may pose a risk to your business. This process can help you understand which systems may be vulnerable and how to protect them best.
2. How to do a cybersecurity risk assessment?
The first step is to identify your key digital assets, followed by identifying potential threats and vulnerabilities. Once your assets and threats have been identified, you can assess the level of risk and then take appropriate actions to reduce or eliminate that risk.
3. What are the five types of cybersecurity threats?
The five basic threats are phishing, ransomware, malware, insider threats, and DDoS attacks. These threats can lead to lost data, data corruption, loss of access to systems or applications, and other significant events that can materially disrupt the business.
4. What are the five steps of security risk assessment?
The five steps are to identify your assets, identify potential threats, identify your vulnerabilities, analyse the risk, and take action on the risk to manage and reduce risk.















































































































































































































































































































































0 Comments