Financial and healthcare companies in Singapore manage enormous volumes of extremely sensitive data, ranging from personal identification to medical records and financial transactions, in today’s digital scenario. Cybersecurity penetration testing (pen testing) is now necessary to protect vital systems with the faster-than-ever evolution of cyberthreats.
This blog examines the importance of cyber security pen testing, how to approach it, and the best practices adapted to the specific challenges encountered by companies in Singapore’s financial and healthcare industries.
Why Cybersecurity Penetration Testing Matters for Singapore’s Financial & Healthcare Firms
Let’s find out the best reasons why cybersecurity penetration testing is important for Singapore’s financial & healthcare firms:
1. Regulatory Compliance
Under Technology Risk Management Guidelines, the Monetary Authority of Singapore (MAS) imposes stringent cybersecurity measures for financial institutions. One major requirement is cybersecurity pen testing.
The Ministry of Health (MOH) and the Personal Data Protection Commission (PDPC) anticipate healthcare professionals to use strong cybersecurity measures that include regular ethical hacking.
2. Protection of Sensitive & Personally Identifiable Information (PII)
Exposure of personal identifiable information (PII), medical records, or consumer financial information can result in significant reputational damage, regulatory fines, and erosion of public trust.
3. Rising Cyberthreat Landscape
Cyber security threats have become more focused and complex, from sophisticated ransomware attacks aimed at hospitals to financial fraud scams.
4. Defense-in-Depth Strategy
By simulating real-world attacks under regulated settings, cybersecurity penetration testing confirms layers of defense ranging from application security to perimeter firewalls.
What Is a Cybersecurity Penetration Test?
Ethical hackers who try to expose vulnerabilities regularly conduct a cybersecurity penetration test, a simulated cyberattack. Unlike vulnerability scanning, which automatically identifies flaws, penetration testing in cyber security uses a hands-on approach to bypass barriers and gain access to sensitive assets.
Cybersecurity Pen tests can evaluate employee susceptibility to phishing, physical security, and other factors, either externally focused (e.g., compromising public-facing systems like web apps and VPN portals) or internally focused (e.g., gaining domain privilege or moving laterally once inside the corporate network).
The Five Stages of Cybersecurity Penetration Testing
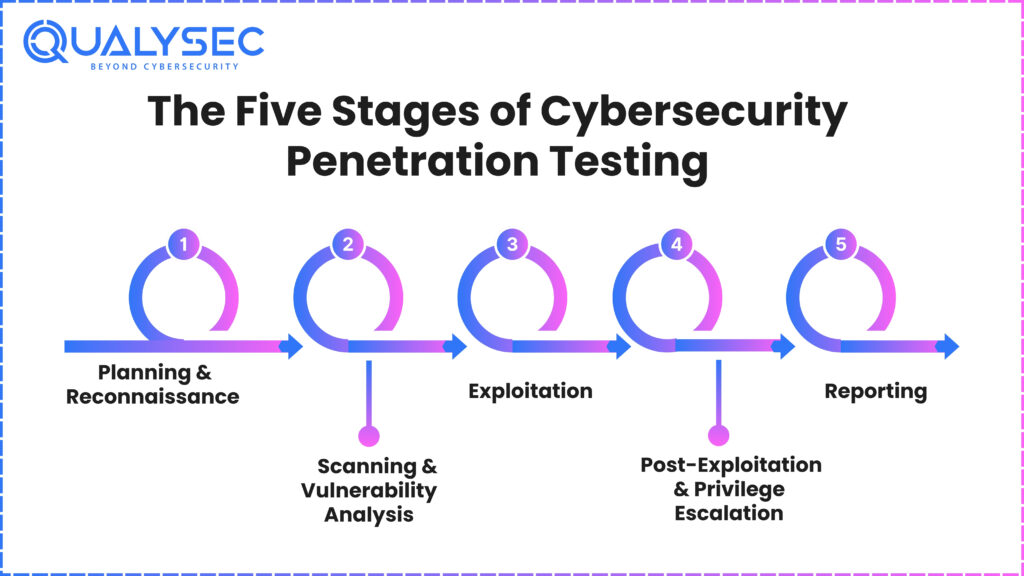
A thorough penetration testing in cybersecurity process has a methodical approach:
1. Planning & Reconnaissance
Define the scope (target systems, rules of engagement, timing), clearly outline collaboration with IT/security teams, and evaluate tolerable risks.
Reconnaissance: Create a profile of the target environment using publicly accessible data, including DNS records, IP ranges, website footers, subdomains, open ports, email harvests, and others.
2. Scanning & Vulnerability Analysis
Search for open ports, incorrectly configured services, out-of-date software, weak encryption, and other flaws using tools like Nmap, Nessus, or OpenVAS.
3. Exploitation
Targeted phishing attacks or network protocol exploitation can all be included in exploitation.
4. Post-Exploitation & Privilege Escalation
Following compromising a system, like an employee workstation, ethical hackers look at lateral mobility (e.g., exploiting trust relationships, discovering domain credentials) to raise permissions toward high-value assets such as servers storing PII or PHI.
5. Reporting
- Reporting of weaknesses, evidence, risk assessments, and proposed solutions.
- Offer a concise executive summary, severity specifics, proof-of-concept data, and recommended action.
Add a retesting plan and a remediation strategy.
Find the right penetration testing companies in Singapore—free quick guide!
Latest Penetration Testing Report

Key Considerations for Singapore’s Financial & Healthcare Sectors
Below are the key considerations for Singapore’s Financial & Healthcare Sectors
1. Data Protection & Privacy
PDPC mandates “reasonable security plans” for companies to stop unauthorized access, collection, use, disclosure, copying, alteration, disposal, or other risks to personal information. Cybersecurity Penetration testing guarantees adherence to data protection best practices and helps to satisfy Principle 12 of the PDPA.
2. Supporting MAS & MOH Regulations
MAS expects regulated entities to annually perform cybersecurity pen tests or after significant modifications to essential systems. MOH’s cybersecurity advice for healthcare providers also calls for regular evaluations, especially for systems processing patient data and medical equipment.
3. Legacy & Operational Technology (OT) Systems
To guarantee system availability and patient safety, healthcare professionals may rely on legacy medical equipment difficult to patch. OT security issues must be included in cybersecurity penetration testing.
4. Cloud & Hybrid Environments
Make sure cybersecurity pen testing includes cloud misconfigurations, weak API endpoints, and unsafe storage buckets as businesses move toward hybrid models using AWS, Azure, or GCP.
5. Third‑Party & Vendor Risk
Financial and healthcare companies often partner with medical software companies, cloud providers, payment gateways, and fintech platforms. Supply-chain risk assessment must be part of cybersecurity pen testing.
Pen‑Testing Methodology: Best Practices for Singaporean Firms
1. Define scope exhaustively
Define asset inventory (IP ranges, domains, application endpoints) and surroundings (DEV, QA, PROD). For testing time, communication channels, and impact tolerances, set some rules of engagement.
2. Use Licensed Frameworks
Align with international norms like OSSTMM, PTES, or NIST SP 800-115. For the financial and healthcare industries, include local considerations from MAS and PDPC to strengthen Cybersecurity for Financial Services.
3. Combine Manual & Automated Testing
Use automated tools for preliminary scanning; however, count on competent ethical hackers to exploit corporate logic bypasses, chained vulnerabilities, or sophisticated scenarios.
4. Simulate Real‑World Threats
Incorporate tests for spear‑phishing, password brute force, business email compromise (BEC), and insider threats. Use intelligence on active APT groups targeting healthcare and financial businesses.
5. Ensure Safe Execution
Test during low-traffic windows to minimize company interruption. Use segmented settings for thorough exploitation. For healthcare systems, verify with clinical engineering teams to ensure no risks to patients or procedures.
6. Document Evidence & Provide Actionable Reports
Each discovery should include screenshots, logs, time stamps, and correction recommendations. Classify according to risk level. Incorporate suggested compensating techniques and mitigating controls.
7. Retesting & Continuous Security
Once fixes are implemented, arrange retests to confirm remediation. Harmonize cybersecurity pen testing with CI/CD cycles and significant infrastructure improvements. Think about purple teaming or bug bounty for ongoing awareness.
- Combines manual & automated testing for accurate results
- Runs 200+ industry-standard test cases
- Zero false positives – all findings are manually verified
- CI/CD integration for smooth DevSecOps workflows
- Get a real-time dashboard to track and manage vulnerabilities
- Receive developer-friendly reports with clear remediation steps
- Share publicly verifiable pentest certificates
- Supports compliance with SOC2, ISO27001, PCI-DSS, HIPAA, and more
- Trusted by startups to enterprises in Fintech, SaaS, Healthcare, and beyond

Choosing the Right Pen-Testing Partner
Here are the factors that will help you choose the right penetration testing services partner:
1. Deep Sector Expertise
Choose a pentesting service provider aware of MAS and PDPC responsibilities. Their advisors ought to be familiar with financial systems, healthcare IT technologies, and medical device risk.
2. Certified Ethical Hackers
Seek testers holding accepted certifications such as OSCP, CEH, CREST, or other recognized certifications. They offer credibility and sophisticated testing techniques.
3. End-to-End Security Services
Top companies provide red teaming, vulnerability management, training, and incident response playbooks in addition to cybersecurity pen testing.
4. Local Presence & Support
A Singapore-based partner with on-ground resources can navigate local compliance laws, send timely communication, and grasp regional threat nuances.
Sample Pen‑Testing Scope for Organizations in Singapore
A common configuration is as follows:
-
- External Web Applications include loan calculators and customer portals.
-
- Domain controllers, file servers, and internal networks, including the DC
-
- Cloud systems: IAM setup, S3 buckets, AWS EC2
-
- Corporate Wi‑Fi access points
-
- Email and Authentication Systems: Exchange, MFA, AD, Azure AD
-
- Third-party connectors: payment gateways, healthcare systems.
-
- Physical examinations: badge cloning, office access
-
- Social Engineering: Spear-phishing, credential harvesting
-
- Risk tolerance, asset sensitivity, and regulatory necessity determine the extent of testing in terms of internal versus external, credentialed versus black-box.
Real-World Challenges & Mitigation Strategies
Below are the real-world challenges & mitigation strategies:
1. Outdated Medical Devices
-
- Challenge: Critical OT equipment may be running unpatchable older firmware.
-
- Solutions: Enforce stringent access, network microsegmentation, secure VLANs, anomaly-based IDS, and compensating forensic controls.
2. Zero‑Day & Business Logic Leaks
-
- Problem: Flaws in processes are not visible by scanners; weaknesses are unknown to the public.
-
- Solution: Expert-led manual testing augmented with situational business-tree assessment, threat modeling, and logical checks.
3. Data Leakages & Misconfigurations
-
- Challenge: Cloud misconfigurations (e.g., open S3 buckets) and insecure APIs can leak sensitive information.
-
- Perform configuration audits, live tests, and automated CI/CD scanning to enforce hardened baselines.
4. Insider Threats
-
- Challenges: Malicious workers or contractors, or just normal human mistakes.
-
- Solution: Grey‑box testing, role‑based access control (RBAC), MFA, staff awareness, and user‑audit logging.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Interpreting & Acting on Cybersecurity Pen‑Testing Reports
Below are the interpretations & actions to be taken on cybersecurity penetration testing reports:
1. Focus on Critical Issues
Rank topics according to risk impact and chance:
- High, for instance: unlimited administrative access and remote code execution.
- Medium: missing security headers, stale TLS
- Low: information leaks, password strength reports, among others
2. Provide Context for Developers & Management
Employ transparent stories:
- Developers get config changes, code pointers, or reproductive steps.
- Managers get risk maps, executive summaries, and possible business impact.
3. Define Action Plans
Every edition ought to include:
- Actions of remediation for assigned stakeholder (e.g., IT team, vendor partner)
- Timeline and follow-up demands
4. Retest & Continuous Oversight
Include continuous vulnerability scans and frequent pen tests in your security posture to revalidate settled problems.
Emerging Trends in Cybersecurity Penetration Testing
Here are the emerging trends in cybersecurity penetration testing:
1. AI-Driven Testing
Auto-prioritization of vulnerabilities by way of artificial intelligence and sophisticated logic-based scripting.
2. Attack Surface Monitoring
Early exposure detection through ongoing scanning of cloud applications, APIs, dependencies, and exposed endpoints.
3. DevSecOps & CI/CD Integration
Integrating pen-testing tools into development processes allows quick, automatic security checks with every release.
4. Purple Team Collaboration
Defense (blue) and attack (red) teams work together in a coherent manner to improve security posture by means of coordinated techniques and feedback loops.
Take the First Step with Qualysec
Qualysec is ready to assist if your Singapore-based healthcare or financial company is prepared to advance its cybersecurity. Let’s find out how:
- Considerable domain experience in MAS-regulated businesses and healthcare systems, making us one of the leading cybersecurity companies in Singapore.
- OSCP and CREST-accredited certified ethical hackers.
- From red teaming to CI/CD-integrated testing, complete services.
- Local presence in Singapore for easy cooperation.
Contact Qualysec right away to arrange a strategic cybersecurity pen test customized to your needs and protect your essential systems and private information from clever attackers.
FAQ
1. What is penetration testing in cybersecurity?
Cybersecurity Penetration testing—also known as ethical hacking or cybersecurity pen testing—is a procedure whereby specialist testers mimic actual attacks to find flaws in networks, systems, and apps.
2. What are the five steps of cybersecurity penetration testing?
- Defining scope, rules, and collecting intelligence is known as planning and reconnaissance.
- Automated programs check for exposures and open ports using scanning.
- Exploitation is when ethical hackers proactively exploit vulnerabilities.
- Post‑Exploitation: Privilege escalation, lateral movement, data exfiltration
- Reporting: Recording results, risk levels, and remedial activities
3. What are the different kinds of cybersecurity penetration testing?
The three different kinds of cybersecurity penetration tests are:
- Black‑Box Testing: Simulates an outside attacker; testers lack internal knowledge.
- Full code and architecture disclosure to testers; extensive analysis of internal threats defines White‑Box Testing.
- Partial knowledge, such as low-level credentials, a hybrid strategy

















































































































































































































































































































































0 Comments