Mobile devices are necessary for everyday living in the present highly connected culture, whether one is using them for personal or professional reasons. As people progressively began relying on smartphones to finish creating notifications for various work, the significance of mobile devices increased. Mobile device security is becoming increasingly crucial since most sensitive data, including finances, e-mails, and business data, is stored on mobile devices.
When it comes to failing to take proper precautions to protect your device, it may become a convenient target for cybercriminals. Such attacks might result in data theft, identity theft, or unauthorised utilisation of personal information.
This entire blog will allow you to gain insight into mobile device security, the importance of mobile security testing, and following best practices to protect confidential data.
What Is Mobile Device Security?
Mobile device security refers to the security measures of these technological gadgets. It means safeguarding devices such as smartphones, tablets, and laptops from risks associated with cyber threats, including data loss, authentication fraud, login failure, and many more.
Mobile devices have emerged as an essential component of everyday existence. These days, individuals use devices for more than just killing time, such as social media and communication. Technologies that facilitate professional and commercial networking have made mobile devices such as PCs that can be utilised anywhere.
Mobile devices must therefore be protected to prevent them from being used as a way to give up personal data. Individuals frequently face dangers to the security of their mobile devices, such as phishing sites and programs, leaks of information, malware, hacking attempts, and more. Mobile App Security Testing Tools can help address these risks.
Latest Penetration Testing Report

Typical Risks to Mobile Device Security
Mobile devices are essential in everyday life, but they also pose a lot of safety hazards. By understanding these hazards, one will enhance the safety of one’s devices and personal data.
1. Malware/Viruses
Malicious links, spyware, and malware can infiltrate mobile devices. Such risky applications can monitor your actions, acquire information from you, and even damage the device itself.
It is critical to acquire applications from reliable sites since harmful programs might destroy private data such as financial details or credentials once loaded.
2. Phishing assaults
Phishing is a prevalent tactic in which attackers use fake emails, messages, or sites to trick you into disclosing sensitive data like passwords for logins or account details. It typically takes the form of fake websites or emails that seem legitimate on cell phones.
Security risks may arise from engaging in these activities; consequently, it is critical to check the source prior to providing any sensitive data.
3. Lack of authorization
Someone might obtain private data if they physically approach your mobile device without authorization. That may occur if systems are not adequately protected using reliable passwords or fingerprint security locks or if they remain unattended.
Those who are not permitted may download unwanted programs once they are enrolled. Companies may also utilize information that was previously recorded to follow where you go.
4. Wireless Internet Access Threats
Using public WiFi exposes the device to the possibility of hacking by a third party attempting to obtain your personal information.
Attackers have an easier time obtaining details about the things you do online, accessing passwords, and various other sensitive data because open networks occasionally lack the level of safety protections present in encrypted networks.
This danger might be mitigated by utilizing a VPN, or virtual private network, or performing critical activities on free WiFi.
5. Essential Elements of Mobile Device Security
Mobile device security is built upon several key components that function together to secure your data. Knowing these crucial elements will help you make wise decisions that will improve the security of the device you are using.
- Safety Options of the Operating System
- Safety of Applications
- Security on the Network
- Identity Verification of Users
- Encryption of Information
Major Mobile Device Security Errors to Beware of
Basic faults might put you at risk, especially when it involves mobile security in cyber security. Becoming knowledgeable of such typical threats will allow you to safeguard your private and professional data more effectively. The following are some crucial errors to avoid:
- Avoiding routine software updates might expose the device to prevalent safety risks. Regularly upgrade the applications and the operating platform.
- Hackers can gain easier entry to simple or frequently used credentials. If feasible, use multiple authentication methods and use passwords that are strong and distinctive.
- Public networks are often unencrypted, making it easy for criminals to capture data while utilizing free wireless connections without a VPN. When connecting to public WiFi, always utilize a virtual private network (VPN).
- Many programs want to get hold of your location, acquaintances, and other private data. Carefully ensure that applications always obtain the necessary rights, as they can exchange information about you with an outside company that regularly shows advertisements on your device’s display.
Mobile Device Security Best Practices
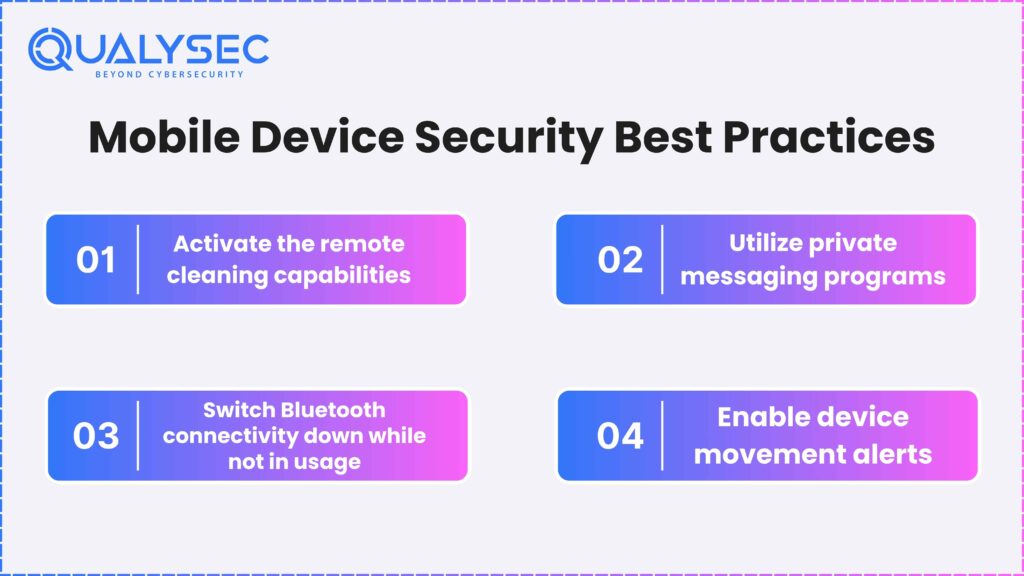
There are more ways to make sure your mobile devices are secure besides avoiding frequent mistakes. You must take preventative action in order to be aware of potential risks. The recommended actions listed below can help you keep your mobile devices safe:
1. Activate the remote cleaning capabilities.
Set up the device to the extent that, in the unlikely circumstance that it goes missing or is stolen, it’s possible to freeze and erase it instantly. It ensures that sensitive data remains safe even if you become unavailable to reach the device in question.
2. Utilize private messaging programs.
To safeguard your discussions and prevent illicit access to your encrypted messages, use applications for messaging with total encryption.
3. Switch Bluetooth connectivity off when it is not in use.
Keeping Bluetooth enabled exposes the device to various attackers. To decrease vulnerabilities, switch it off while it is not in use.
4. Enable device movement alerts.
To detect vulnerabilities swiftly, enable warnings for unusual activities on the device, which include fresh accounts or illegal access requests.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
The Function of Businesses in Mobile Security
Businesses play a crucial role in Mobile Application Security Assessment since mobile policies and procedures have a significant influence on how employees and customers handle their mobile devices.
Also Read:
What is Mobile App Security?
What is mobile applications security testing?
Conclusion
With the growing importance of mobile devices in every aspect of our lives, mobile device security is more essential than ever. This piece of writing has shown everyone the need to implement solid safety measures to defend oneself from a range of threats, like spyware, phishing emails, and unauthorized access to information.
Understanding the differences between iOS and Android security allows you to tailor your planning to the specific system. Understanding which common faults are to be avoided improves the health of the device you use.





















































































































































































































































































































































0 Comments