As the digital age transforms the healthcare sector today, connected medical devices, or Medical IoT Security (Internet of Medical Things), are becoming increasingly pivotal to patient care. From wearables that monitor vital signs in real time to infusion pumps that administer measured doses, these devices enhance efficiency and outcomes.
But though Medical IoT is convenient and innovative, it is accompanied by the danger of catastrophic cybersecurity attacks. Most of these devices are utilized in open environments, sometimes with inadequate encryption, password protection, or update mechanisms.
In this article, we’ll explore what makes IoMT devices so susceptible to threats, real-world incidents that underscore the danger, and a set of best practices for healthcare providers to secure their connected medical ecosystem. Let’s dive into how the industry can strike a balance between innovation and security.
What is Medical IoT (IoMT)?
Internet of Medical Things (IoMT) is a network of medical devices and software applications that communicate with each other over the internet to collect, transfer, and analyze health data.
The devices are designed to facilitate clinical care by:
- Remote monitoring of vital signs
- Automating medication dispensing
- Enabling real-time diagnosis
- Enabling telemedicine platforms
Examples are:
- Wearable heart rate or fitness monitors
- Smart glucometers
- Implantable defibrillators
- Remote patient monitoring devices
- Connected medical imaging equipment, like CT or MRI scanners
With hospitals, clinics, and even residences becoming increasingly networked, IoMT is at the forefront of data-driven healthcare. Yet, with increasing connectivity comes a wider attack surface for hackers and cyber attackers to exploit.
Why Is Medical IoT Security So Important?
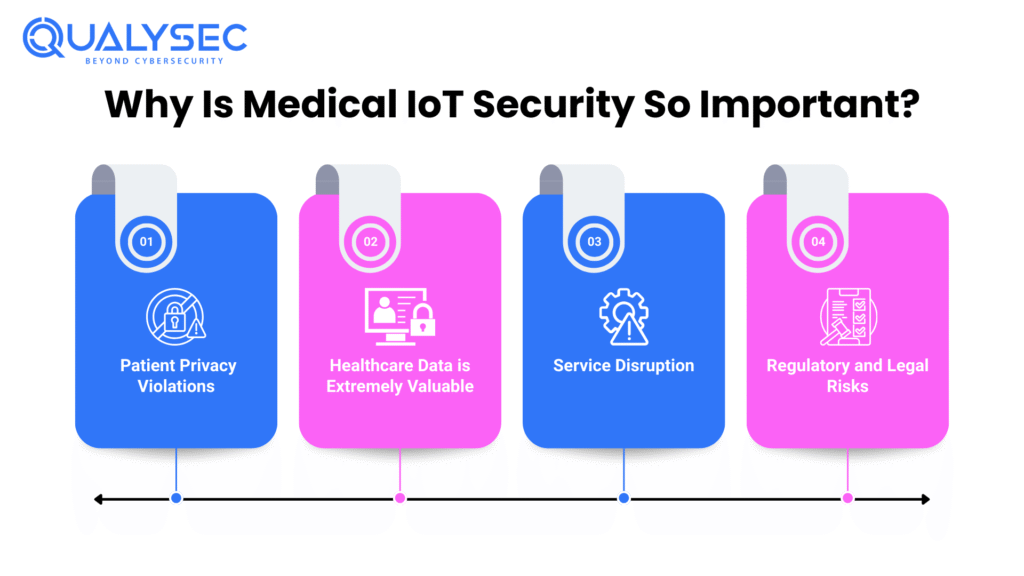
IoMT security isn’t simply an IT problem—it’s a matter of life and death.
Take a remote hack on a pacemaker or a dose level change hack on an insulin pump. The consequences can be fatal. Even aside from patient safety, the dangers of bad cybersecurity are:
a. Patient Privacy Violations
IoMT devices collect sensitive data—blood pressure, blood sugar levels, even mental health readings. A breach can leak the data, violating patient confidentiality and legal privacy.
b. Healthcare Data is Extremely Valuable
While credit card information can be canceled and reissued, medical records consist of thorough, longitudinal data. Because of that, stolen healthcare information is money on the dark web.
c. Service Disruption
Ransomware that targets hospital networks may delay surgery, cause diagnosis delays, and put lives on hold, especially when life-critical equipment like ventilators or monitors is taken offline.
d. Regulatory and Legal Risks
Not protecting medical IoT puts one at risk of large penalties and fines by law under HIPAA, GDPR, or HITECH.
Protecting IoMT is protecting patients, maintaining healthcare integrity, and maintaining public trust.
Latest Penetration Testing Report

Common IoMT Device Weaknesses
Most medical devices were not built with internet connectivity. Adding connectivity without re-engineering the core leaves some weaknesses:
a. Older Operating Systems
More sophisticated devices use outdated versions of OS (like Windows XP or previous Linux), on which no security patches are being developed.
b. Weak or Default Passwords
The majority of devices come with default passwords that are never altered by their users, and hence, the attackers easily gain access.
c. Lack of Encryption
Unencrypted data from certain IoMT devices is transmitted over hospital networks, which makes them vulnerable to interception.
d. No Patch Management
Healthcare environments do not typically replace equipment for fear of breaking it, and so vulnerabilities remain unmitigated for years.
e. Inadequate Access Controls
Equipment is also connected to hospital-wide networks with no segmentation, so attackers can laterally move if one device is compromised.
Real-World Incidents That Reveal the Risks
The threats are not theoretical. Let’s take a look at real-world attacks where Medical IoT vulnerabilities were exploited:
a. WannaCry Ransomware Attack (2017)
This ransomware attack also hit the UK National Health Service (NHS) severely. It shut out hospital staff from patient records and canceled over 19,000 appointments, including surgery. Network-enabled devices like MRI scanners and blood storage devices were impacted.
b. Medtronic Insulin Pump Vulnerability (2019)
Thousands of Medtronic insulin pumps were recalled in the US by the FDA due to their vulnerability, as the attackers had access to remote insulin doses through them, leading to potential serious injury.
c. Ryuk and Conti Ransomware Attack U.S. Hospitals
In recent times, highly structured ransomware gangs have attacked American hospitals, encrypting data and demanding payment for its release. The attacks commonly involve targeting unprotected medical devices.
These are evidence of a bleak reality: cybercriminals are targeting healthcare facilities, and one can sense the effect.
IoMT Security Regulatory Frameworks
In an attempt to fight growing cyberattacks on healthcare, several regulatory bodies have established standards and guidelines:
a. HIPAA (U.S.)
The Health Insurance Portability and Accountability Act requires healthcare providers to safeguard electronic protected health information (ePHI) using technical, administrative, and physical controls.
b. FDA Guidelines
The U.S. Food and Drug Administration offers pre-market and post-market guidance for cybersecurity of medical devices, and the encouragement of manufacturers to take technical security from the outset of design.
c. GDPR (EU)
The General Data Protection Regulation mandates strict controls on the collection of personal data, including health data, for any firm handling data of EU citizens.
d. NIST Cybersecurity Framework
This is an American federal standard that presents formalized processes for handling cybersecurity risk in all industries, including healthcare.
Compliance is mandatory—it’s a law and a critical element of planning cybersecurity.
Securing Medical IoT Devices with Best Practices
As protection against risks of this type, medical workers and equipment providers should team up. That is how it goes:
a. Inventory and Asset Management
Have a current roll call of devices connected.
Establish categories for device types, operating systems, vendors, and documented exploits.
b. Network Segmentation
Isolate IoMT devices from the heritage hospital IT infrastructure and guest wireless.
Employ VLANs and firewalls to limit access of devices to critical systems only.
c. Secure Communication Channels
Enwrap data passing between devices and servers in encasing (e.g., TLS protocols).
Refrain from relying on unencrypted Bluetooth or public wireless.
d. Regular Software Updates and Patching
Schedule maintenance windows for updating.
Work with vendors to roll out security patches once they are available.
e. Authentication and Access Control
Implement multi-factor authentication (MFA) where possible.
Turn off unnecessary ports and services to reduce exposure.
f. Monitor and Respond in Real-Time
Implement intrusion detection systems (IDS) to alert of odd behavior.
Set up alarms on anomalous device behavior, such as communication with unknown IPs.
g. Employee Training and Awareness
Train all employees—doctors, nurses, and admin—on phishing, password best practices, and suspicious activity detection.
h. Establish a Security Incident Response Plan
Create and drill a response to a cyberattack.
Establish roles, responsibilities, and timelines for containment, recovery, and reporting.
Applying AI and Machine Learning to IoMT Security
As cyberattacks become more and more sophisticated, traditional security products are not adequate. Artificial Intelligence (AI) and Machine Learning (ML) offer proactive, dynamic defense capabilities.
How AI Can Help
Anomaly Detection: AI can continuously monitor devices 24/7 and alert on atypical activity, like sudden spikes of data or attempted unauthorized access.
Threat Prediction: ML algorithms trained on historical data can identify trends and forecast probable threats before they occur.
Automated Response: Some systems can automatically quarantine infected devices to prevent threat propagation.
These technologies improve speed and accuracy in threat detection and response.
The Future of Medical IoT Security
As Medical IoT grows, we can expect a series of trends to shape its future:
a. Zero Trust Architecture
A model in which all users, devices, and connections are continuously authenticated—no implied trust.
b. Blockchain for Device Integrity
Blockchain can offer immutable logs and secure sharing of device information among authorized parties.
c. Cybersecurity-by-Design
Vendors will begin embedding security into device hardware and software from the beginning, rather than as an afterthought.
d. More Regulatory Oversight
Hear more about stricter worldwide regulations and audit processes aimed exclusively at medical device cybersecurity.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion: Creating a Secure Connected Healthcare System
The potential of Medical IoT Security is tremendous—better diagnostics, quicker care, and improved results. But unless it’s done with decent security, all that can rapidly become a risk.
Health care providers, manufacturers, and regulators need to collaborate to make interrelated devices secure, compliant, and robust. A strategy that crosses technology, policy, and education is the solution to keeping patients safe in the digital age.
Because in medicine, a cybersecurity breach isn’t an IT problem—it’s an assault on human life.















































































































































































































































































































































0 Comments