Cybersecurity attacks, and particularly data breaches, are slowly emerging as a serious problem, given the increasing frequency of such situations. As companies collect and store more information on their networks, safeguarding these assets becomes even more critical. Data is the lifeblood of any organization: the more data a business collects, the more it can analyze to enhance the provision of services, organization of work, and targeting of the required market. However, there is a problem with the increased volume of data, which makes companies more appealing to hackers looking for a weakness to gain access to sensitive data. Software Penetration Testing plays an essential role in identifying these vulnerabilities to protect your information.
A data breach occurs when an organization releases or communicates private, secure, and confidential data in an untrusted setting. This may be a direct hack of a business’ security network or when a member of staff leaks information by emailing it to the wrong person. In an effort to curb data loss, many companies are adopting Software Pen Testing as a necessary security standard.
What is Software Penetration Testing?
Software Penetration Testing also referred to as “pen-testing”, entails undertaking a range of tests to expose vulnerabilities within a particular software system. This process, supported by pen testing software, is similar to how testers examine an actual vulnerability in the software to open up its flaws and weaknesses to outside attacks. Professional security specialists conduct pentesting, one of the most popular and effective methods for determining the security levels of software systems.
The pen testing process sometimes only takes a team, such as a security tester and a report writer. The security tester performs a number of tests in order for him or her to gain entry into the system and determine areas that are vulnerable to attack. During the test phase, the report writer of the pen testing prepares a detailed report that outlines the discovered vulnerabilities, the ways that such vulnerabilities were exploited, and the losses that the company would incur if the given vulnerabilities were not remedied. The client then uses this report to make decisions on reinforcing security measures.
The different types of Software Pen Testing Services include:
- Web App Pen Testing – Identifies vulnerabilities in web-based applications.
- Mobile App Pen Testing – Assesses security risks within mobile apps.
- Cloud Pen Testing – Focuses on vulnerabilities in cloud infrastructure.
- Network Pen Testing – Evaluates the security of network components.
- Blockchain Pen Testing – Examines security in blockchain systems.
Who Performs Software Penetration Tests?
A possible insight is that the success of a penetration test can be closely related to who conducts it. In an ideal world, security professionals perform software penetration tests with minimal prior knowledge of the targeted system. This approach allows the unfamiliar tester’s perspective to reveal weaknesses that the system’s developers may not have considered. For this reason, corporations allow third-party contractors to conduct such evaluations since they come in with impartial views. These external contractors are known as ethical hackers– personnel who are hired to find flaws and offer recommendations, as well as have permission to invade.
It is worth noting that ethical hackers can possess a varied background. Some are professional developers with college degrees, and some are certified pen testers holding degrees in computer science and certifications as professional developers with either a college degree or certification specifically in Wynhet forwards or analytical mathematics or sciences. Some learn themselves. While those are the former black hat hackers, ethical hackers are hackers that were involved in the wrong side but now work for good. Who is best suited for a pen-testing job can also differ from company to company, depending on the objectives of the organization and the type of pentest being undertaken.
Want to secure your software from cyber-attacks? So why wait? Talk to our cybersecurity expert now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Software Pen Testing VS Software Testing VS Software Security Testing
- Software Penetration Testing: It also known as a pen test, is a security evaluation that simulates real-world cyber-attacks to identify potential vulnerabilities in a system.
- Software Testing: It is the process of assessing a software product or application’s performance, functionality, behavior, and more to ensure the software works properly.
- Software Security Testing: It focuses on identifying and fixing security weaknesses in a software application to protect it from unauthorized access or breaches.
“Related Read: SaaS Application Security Testing”
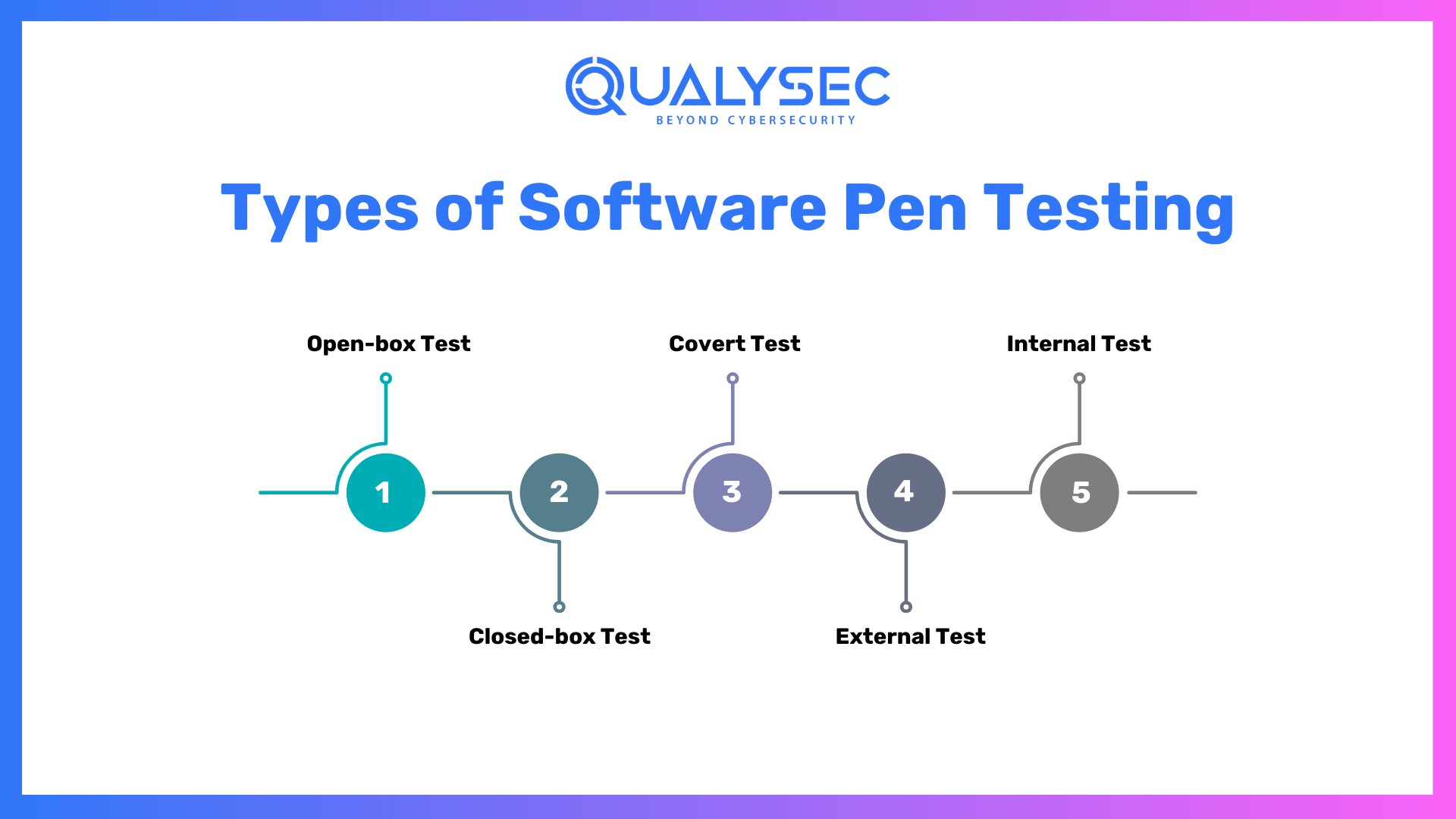
Types of Software Pen Testing
There are several types of software penetration testing, each designed to assess security differently. The main types of pests include:
- Open-box Test: In this test, the pentester is given some prior information about the target company’s systems. Such information may encompass areas of the company security measures, network configuration, or anything about the company that one might consider pertinent in the pursuit of his/her objective. This type of test is usually meant to challenge a hacker who has insider information or has partial control over the system by use of social engineering.
- Closed-box Test: Often referred to as a single-blind test, the assessor has no information about the target company’s systems other than its name. This is something that will help imitate an attack by an outsider with no prior knowledge of the target. This setup demands the tester to search for information on his own, which makes it better suited for emulating external threats.
- Covert Test: Also referred to as the ‘double-blind’ test, this kind is conducted in a way that the majority of the company remains uninformed, including IT and security staff. Only a few top managers know it’s happening. The test checks how the company reacts to a surprise attack. It’s like a real cyber threat.
- External Test: In this test, a hacker tries to access the company’s public systems. This includes websites and email servers. The hacker works from outside the company. This test checks if these public systems are safe.
- Internal Test: In this test, the hacker works inside the company’s network. It shows what damage an insider could cause. The test checks if internal security is strong enough to block unauthorized actions.
The Software Penetration Testing Process
A pentest generally follows five key stages as part of the penetration testing methodology, each of which plays a vital role in assessing and understanding the system’s security. The five stages include:
1. Planning and Reconnaissance
Setting the Objectives and Scope: The present phase offers an overview of the test, which covers what systems are to be tested, what the objectives are, and what approaches will be utilized concerning the timelines.
Conducting Test Scenarios: The tester obtained the required details, such as network information, domain names, and mail servers, to learn how the system works and look for any possible weaknesses. This phase is essential as it assists the testing phase of the requirements.
2. Scanning
Fixing Problems: During the scanning process, the testers try to forecast the behavior of certain pieces of software that have not yet been executed by inspecting its source code. Static analysis tools allow for single-pass review of code in relation to other known problems.
Detective Gathering: in static analysis, the code is created first and then run to see how it behaves. This represents an innovative way that shows the software reacting to different intrusion attempts in as much as other factors sensitive to the intervention from static analysis do not apply.
3. Gaining Access
Taking Advantage of Growing Pains: For this phase, the testers will scan for the vulnerabilities they have identified to gain access to the system. A variety of tools are used, including SQL injection, cross-site scripting, and backdoor installation. This series of events allows the testers to recreate what any real-life attacker would do and help understand the magnitude of damage that could result from such actions.
4. Maintaining Access
Simulating Persistent Threats: In this step, testers try to stay inside the system without being noticed. This is like how advanced persistent threats (APTs) work. APTs hide in systems for a long time, slowly collecting important information. By staying hidden, testers check if the system has strong monitoring and alert systems.
5. Analysis
Compiling the Report: In this step, testers make a detailed report. The report lists all weak spots, the data they accessed, and how long they stayed hidden. Security experts then review the report. They use it to improve defenses, like setting up Web Application Firewalls (WAF), to fix weaknesses and protect the system better.
Want to see a real software penetration test report? Tap the link below and download one right now for free!
Latest Penetration Testing Report

Other Categories of Penetration Testing Techniques
Software Penetration testing methods vary based on the test’s focus area, whether it’s an external, internal, or combined approach:
- Blind Testing: The only information the pentester has is the name of the company that is the target. The main aim of this method is to help security personnel witness how a real attack plays out and how the organization goes about countering it.
- Double-Blind Testing: Another reasonable precaution is to ensure that even the security staff has no prior knowledge of the test. The reason for doing this is to eliminate any chances the security staff have to prepare for the test, thus offering a true reflection of the organization’s level of security.
- Targeted Testing: This is an approach where both the tester and the security team complement each other in the course of the test by exchanging ideas. This collaborative approach assists the security personnel in understanding the key aspects of the security team and improving their response plans.
The Relation between Pen Test Engagements and a Web Application Firewall
Web Application Firewall is an intermediary system that sits between an external client and an internal application. WAF is used to place an additional layer on top of web security systems that will help to stop malicious activities. But what is the relationship between the two systems? WAF creates a top-down view of the traffic, enabling Layer 7 security policies and allowing all HTTP(S) traffic. Pen testing frameworks usually have HTTP requests as their core components, and WAF provides a way for developers to filter out which components are accessible to users. So why bother about WAF?
- Using WAF Logs: During a penetration test, especially when it isn’t hidden, testers can use Web Application Firewall (WAF) logs. These logs show areas where the app might be weak in security.
- Post-Test Improvements: After a pentest, companies often change WAF settings. This helps stop the types of attacks that were found in the test. For example, if one type of attack worked, WAF settings can be adjusted to block similar attacks in the future.
- Meeting Compliance: Penetration testing also helps companies meet important security rules. Some rules, like PCI DSS (Payment Card Industry Data Security Standard) and SOC 2 (Service Organization Control), require regular security testing. A certified WAF is sometimes needed, such as with PCI-DSS 6.6. These rules make WAFs an important part of staying compliant.
Common Tools for Software Penetration Testing
There are several popular tools used in software pen testing:
- OWASP ZAP: This is a free, open-source tool. It helps testers find weak points in web applications. It’s easy to use, so it works for both beginners and experts.
- Vega: Vega is also free and open-source. It helps detect different types of weaknesses in web applications.
- SQLmap: This tool is designed for SQL injection attacks. It automates these attacks to help testers find and test SQL vulnerabilities safely.
Choosing a Software Penetration Testing Vendor
If a company wants to hire a software pen-testing vendor, here are some things to consider:
- Skill and Expertise: Make sure the vendor has highly skilled security experts. They should be able to do the specific tests needed for the company.
- Reputation: Research the vendor’s reputation in the industry. Read reviews, and if needed, ask for references from other companies.
- Methodology and Budget: Know the vendor’s approach to pentesting and how they handle sensitive data. Also, make sure their pricing matches the company’s budget.
Why Companies Trust Qualysec for Software Penetration Testing?
Software systems are easily broken by hackers, but companies cannot afford the risk. With the emerging threat of cyberattacks, businesses need proactive security solutions. One of the best ways to prevent breaches is comprehensive penetration testing.
QualySec offers expert penetration testing services trusted by companies of all sizes. Our professional team ensures that your applications and software are secure, compliant with security standards, and protected against latest threats.
Conclusion
Software Penetration testing is very important for any company that wants to stay safe from cyber threats. These tests help find weak spots before hackers do. By running regular penetration tests, companies can find issues and fix them early.
For extra security, using WAFs along with regular testing gives a layered defense. This means immediate risks and long-term security gaps are covered. WAFs keep an eye on outside threats, while penetration tests catch new risks before they cause problems. With both defenses, companies are much safer.
Whether a company builds its own pentesting team or hires a trusted vendor, it should make penetration testing a priority. Cyber threats are always growing, so staying ahead is key. Regular testing, updating defenses, and using tools like WAFs are all important steps to stay secure in a digital world.
FAQ’s
Q. What is a penetration test in software?
A: This is one type of security testing method that is used to expose security vulnerabilities within a particular software system.
Q. How much does an average software pentest cost?
A: A software penetration test can cost between $500 to $30,000, depending on a few other metrics including the complexity of the apps and the scope of testing.
Q. What is the timeline for Software Penetration Testing?
A: On average, It usually takes around 7-10 days to complete, based on the scope and complexity of the application.





























































































































































































































































































































0 Comments