SOC 2 penetration testing or (Service Organization Control Type 2) is a process simulated attack conducted to achieve SOC 2 compliance. It is done to identify vulnerabilities in applications, networks, or other digital systems and ensure their security measures are up to date.
Developed by the American Institute of Certified Public Accountants (AICPA), SOC 2 is an industry standard that organizations need to comply with. It demonstrates that the organization has adequate security measures to manage and protect customer data.
In 2023, nearly 353 million people were affected by data breaches and leakage. With such high risk, organizations need to comply with SOC 2. Therefore, this blog will give you all the information you need on SOC 2 penetration testing, including its process and best practices.
Understanding SOC 2 Compliance
Before we dive into why penetration testing is important to achieve SOC 2 compliance, let’s understand this industry regulation.
What is SOC 2?
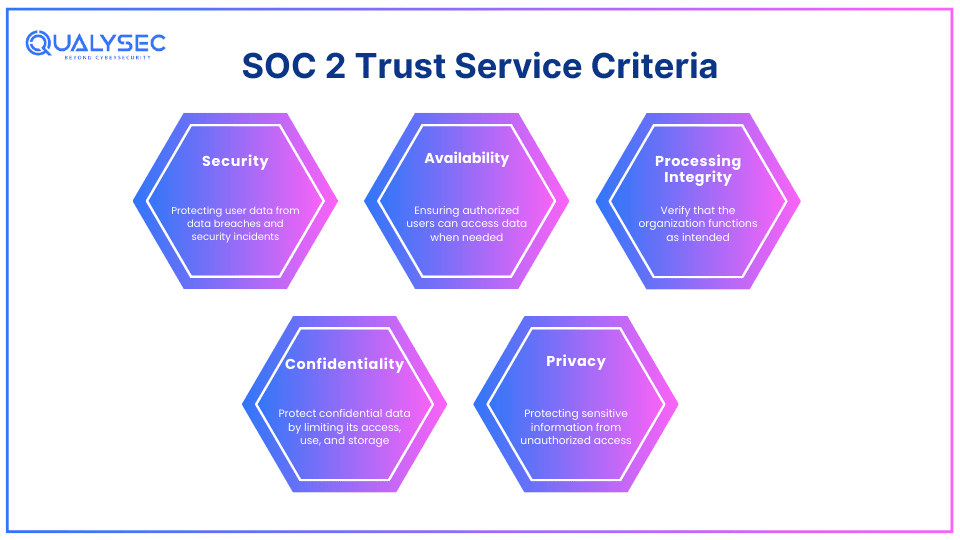
SOC 2 or Service Organization Control Type – 2 is a security framework that outlines how an organization should protect customer data from data breaches and security incidents. It is an auditing procedure that tests whether the organization has the necessary security measures to protect customer data. The AICPA designed SOC 2 framework based on 5 “Trust Service Criteria (TSC)”:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
It is basically the checklist that the organization needs to tick, in order to achieve SOC 2 compliance.
Why SOC 2 Matters?
Complying with SOC 2 is not a small task. It takes a significant amount of money, time, planning, and work. However, it is equally rewarding for the company that achieves this. The benefits of SOC 2 Penetration Testing compliance exceed far beyond just a security certificate, such as:
1. Improve your Services
A SOC 2 audit doesn’t just show you where your security lacks and how it can be improved. It also shows you different ways to streamline your business operations. It helps you make necessary changes to your security measures that improve your organization’s efficiency. For example, it will tell you to add data protection measures like multi-factor authentication, access control policies, etc.
2. Saves Time and Money in the Long-Run
Having a SOC 2 certificate helps you to do business with larger enterprises. It even gives you a list of best practices to protect sensitive data. Customers are drawn more toward those businesses that guarantee protection for their data. Additionally, a SOC 2 certificate makes it easier to achieve other certifications due to their similarities, for example, ISO 27001.
3. Protect your Brand’s Reputation
It doesn’t matter how appealing your brand is or how loyal your clients are. If you experience a single data breach, customers will leave you like rats leave a sinking ship. Additionally, it can cost you millions on recovery, cleanup, new controls, and building customer trust from scratch. Implementing SOC 2 policies can save you from these devastating consequences.
4. Gives you a Competitive Edge
Any company can say they take customer data protection seriously. But customers don’t really care for such claims unless they provide some evidence. This is exactly what a SOC 2 certificate does. Achieving SOC 2 compliance proves that you have top-notch security. This might be the nudge that may make many companies and customers choose you over your competitors.
The Role of Penetration Testing in SOC 2 Compliance
The trust service criteria (TSC) of SOC 2 compliance mention that organizations need to conduct some kind of security testing for their security measures, such as penetration testing.
What is Penetration Testing?
Penetration testing is a cybersecurity practice that tries to find and exploit the vulnerabilities in digital systems to check their resilience against real attacks. Pen testers, also called “ethical hackers” use automated tools and manual techniques to “act” like attackers and test the effectiveness of an organization’s current security measures. You can choose from a wide range of pen test services based on your business, such as:
- Web app penetration testing
- Mobile app penetration testing
- Network penetration testing
- API penetration testing
- Cloud penetration testing
- IoT device penetration testing
- AI/ML penetration testing
Why Penetration Testing is Essential for SOC 2
By simulating real-world attacks, penetration testing helps strengthen the organization’s defenses and ensure they meet SOC 2 penetration testing requirements.
- Identify Vulnerabilities: A pen test helps uncover security weaknesses in systems and applications.
- Assess Security Controls: It checks the effectiveness of the current security controls.
- Simulate Real-World Attacks: By mimicking potential attacks, it shows how different systems would react to actual attacks.
- Strengthen Defenses: Insights from a pen test help in improving the organization’s security posture.
- Protect Sensitive Data: Ensures that personal and sensitive customer data is securely handled.
- Meet SOC 2 Requirements: Fulfils the need for security testing to achieve compliance with SOC 2
Conducting SOC 2 Penetration Testing
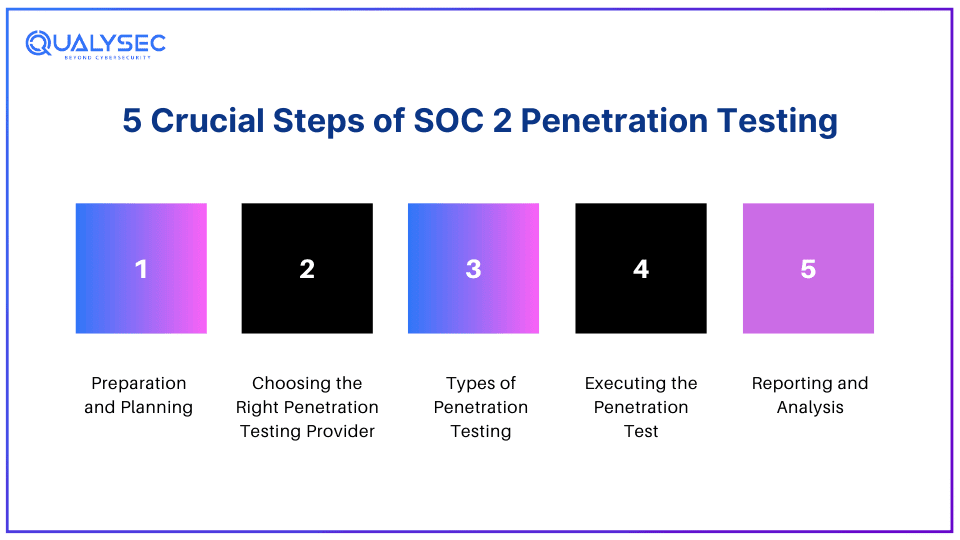
Conducting SOC 2 penetration testing is a critical step since it helps ensure the security and compliance of the systems. From preparation and planning to reporting, the process involves several key stages.
1. Preparation and Planning
Before starting a pen test, one must prepare thoroughly and plan the essentials. This may include defining the scope, identifying key applications and systems to test, and outlining clear objectives. Proper planning ensures that the test covers all critical areas required to meet SOC 2 compliance.
2. Choosing the Right Penetration Testing Provider
Look for a penetration testing provider with a strong track record. Ensure it has relevant certifications and expertise in providing SOC 2 compliance testing. The right provider will understand your requirements and provide tailored solutions to effectively identify security vulnerabilities and meet compliance needs.
3. Types of Penetration Testing
There are various types of penetration testing one can choose from, such as external, internal, and application-specific testing. External tests focus on security threats outside of the network, while internal tests simulate insider threats. Application-specific tests target vulnerabilities in software applications (web, mobile, and cloud).
4. Executing the Penetration Test
Penetration testers use various automated vulnerability scanning tools and manual testing techniques to identify vulnerabilities. They follow various industry-approved methodologies and frameworks, such as OWASP Top 10, SANS 25, PTES, etc. to simulate real-world attacks. It requires skilled testing professionals with high technical knowledge.
5. Reporting and Analysis
After testing, the testers generate detailed reports. These reports outline identified vulnerabilities and their potential impact when exploited. Additionally, they include suggestions for fixing these vulnerabilities. This helps organizations make necessary improvements in their security measures that are required for SOC 2 compliance.
Ever seen a real penetration testing report? Well, now’s your chance! Tap the link below and download a sample report right this moment!
Latest Penetration Testing Report

Best Practices for SOC 2 Penetration Testing
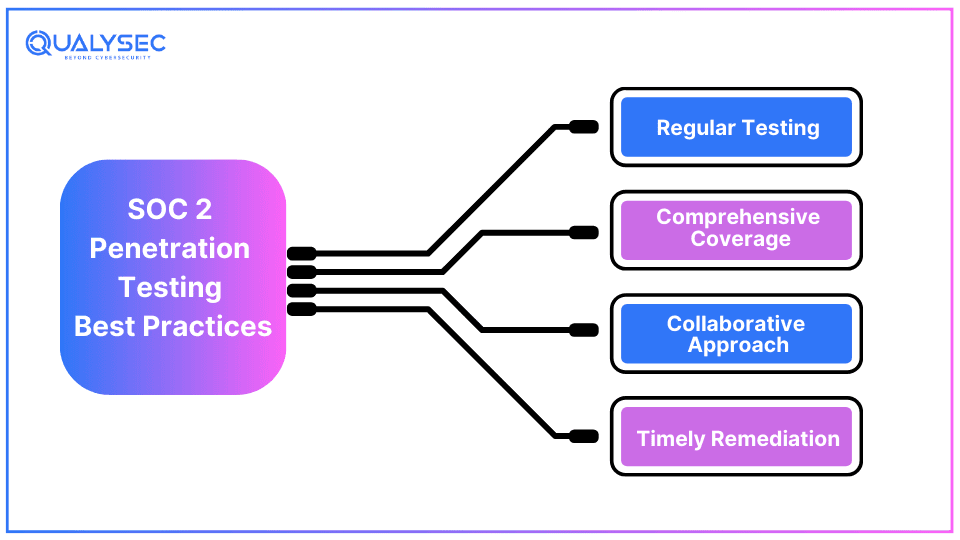
To effectively identify security weak points and a robust security posture, security auditors recommend implementing SOC penetration testing best practices, such as:
1. Regular Testing
Conducting pen tests regularly is crucial to stay ahead of evolving threats and maintain security. regular testing helps identify new vulnerabilities that may emerge if there are changes in the systems or its code. this ensures that the security measures are up to date, which supports SOC 2 compliance.
2. Comprehensive Coverage
Cybercriminals can breach an organization from any point. Ensure the penetration test or SOC 2 vulnerability scanning you do examines all critical systems, including applications and networks. This helps uncover vulnerabilities across the entire IT infrastructure, not just specific components. Additionally, it supports SOC 2 compliance and overall data security.
3. Collaborative Approach
This signifies that the external pen testing team should work closely with the internal development team to fix the identified vulnerabilities. It involves effective communication so that all relevant information is shared and that the testing is thorough. Teamwork in pen testing enhances the accuracy of the test results and supports a more effective remediation process.
4. Timely Remediation
One must address the identified vulnerabilities on time to maintain proper security and compliance. Timely remediation involves prioritizing vulnerabilities as per their impact and fixing them as soon as they are discovered. This helps prevent potential security breaches and ensures the organization continuously meets SOC 2 compliance requirements.
Emerging Trends in SOC 2 Penetration Testing 2024
In 2024, one of the major emerging trends in SOC 2 penetration testing is advanced threat simulation. This involves using various sophisticated techniques to mimic real-world cyberattacks more accurately. Advanced threat simulations help organizations to understand in a better way how their systems can resist new and complex attacks.
Advanced threat simulation includes techniques like “adversary emulation”, where the testers replicate the techniques and procedures of known attackers. With this technique, organizations can identify and address security weaknesses more effectively. Additionally, this approach is crucial for staying ahead of evolving cyber threats and ensuring compliance with SOC 2.
Conclusion
The SOC 2 compliance standard was established by the AICAP in 2010 to check whether organizations have the necessary security measures to protect customer data. The SOC 2 penetration testing is a critical part of achieving this compliance. Over the years, it has garnered more roles and is now a prized element for organizations. It helps them prevent data breaches and security incidents, attract more customers, and protect brand reputation.
Do you want to perform SOC 2 penetration testing? Qualysec has skilled pen testers who have the required certifications and knowledge to test your applications and systems inside and out. Protect your business from online threats and comply with this industry-standard now! Tap the link below to talk to our experts!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
FAQs
Q: Does SOC 2 include penetration testing?
A: While OSC 2 itself doesn’t explicitly mention performing penetration testing, it is indirectly needed to check the systems for vulnerabilities and up-to-date security measures.
Q: Is SOC 2 a standard or framework?
A: SOC 2 or Service Organization Control Type 2 is a cybersecurity framework that outlines how organizations should protect customer data.
Q: What is SOC 2 testing?
A: SOC 2 compliance testing means that the tester or auditor has tested for security controls that are needed to meet the SOC 2 criteria. Moreover, it is a general analysis of an organization’s security whether it can resist a data breach or other security incidents
Q: Who needs SOC 2 audits?
A: An organization that stores, manages, or transmits any kind of customer data, likely needs to comply with SOC 2 standards.

























































































































































































































































































































0 Comments