In today’s digital age, you may see that web applications are everywhere, from online banking and shopping to social media and business portals. They offer convenience and accessibility to the user but they may also present significant risks if not properly secured. Web application security protects these applications from cyber threats that could compromise data, disrupt services, or cause financial losses.
In this blog, we will cover what website application security is, why it’s important, common threats, best practices, and the tools available to keep your web applications secure.
What is Web Application Security?
Web application security is a branch of cybersecurity focused on protecting web applications, which are software programs accessed through a web browser. It involves securing the application from various threats, ensuring data confidentiality, integrity, and availability, and preventing unauthorized access or manipulation. It consists of a range of practices and tools designed to defend web applications against common cyberattacks such as SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks.
Web applications are typically more vulnerable than traditional software applications because they are accessible over the internet, making them prime targets for cybercriminals. Therefore, implementing strong robust web application security measures is important for any organization that relies on these applications for its operations.
Why is Web Application Security Important?
Web app security testing helps to find security vulnerabilities in Web applications. It is essential for several reasons:
1. Data Protection: Web applications often handle sensitive information, such as personal details, financial data, and intellectual property. Without proper security, this data can be exposed to unauthorized parties, leading to data breaches, identity theft, and significant financial losses.
2. Compliance: Many industries are governed by strict regulations that require companies to protect their customers’ data. If a company fails to comply with these regulations it can result in hefty fines and also damage to an organization’s reputation. Web application security helps ensure compliance with standards like GDPR, HIPAA, and PCI DSS.
3. Reputation Management: A security breach can severely damage an organization’s reputation. Organizations that do not protect customer data risk losing business as customers lose faith in them. However, when a company ensures safe and sound web application security it can help maintain and even enhance its reputation.
4. Operational Continuity: Cyberattacks on web applications can disrupt business operations, leading to downtime, loss of productivity, and financial losses. Secure applications are less likely to suffer from such disruptions, ensuring continuous operation, and can be this way very useful.
5. Competitive Advantage: All those companies that prioritize web application security testing can differentiate themselves from their competitors. A strong commitment to security can attract customers who are increasingly concerned about the safety of their personal information.
What are Common Web Application Security Threats?
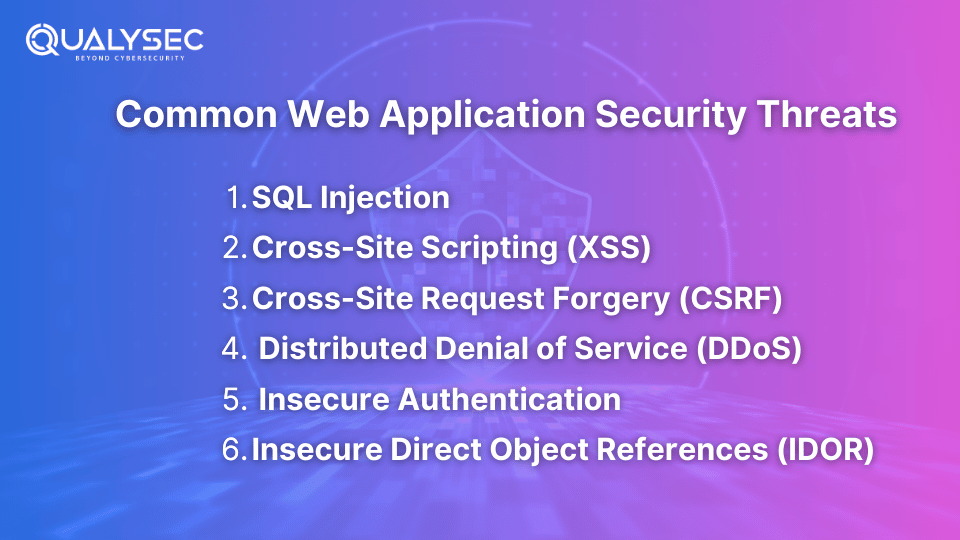
Web applications face a variety of threats, some of the most common include:
1. SQL Injection: This attack involves injecting malicious SQL queries into a web application’s database query process. It can lead to unauthorized access to sensitive data, data manipulation, or even deletion.
2. Cross-Site Scripting (XSS): XSS attacks involve injecting malicious scripts into a web application’s output, which are then executed in users’ browsers. This can lead to session hijacking, defacement, or the theft of cookies and other sensitive information.
3. Cross-Site Request Forgery (CSRF): In CSRF attacks, a user is tricked into executing unintended actions on a web application where they are authenticated, such as transferring funds or changing account details.
4. Distributed Denial of Service (DDoS): DDoS attacks overwhelm a web application with traffic, rendering it unavailable to legitimate users. These assaults have the potential to seriously interrupt business operations and cause downtime.
5. Insecure Authentication: Weak or improperly implemented authentication mechanisms can allow attackers to gain unauthorized access to a web application. This includes issues like poor password policies, lack of multi-factor authentication (MFA), and insecure session management.
6. Insecure Direct Object References (IDOR): IDOR vulnerabilities occur when an application exposes internal implementation objects (like files, directories, or database records) to users. These references can be manipulated by attackers to gain access to private information.
Best Practices for Enhancing Web Application Security

To protect your web applications from potential threats, it’s essential to follow the best practices for security:
1. Regular Security Testing:
Vulnerability scanning, as well as penetration testing, is mandatory to perform to determine security issues in the web applications that you develop.
2. Use HTTPS:
Encryption is important when it comes to the exchange of data, between the user’s browser and the web application, always adopt the use of HTTPS (SSL/TLS). This ensures that information cannot be intercepted by the attackers.
3. Implement Strong Authentication:
You should always enforce strict password policies, insist on MFA, and make your sessions secure to prevent anyone from gaining access to your accounts.
4. Sanitize User Inputs:
You have to sanitize all user inputs to prevent SQL injection, cross-site scripting, and all other injection-type attacks. Make sure your application can only take data in the right format.
5. Keep Software Up to Date:
You should update your web application software and all that belongs to it such as dependencies, frameworks, and libraries. This is true since vulnerabilities that are known can be addressed and closed within a short time to prevent hackers from exploiting them.
6. Access Control:
You should follow policies of least privilege and grant access only where it is necessary for the user’s requirements. Ensure that there is a routine check of the permission settings given to the users.
7. Security Training:
Another one is that you have to provide your development team with information on how to code securely and what threats are currently existing. The best way to avoid many of these openings is through increased awareness and training.
8. Security Monitoring and Logging:
Make sure that you incorporate the log and monitor system that can help detect security and respond to it in the shortest time possible. It is also important to ensure that logs are adequately secured and checked for any illegitimate activity.
Top 5 Web Application Security Tools
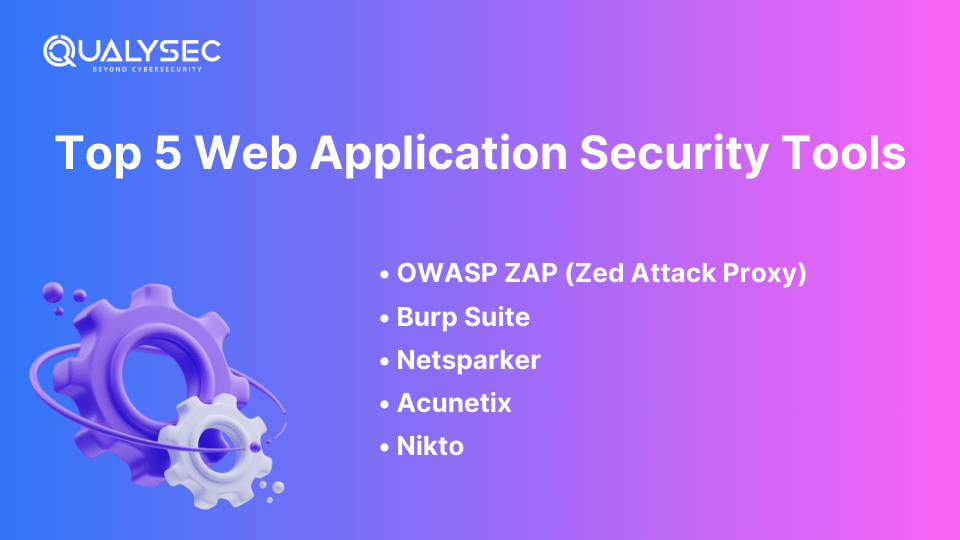
To enhance website application security, several tools can help identify and mitigate vulnerabilities. If you are searching for the most useful web application security tools, we have listed five of the best ones below.
1. OWASP ZAP (Zed Attack Proxy): A web application security scanner that is open-source is the OWASP ZAP which is used to find some of the security flaws in your web applications. It is relatively easy to understand which makes it good for developers and security personnel.
2. Burp Suite: Burp Suite is one of the most commonly used web application vulnerability scanners, which provides a set of instruments for testing and revealing vulnerabilities in Web applications. It can assist in the detection of problems like SQL injection, cross-site scripting, and other problems.
3. Netsparker: This is a tool whereby a web application scans for vulnerabilities in web applications and services such as SQL injection and cross-site scripting. It is worth mentioning that Netsparker has proved to be very accurate and its functioning is rather simple.
4. Acunetix: It is a type of web application vulnerability scanner that can detect all forms of security vulnerabilities in web applications including SQL injection, cross-site scripting, and other related vulnerabilities. Some of the biggest companies around the world use Acunetix.
5. Nikto: The Nikto web scanner is a security tool that scans thousands of possible security issues including outdated software and dangerous files in web servers.
How Does Qualysec Keep Your Web Applications Secure?
Qualysec is one of the best cybersecurity companies whose main goal is the protection of web applications against various threats. They include an efficient range of services that address the security requirements of your web applications.
Here’s how Qualysec ensures your web applications remain secure:
1. Comprehensive Security Assessments: Qualysec also applies vulnerability assessments and penetration testing to establish the probability of your web applications being vulnerable to security threats. These have incorporated the aspects of their professionals launching real attack scenarios in a bid to expose some concealed loopholes.
2. Customized Security Solutions: Qualysec is aware that every web application is different. It offers solutions on a subscription basis that are in line with your needs to give you the best security for your applications based on the leading threats.
3. Continuous Monitoring and Support: Qualysec has the service of security monitoring that runs all the time scanning for security threats and engaging them immediately. Their team of experts is always in a position to assist you in keeping the environment on the web safe.
4. Compliance Assurance: Qualysec makes sure your web applications are compliant with standard policy and law to prevent you from paying fines or facing legal problems while at the same time ensuring that the customer’s trust is secured.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
Web application security is one of the modern-day factors of cybersecurity as applications are business enablers, data processors, or world connectors. It is crucial to realize that the number of threats related to web applications increases and therefore advanced methods of protecting web applications should be established.
Website application security is not just a technical requirement; it’s a critical business necessity. By understanding the risks, implementing best practices, and leveraging the right tools and expertise, you can protect your web applications from the growing array of cyber threats and keep your business and customers safe.
So, understanding the value of secure web applications involves recognizing vulnerabilities, potential threats, and the measures to counter them. This is the first crucial step in protecting your online assets. With the proper tools accessed and the help of companies such as Qualysec, your web application can be safe, sound and serve your business securely against any other threats present within cyberspace.
Frequently Asked Questions
1. How to secure web applications?
Web application security entails appropriate security measures that involve security testing, SSL/TLS usage, secure authentication, filtering user inputs, and use of updated software. Security should also be given much attention and such things ought to be checked for including suspicious activities and security training for the development team.
2. What are the common security vulnerabilities in web applications?
Some of the typical Web application security risks are such as SQL injection, cross-site scripting, cross-site request forging, insecure authentication, insecure direct reference, and denial of service attack.
3. Is web application security different from network security?
Yes, web application security focuses on securing software applications that are accessible via the web, while network security is concerned with protecting the infrastructure, including servers, routers, and communication channels, from unauthorized access and attacks.
4. What are the top 10 OWASP?
The OWASP Top 10 is a list of the most critical web application security risks, published by the Open Web Application Security Project (OWASP). It includes risks like SQL injection, XSS, security misconfigurations, and sensitive data exposure, among others.
5. How does Qualysec ensure compliance with security regulations?
Qualysec works closely with your organization to understand the specific regulatory requirements you must meet, such as GDPR, HIPAA, or PCI DSS. They perform detailed security assessments and help you implement necessary controls to ensure your web applications comply with these standards, minimizing the risk of legal issues and ensuring the protection of your customers’ data.
6. Why is HTTPS important for web application security?
HTTPS encapsulates the information sent from a user’s browser to the web application to ensure that the attacker does not get access to information such as passwords, credit card details, and personal information. It is a security measure that protects against HTTPS/HTTP injection and man-in-the-middle attacks, while also providing data integrity and confidentiality for users.























































































































































































































































































































































0 Comments