In the digital age, in which each aspect of our lives is connected to technology, the need to defend our systems and information has never been critical. Imagine leaving your front door open in a neighborhood of potential disasters—that’s what an insecure device seems like. Security testing acts as your digital lock, ensuring hackers and threats don’t have an easy way in. But what exactly is security testing, and why has it become so important for organizations in 2025?
Let’s break it all down step by step in this comprehensive guide that is designed for everyone from curious individuals to business owners looking to secure their digital landscapes.
Why Is Security Testing Important in 2025?
Every year the digital ecosystem becomes more dynamic. As AI, the Internet of Things (IoT), and blockchain rise, they seem to open new doorways of innovation. However, with them comes new ways for cybercriminals to take advantage of their uses. So, the hackers are smart, and they learn from the innovations and they apply them to more sophisticated attacks. Industries like Healthcare, banking, and retail are among these, which makes security testing a mandatory aspect for every organization. This process aims to reduce financial losses, reassure consumers, and satisfy all regulatory requirements.
Key Objectives of Security Testing
The primary intention of security testing is simple: to become aware of and mitigate vulnerabilities before attackers do. Here’s a more in-depth look at its primary objectives:
- Identify Weaknesses: Pinpoint areas where the system is maximum susceptible to attacks.
- Ensure Compliance: Align with enterprise-unique policies together with GDPR, HIPAA, and PCI-DSS.
- Protect User Data: Safeguard sensitive customer and organizational data from unauthorized right of entry.
- Establish Trust: Build confidence among customers and stakeholders through ensuring robust security measures.
By addressing those objectives, even the most innovative software program could succeed in the face of a safety breach.
Types of Security Testing
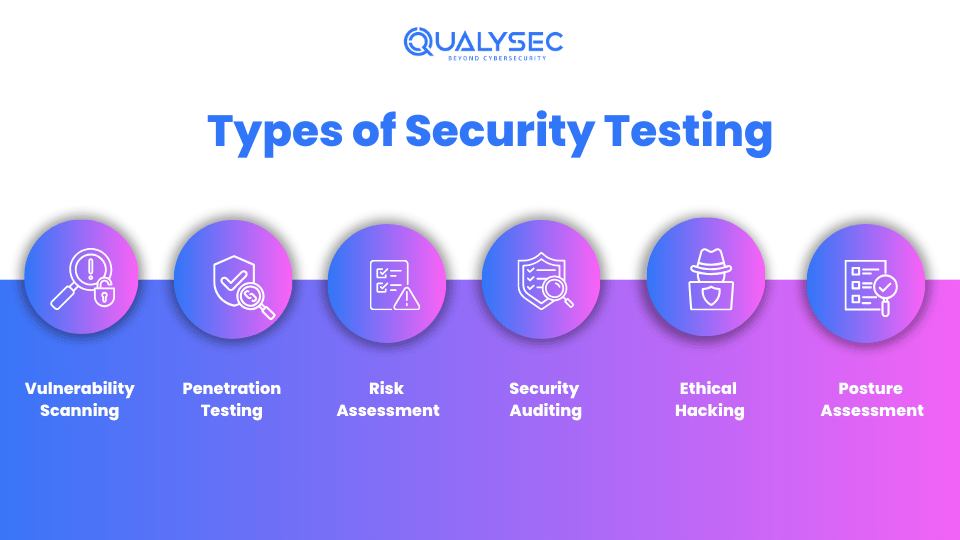
IT Security testing isn’t always a one-size-suits-all technique. It encompasses diverse strategies tailor-made to different systems and requirements. Let’s discover the important key types:
1. Vulnerability Scanning
This automated method scans systems to become aware of acknowledged vulnerabilities. It’s like digital health. Take a look at-up to your software program.
2. Penetration Testing (Pen Testing)
In penetration testing, ethical hackers simulate actual global attacks to check how the machine holds up under pressure. Think of it as a controlled fireplace drill to your system’s defenses.
3. Risk Assessment
Risk assessment evaluates potential risks, prioritizing them primarily based on their severity and impact.
4. Security Auditing
This includes an intensive evaluation of a business enterprise’s security rules and infrastructure to ensure compliance.
5. Ethical Hacking
Ethical hackers mimic cybercriminals however with permission, identifying gaps and supplying answers.
6. Posture Assessment
Posture assessment provides a holistic view of an agency’s general security stance, combining numerous testing strategies.
Each type of security testing serves a specific purpose and, when combined, provides a sturdy security framework.
Manual vs Automated Security Testing
When it involves protection checking out, companies often face a preference between guide and automated tactics. Here’s a breakdown:
Manual Testing
Manual testing includes human intervention, imparting a creative and flexible method. It is ideal for scenarios wherein attackers rely upon ingenuity in preference to predefined patterns.
Automated Testing
Automated testing makes use of tools and scripts to perform repetitive tasks at scale. It’s quicker, faster, and cost-efficient, however, it lacks the intuition that manual testing brings.
Why Not Both?
Most agencies undertake a hybrid technique, leveraging the high quality of each world for maximum security coverage.
Security Testing Process Explained
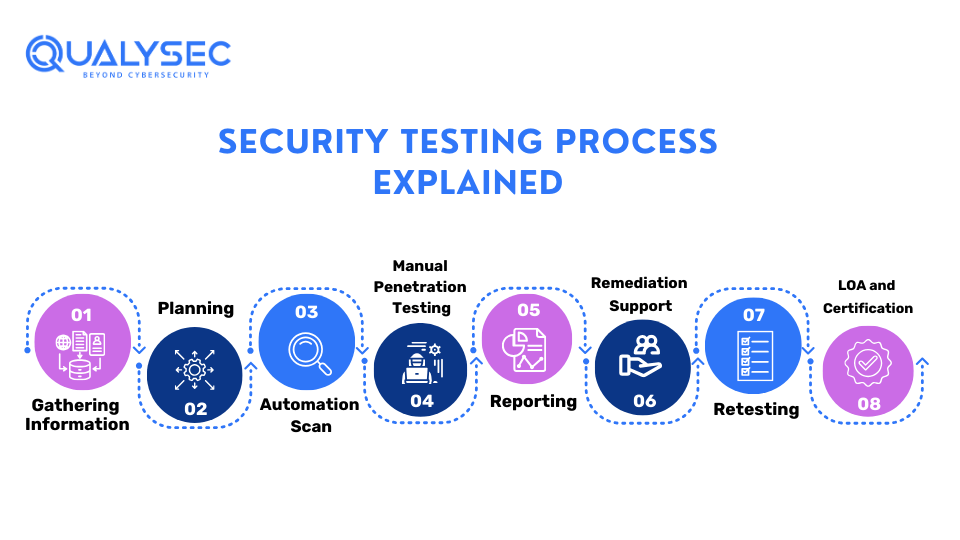
The security testing process is a systematic method geared toward uncovering and addressing vulnerabilities. Here’s the way it works:
- Planning: Define targets, scope, and resources required for testing.
- Information Gathering: Collect statistics approximately the gadget, which include its structure and known vulnerabilities.
- Execution: Run checks based on the selected methods (e.g., penetration testing, vulnerability scanning).
- Analysis: Analyze results to prioritize vulnerabilities and examine their capacity impact.
- Reporting: Create distinct reports outlining findings and recommendations.
- Retesting: Validate that each identified vulnerability has been resolved.
Following this process ensures thorough and efficient security assessment.
6 Principles of Security Testing
Here are the six basic principles of security testing:
1. Confidentiality
Among the important characteristics of data security, confidentiality is one of them. Confidentiality is an organization or individual responsibility to keep the information confidential. For example, confidential information is any information not intended for third parties. Confidentiality exists in order to safeguard the interests of those involved from leakage of information.
2. Integrity
Integrity is one of the core security concepts. It refers to system and data integrity. The whole reason integrity is used is that we want to be sure that a file or data record has not been altered or had unauthorized access. Integrity is one of the basic concepts of security itself and is always confused with confidentiality and non-repudiation.
3. Availability
The definition of availability is quite simple in information security, get your information when you need it. Downtime due to data disturbance usually creates problems such as loss of productivity, widespread loss of reputation, fines, regulatory action, and many more problems. So it becomes very important to make a plan for data availability in case of a data breach.
4. Authentication
This is the process of accepting or rejecting the truth of an attribute of a single piece of data claimed valid by an entity. Authentication can be seen as a set of security procedures designed to authenticate the identity of an object or person.
5. Authorization
Authorization is a security mechanism to determine access levels or user/client privileges related to system resources, including files, services, computer programs, data, and application features.
6. Non-repudiation
In the context of information security, non-repudiation means that it is possible to prove the identity of the user or process sending a particular message or executing a certain action. Electronic commerce has been made possible with the introduction of proof of non-repudiation because it protects businesses against fraud and ensures that a company can trust a message or transaction from a particular user or computer system.
Tools for Security Testing
In 2025, quite a few tools make security testing more efficient. Here’s a listing of some widely-used alternatives:
- OWASP ZAP (Zed Attack Proxy): An open-source device best for web application security testing.
- Burp Suite: A top preferred among protection experts for penetration testing.
- Nessus: Excellent for vulnerability checks and threat evaluation.
- Metasploit Framework: A powerful device for simulating real-world attacks.
- QualysGuard: A cloud-primarily based solution for vulnerability scanning and continuous tracking.
The choice of tool depends on your precise necessities and budget.
Common Vulnerabilities Identified
Security testing frequently uncovers vulnerabilities that could otherwise be ignored. Here are some of the common ones:
- SQL Injection: Malicious queries exploit the vulnerabilities present in the databases.
- Cross-Site Scripting (XSS): It injects harmful scripts on web applications that impact customers.
- Broken Authentication: Login mechanisms that are weak and lead to unauthorized right of entry.
- Data Leakage: Accidental exposure of sensitive records.
- Misconfigured Systems: Default settings that depart systems open to attacks.
Identifying these vulnerabilities is step one closer to a more secure system.
Benefits of Security Testing
Investing in cybersecurity pentesting brings numerous benefits:
- Prevent Data Breaches: It reduces the threat of unauthorized information access.
- Ensure Compliance: It avoids the fines and penalties imposed by regulations.
- Protect Reputation: It builds trust with the customers and the stakeholders.
- Cost Savings: Fixing vulnerabilities early is far less expensive than managing breaches later.
Challenges in Security Testing
Despite its importance, security testing isn’t without challenges:
- Rapidly Changing Threat Landscape: New threats emerge constantly, requiring continuous updates.
- Complex Systems: Modern systems are interconnected, making comprehensive testing more difficult.
- Resource Limitations: Time, price range, and expertise constraints can affect testing effectiveness.
Overcoming these challenges calls for a strategic approach and skilled professionals.
Best Practices for Security Testing
Here are a few guidelines to make certain successful security testing:
- Integrate Early: Include security testing in the development lifecycle to catch problems early.
- Use Reliable Tools: Invest in tools appropriate to your needs and frequently update them.
- Educate Your Team: Train personnel on best security practices.
- Conduct Regular Tests: Frequent security testing ensures that new vulnerabilities don’t go unnoticed.
Industries That Rely on Security Testing
Some industries are particularly reliant on protection checking out:
- Banking and Finance: Protecting customer data and stopping monetary fraud.
- Healthcare: Ensuring patient data confidentiality under HIPAA.
- E-trade: Safeguarding payment gateways and user information.
- Government: Protecting important infrastructure from cyberattacks.
Future Trends in Security Testing in 2025
Going ahead, here are some trends shaping the future of security testing in 2025:
- AI and Machine Learning: Automating hazard detection and prediction.
- DevSecOps Integration: Embedding security inside DevOps processes.
- Zero-Trust Security Models: Eliminating implicit acceptance as true throughout systems.
How to Choose the Right Testing Provider
When choosing a security testing service provider, recollect the following:
- Experience: Ensure the company has an understanding of your enterprise.
- Reputation: Check reviews and references.
- Flexibility: Choose a provider that gives tailor-made solutions.
3 Things to Check While Opting for an External Security Vendor
When a company has a limited budget for a security testing project, it often chooses to outsource this testing. An overarching question then arises in the minds of the professionals: How do you choose the right security testing vendor? Choosing the best vendor is not an easy task. The following are three things to consider when choosing the best cybersecurity pentesting vendor.
1. Make sure the company has an up-to-date vulnerability database and experienced security engineers.
2. Return on investment (ROI) must be positive relative to cost.
3. Check the reputation of the third-party vendor in the marketplace.
Security Testing with Qualysec
Qualysec is a world-renowned cyber security firm that offers state-of-the-art security testing solutions. It provides services ranging from test and vulnerability assessment to complete application security tests.
Companies of every scale use our products to test the security of their applications while protecting their digital resources. We offer complete solutions, which both security professionals and non-technical persons can use.
Our cybersecurity experts will perform a thorough security audit and penetration testing of your systems. Thereafter, Qualysec will provide you with a detailed and extensive report, along with an action plan to fix issues for any security vulnerabilities we detect.
Conclusion
Security testing is more than a technical requirement; it’s a business necessity in 2025. It helps companies protect themselves from economic and reputational damage by figuring out vulnerabilities and ensuring compliance. With an investment in the right tools and tactics, and the right people, businesses can stay one step ahead of cyber criminals.
FAQ
1. What is Security Testing?
Security Testing is the process of detecting the vulnerabilities in the software so that the chances of invading the infrastructure system of any company are avoided.
2. How is Security Testing different from Software Testing?
Cybersecurity penetration testing helps uncover vulnerabilities that a hacker may exploit to gain access to the systems. Whereas, software testing is concerned with discovering flaws in software functioning.
3. How expensive is penetration testing?
Penetration testing is between $490 and $999 per scan depending on your plan. To get an idea of how much Qualysec’s solution costs, visit our website.
4. Does Qualysec support Security Testing?
Yes, Qualysec provides both automated and manual security testing. Qualysec can support you in performing web application, mobile application, network, blockchain, and API security testing.








































































































































































































































































































































0 Comments