Android penetration testing refers to a detailed examination of mobile devices, applications, and systems to find possible vulnerabilities that an attacker might use. Ethical hackers, also known as white-hat hackers, use actual attack techniques to find vulnerabilities and exploit them.
The Android application penetration testing aims to discover attack surfaces and security flaws and provide a remediation recommendation on how to resolve them. This process helps organizations improve the security of their mobile assets thereby, ensuring lower chances of security breaches, damage to reputation, and losses.
Why is Android Penetration Testing Important?
Android app penetration testing is important because Android is one of the most used platforms for running apps like banking and social networking that are considered vulnerable to cyber-attacks. Therefore, through the identification and mitigation of vulnerability causes such as buffer overflow and malware, it directly improves the security of applications, increases efficiency, and directly leads to growth in customers’ trust. Hence, these proactive measures effectively detect the risk and cost of possible data breaches. Therefore, secure the private information of the customers.
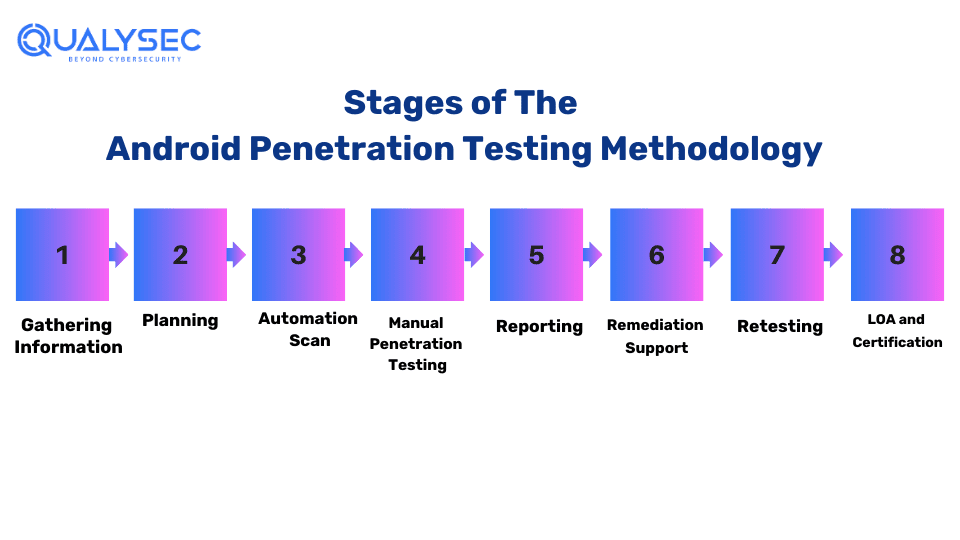
Stages of the Android Penetration Testing Methodology
There are several steps involved in carrying out penetration testing for Android apps. To identify and secure the application, each testing step is crucial. Here, we get in-depth knowledge about every step.
Step: 1
Information gathering is a comprehensive process that involves compiling all relevant data and evidence to support the current state of the objective or challenge.
Step: 2
Planning is the detailed processes that involve setting goals and taking appropriate action, as well as potentially making use of resources to help achieve the objectives.
Step: 3
Auto tool scanning is the strategy implemented by using automated tools that identify flaws on the surface level.
Step: 4
At manual testing, gathering data is crucial for the pen tester. Pen testers use a manual approach to test the security procedures. Therefore, they conducted a thorough review of the app, which led to the identification and mitigation of security issues. The most reliable part is at this point: there are no false positives.
Step: 5
In the reporting stage, the testers then provide the developers with an extensive report that includes all of the details about each vulnerability that was discovered, along with a level of severity and a mitigation reference.
To find out more about what a pen test report looks like and the advantages it offers, check out our extensive report for free.
Latest Penetration Testing Report

Step: 6
During the remediation stage, the task entails engaging with the vulnerabilities. If team members require assistance, the testing team will provide it to the development team by a consultation call.
Step: 7
During the retesting stage, the application is run by the app testers to make sure there are no more vulnerabilities. which confirms the app’s security.
Step: 8
LOA and Certification: The testing company is the one that issues this proof certificate. However, this is meant to offer the highest level of security for all users to use the application.
Benefits of Android Penetration Testing
Android penetration testing is crucial for several reasons:
Security Assurance:
Through penetration testing, the security of Android applications can be identified and their flaws and weaknesses can be corrected before the bad actors misuse these apps. Thus, this makes sure that the app is secured and that users’ data are protected.
Compliance:
Many industries and organizations have their own data security and privacy regulations. The process of penetration testing ensures that Android apps adhere to these criteria and rules.
Risk Mitigation:
Through the identification of these security issues, a developer has the opportunity to patch these problems before they turn into big threats to the organization or its users. Thus, this preventive approach minimizes the possibility of security breakthroughs and the costs that come with them.
Protecting User Trust:
Users demand privacy when transferring their data across mobile apps. Therefore, penetration testing is an effective way of upholding user trust because it shows the organization’s active focus on security and privacy issues.
Legal and Reputational Protection:
Penetration testing can offer legal protection in the case of a security breach by proving that reasonable precautions were taken to secure the application. Reducing the effects of any security incidents also aids in preserving the organization’s reputation.
Best Practices for Android Penetration Testing
Comprehensive Application Testing:
Implement in-depth analysis of the Android application using dynamic and static testing. Dynamic analysis is the process of running the application in a controlled situation to observe the behavior, whereas Static analysis means scrutinizing the application code, libraries, and dependencies for vulnerabilities.
Security Configuration Review:
Assess the security configurations of the Android device and the application. This entails examining permissions, data storage architecture, network communication protocols, and authentication schemes to identify all possible attack surfaces and security glitches that a hacker may exploit.
Input Validation and Sanitization:
Check the application for input validation and sanitization to safety against vulnerabilities. Input validation makes sure that user input is validated and sanitized correctly to prevent common attacks such as SQL injection, Cross-Site Scripting (XSS), and Command Injection. However, failure to properly validate and sanitize input can give way to extensive and severe vulnerabilities.
Data Protection and Encryption:
Assess the security of sensitive data stored on the Android device and transmitted over the network. Make sure that confidential data is encrypted in both in-motion and at-rest modes using the methodology of high-grade cryptography algorithms and secure protocols. Moreover, consider the implementation of key management practices to avoid unauthorized access to encrypted data effectively.
How Qualysec will help you in Android penetration testing?
When it comes to Android penetration testing, QualySec Technologies is a trustworthy partner. In addition to quality-driven testing, they use a unique approach that prevents false positives and finds real problems.
Organizations primarily choose QualySec because of our affordable prices. Additionally, they pay close attention to deadlines and base their partnership approach on mutual benefit. Additionally, the company acknowledges the value of privacy and promises to handle your information with the utmost secrecy.
Qualysec’s Android application security team uses strong tools, everyday status updates, and certified cybersecurity specialists to shield your application from potential threats. Hence, you can also enjoy dependability, assurance, and dedication to the mobile app’s security when you select QualySec Technologies as your partner.
To secure your mobile application and prevent it from getting attacked by hackers, schedule a call with the experts at Qualysec.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
The method employed to guarantee the reliability and security of mobile apps and devices is called Android app penetration testing. Protecting sensitive data, business operations, and regulatory compliance can be achieved through the use of cyberattack simulations and vulnerability identification. By implementing thorough planning, designing, and collaborating with developers, penetration testers can ensure that Android platforms are adaptable to various cyber threats. A safer environment for mobile apps to function in is ensured by carefully choosing the right tools and vendors, QualySec Technologies among them, to ensure that the focus is on Android app security in every aspect, leaving no opportunity open to attackers.
FAQs
Q. What is Android app penetration testing?
A. Android app penetration testing involves the process of analyzing the security of the Android application through simulating real-world attacks. Further, it covers detecting vulnerabilities, risk assessment, and suggesting security remediations against malicious exploitation as well as unauthorized access.
Q. How to test Android app security?
A. To test Android app security, conduct penetration testing to discover flaws, review code for damages, use dynamic analysis tools to detect runtime problems, and use static analysis tools for complete code review. Furthermore, analyzes data encryption methods for storage and transmission.
Q. What are the three 3 types of penetration tests?
A. The three types of penetration tests are:
-
- Black Box Testing
-
- White Box Testing
-
- Gray Box Testing












































































































































































































































































































































0 Comments