An information security practice called penetration testing aids businesses in locating holes and weaknesses in their IT infrastructure. This can guarantee adherence to information safety laws and assist stop assaults. Through imitating a crime, penetration testing tools evaluate an infrastructure business. These applications may consist of packet tests, networking sensors, both static and dynamic evaluation tools, and even more.
The Usage Of Penetration Testing Tools?
As a component of a penetration test (pen test), penetration testing tools are utilized to streamline specific processes, increase testing productivity, and identify problems that may be hard to spot with just human review methods. Two popular tools for penetration testing.
Methods for penetration testing
After threats and vulnerabilities are identified, their subsequent attacks ought to be concerned with those risks that were identified in the environment. The penetration testing should be commensurate with the degree of significance and size of an organization.
it should include all locations of sensitive data; all key applications that store, process, or transmit such data; all critical network connections; and all major access points. It should attempt to exploit security vulnerabilities and weaknesses present throughout the environment, attempting penetration at the network level and into core applications.
This would define the penetration testing in cyber security exercise, which ascertains if indeed there is a mechanism for unauthorized access to key systems and files. Once access is gained, all remedies and re-testing of penetration testing must ensure a clean test with no further access for unauthorized individuals or other types of malicious Works.
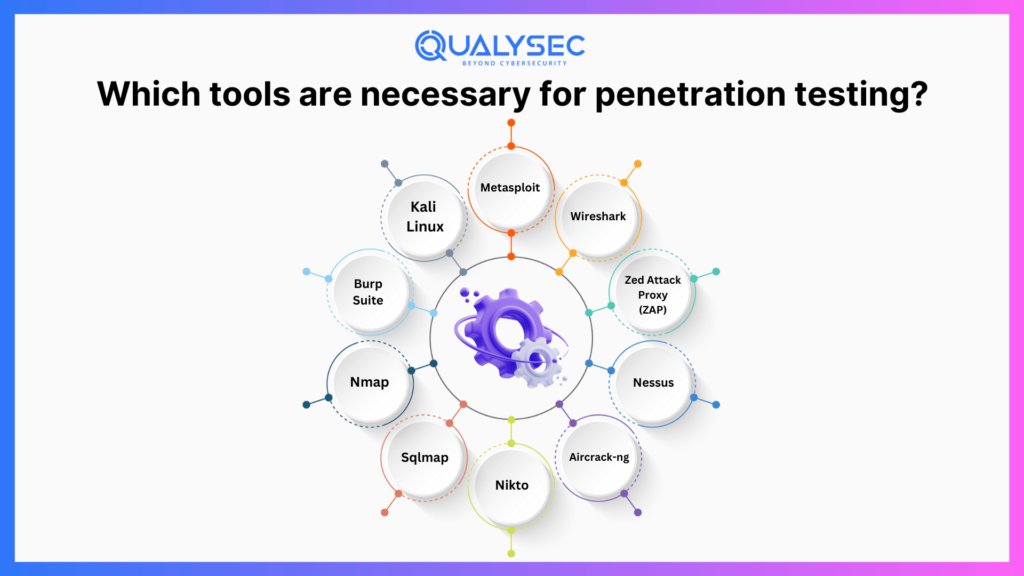
Which tools are necessary for penetration testing?
Whatever one intends to gain will impact it. People who are searching for a penetration testing tool usually fall into one of two groups: those who are pen testing specialists seeking specialized tools to accelerate their job or the organization that is seeking to streamline their safety measures and receive continuous defense.
Since these resources need more experience, I will begin this piece by discussing the tasks you may automate if one does not have much or no prior understanding of security.
Bright Security presents an advanced penetrating tool, relying on the DAST approach to protect applications, with Artificial Intelligence in its arsenal for the detection of complex security vulnerabilities that would otherwise fall prey to traditional methods.
Latest Penetration Testing Report

Metasploit
It establishes itself as preferred with vulnerability scanning, listening, and evidence collection being the main features, ideal for pen testers who are working with several different companies or applications.
Kali Linux
It is a pen-testing distro that contains some of the most powerful tools for sniffing and injecting, password cracking, and digital forensics.
Burp Suite
It is an easy-to-use web application security testing tool, offered free in community versions or for sale as a commercial professional edition.
Nmap
It can scan a single unit of IP, port, or host to a range of IPs, ports, and hosts; it can also be used, if programmed properly, to identify services that are actively running in the host.
Sqlmap
with its testing engine and several modes of injection attacks, is suitable for testing for injection flaws but is limited in detecting others.
Wireshark
It is an open-source tool used for real-time and network traffic analysis; it can show which systems and protocols come live in a network.
Zed Attack Proxy (ZAP)
It is free and free software that sits between your browser and the website you are testing.
Nessus
This checks the target machine, identifies running services, and creates a list of detected vulnerabilities.
Aircrack-ng
It is the tool that cracks the bugs found in wireless connections.
Nikto
It is an open-source web server scanner, that performs extensive tests against web servers.
The Penetration Testing Process
There are typically five steps in the penetration testing process. Penetration testers employ techniques that streamline data collection and the corporation’s utilization of resources throughout all of these phases.
Planning and reconnaissance:
The pentester defines the objectives and scope of a test. Based on the results, the pentester prepares for the test by gathering intelligence that may include reconnaissance on the method by which targeted environments may be compromised and what weaknesses may be present.
Scanning:
It helps the penetration tester get a better idea of how the target application might react to different intrusion attempts.
The pentester may perform any combination of static and dynamic analysis to access the target network.
Gaining access:
The pentester makes use of various pen testing techniques like SQL injection and cross-site scripting (XSS) for vulnerability identification.
Maintaining access:
The pentester now tries to answer whether an attacker would possibly make use of that vulnerability to give himself continuous access to the system and make available much more access.
Analysis:
The pentester prepares a rather elaborate report summing up all results from the application penetration testing procedure, activity or the very act.
The report usually specifies the exploited vulnerabilities, the duration spent undetected inside the system, the accessed sensitive information, and much more.
Why Should Companies Consider Qualysec As A Service Provider For Penetration Testing?
Choosing the right company could be crucial to getting the best service for you, even if it is frequently recognized that this is an essential phase in system security. Prominent penetration tests firm QualySec is proud of its in-depth penetration testing and reporting.
The solution and service that are included:
- Web App Pen Testing
- Mobile App Pen Testing
- API Penetration Testing
- Network Penetration Testing
- Cloud Penetration Testing
- IoT Device Pen Testing
The skilled penetration testers will examine the program throughout its entirety as well as its supporting architecture, which includes every network device, management platform, and other parts.
Our comprehensive analysis helps you find security vulnerabilities so you can fix problems before someone else can.
Another of our company’s main advantages is our proficiency in extensive cybersecurity penetration testing, where our experts carry out in-depth and complex analyses to find vulnerabilities in an organization’s digital infrastructure.
Additionally, these procedures probe deeply for defects in the system, going beyond cursory scans.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
Pen testing, its various forms, stages, and techniques, in addition to the information technology penetration testing methodology concerned, were all thoroughly explained in the following text.
Ultimately, this will be what cybercriminals would carry out the attack, and the defense team will work to protect the companies and get ready for intruders by conducting pen tests and taking advantage of them whenever possible to assess the harm.
Obtain thorough penetration testing tools and expert assistance from QualySec Technologies right now! To start the process of protecting your business and wealth, fill out the application.








































































































































































































































































































































0 Comments