What Is Website Security Testing?
The act of assessing a website or online application’s safety measures in order to find any possible risks, defects, or flaws that a hacker might take advantage of is known as website security testing. Website security testing aims to preserve customer trust while protecting important information and guaranteeing the website’s accessibility, privacy, and validity.
Building a safe web page and preventing the loss of sensitive information require routine website security testing. It assists businesses in locating and addressing security flaws, adhering to market rules and guidelines, and preserving customer trust.
How to conduct a website security testing?
There are two main approaches to conducting web security testing: manual testing and automated testing. Both approaches have their advantages and limitations and are often used in combination to achieve comprehensive testing coverage.
Manual Testing:
Utilizing human knowledge and instinct, manual testing finds weaknesses that machines would overlook. The person performing the test behaves like an individual on the web page, trying to attack loopholes by altering input areas, cookies, and HTTP calls.
Automated Testing:
This is the process of using applications that continually examine a web page for bugs and flaws. Automated instruments can effortlessly discover typical risks, saving valuable time during test. Yet, they may produce incorrect findings or overlook complicated flaws that need human evaluation.
Website Security Testing Methods and Devices
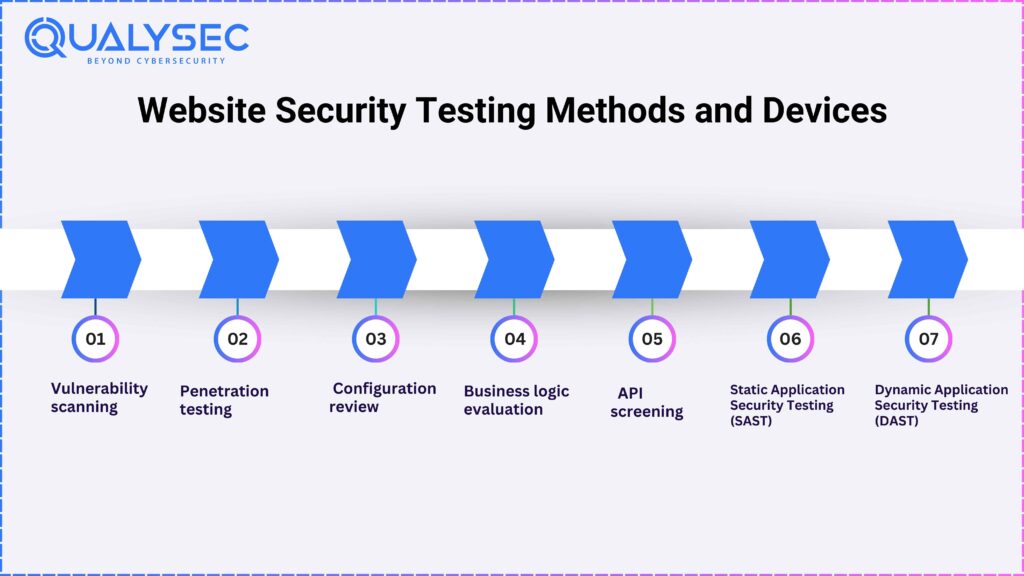
Website security testing procedures are several approaches for determining the safety of a web page or mobile application. These approaches assist in detecting risks, shortcomings, and faults that hackers may use. Several popular website assessment techniques and instruments include:
Vulnerability scanning:
An automated programs analyse webpages for identified vulnerabilities, errors, and out-of-date elements. Security scanners can swiftly discover safety holes and offer remedy recommendations
Penetration testing:
This traditional testing process involves security experts simulating real-life attacks on a web page or mobile app in order to find risks and flaws that machinery would overlook. A penetration test often combines bug abuse, and social engineering, and additional attack methods.
Configuration review:
security professionals check the configuration options of websites, servers for applications, data bases, and various other technological stacks elements to verify that they’re safe as well as up to speed.
Business logic evaluation:
This method examines the app’s business reasoning in order to find any faults or weaknesses that could give rise to improper or unauthorized behaviors. Manual analysis and the development of bespoke test cases are common methods in company intelligence testing.
API screening:
If an internet-based app employs APIs, safety testing ought to involve an assessment of the APIs for risks such as unsecured release of information, poor authorization, and entry restriction problems.
Static Application Security Testing (SAST):
SAST tools examine the original source of an online application to detect possible weaknesses, programming mistakes, or unsafe development methods. SAST tools include SonarQube, Checkmarx, and Fortify.
Dynamic Application Security Testing (DAST):
DAST instruments interact with an active web-based application to look for safety risks such as validating input problems and identification faults. Burp Suite and OWASP ZAP are prominent DAST utilities that may be utilized in this manner.
Latest Penetration Testing Report

Recommended Practices for Website Security Testing
Make testing for cross-browser compatibility a priority
Due to the possibility of safety issues emerging from various browser’ interpretations of the source code of a site, cross-browser compatibility testing is crucial during website security scan. For instance, an internet page that is safe in a particular browser might have weaknesses in security in others.
You can find and address any possible bugs by testing the website across a variety of browsers and platforms. subsequently is also critical that you evaluate the internet address on cell phones, which utilize numerous browsers and might include various security issues.
Employ based on risks assessment
Risk-based assessment aims to discover and mitigate most significant risks and vulnerabilities. This strategy entails evaluating the probability and possible effect associated with every vulnerability in order to arrange the screening attempts, making sure the more significant hazards are taken care of immediately.
To properly execute based on risk evaluation, companies need to have a thorough grasp regarding their website’s resources and possible dangers.
This involves detecting private data, like user passwords, banking data, or private data, as well as comprehending the sorts of assaults which are the most prone intended for a website.
Establish a security vulnerability incentive system
To fill out reward systems associated with ethical hackers in recognizing and reporting security vulnerabilities from the website owner and developer, a bounty program is a reward scheme. Having a bounty program works in a few ways for testing the security of a website.
Identifying vulnerabilities:
Ethical hackers working in the bounty program can bring their skills to bear, identifying and reporting a vulnerability that can be costly to automate or be detected through manual testing.
Creating a good reputation:
A bounty program will leave a positive impact on the website owner or developer. Security shows dedication to the website and willingness to collaborate with the security community in recognizing and addressing the issues.
Lowering testing costs:
The bounty program can help reduce the cost incurred during a website security audit. Instead of hiring security experts to perform regular security tests, the bounty program can enable ethical hackers to do the testing for pay.
Perform penetration testing:
Penetration testing, sometimes called hacking with ethics or penetration testing, is an important suggested procedure for website security assessment.
It involves modelling practical attacks on your internet site or mobile application in order to detect flaws and flaws prior hostile attackers attack them.
Frequent penetration testing allows you to discover safety hazards that computers or human testers could have overlooked while initiating proper action to fix them.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
Web security testing is a method of guaranteeing a web application is safe and that any vulnerabilities have been resolved. As a result, companies and associations must guarantee they do safety monitoring on frequently through external services.
Qualysec is a major cybersecurity organization that specializes in website security testing services for enterprises. As a result, using Qualysec may help businesses eliminate vulnerabilities and comply with numerous standards.








































































































































































































































































































































0 Comments