In the networked digital space, taking care of organizational assets is becoming more of a crucial issue. A security risk assessment becomes a foundational task that aids in the identification and reduction of the effects of the possible sources of threats. It involves multifaceted analysis of impacts and probabilities, and applying strategies to strengthen the defenses. As per IT governance, authorities recorded 2,080,728379 publicly breached data in 2024, which is still increasing.
With detailed coverage of the security risk assessment, organizations can strengthen their resilience, achieve compliance, and lessen the effects of security events. In this blog, we’ll study how this fundamental mechanism enhances the current organizational model through adaptation to changing threats.
Security Risk Assessment Definition?
A security risk assessment is a process of identifying, analyzing, and evaluating strengths, and weaknesses. Additionally, potential threats target organizations’ assets, such as information, technology, staff, and physical infrastructure. It covers the systematic process of risk assessment, that is, measuring the risk probability and its consequences on the organization. This way of assessing security will enable the professionals in this field to bring the importance of risks in order. Hence, methodically develop strategies to get rid of them or to manage them effectively.
Performing security risk assessment in advance enables organizations to proactively combat the visibility, manage compliance with the regulation, and lessen the negative effects of security incidents. The protection of the organization at large and its resources is an effort to enhance overall resilience.
The Purpose of Security Risk Assessment
Cyber Security risk assessment is the key process that helps to specify, examine, and rank possible threats to company resources, operational abilities, and employees. It is mainly monitoring the systems with the view to eliminate any risks whether they are weaknesses or exposure to threats and curtailing their detrimental effects.
Identify Assets:
These real and abstract resources are important to an organization and need to be safeguarded. These cover applications, IT infrastructure, data, intellectual property, human resources, and so on.
Recognize Vulnerabilities:
Vulnerabilities are understandable errors in assets or systems that can be exploited by a hacker. These might be technical vulnerabilities such as software bugs or a careless manner of configurations, but also human ones, for instance, social engineering.
Identify Risk:
Threat assessment is done by taking into consideration the potential harm. Additionally, the threat that is going to be used to exploit a vulnerability to cause damage to an organization. It takes into account the severity of the logical error. The error poses a high risk of exploitation for attacks, and the effects of such exploitation.
Remediate Them:
Risk mitigation is applied to fix the security loopholes. Find them through testing the system against however many security tools used. This could consist of patching software, updating configurations, deploying security controls, training employees, etc. Verify the effectiveness of remediation by performing an audit.
What is the Difference Between Risk Management and a Security Risk Assessment?
| Aspect | Risk Management | Security Risk Management |
| Scope and Focus | Risk management is not only about anticipation and control of risks. It extends into a wider spectrum, involving the identification, assessment, and prioritization of risks in different areas. It includes financial, operational, and strategic focal points. | Security Risk Assessment is a specific subset of risk management. It particularly focuses on security threats and vulnerabilities found within an organization’s infrastructure, systems, and processes. |
| Purpose and Objectives | Risk management is aimed at improving the decision-making process. Through the entire and timely risk assessment, bearing in mind the possible effect of identified risks on the business objectives and working out the most appropriate techniques for managing or mitigating these risks. | This risk assessment type is commonly called security risk assessment. It aims to determine security vulnerabilities and evaluate their chances of occurrence. Equally, the magnitude of damage that may be caused by them, and then suggest specific measures to make the system more secure against any potential risks. |
| Implementation and Execution | Risk management involves the development of a risk management infrastructure. The building up of risk management frameworks, policies, and procedures, and the setting up of a multidisciplinary team that uses tools and methods such as risk registers, scenario analysis, and risk modeling. | Security risk assessment in most cases follows a certain structured way that entails asset/threat identification, vulnerability assessment, and risk analysis methodologies. It may include penetration testing, vulnerability scanning, and security audits which can be tailored to meet the specific security requirements. |
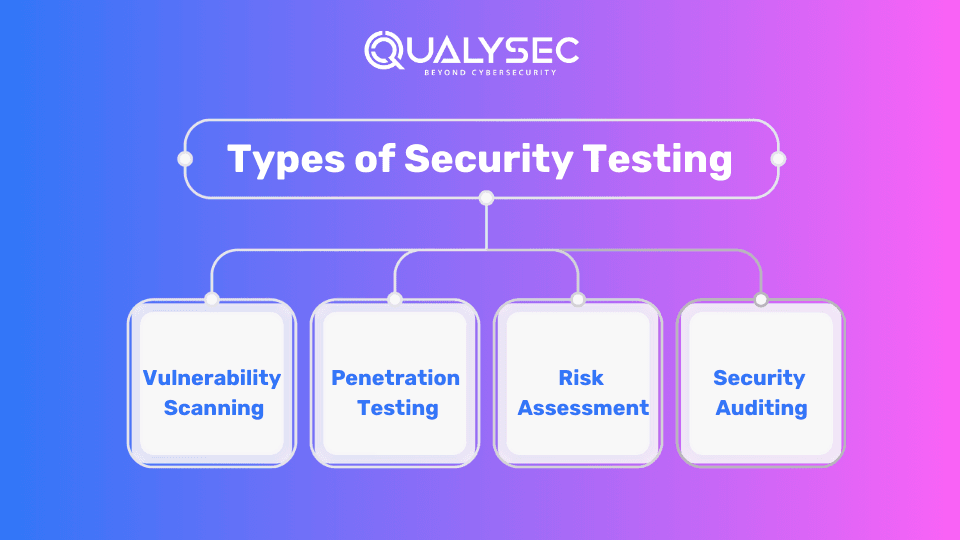
Types of Security Testing
Security risk assessment is the most crucial aspect that is used to protect the systems against cyberattacks. It implies the use of different techniques such as penetration testing, vulnerability assessment to review the code, risk assessment, and security auditing. It plays a major role in the identification and mitigation of security risks.
Vulnerability Scanning:
Vulnerability scans are done usually with the help of automated tools. Organizations can find weaknesses in the software, network, or system as they scan it. It becomes evident that vulnerabilities, such as a forgotten patch, misconfiguration, or weak encryption, could be provoked by the attackers.
Penetration Testing:
Penetration testing, also known as ethical hacking, replicates actual attacks and helps in assessing the security level of a system. Skilled security experts try to exploit vulnerabilities and in doing so get in without permission. By showing various ways of getting in and recommending how to make the systems stronger.
Risk Assessment:
Risk assessment is conducted through a process of identifying and evaluating risks and their impact on the stability of the security package. Furthermore, it helps to prioritize security measures by giving the sum of the risk factors such as the chance of happening, the extent of the damage, and defensive strategies contrary to the risk.
Security Auditing:
The role of a security audit involves the complete overseeing of an organization’s security controls, policies, and strategies. It allows you to verify compliance with security standards, highlight issues, and recommend measures that will improve the security posture.
conduct a vulnerability assessment and penetration testing (VAPT) or your applications in one place. Choose Qualysec to protect your business digitally now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Steps for Security Risk Assessment
The process of starting a thorough security risk assessment is inherently characterized to reveal virtual security loopholes point-blank. So, let’s jump into a detailed description of the security assessment.
Data Gathering
in the first stage, the concentration is solely on the collecting of exclusive data. This testing team works with their clients closely and gets to know key application details. Now it is important to emphasize that users’ roles, permissions, and data flows are well-known for building an appropriate testing strategy.
Strategic Planning and Scoping
The assessment service provider takes in-depth environmental and functional aspects of the application, setting up clear milestones and goals. This in-depth analysis helps them adjust and modify the testing method to precisely identify weaknesses as well as threats. Developing the strategy for penetration testing implies setting up the scope, decision of the methodology, and criteria of the testing. A detailed checklist serves as the baseline and identifies the major components including authentication methods, data processing, and input validation.
Automated Scans
Automated and intrusive scans are critical, especially in a staging area. Specialized programs provide for exposed places on the application’s inner network where they possibly cause a breach. Performing such intrusive scans can expose the surface-level vulnerabilities of the staging environment at the earliest possible point.
Manual Penetration Testing
Cyber risk assessment companies offer in-depth manual penetration testing services that are adapted to correspond with the particular needs and security standards of the entity. Such technique thus results in the complete assessment of vulnerability throughout all the crucial sectors. Manual penetration testing is conducted on multiple platforms such as:
-
- Web Applications
- Mobile Apps
- Cloud Applications
- AI/ML Applications
- IoT Devices
- APIs
Detailed Reporting
The tester team pinpoints the vulnerabilities and provides a systemic representation of the risk· The report also includes steps to fix these vulnerabilities effectively. A senior consultant conducts a high-level penetration test and reviews the comprehensive report.
Check out a real penetration testing report with just one click!
Latest Penetration Testing Report

Guidance through Remediation
Through consultancy calls, the risk assessment team helps the development team eliminate identified vulnerabilities. Developers and penetration testers have the advantage of direct engagement. This gives them a chance to propose solutions for the identified vulnerabilities that will result in swift and efficient remediation, thus nurturing the security posture of the application.
Evaluating Efficacy through Retesting
After all the mitigation steps are applied, the testing team goes through a detailed retest procedure. This is done to check whether the remediation methods worked or not.
LoA and Certification
The security risk assessment company provides a Letter of Attestation as a witness to the organization’s security level based on testing. This letter serves multiple purposes: conforming, exemplifying, as well as tackling security regulatory issues. Furthermore, the organization will provide a Security Certificate, which is just another element that ensures a sufficient level to respond to all the cybersecurity requirements of today’s changing world.
Conclusion
Security risk assessment is an essential pillar for the establishment of effective organizational resilience. It is constantly adapting to the dynamic threat landscape. Through the careful assessment of assets, weaknesses, and threats, companies can develop customized plans to reduce possible damages. Various methods such as Vulnerability scanning, penetration testing, and risk evaluation can be employed to reinforce the protection barriers as well as implement strong security measures.
Nevertheless, keeping the assessment cycle of identification, repair, and retesting continuously reassures progressive risk management of valuable instruments. Implementation of the security risk assessment is not only a step towards compliance and visibility, but it also builds a culture of vigilance, resilience, and readiness in response to many new threats.
FAQs
Q: What are the basic components of security risk assessment?
A: Security risk assessment involves several stages, such as highlighting the target assets, assessing the threats and vulnerabilities, evaluating the impact level, determining the risk level and the strategies on how to mitigate. Additionally, this involves examining the documents, reviewing the facts, and then determining if the measures are still relevant or otherwise.
Q: What is the security assessment?
A: A security assessment is an appraisal procedure implemented to identify and analyze vulnerabilities and risks. Additionally, measuring the security posture of a system, network, or organization. It includes prioritizing which vulnerabilities should be addressed by implying a comprehensive plan. Therefore, to reduce the risks and create a dependable security framework.
Q: What is the purpose of a security risk assessment?
A: A security risk assessment identifies and assesses any threats and vulnerabilities within a system, organization, or environment. The main goal of this framework is to find out, examine, and place some priority on risks. Furthermore, apply adequate mitigation methods to protect the assets, the information, as well as the operations.
































































































































































































































































































































0 Comments